Top 10 Web Application Security Hazards
{ Part - 2 }
Null - Humla Session
Flipkart - Bangalore
Disclaimer
- This presentation is intended for educational purpose only and I cannot be held liable for any kind of damages done, whatsoever to your machine, or any other damages.
- Don't try this attack on any other system without having context knowledge or permission, this may harm someone directly or indirectly.
- Feel free to use this presentation for practice or education purpose.
^ I hope - You gotcha ^
Agenda
- No Revision of Part - 1
- Understand New Attacks
- Self exploratory exercise
- Learn + Hack
- Q & A
 for Social Media
for Social Media
Twitter handle
Hashtag for this session
Humla
Means 'attack' in Hindi



Objectives for this session
- Build Security Awareness for web application
- Learn way to discover Security vulnerabilities
- Learn basic of secure web application via OWASP Top 10
Let's Begin our Journey
of
Top 10 Web Application Security Hazards
* We won't talk about Injection & XSS *
Setup the Test Lab
Install XAMPP
Acronym for:
- X (to be read as "cross", meaning cross-platform)
- Apache HTTP Server
- MySQL
- PHP
- Perl
Targeted Application
Client Side language : HTML & Javascript
Server side Language: PHP
DB : MYSQL
Why PHP ? - Any answer Here?
Why MySQL? MySQL is Girlfriend of PHP <3
PHP is used by 82.2% of all the websites as server-side programming language.
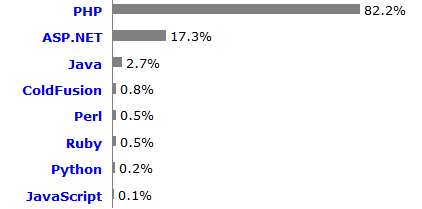
http://w3techs.com/technologies/overview/programming_language/all
PHP: 244M sites

2.1M IP addresses

Don't Mind Power of PHP > Facebook & yahoo
http://w3techs.com/blog/entry/web_technologies_of_the_year_2013
Play ground
Mutillidae
It's a free, open source web application provided to allow security enthusiast to pen-test and hack a web application.
V.2X developed by Jeremy Druin aka webpwnized.
All set with Multillidae ?
Am I Vulnerable To 'CSRF' ?
OWASP A8 - CSRF
Cross-Site Request Forgery
CSRF Attack Cycle
CSRF AKA. XSRF
The attacker exploits the trust a website has against a user’s browser.
- Permission faking\stealing
- Disruption of the normal sequence of the site
Demo #1
Login ID - admin
password - adminpass
HTTP GET Request
http://127.0.0.1/xampp/mutillidae/index.php?do=logout
: Answer Demo 1:
<html>
<title> CSRF Demo 1 </title>
Click me </a>
</html>
Understanding
- Logout page was a simple HTTP GET that required no confirmation
-
Every user who visited that page would immediately be logged out - that's CSRF in action.
Yes it's not dangerous but annoying
So what do you think,
it's all about Click ?
ssh, No!!
Would you like to write CSRF exploit without click ??
Image Tag
<img style="display:none;" src="your Request">
Image tag does not require clicking the link compared Tag-A requires clicking on the link to activate the HTTP request
Can we try Demo 1 with Image tag ?
CSRF GET Request with Image Tag
<html>
<title> CSRF Demo 1 </title>
</html>
The Nature of browsers is to send HTTP requests to visual objects such as picture or remote files (CSS, JS, etc.) even while loading the page without the user's permissions.
Iframe tag
<iframe
src="your Request"></iframe>
Java
Script code
X.src = "URL";
Can we try Demo 1 with Iframe & JS ?
HTTP Request
<iframe
src="http://127.0.0.1/xampp/mutillidae/index.php?do=logout"></iframe>
<script> var X= new Image();
X.src= "http://127.0.0.1/xampp/mutillidae/index.php?do=logout";
</script>
Challenge #1
:: Solution #1 ::
<html>
<title> CSRF Demo 1 </title>
<a href =http://127.0.0.1/xampp/mutillidae/index.php?page=user-poll.php&csrf-token=&choice=nmap&initials=n&user-poll-php-submit-button=Submit+Vote>
Click me </a>
</html>
Challenge #2
{ Post HTTP Request }
: Solution Available :
http://127.0.0.1/xampp/CSRF Attack/Add New Blog Entry - CSRF POST.html
Does it easy to create CSRF HTTP request ?
No - you should try out
~ CSRF Finder Firefox add-on ~
* One Click POC *
* Hybrid automation *
Thank you - Piyush Pattanayak
CSRF Finder Demo
Live Challenge
* Signup disabled *
Please use the username test and the password test
CSRF & XSRF
Update the user info. without their knowledge
http://testphp.vulnweb.com/userinfo.php
You've been CSRF'd with static token!
Can we exploit this with Level #2 ?
Popular Cool findings
Facebook CSRF worth USD 5000 by Amol
Google Groups Profile CSRF
Google Account display pic deletion
Facebook Account deactivation
Advance Leanings - CSRF Token Validation Fail
http://haiderm.com/csrf-token-protection-bypass-methods/
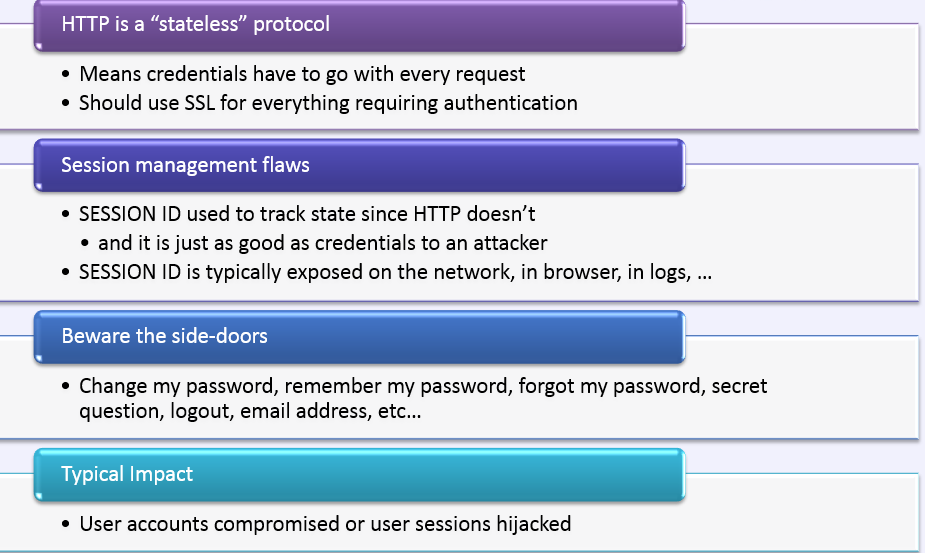
Am I Vulnerable To 'Broken Authentication &
Session Management'?
A2 - OWASP TOP 10

Lets' bypass the Mutillidae
Can we do it ?
Part -1 Learning with SQL Injection
Apply Brute Force Attack
/xampp/mutillidae/index.php?page=login.php
Account Lock Policy & Captcha missing :P
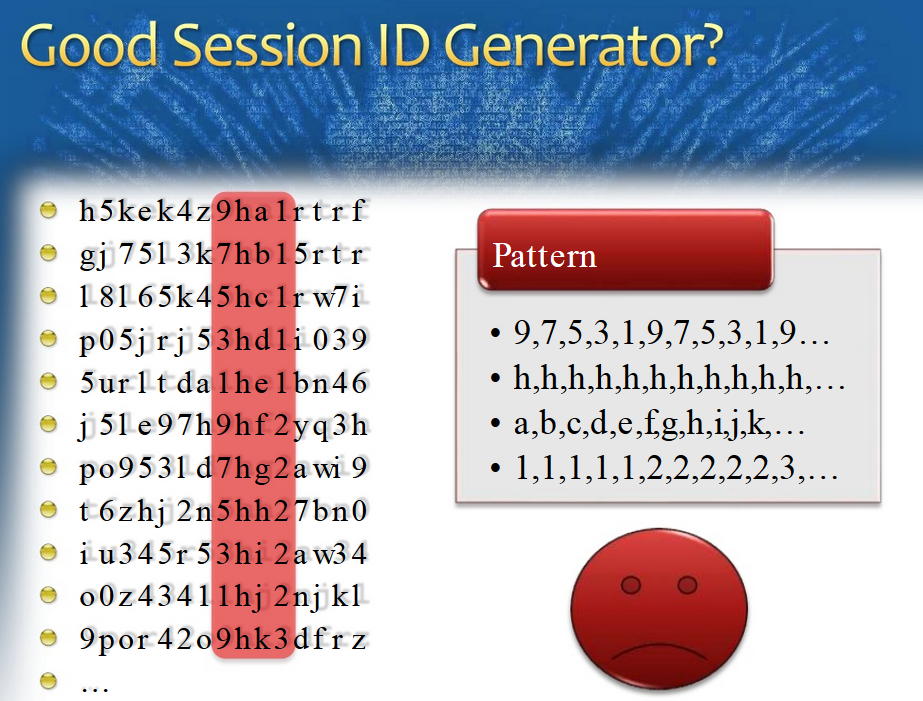
In-secured Session-ID
XSS Session Hijacking
PHPSESSID=0ebmp37g8v8stqsjpf1ln40c20
JSESSIONID
ASP Session.SessionID
Let's Try out Part 1 learning and exploit the session
So, Let's Learn about Web App DB structure
Passwords are stored in plain text.
oh really -- ':(
OWASP #A6
Password is protected, when stored using encryption algorithm. Are you sure?
http://www.md5online.org/
You may also try out hash but password salt is a recommended solution so far.
Password Policy should be applied nicely and should not be weaker.
-- * --
Security & Business logic should be applied for changing password.
Change password doesn't ask for Current password - LOL
Robots.txt
All Sensitive data expose
Take Away
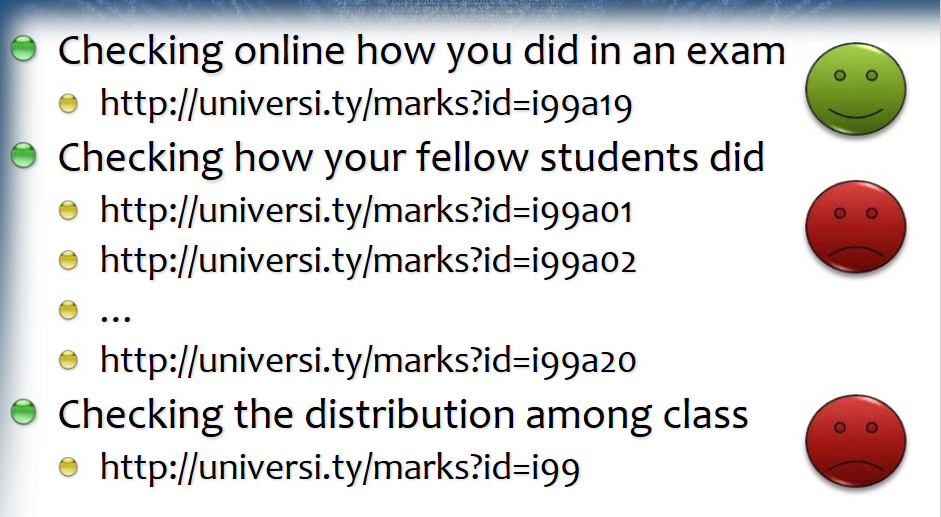
Avoiding Insecure Direct Object References
URLS' Pattern

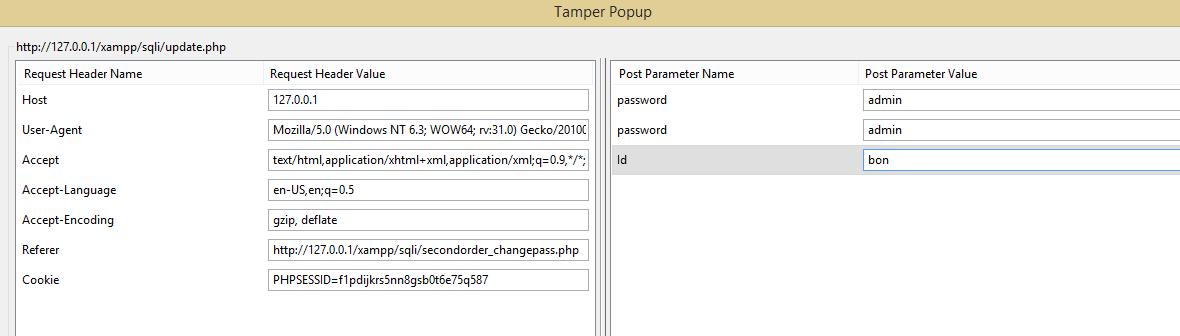
Enumeration using parameter
https://99tests.com/testers/3298
Secret PHP Server Configuration Page
http://127.0.0.1/xampp/mutillidae/index.php?page=phpinfo.php
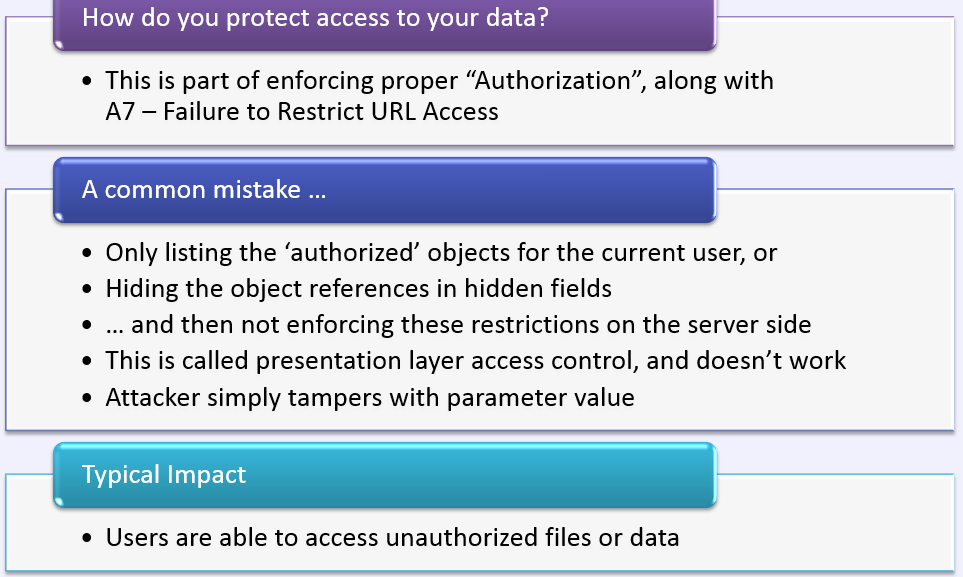
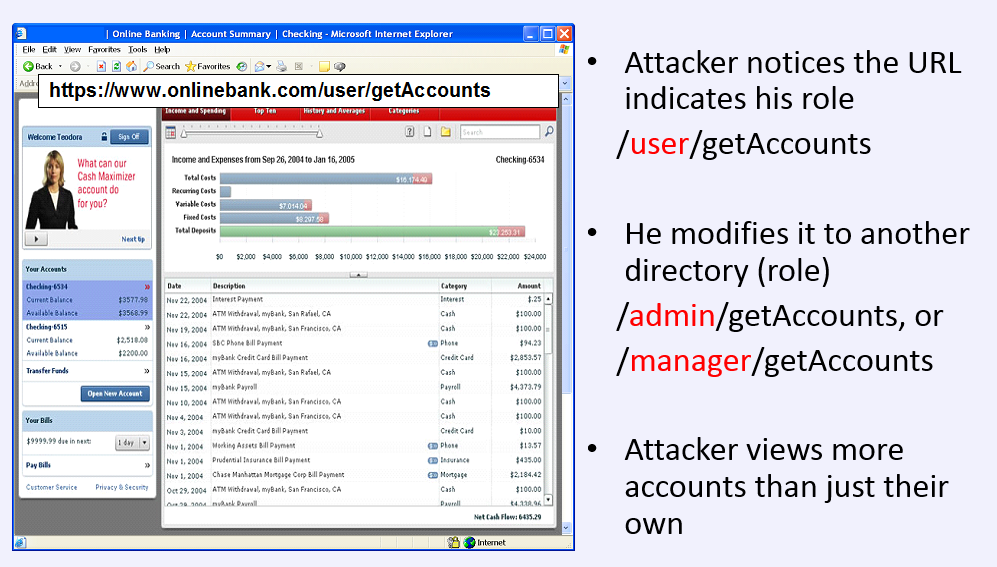
Missing Function Level Access Control
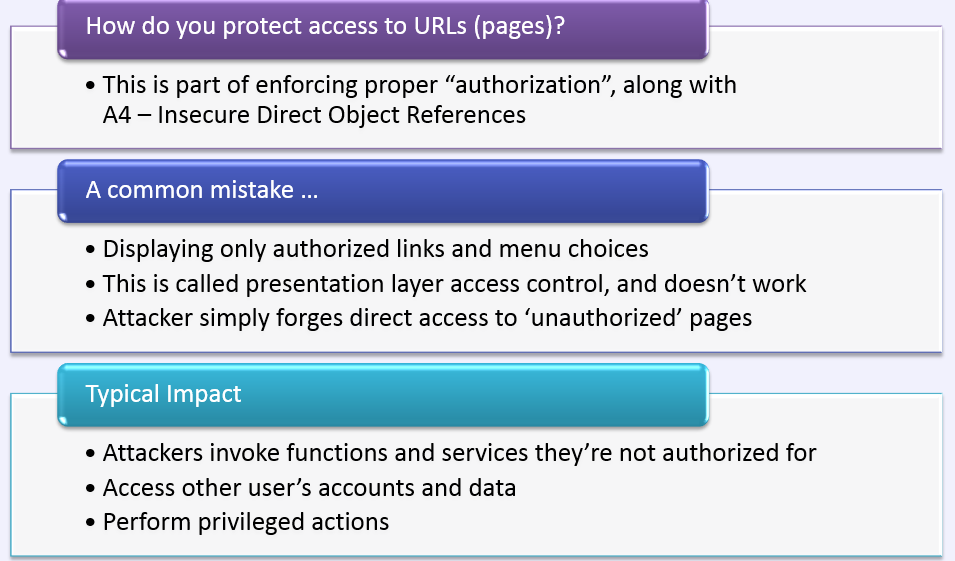
Concept
LIVE
http://stepinforum.org/mailers2014/
OWASP #A9
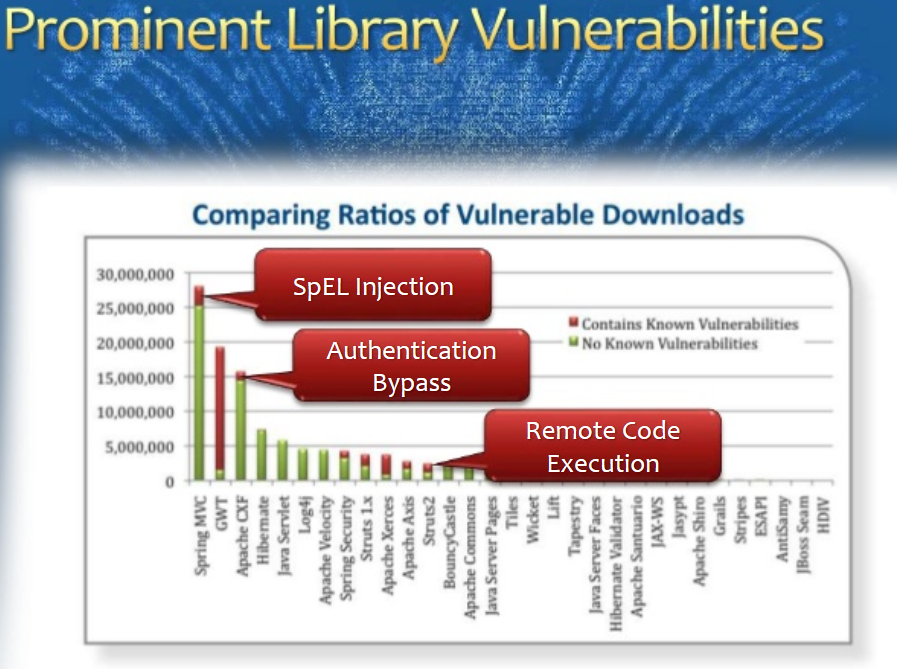
Using Known Vulnerable Components
Cool Wordpress Projects
Latest buzzing known vulnerabilities
Google - SSL Heart bleed Fix verification script
https://lastpass.com/heartbleed/
History Attack !!!

Security Misconfiguration
OWASP -#A5

Click Jacking
Code: – <iframe src= http://www.testingcircus.com> </iframe>
Live Demo: – http://goo.gl/6gEq2I
Click jacking Testing tool: – http://goo.gl/27VgQb
If you are planning to host your own server
"Securing a Linux Web Server in 10 Steps"
by Akash Mahajan
Elmah.axd Error logs
Google search
https://www.owasp.org/index.php/Top_10_2013-A10-Unvalidated_Redirects_and_Forwards
Vulnerable Redirection
http://127.0.0.1/xampp/mutillidae/index.php?page=redirectandlog.php&forwardurl=http://www.owasp.org
I don't think so, i need to explain you what you can do here :D
Yes - I'm Done!

Feel free to write me at bug.wrangler at outlook.com
We need you!
- Attend Null Meets-up & give presentations.
- Share your ideas & leanings.
- Talk to our community champions & gain from leanings.
- Your feedback helps us to build a good community.
- Looking forward to your ongoing support.
http://null.co.in/
Say 'Hello' @null0x00
Credits

- Twitter Folks -
@TroyHunt , @yog3sharma , @Lavakumark @HaiderMQ
#Nullblr Leads & Champions
Big thank you to @null0x00 ,@ru94mb & you All.
Indian Hackers/Infosec guys & groups you should be following in Twitter
Thank-you http://garage4hackers.com/ community
Thank you!
Keep the security ante up.
License and Copyrights
Copyrights 2013-2014 Abhinav Sejpal
-----
(CC BY-NC-ND 3.0)
Attribution-NonCommercial-NoDerivs 3.0 Unported
Dedicated to my lovely daddy