Privacy awareness
and control
A presentation by José Aguinaga
Disclaimer
Use content to your own risk, can't be held liable or accountable of the information
Me.
Hacked.
Story time.
Story #1
The disgruntled lover
😱
👻
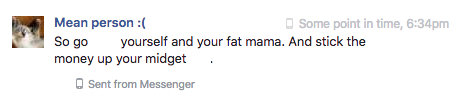
Story #2
The big brother
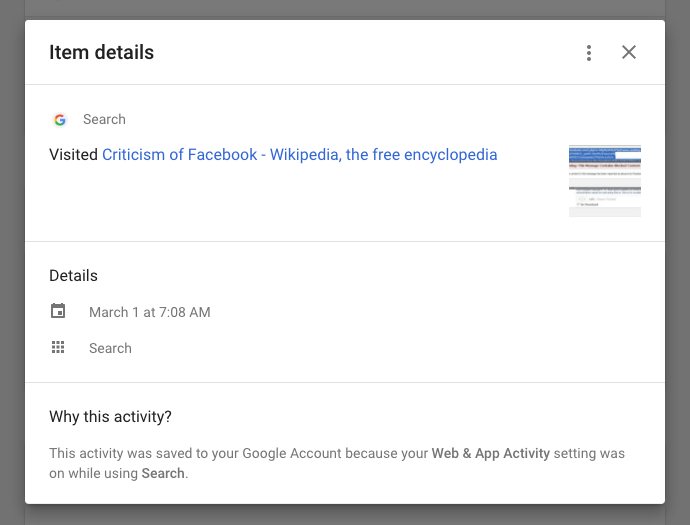
Story #3
The unrequested loan
😂😂😂
Sharing information.
The four stages of information sharing
Stage 1
Unaware and without any control
We are sharing information without being aware it’s happening, and we can not do anything about it.
Stage 2
Aware but without control, or very little
We know we are sharing information, but we can't do anything to stop it.
Stage 3
Control, but without awareness
We are unaware that we are sharing information, but we are given the control of stopping doing so.
Stage 4
Awareness and control
We know what we are sharing, and we can control whether we keep sharing it or not.
We should always aim for stage 4
Understanding types of information.
Three types of information.
Public Information
Anyone can see this information
Your first name, physical appearance, general location, perceived gender.
Private Information
Trusted parties have access to this information
Personal phone, home address, personal documents, age, economical situation, family.
Confidential
Information
Binded by law individuals only
Bank account details, behavioural patterns, economical investments, social security information.
Real problems come when private or confidential information is shared without awareness or without being able to control
Regaining awareness
Our current awareness on privacy matters is way below the threshold companies use to handle your information.
“If you have something that you don't want anyone to know, maybe you shouldn't be doing it in the first place”
Eric Schmidt, Google Chairman CNBC's Interview 2009
“Privacy is no longer a ‘social norm’”
Mark Zuckerberg, Facebook CEO, Crunch Awards Interview 2010
“You already have zero privacy. Get over it”
Scott G. McNealy, CEO of Sun Microsystems Inc, 1999
The reality is that the tools we use abuse in many instances our privacy - if you are not paying for it, you are the product.
“No place to hide”, a book describing the findings of Edward Snowden while working for the NSA, describes the depth of the PRISM program to harvest and interpret people's information through multiple web services.
“Mass surveillance creates a prison in the mind”
Glenn Greenwald, “Why privacy matters” TED Global.
NSA Files Decoded
http://www.theguardian.com/world/interactive/2013/nov/01/snowden-nsa-files-surveillance-revelations-decoded
Regaining
control
1. Lock your screen
Leaving your computer unlocked while not being on your workstation makes it prone to privacy attacks.
This goes the same for your phone. Notifications should not be show on lock screen.
Personal Recommendation: Hot corners + Screen saver
2. Cover your camera
..as well as your screen. Privacy shades on your display stops strangers to snoop confidential information. A camera cover stops potential hackers to take over more than just digital information located in the device.
Personal Recommendation: None
3. Separate users
Use a different user for your everyday activities, and a super admin user for controlling privileged actions on your computer. Were it to be compromised, access would be limited to the malware.
Personal Recommendation: OS setup.
4. Uninstall Adobe Flash
Flash is no longer required for sites like YouTube. For years, it has been the entry point of failure for multiple vulnerabilities while browsing webpages.
Personal Recommendation: HTML5 Video
4. Ditch gmail
Unless you really enjoy their flawless synchronization alongside all their products, using a more private aware provider is a better option.
Personal Recommendation: Proton Mail (Free)
Kolab Now ($)
5. Set up a password strategy
Either use a password manager or your own (ideally an offline local solution), or setup a tabula recta for generating site specific passwords.
Passwords: Long, unique, memorable.
Personal Recommendation: Tabula recta
6. Set up a firewall
The easiest way to ensure traffic doesn't go outside your computer is to setup outbound rules to avoid malware or third party software to ping home.
Personal Recommendation: Little Snitch, Private Eye
7. Disable suggestions
Most autocomplete or autosearch features leak every request inserted in them. A big example is Mac OSX Spotlight
Personal Recommendation: Disable Spotlight
8. Get a VPN
Your traffic should be your concern, and your concern only. Specially while browsing on public wifi.
Additional note: Avoid public wifi when possible.
Personal Recommendation: NordVPN ($), FreeVPN.Ninja (Free)
9. Browse with Firefox
Although Chrome is definitely a great browser, the guys at Mozilla put privacy one of their top concerns.
Learn how to setup: HTTPS Everywhere, Cookie and User Agent buster.
Personal Recommendation: See “Additional Links”
10. Drop US services
After the NSA files were exposed, it has been revealed that major internet services providers located in the US are being used as data sources for mass surveillance.
Additionally, under US Patriotic Act, companies under US soil can be requested to hand over any customer information (e.g. Lavabit)
Personal Recommendation: See https://prism-break.org
Additional links
https://pack.resetthenet.org/
https://securityinabox.org/
https://www.privacytools.io/
https://prism-break.org/en/
https://ssd.eff.org/
FAQ
Why how much information we share is relevant while working in the banking industry?
How you handle your own personal information is a reflection of how you handle others’.

Phone notifications usually contain sensitive information. Anyone that oversees a notification might be able to get information from a client, investor, or third party.
Disable notifications on lock screen to avoid this.
Why should I pay attention to the latest trends in privacy in the world of fintech?
Fintech technologies usually also cover it's share of privacy related operations, which might affect potential customers/investors.
Being aware of most up-to date payments technologies allows to give clients the best insights on investments, latest development in digital currencies and other financial developments.
Enroll to multiple fintech newsletters to spot the latest news in the industry
Why you should always lock your screen if you are not in front of your workstation?
Your workstation contains privileged information that affects the company and/or its clients.
Anyone that has physical access to your computer even for a few seconds is able to retrieve confidential data, infect the network, plug malware into your computer or setup even surveillance software.
See
https://github.com/juuso/keychaindump
What can I do to delete my online persona and “start from scratch”, so to speak?
You can't. You can only start slowly migrating from the services you use everyday.
A mix of technologies is required for setting up full anonymity. From setting untraceable bitcoin wallets, to setting up Tails, the task can be pretty daunting... but possible.
See
https://prism-break.org