Dockercon EU 2015 Recap

Lee Calcote
clouds, containers, networks and their management




Conference Themes
- Usable Security
- Quality
- Production Ready

Security
-
Industry’s First Hardware Signing of Container Images
-
User Namespaces Provides Enhanced Access Control
-
Built-in container security analysis in Docker Hub
Security - Docker Content Trust
(launched at Dockercon SF)
- TUF and Notary enable:
-
Survivable Key Compromise
-
Proof of Origin
-
Protection against untrusted transports.
-

-
integrates the guarantees from The Update Framework (TUF) into Docker using Notary, an open source tool that provides trust over any content.
-
Hardware signing of container images reinforces Docker Content Trust
Hardware Signing of Container Images
Yubico released Yubikey 4 at DockerCon with the goal of increasing the security of Docker images.
A YubiKey is a small hardware device that offers two-factor authentication with a simple touch of a button.
http://blog.docker.com/2015/11/docker-content-trust-yubikey/

Docker Experimental only
notary key generate
notary key list
notary key backup
export DOCKER_CONTENT_TRUST=1
docker pushSecurity - Project Nautilus
Built-in container security analysis in Docker Hub
Project Goals
- Scale up the security posture assessment
- Notify users of new vulnerabilities in existing code proactively
- Provide visibility to end-users on the security posture of images
Security - Project Nautilus
Text
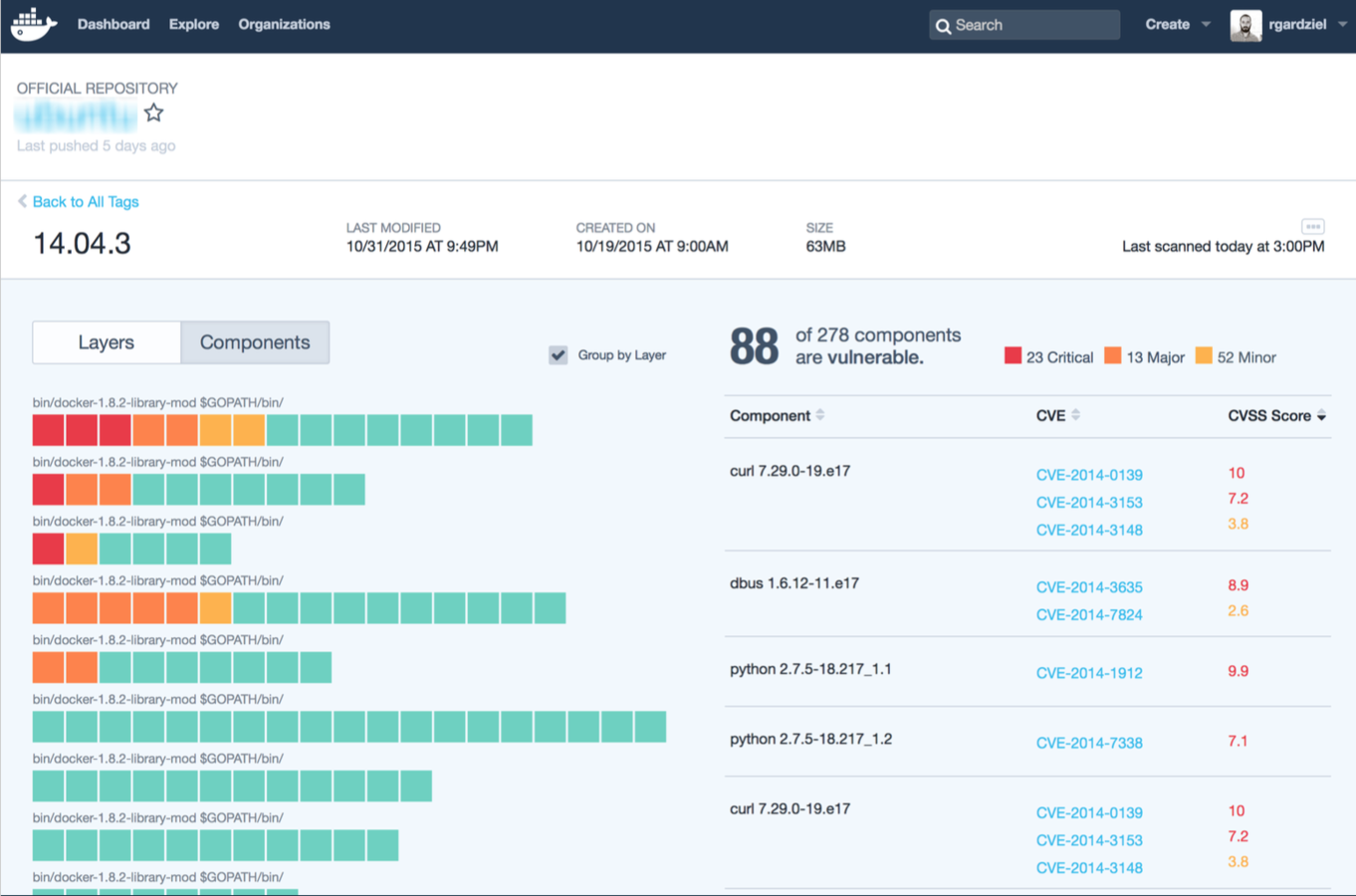
Security - Project Nautilus
-
An image-scanning service that makes it easier to build and consume high-integrity content
-
Steps through a sequence of tests, including:
-
Image security
-
Component inventory/license management
-
Image optimization
-
Basic functional testing
-
- Functions as a source of truth for certification metadata
- Has an extensible backend; may support 3rd-party plugins

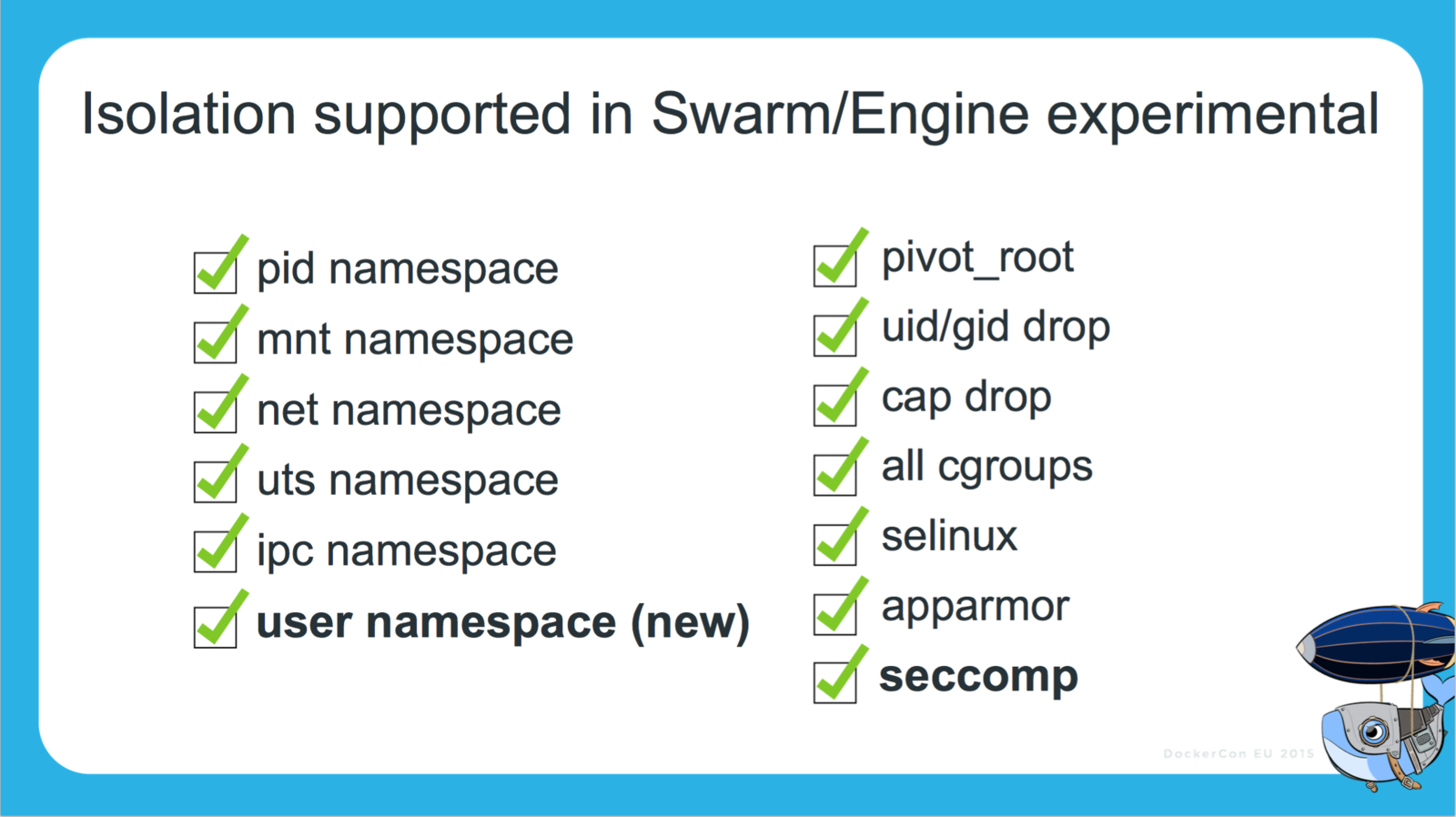
Security - User Namespaces
-
containers themselves don’t have access to root on the host
-
only the Docker daemon does.
-
-
user namespaces gives IT operations the ability to separate container and Docker daemon-level privileges to assign privileges for each container by user group.
-
IT operations will lock down hosts to a restricted group of sysadmins per security best practices
-
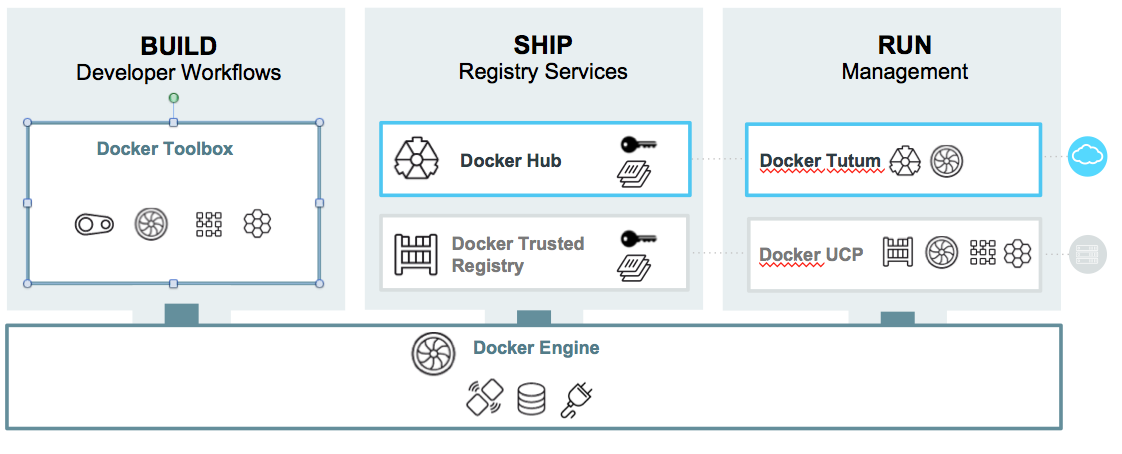
Docker Universal Control Plane
-
"an on-premises solution for deploying and managing Dockerized distributed applications in production on any infrastructure."
-
gives IT ops a single Docker-native management interface for all container on-premise or in cloud
Currently in beta. Sign-up here.
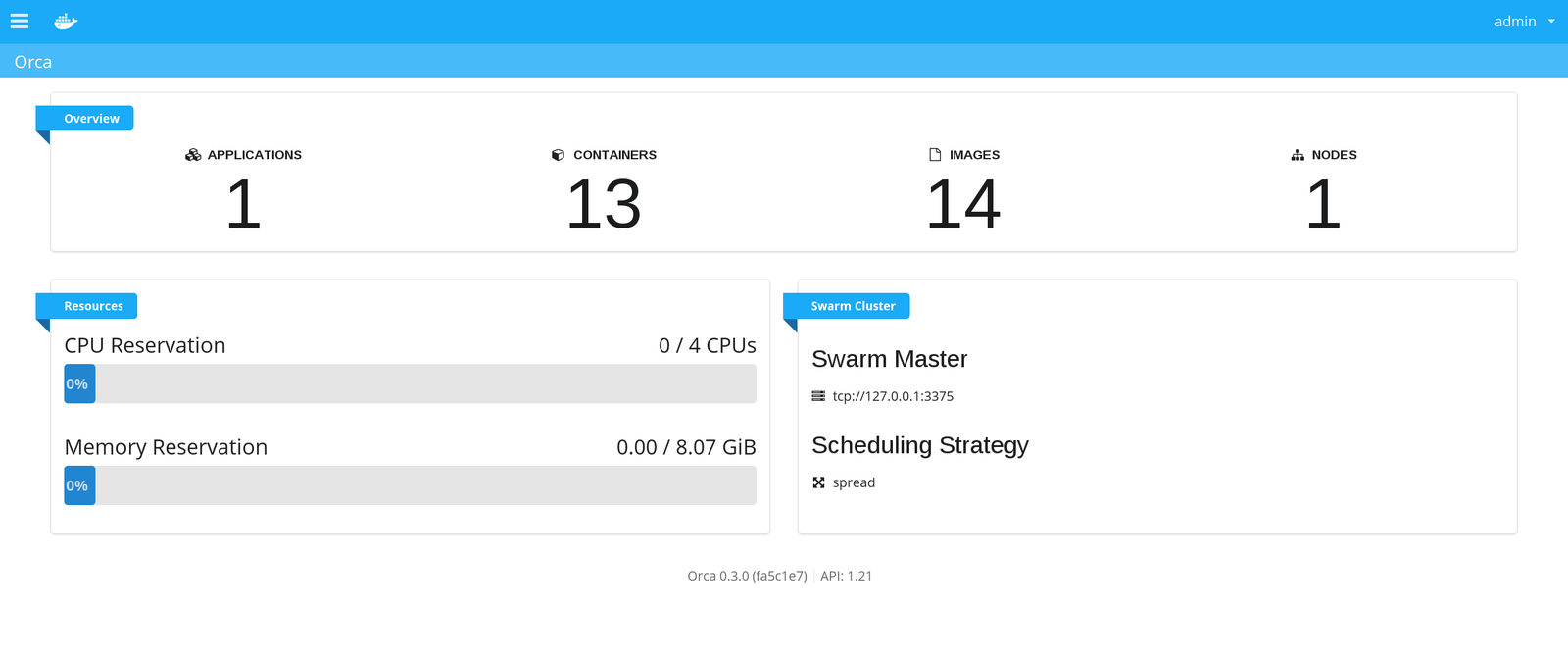
UCP is to containers as vCenter is to VMs
User Management
•LDAP/AD integration with Trusted Registry
•Role based access control (RBAC) to cluster, apps, containers, images
Resource Management
•Visibility into cluster, apps, containers, images, events with intuitive dashboards
•Manage clusters, images, network and volumes
•Manage apps and containers
•Monitoring and logging
Security & Compliance
•On-premise deployment
•Out of the box TLS
•LDAP/AD authentication
•User audit logs
•Out of the box HA
Containers as a Service
Production-Ready Swarm 1.0 Clustering

Scaling Swarm to 1,000 AWS nodes and 50,000 containers!


Multi-host networking
• Docker Engine 1.9 features a new networking system, and Swarm integrates fully with this. Any networks you create in Swarm will seamlessly work across multiple hosts.
Persistent storage
- Engine 1.9 has a new volume management system
- If you use a volume driver that works across multiple hosts (such as Flocker or Ceph) you’ll be able to store persistent data on your Swarm regardless of where containers get scheduled on your cluster.
- Volume management works from the command line interface with plug-ins
- There are drivers available for Blockbridge, Ceph, ClusterHQ, EMC and Portworx.

Production-Ready: Docker Hub Autobuilds
- Docker Hub build system can now be configured to dynamically trigger builds as your team creates new git branches and tags.
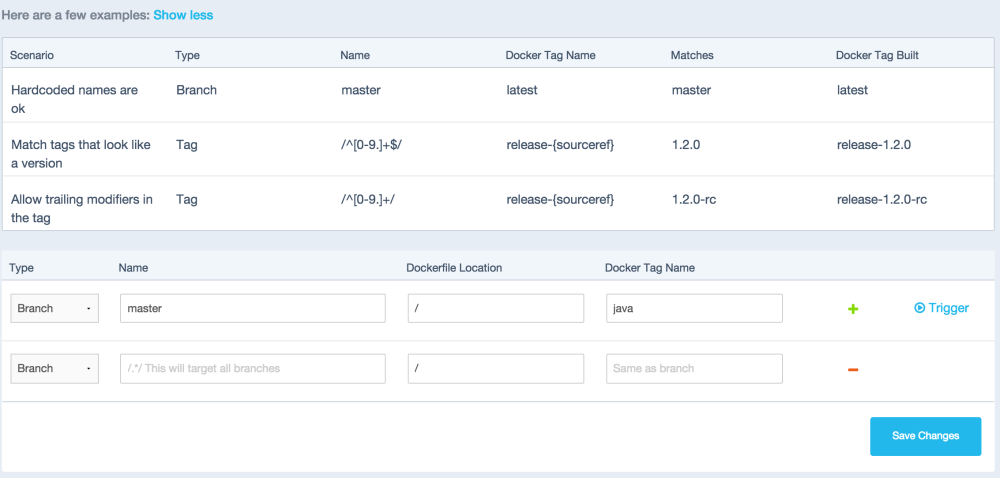
Dynamic Matching
Parallel Builds
- Automated Build system will execute as many builds in parallel as you have private repositories.
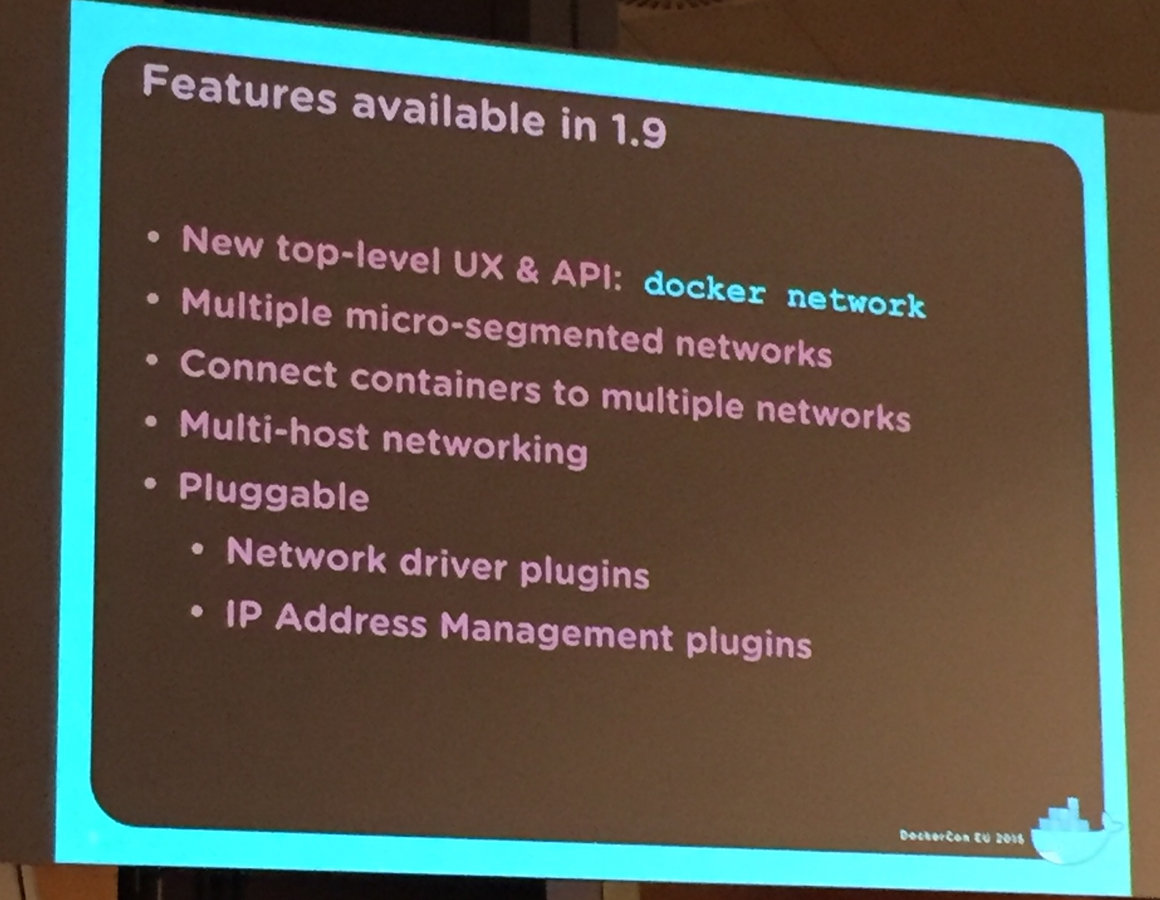
Networking
-
Multi-host networking no longer experimental
-
Out of the box overlay networking in 1.9
-
New 'docker network' command provides management of networks as a top-level object
-
Extensibility through network plugins
-
Already 6 implementations done or under development


Support for DNS to come later
An IP per container... contrasted with an IP per pod in kubernetes
Surgically Segmented Networks
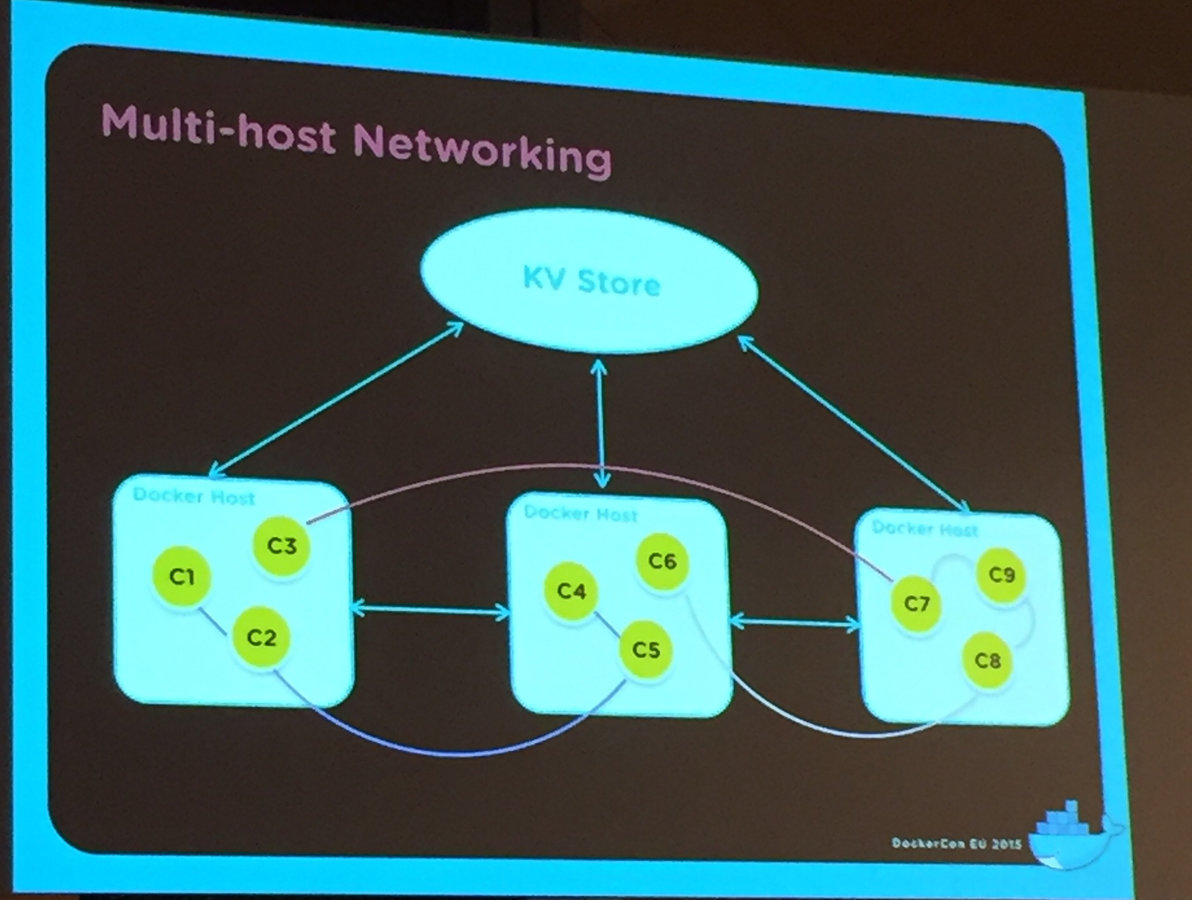
- Network driver plugins available are from Cisco, Microsoft, Midokura, Nuage, Project Calico, VMware, and Weave.
- Default IP addressing remains same, but IPAM is pluggable
VXLAN as the Overlay
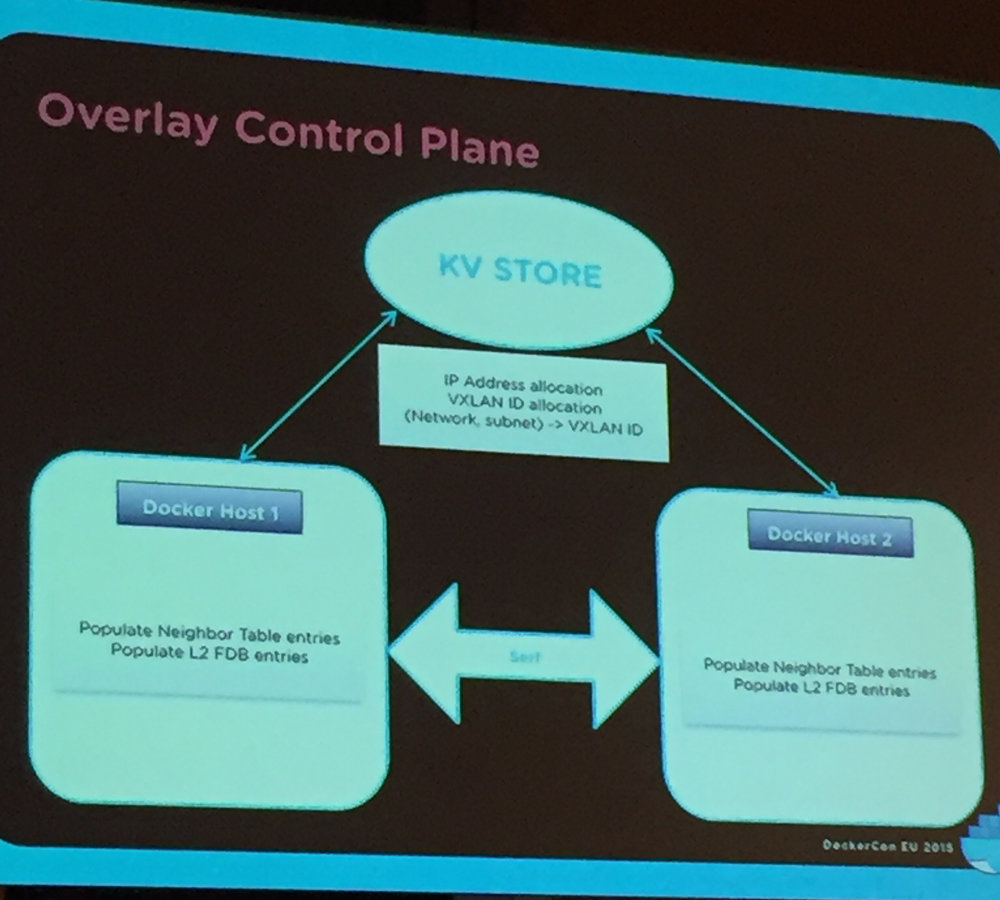
Serf for cluster membership
Resources

Video

Slides
Upcoming Online Events
-
Dec 10th: Introduction to Docker Security
-
Dec 17th: Intro to Docker - Demo and FAQ
-
Feb 11th: Introduction to the Docker Platform