Actionable Blockchain Cybersecurity Solutions -
WEST AFRICA CYBER SECURITY AND BLOCKCHAIN TECHNOLOGY CONFERENCE
(WACSBTC2018)
Presenter: Chimezie Chuta,
Coordinator -Blockchain Nigeria User Group
The Blockchain Technology is...
A Distributed Digital Record of Transactions, Secure, Immutable, Append-only, Decentralized, Time-stamped, Hashed and Transparent.
Demo: http://www.blockchainnigeria.group/blog/explaining-bitcoin-hash-functions-newbie
Blockchain & Cybersecurity
Cybersecurity professionals should see themselves as the Guardians of the World’s Data and infrastructures
Blockchain & Cybersecurity
As a technology built primarily with security in mind, blockchain offers a lot of promise in terms of its cybersecurity potential
Blockchain & Cybersecurity
Proving that someone is who they purport to be on the web is not easy, and determined attackers are extremely adept at spoofing, phishing and mimicking their quarry.
Blockchain & Cybersecurity
It's all about Critical DATA and fight to own the
1s and 0s.
Blockchain & Cybersecurity
Data exists to be shared among counterparties, partners, clients, customers, and colleagues. Ensuring that data is only accessible to authorized eyes is a complex task.
The Blockchain Technology
TYPICAL DATA STATES
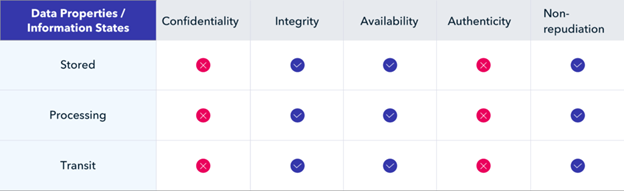
The Blockchain Technology
DATA PROPERTIES
Data Should Have Integrity
Data Should Have Confidentiality
Data Should be Accessible
Data Should have Authenticity
Non- repudiation
TYPES OF BLOCKCHAIN
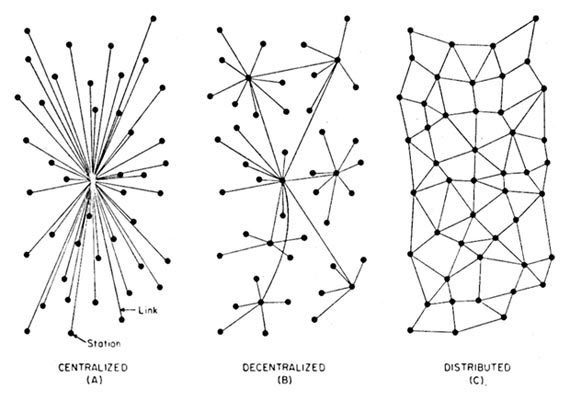
A true Blockchain has to be Decentralized & Distributed.
TYPES OF BLOCKCHAIN
A true Blockchain has to be Decentralized & Distributed.

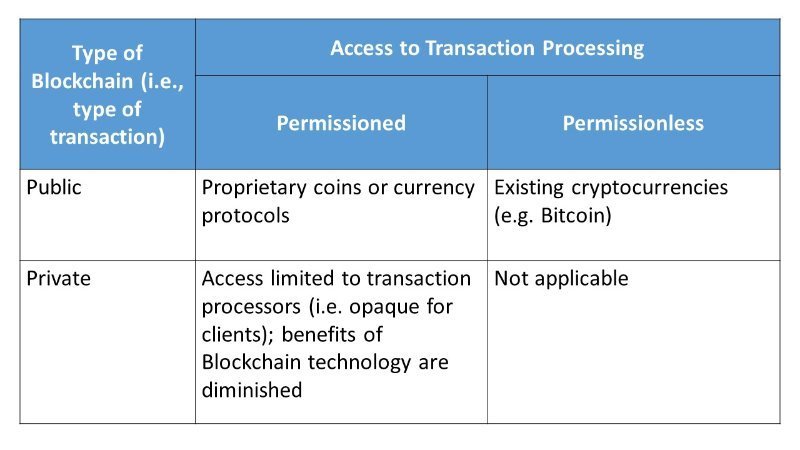
TYPES OF BLOCKCHAIN
Public, Private, Consortium Blockchains exist.
The Blockchain Technology
Demo: http://www.blockchainnigeria.group/blog/explaining-bitcoin-hash-functions-newbie
HASH FUNCTION
Core

The Blockchain Technology
HASHING VS ENCRYPTION
Core Security
Hashing is used to validate the integrity of the content by detecting all modifications and thereafter changes to a hash output. Encryption encodes data for the primary purpose of maintaining data confidentiality and security. It requires a private key to reverse encrypted text to plain text.
The Blockchain Technology
-
DATA LAYER : Blocks
COMPONENTS
Blocks are time-Stamped
Nonce
Previous block transactions
Merkle Root Transactions
(Merkle Tree is used to cheaply prove the existence of a piece of data without validating the entire data set)
The Blockchain Technology
COMBATING DDoS
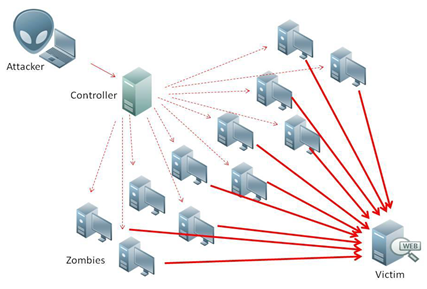
The Blockchain Technology
COMBATING DDoS
A DDoS (distributed denial of service) attack occurs when many devices connected to the Internet are recruited (as part of a ‘botnet’) to ‘attack’ i.e. simultaneously and repeatedly send traffic to a victim’s server with the aim to overload it.
The Blockchain Technology
COMBATING DDoS
The average financial cost of a DDoS attack for a small or midsize business is about $123,000
The Blockchain Technology
COMBATING DDoS
DECENTRALIZATION OF CLOUD SERVICES
Maidsafe, Blockstack
The Blockchain Technology
DECENTRALIZATION

The Blockchain Technology
DECENTRALIZED NAME SERVERS
Blockchain-based DNS is not vaporware
Blockstack, Ethereum Name Service, and Namecoin.
Early Disruptors
BLOCKCHAIN IS NOT THE SILVER BULLET FOR EVERYTHING!
Wrapping up
Questions?
Get My Book!

http://blockchainnigeria.group/pay
About Me
https://web.facebook.com/chimezie.chuta
https://twitter.com/mezie16
https://www.linkedin.com/in/chimeziechuta
https://slides.com/chuta
Coordinator: Blockchain Nigeria User Group
http://blockchainnigeria.group
Founder: StartUPBits.fund | Ayori.io | fragcom.com