Network Layer
-
RIP
Dr. Alexios Louridas
What are we going to see?
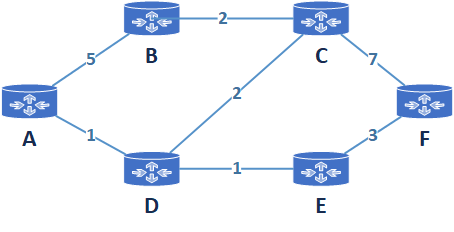
- Routers = {A,B,C,D,E,F}
- Links = {(A,B),(A,D),(B,C),(D,E),(D,C),(C,F),(E,F)}
- Cost of Link (example) = c(A,B) = 5
- Cost can be related to bandwidth, throughput, congestion, delay...
- Cost of Path (A,B,C,F) (example)= c(A,B)+c(B,C)+c(C,F)
Network Graphs
What is the least-cost path between A and F?
Routing algorithms are responsible to answer the question
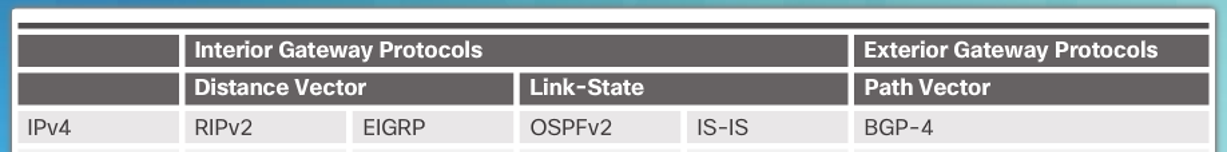
Dynamic Routing Protocol Overview
Routing within autonomous systems (group of networks under a single administration) are referred as interior gateway protocols, whereas routing between autonomous systems are referred as exterior gateway protocols.
RIP protocol was updated to RIPv2 to accommodate growth in the network environment
RIPv2 does not scale to current larger network implementations
Routing Protocols developed to meet the need of larger networks include:
Open Shortest Path First (OSPF)
Intermediate System-to-Intermediate System (IS-IS).
Enhanced IGRP (EIGRP)
Border Gateway Protocol (BGP) is used between Internet service providers (ISPs)
The Bellman-Ford algorithm’s primary principle is that it starts with a single source and calculates the distance to each node. The distance is initially unknown and assumed to be infinite, but as time goes on, the algorithm relaxes those paths by identifying a few shorter paths. Hence it is said that Bellman-Ford is based on “Principle of Relaxation“.
Bellman-Ford equation
cost from neighbour v to destination y
cost to neighbour v
minimum taken over all neighbours v of x

Distance Vector Routing
In Distance Vector Routing, each router periodically shares its knowledge about the entire internet with its neighbours.
-
Sharing knowledge about the entire autonomous system. Each router shares its knowledge about the entire AS with its neighbours. At the outset, a router's knowledge may be sparse. How much it knows , however, is unimportant; it sends whatever it has.
-
Sharing only with neighbours. Each router shares its knowledge about the entire AS with its neighbours. At the outset, a router's knowledge may be sparse. How much it knows , however, is unimportant; it sends whatever it has.
- Sharing at regular intervals. Each router shares its knowledge to its neighbours at fixed intervals, for example, every 30 seconds.
-
Each node constructs a one-dimensional array (a vector) containing the "distances" (costs) to all other nodes and distributes that vector to its immediate neighbours.
-
The starting assumption for distance-vector routing is that each node knows the cost of the link to each of its directly connected neighbours.
-
These costs may be provided when the router is configured by a network manager. A link that is down is assigned an infinite cost.
RIP (Routing Information Protocol)
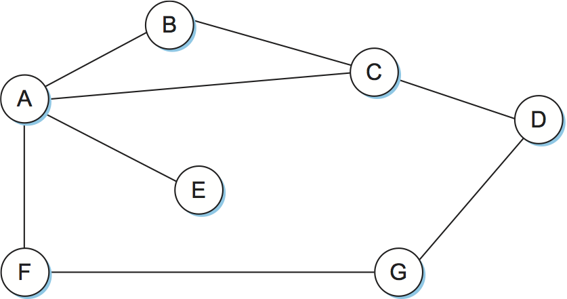
| A | B | C | D | E | F | G | |
|---|---|---|---|---|---|---|---|
| A | 0 | 1 | 1 | Inf | 1 | 1 | Inf |
| B | 1 | 0 | 1 | Inf | Inf | Inf | Inf |
| C | 1 | 1 | 0 | 1 | Inf | Inf | Inf |
| D | Inf | Inf | 1 | 0 | Inf | Inf | 1 |
| E | 1 | Inf | Inf | Inf | 0 | Inf | Inf |
| F | 1 | Inf | Inf | Inf | Inf | 0 | 1 |
| G | Inf | Inf | Inf | 1 | Inf | 1 | 0 |
Initial Distances Stored at Each Node
-
Add one hop to the hop count for each advertised destination.
-
Repeat the following steps for each advertised destination:
-
If (destination not in the routing table)
-
Add the advertised information to the table.
-
-
Else
-
If (next-hop field is the same)
-
Replace entry in the table with the advertised one.
-
-
Else
-
If (advertised hop count smaller than one in the table)
-
Replace entry in the routing table.
-
-
-
-
-
Return
RIP Updating Algorithm

-
Routers send their advertisements every 30 seconds;
-
A router also sends an update message whenever an update from another router causes it to change its routing table.
-
One point of interest is that it supports multiple address families, not just IP. RIP version 2 (RIPv2) also introduced the subnet masks, whereas RIP version 1 worked with the old classful addresses of IP.
-
All link costs are equal to 1, just as in our example. Thus, it always tries to find the minimum hop route. Valid distances are 1 through 15, with 16 representing infinity. This also limits RIP to running on fairly small networks—those with no paths longer than 15 hops.
RIP (Routing Information Protocol)

| A | B | C | D | E | F | G | |
|---|---|---|---|---|---|---|---|
| A | 0 | 1 | 1 | 2 | 1 | 1 | 2 |
| B | 1 | 0 | 1 | 2 | 2 | 2 | 3 |
| C | 1 | 1 | 0 | 1 | 2 | 2 | 2 |
| D | 2 | 2 | 1 | 0 | 3 | 2 | 1 |
| E | 1 | 2 | 2 | 3 | 0 | 2 | 3 |
| F | 1 | 2 | 2 | 2 | 2 | 0 | 1 |
| G | 2 | 3 | 2 | 1 | 3 | 1 | 0 |
Final Distances Stored at Each Node
Two-Node Loop Instability
Distant Vector (DV) Tables can be wrong

Before Failure
| D | HC | NR |
|---|---|---|
| X | 1 | A |
| D | HC | NR |
|---|---|---|
| X | 2 | A |

AftEr Failure
| D | HC | NR |
|---|---|---|
| X | Inf |
| D | HC | NR |
|---|---|---|
| X | 2 | A |

AftEr A received Update from B
| D | HC | NR |
|---|---|---|
| X | 3 | B |
| D | HC | NR |
|---|---|---|
| X | 2 | A |

AftEr B Receives update from A
| D | HC | NR |
|---|---|---|
| X | 3 | B |
| D | HC | NR |
|---|---|---|
| X | 4 | A |

Finally
| D | HC | NR |
|---|---|---|
| X | Inf |
| D | HC | NR |
|---|---|---|
| X | Inf |
Three-Node Loop Instability
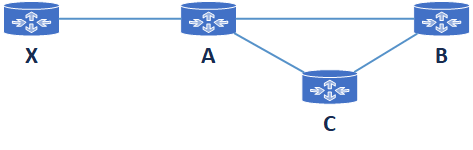
Before Failure
| D | HC | NR |
|---|---|---|
| X | 1 | A |
| D | HC | NR |
|---|---|---|
| X | 2 | A |
| D | HC | NR |
|---|---|---|
| X | 2 | A |

After A send the route to B and C, but the packet to C is lost
| D | HC | NR |
|---|---|---|
| X | Inf |
| D | HC | NR |
|---|---|---|
| X | Inf |
| D | HC | NR |
|---|---|---|
| X | 2 | A |

After C send the route to B
| D | HC | NR |
|---|---|---|
| X | Inf |
| D | HC | NR |
|---|---|---|
| X | 3 | C |
| D | HC | NR |
|---|---|---|
| X | 2 | A |

After B sends the route to A
| D | HC | NR |
|---|---|---|
| X | 4 | B |
| D | HC | NR |
|---|---|---|
| X | 3 | C |
| D | HC | NR |
|---|---|---|
| X | 2 | A |

Solution - Split Horizon
- The split horizon rule prevents routers from advertising a route back to the same neighbour from which they received it.
- Specifically, if a router learns a route from a neighbour, it does not advertise that route back to the same neighbour.
- This avoids loops caused by using the same route in both directions.
-
When a route fails, distance vector protocols spread the news about the route failure by poisoning the route.
-
Route poisoning involves advertising the failed route with a special metric value called Infinity (e.g., RIP defines infinity as 16).
-
Routers consider routes advertised with an infinite metric as failed and avoid using them.
-
This prevents routers from endlessly updating each other with incorrect information.
solution - Route Poisoning


Solution - Holddown Timers
-
Holddown timers prevent rapid route changes due to transient issues.
-
When a router detects a route failure, it starts a timer.
-
During this time, the router ignores any updates related to the failed route unless it receives an update from the router of that downed link.
-
After the timer expires, the router can update its routing table.
-
RIPv2 has some Link State characteristics
-
RIPv2 supports classless routing
-
RIPv2 supports Authentication
Main differences
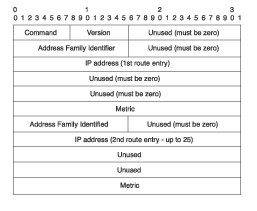
| Header Field | Description |
|---|---|
| Version | Specifies the RIP version used. It is set to 2 for RIPv2 and set to 1 for RIPv1. |
| AFI | Specifies the address family used. RIP is designed to carry routing information for several different protocols. Each entry has an AFI to indicate the type of address specified. The AFI for IP is 2. The AFI is set to 0xFFF for the first entry to indicate that the remainder of the entry contains authentication information |
| Route Tag | Provides a method for distinguishing between internal routes (learned by RIP) and external routes (learned from other protocols). You can add this optional attribute during the redistribution of routing protocols. |
| IP Address | Specifies the IP address (network) of the destination. |
RIP Header Fields
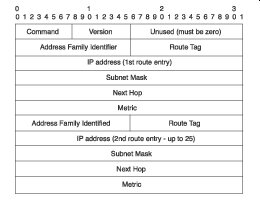
| Header Field | Description |
|---|---|
| Subnet Mask | Contains the subnet mask for the destination. If this field is 0, no subnet mask has been specified for the entry. |
| Next Hop | Indicates the IP address of the next hop where packets are sent to reach the destination |
| Metric | Indicates how many router hops to reach the destination. The metric is between 1 and 15 for a valid route or 16 for an unreachable or infinite route. |
| As in Version 1, the router permits up to 25 occurrences of the last five 32-bit words (20 bytes) for up to 25 routes per RIP message. If the AFI specifies an authenticated message, the router can specify only 24 routing-table entries. The updates are sent to the multicast address of 224.0.0.9 |
RIP HEADER FIELDS
1
RIPv1 broadcasts a Request packet
2
RIPv2 multicasts a Request packet at IP address 224.0.0.9
3
Neighbours receive request and send a response packet with their routing table
4
When a response is received their routing table is processed.
RIP Timers
update
The update timer specifies the frequency of the periodic broadcasts. By default, the update timer is set to 30 seconds. Each route has a timeout value associated with it. The timeout gets reset every time the router receives a routing update containing the route.
invalid
When the timeout value expires, the route is marked as unreachable because it is marked invalid. The router marks the route invalid by setting the metric to 16. The route is retained in the routing table. By default, the invalid timer is 180 seconds, or six updates periods (30 x 6 = 180).
flush
A route entry marked as invalid is retained in the routing table until the flush timer expires. By default, the flush timer is 240 seconds, which is 60 seconds longer than the invalid timer.
Holddown / Suppress
For infinite loop avoidance RIP now implements an additional timer, the holddown timer. The holddown timer stabilizes routes by setting an allowed time for which routing information regarding different paths is suppressed. After the metric for a route entry changes, the router accepts no updates for the route until the holddown timer expires. By default, the holddown timer is 180 seconds.

Summary - Final Thoughts
-
Distance-vector protocol.
-
Uses UDP port 520.
-
Classless protocol (support for CIDR).
-
Supports VLSMs.
-
Metric is router hop count.
-
Maximum hop count is 15; infinite (unreachable) routes have a metric of 16.
-
Periodic route updates sent every 30 seconds to multicast address 224.0.0.9.
-
25 routes per RIP message (24 if you use authentication).
-
Supports authentication.
-
Implements split horizon with poison reverse.
-
Implements triggered updates.
-
Subnet mask included in route entry.
-
Administrative distance for RIPv2 is 120.
-
Used in small, flat networks or at the edge of larger networks.
Router# show ip rip database
// Displays all the routes known by RIP
// even routes that are not currently in
// the routing table
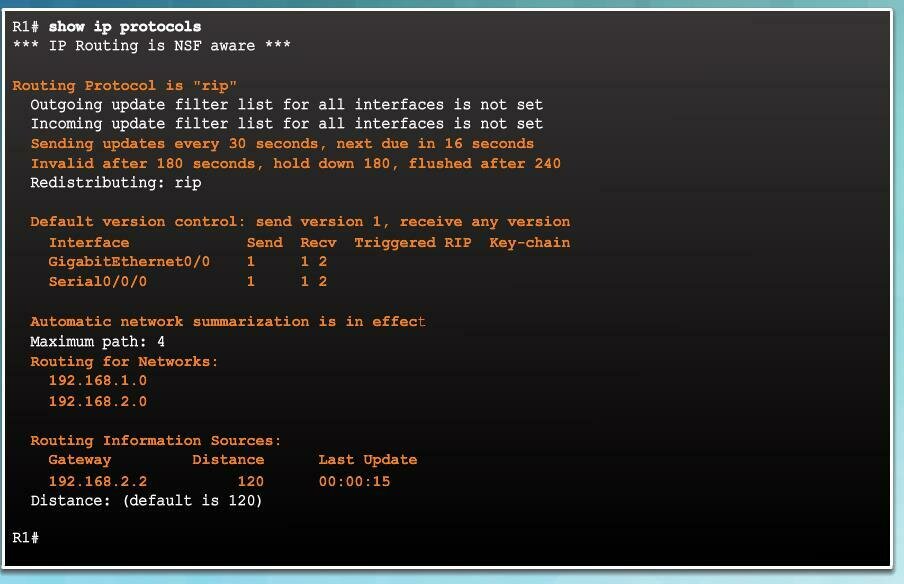
Router# show ip protocols
// Displays detailed information about
// dynamic routing processes currently running
// on the router
Router# show ip route 172.16.3.0
// Displays detailed information about the route 172.16.3.0Rip Configuration
Rip Configuration
Router# show ip route 172.16.3.0
// Displays detailed information about the route 172.16.3.0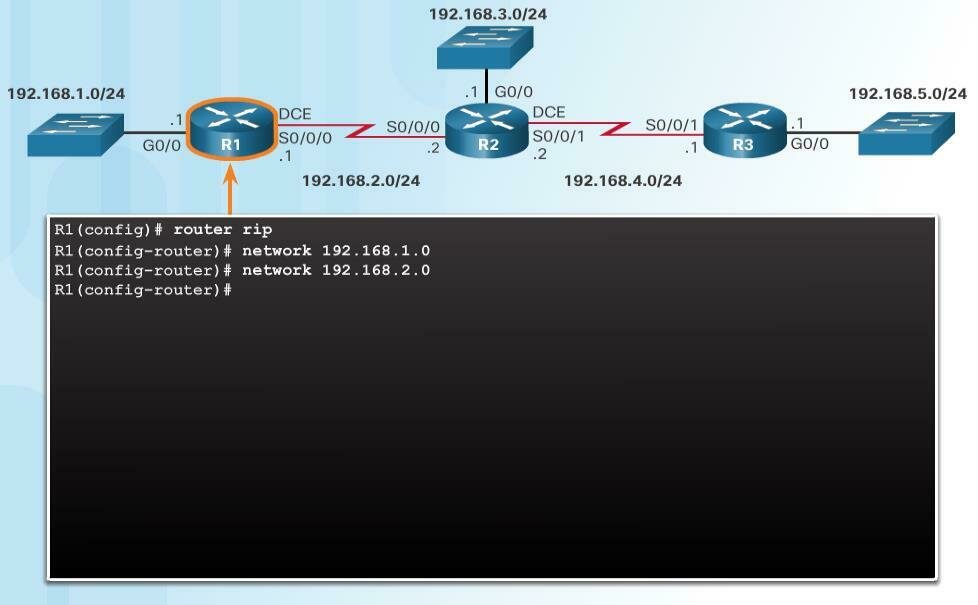
Enabling RIP
The network network address router configuration mode command:
- Enables RIP on all interfaces that belong to a specific network
- Advertises the network in RIP routing updates sent to other routers every 30 seconds.
Rip Configuration
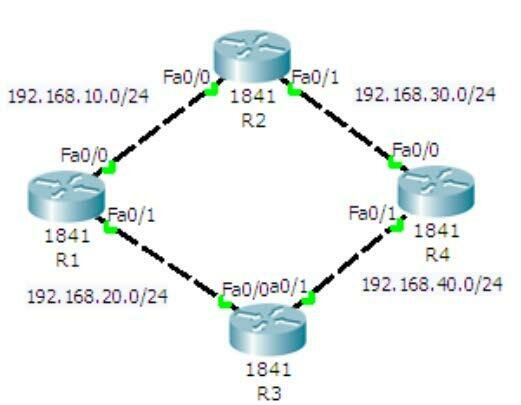
R1(config)#router rip
R1(config-router)#network 192.168.10.0
R1(config-router)#network 192.168.20.0-
Do a simple design of 4 routers with two Hosts connected at each end. Find a suitable topology
-
Do another network with 16 nodes to prove that RIP fails at 16 hops
Tasks
