Using Data Integration for Security Testing


Sébastien SALVA and Loukmen REGAINIA*,
ICTSS 2017, Saint-Petersburg
10 October 2017
Introduction
- Software security is essential and should be considered as early as possible
- Security is not a common skill in developement teams
- Developers lack guidance for secure development and security tests
- Developers are provided with a plethora of documents:
-
- Security patterns express a set of reusable solutions to recurrent security problems
- Attack patterns present information about attacks (steps, countermeasures, etc.) in a form comprehensive for both professionals and academicians
Plan
-
Security patterns and ADTrees
-
Data acquisition and integration
-
Method steps
-
Evaluation
-
Conclusions and perspectives
Introduction
- The number of these documentation is continually growing making difficult:
- The choice of the appropriate solution
- Testing the chosen solution
- ->pragmatic approach to guide developers in choosing security solutions and writing concrete test cases
- Main features:
- Security data acquisition in a data-store putting together attacks and patterns
- Generation of Attack Defense Trees
- Generation and the execution of GWT (Given, When, Then) test cases
Security patterns
- Reusable solution to a recurrent security problem
- Use of a security pattern requires an instantiation phase
- Number of patterns is growing (176)
- A security pattern is often related with other patterns
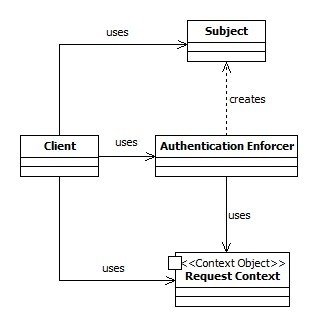
Data Integration
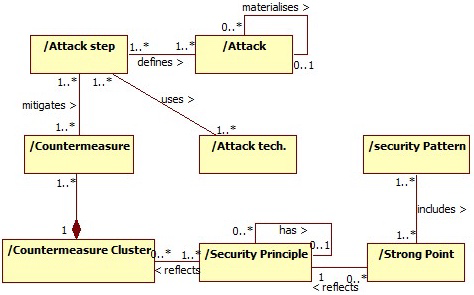
Data acquisition method associating security patterns, attacks, etc. [Crisis17]

- 26 security patterns
- 217 countermeasures (21 clusters)
- 448 attack techniques
- 66 Security principles
- 209 Attack steps
- 215 hierarchically organized attacks
Title Text
Attack Defense Trees
- "Attack Defense Trees ADTrees are graphical representations of possible measures an attacker might take in order to attack a system and the defenses that a defender can employ to protect the system " [Kordy et al. 14]
- An ADTree can be expressed with
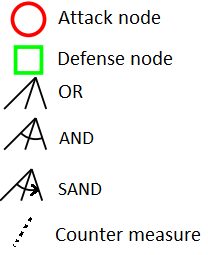
Opponent "o"
Proponent"p"
Algebra (ADTerms):
Data Integration
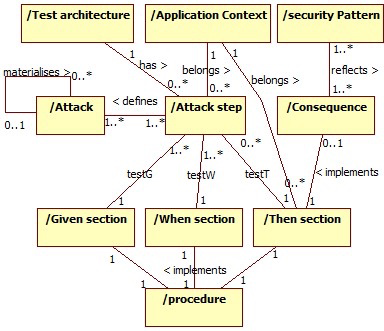
- Application Context
- Prerequisites
- Test architecture
- 43 Patterns consequences
- 209 GWT test Cases
- 632 Generic procedures (Reusable for all applications in a specific context (Web, mobile, etc.))
Meta-model extension for test case generation.
Step 1: Initial ADTree
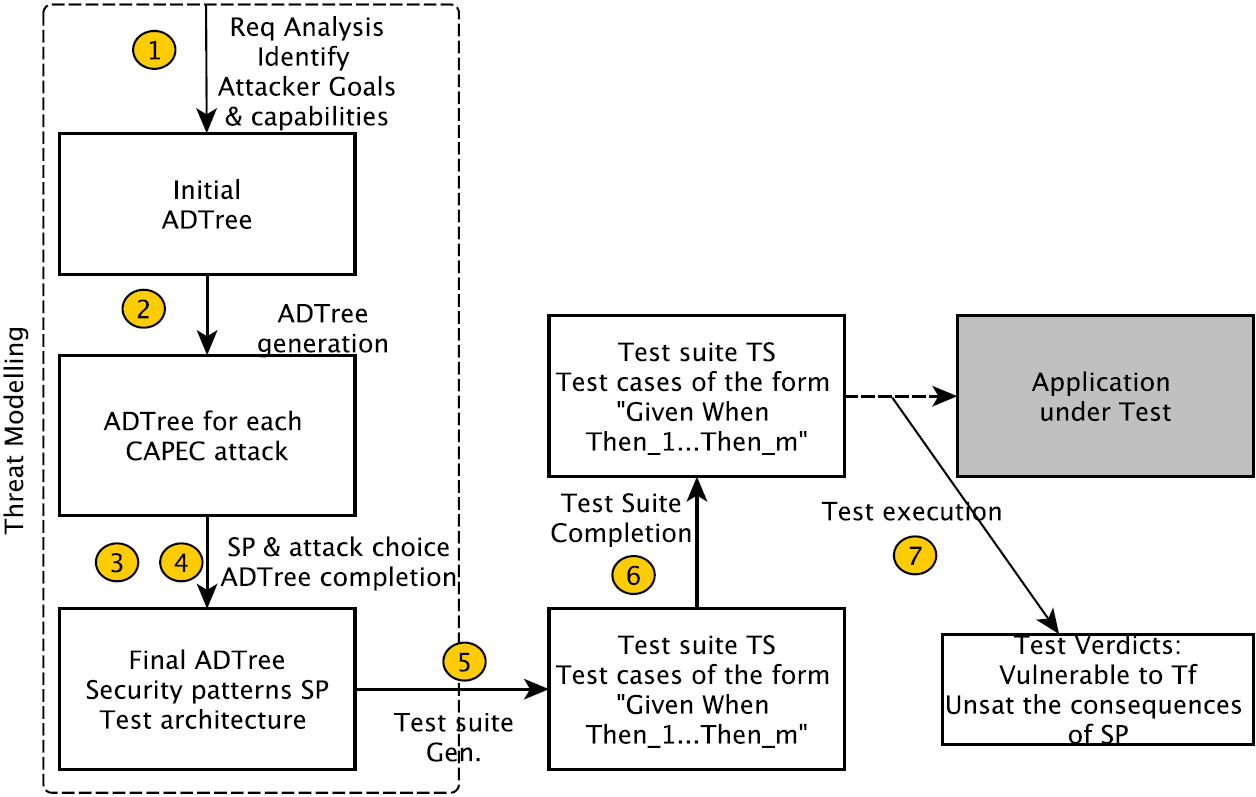
Method steps

Step 2: ADTree Generation
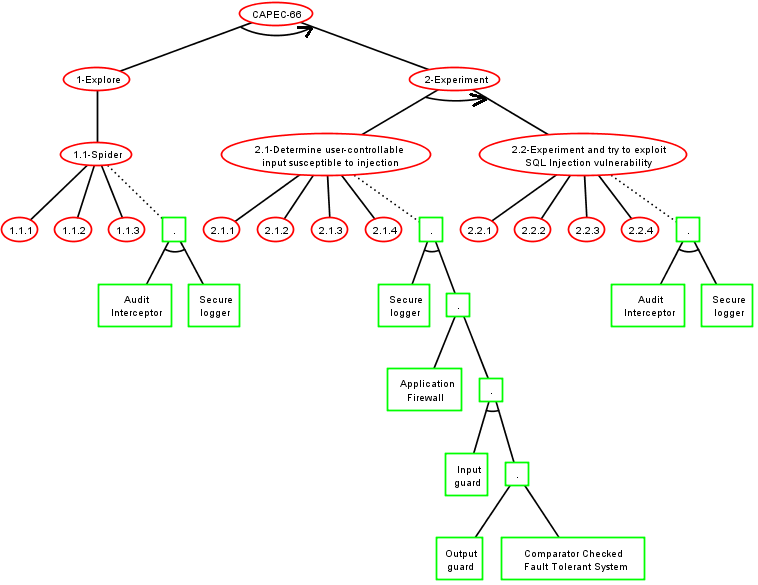

Step 3: Security pattern choice

Basic Attack Defence Step (BADStep)
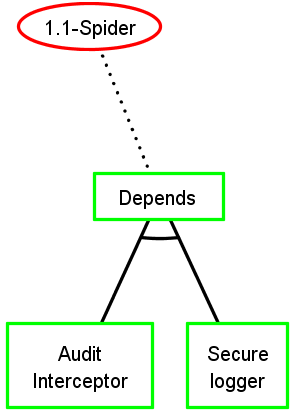
Keep security pattern conjunctions
Step 3: Security pattern choice
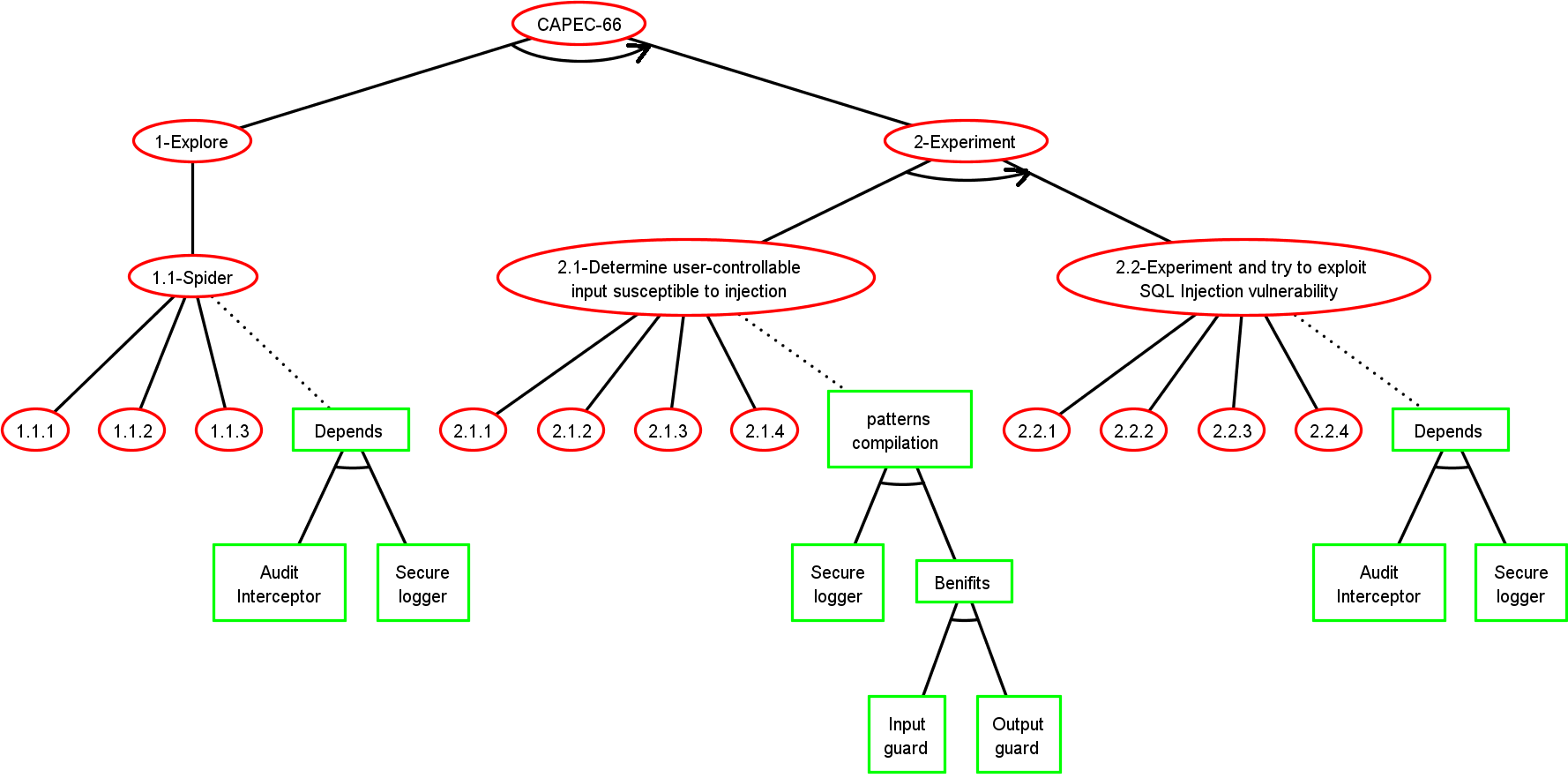

Step 4: Final ADTree generation





Step 5: Test suite generation
Step 5: Test suite generation

BADStep
Test scenario extraction from ADTree using ADTerms
Step 5: Test suite generation
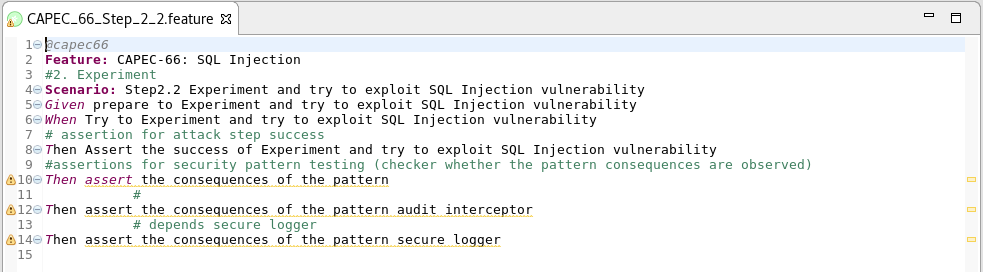
Step 6: Test case completion
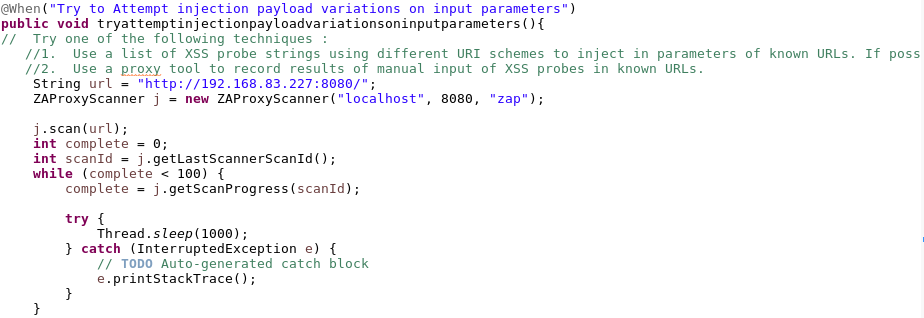


Step 7: Test suite execution
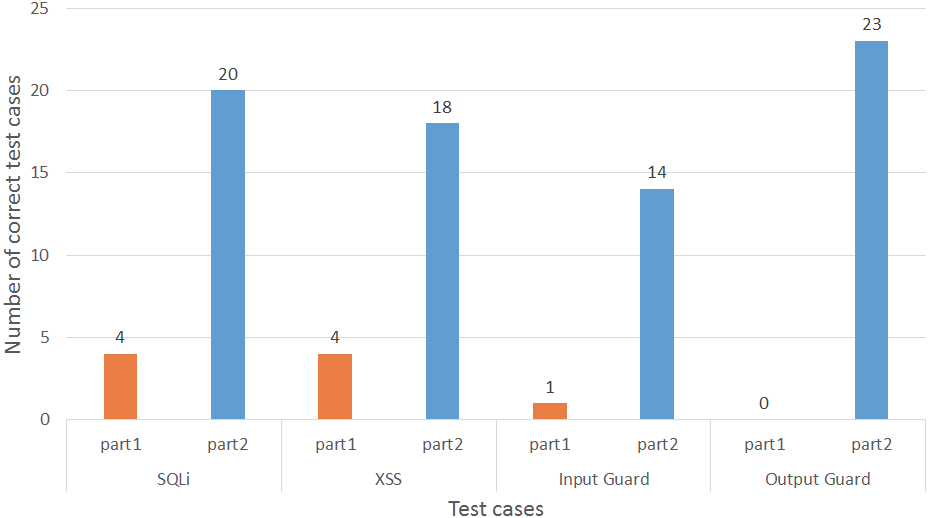
- Test cases are executed and a set of verdicts are obtained:
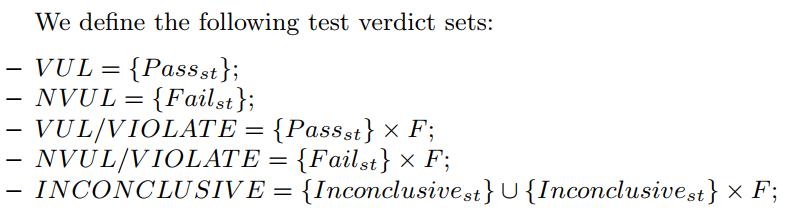
Step 6: Test case completion

+



Step 7: Test suite execution
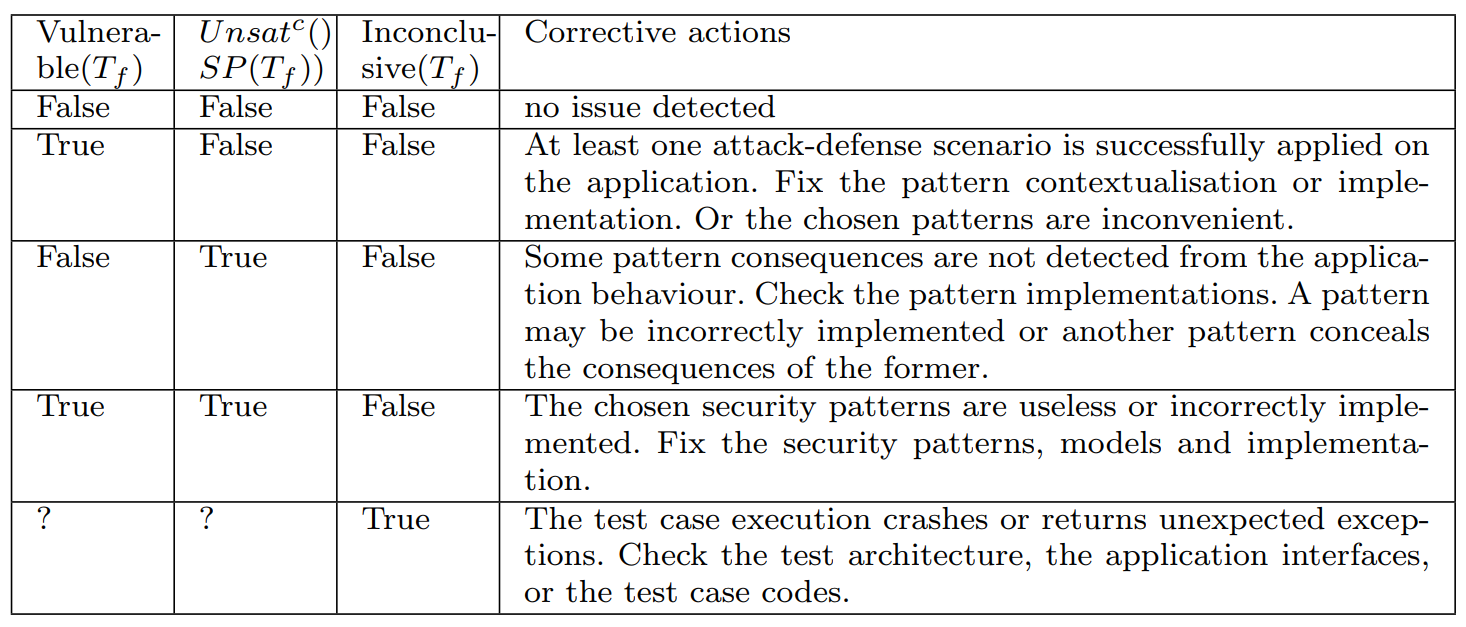
Final Verdicts :
Methodology Evaluation
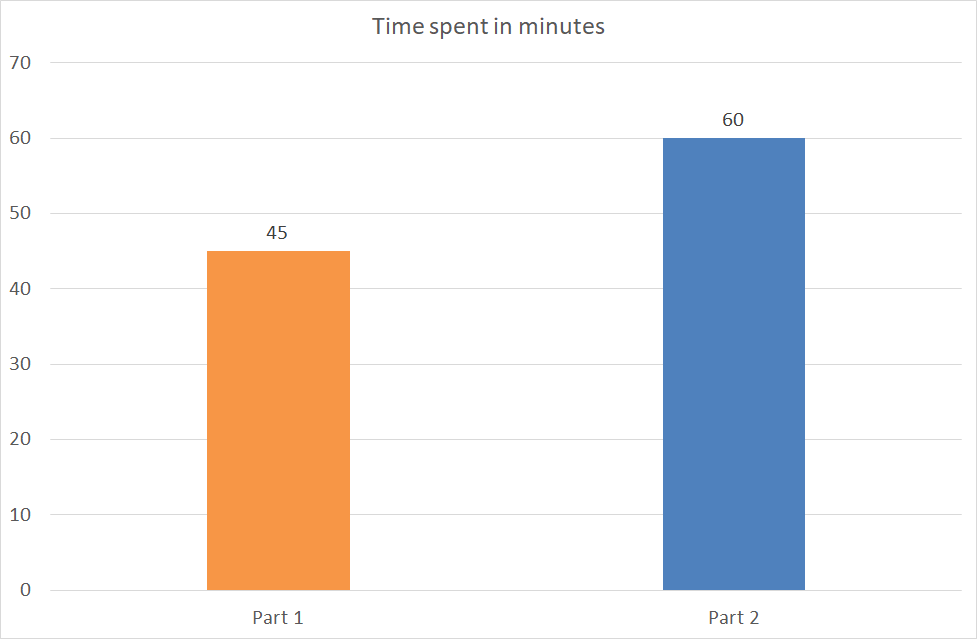
Part 1 (1h30):
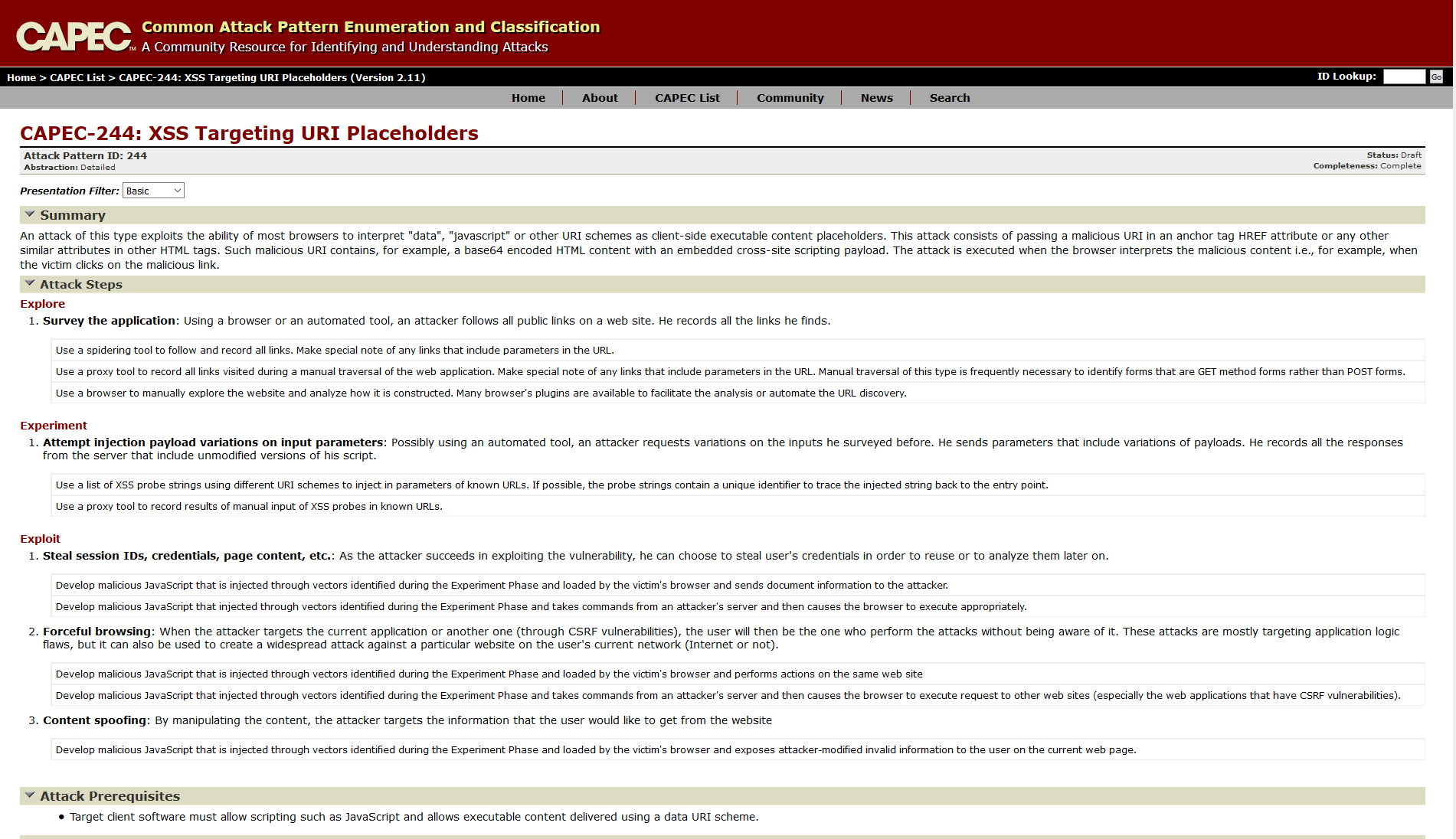
- CAPEC Documentation of SQL injection and XSS attacks
- How to manually perform the attacks
- Security patterns documentation
Part 2(1h30):
- CAPEC Documentation of SQL injection and XSS attacks
- How to manually perform the attacks
- Security patterns documentation
- ADTrees
- GWT test cases
Questions:
- Q7 : Was it easy to write test cases ?
- Q8 : How long did you take for writing tests ?
- Q9 : How confident are you about your tests ?
- Q10 : Provide your test cases ?
Criteria:
- C1: Comprehensibility
- C2: Effectiveness
- C3: Efficiency
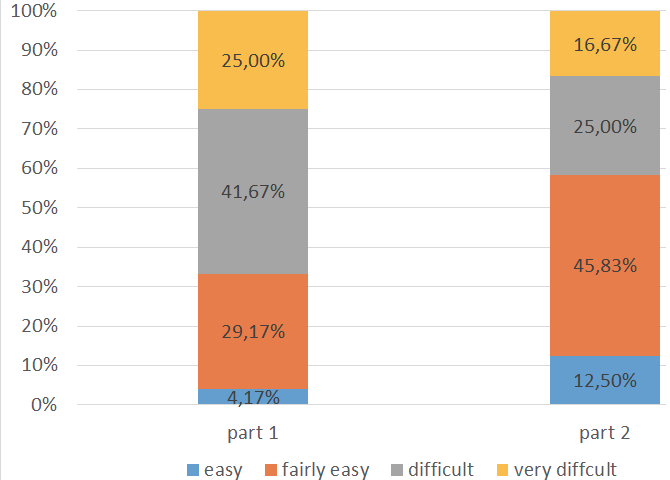
Methodology Evaluation results
- C1: Comprehensibility
Methodology Evaluation results
- C2: Effectiveness
Conclusions
We presented:
- A data-store gathering
- 215 attacks, 209 steps, 388 GWT tests, 632 generic procedures;
- Automated generation of GWT and ADtrees
- Data-Stores and Tools are available in
Perspectives
- Complete the approach with Runtime-verification to test other properties; (Security test+ behavior + pattern properties);
- Collaborating with MITRE-CAPEC to link security patterns with Attack patterns;
Perspectives
- Complete the approach with Runtime-verification to test other properties; (Security test+ behavior + pattern properties);
- LTL Behaviral properties
- SP behaviors
- application traces
- detecting security pattern behavioral occurences

Perspectives
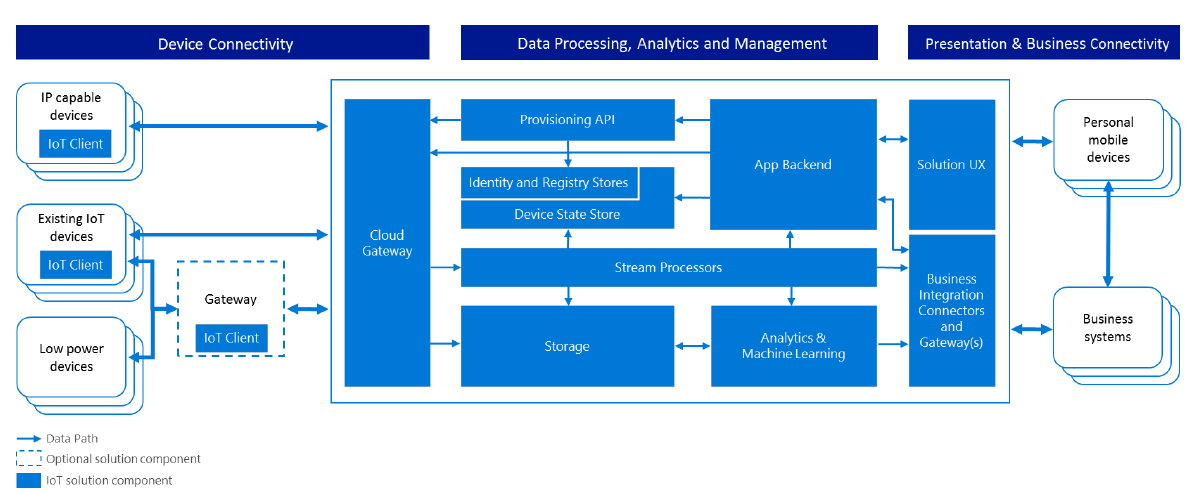
Reference Architecture (Example: IOT azure microsoft)
Perspectives
Reference Architecture (Example: IOT azure microsoft)
Security
Data integration for security reference architecture building
Thank you for your attention

Step 4: Final ADTree generation

Each node of the initial ADTree denoted with attack $$Att \in T$$ is automatically substituted with its ADTree $$T(Att)$$ The final ADTree is denoted $$T_f$$ whose root is the root of $$T$$
Methodology Evaluation results
- C3: Efficiency
Step 5: Test suite generation

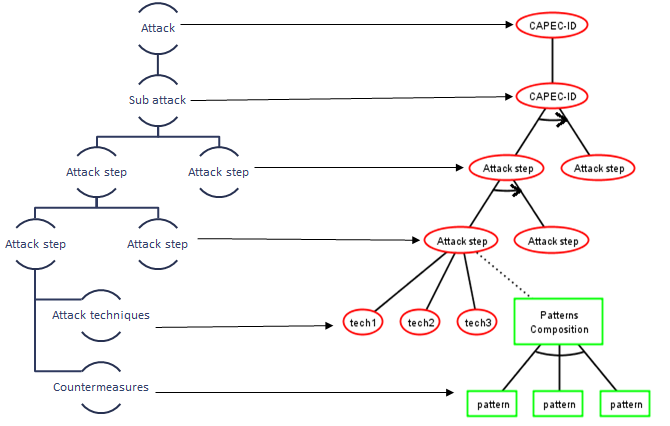
Attack Patterns
- An attack pattern describes:
- Techniques, context, indicators, prerequisits, etc.
- The sequencing of the attack steps
- The potential countermeasures
- CAPEC (Common Attack Pattern Enumeration and Classification) is the main resource of attack patterns :
- The unification of attack descriptions
- A data base of more than 500 detailed attack patterns

Step 2: ADTree Generation

Scenario: Attack x step y
Given: prerequisites
When: Actions
Then: Assertions
-
One Then section: Attack step success;
-
Many Then sections: Presence of security pattern consequence;
Generic Procedure:
Reusable for all applications in a specific context (Web, mobile, etc.) Completed with guidelines :
- Resources required -CAPEC-
- Attack step techniques -CAPEC-
- Outcomes/Indicators -CAPEC-
- Patterns consequences
Step 5: Test suite generation
Attack Defense Trees
- An ADTree is also defined with ADTerms
- An ADTerm, expresses two types of roles (opponent "o") and (proponent "p") in addition to four types of relations