Zero Knowledge Proofs and Blockchain Privacy
Instructor: Andreas Park
Transaction Processing
- Self-custody of assets
- Access to financial infrastructure
- Conceptually non-custodial services
- Value management layer = common resource
- Platform approach to commerce
Revisit: What makes blockchain-based finance different from TradFi?
{
{
features
consequences
assets ownership by accounts
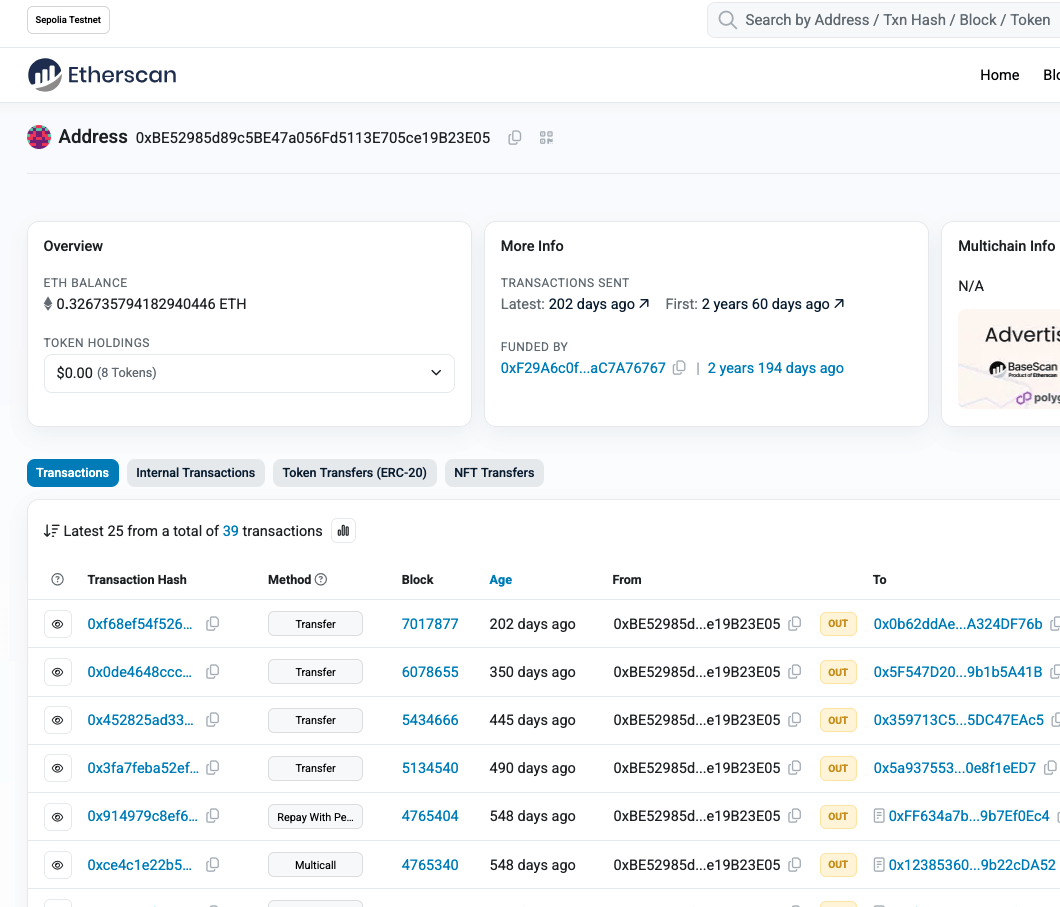
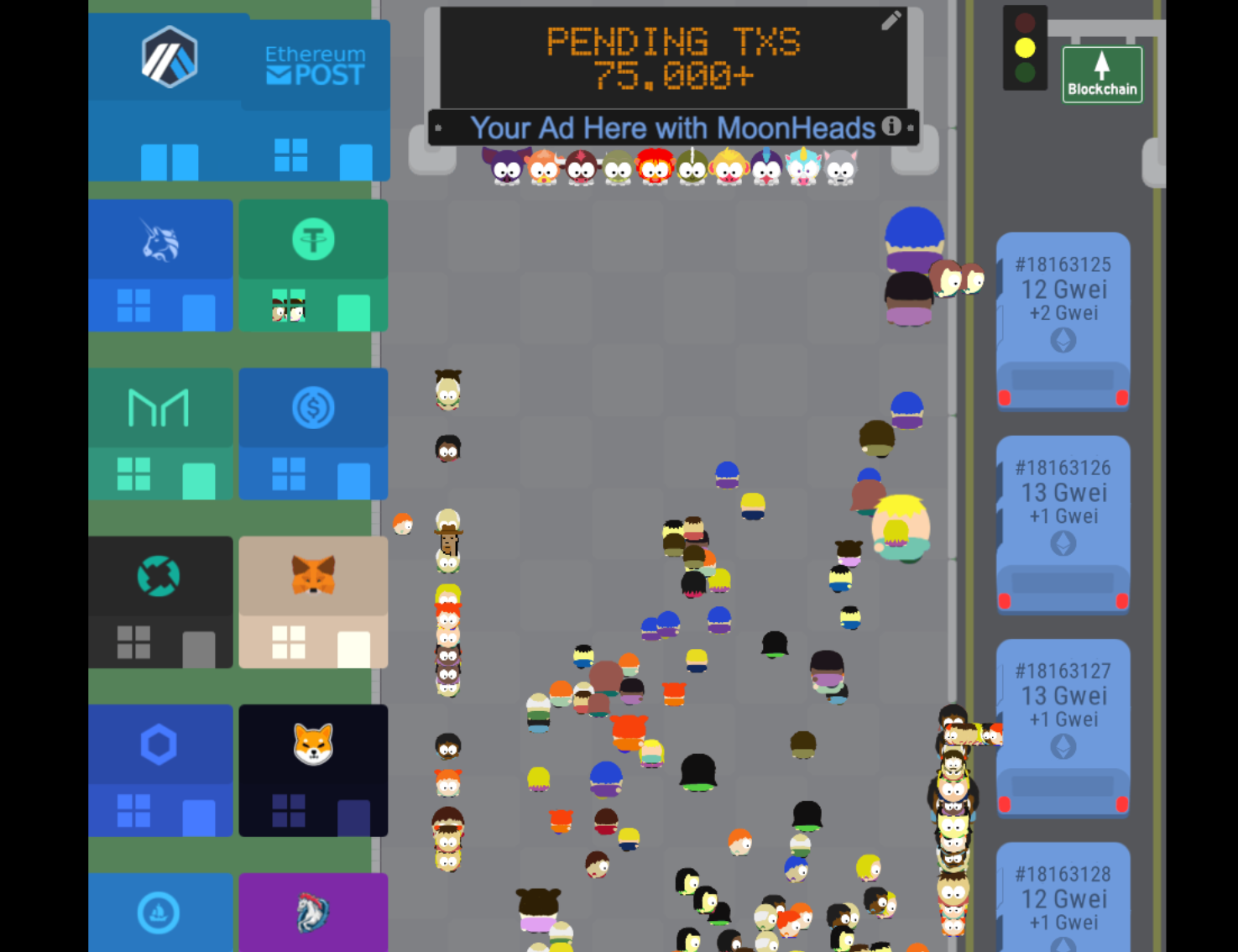
Transaction Visualization
transactions
decentralized applications
tokens
The
"Mem-Pool"
Key Insight: there is no built-in privacy!

Blockchain has no privacy
Example:
- you buy something online using a stablecoin and ship it to your home address
- the merchant can now
- link your name and address to your account
- knows everything you ever did with this account
- knows everything you ever will do with this account
- can use data analytics to map you and other contact
- intrinsic feature of public blockchains is that information gets stored by public addresses.
- logic of smart contracts is visible to all
- => firms have need of secrecy, individuals have rights to privacy
Root problem
Solutions
- large numbers of wallets/addresses
- coinjoin
- ring signatures
-
zero knowledge proofs
Blockchain has no privacy
So no privacy. So why is everyone concerned about money laundering and crime?
But KYC for AML/CFT is all abound
- criminals are real and they are using blockchains
- tax evasion, ransomware payments, ransom payments (real kidnappings!)
- for tokenized assets firms need to know
- their shareholders for communications
- avoid politically exposed persons
How can we have compliance that keeps criminals out?
Basic FINTRAC/FINCEN Rules for Money Services Businesses
- Basic rule: for any virtual currency transaction money services businesses need to verify and record the identity of the person involved
- Transactions over $10,000 need to be reported
- lots of smaller rules surrounding suspicious activties
\(\Rightarrow\) the rules are "tight"
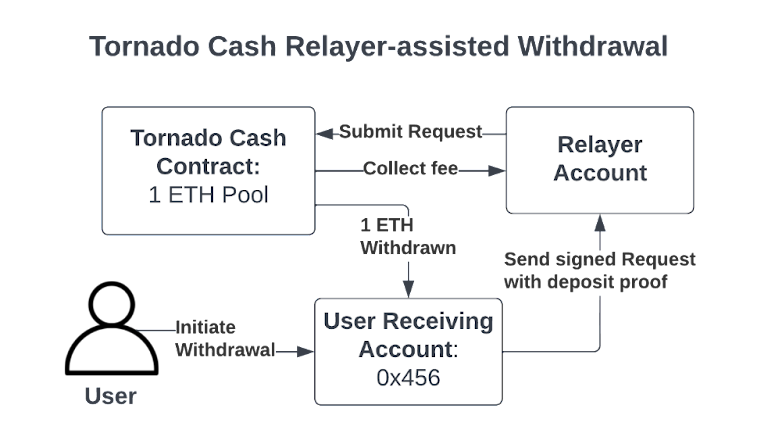
Tornado cash: a privacy Solution
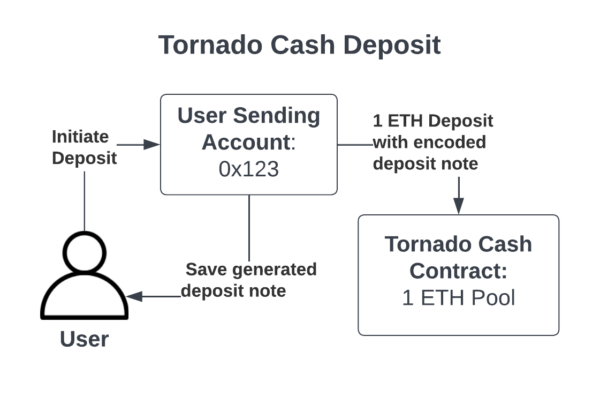
Banned addresses (usually by OFAC order)
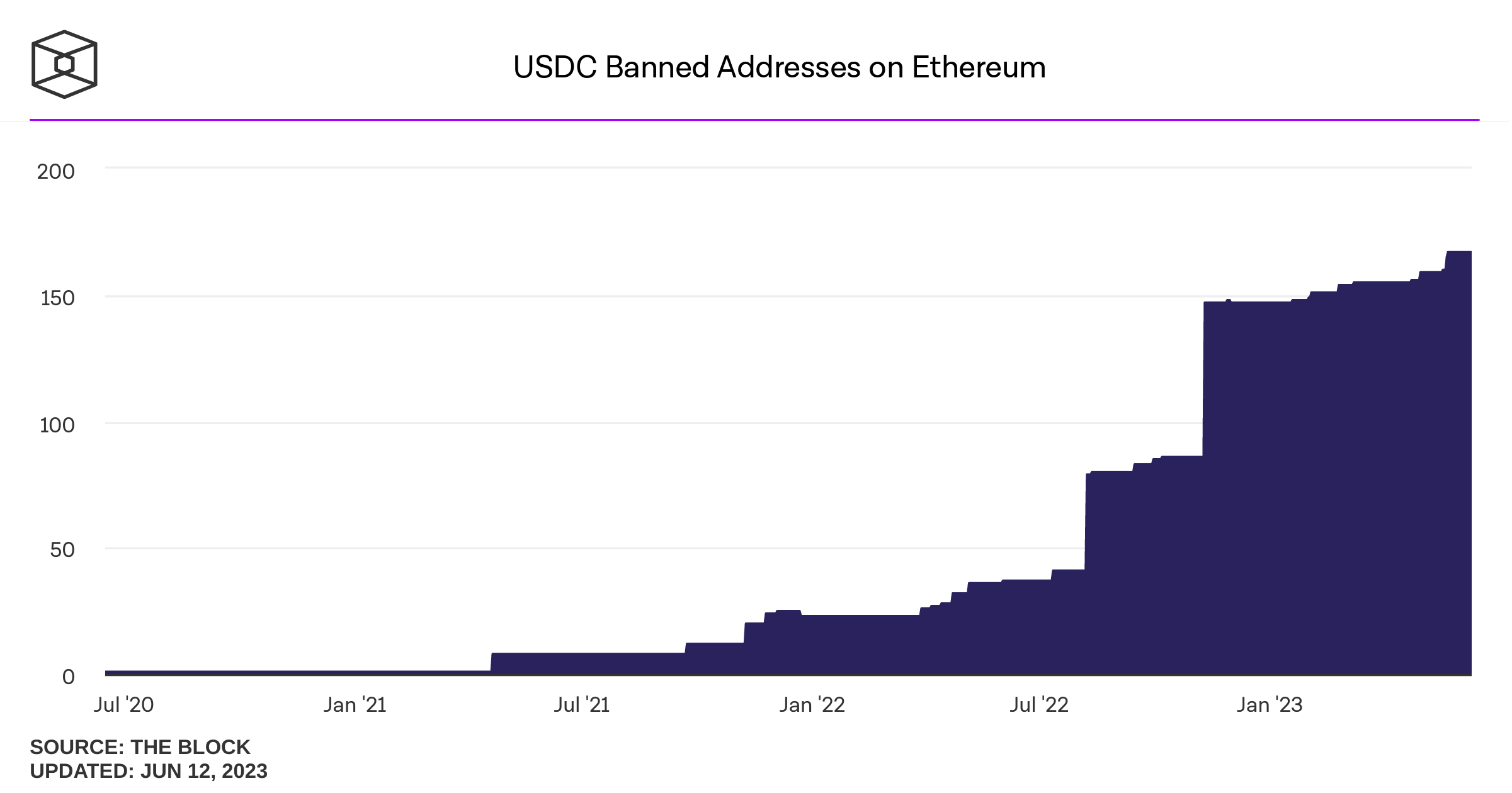
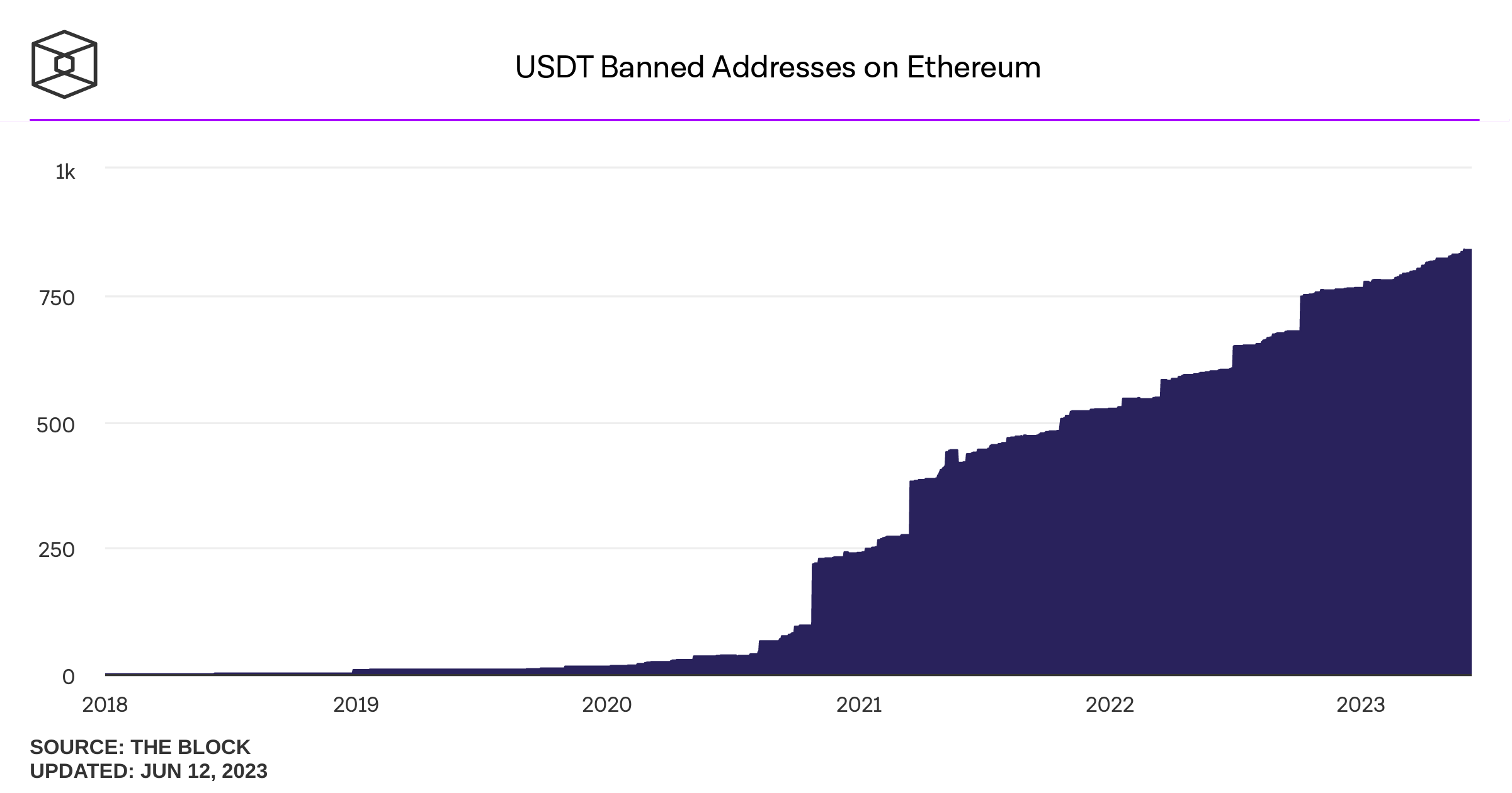
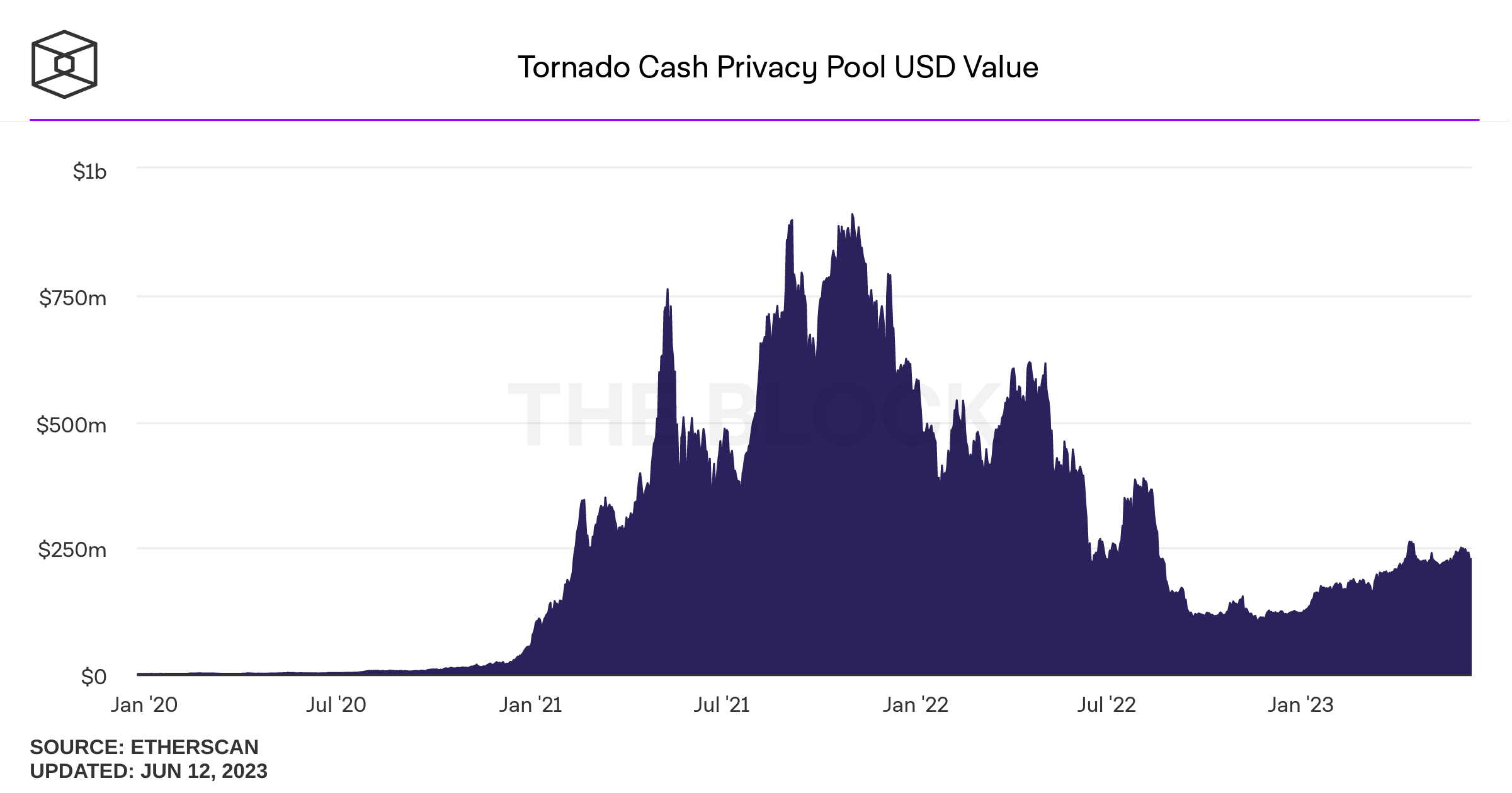
August 8, 2022: OFAC sanctions Tornado Cash
The Common View
The Reality
- no evidence that Hamas has received significant volumes of crypto donations.
- full understanding of blockchain analysis and context is needed
- Elliptic: Wall Street Journal [must] correct misinterpretations of the level of crypto fundraising by Hamas.
- in discussions with Senator Warren to ensure parties have a proper appreciation of the complexities and nuances of analyzing these wallets.
Zero Knowledge Proofs
Basic Premise
A mechanism that proves to one party (the VERIFIER) that another party (the PROVER) possesses some knowledge, without revealing the knowledge itself or any other information that can be used to re-construct it
This is a probabilistic statement not a math proof


I was born between 1976 and 2000
Range Proofs
Examples
I am an EU citizen
Set Membership
Formal Technology:
- STARK = Scalable Transparent Argument of Knowledge (Eli Ben-Sasson, Iddo Bentov, Yinon Horesh, and Michael Riabzev 2018)
- SNARK = Succinct Non-interactive Argument of Knowledge (Nir Bitansky, Ran Canetti, Alessandro Chiesa, and Eran Tromer 2012)
WHY?



Computational
Integrity
I performed the computation
you asked me to
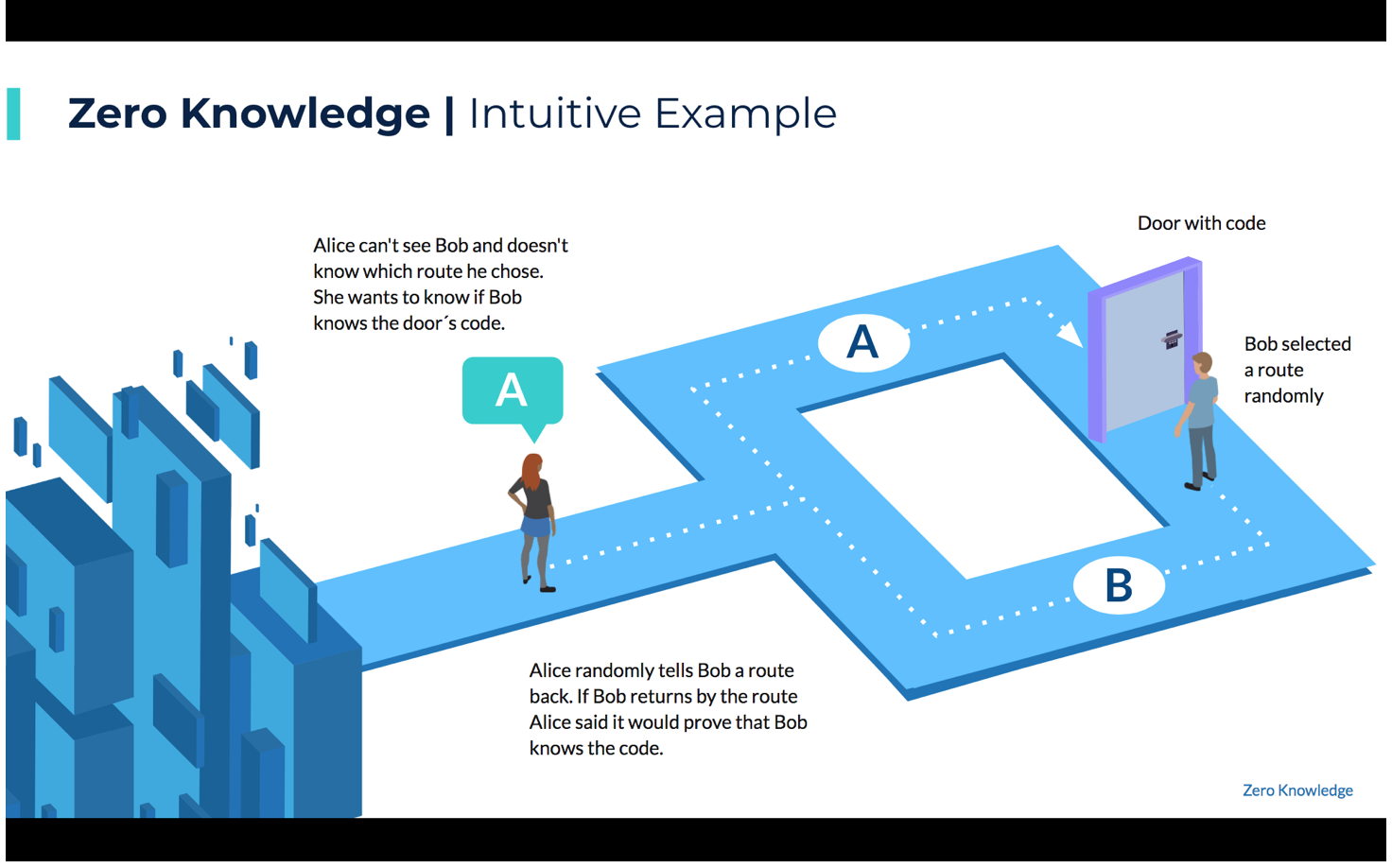
Toy example #1 for a zero knowledge proof

Verifier Victor
Prover Peggy
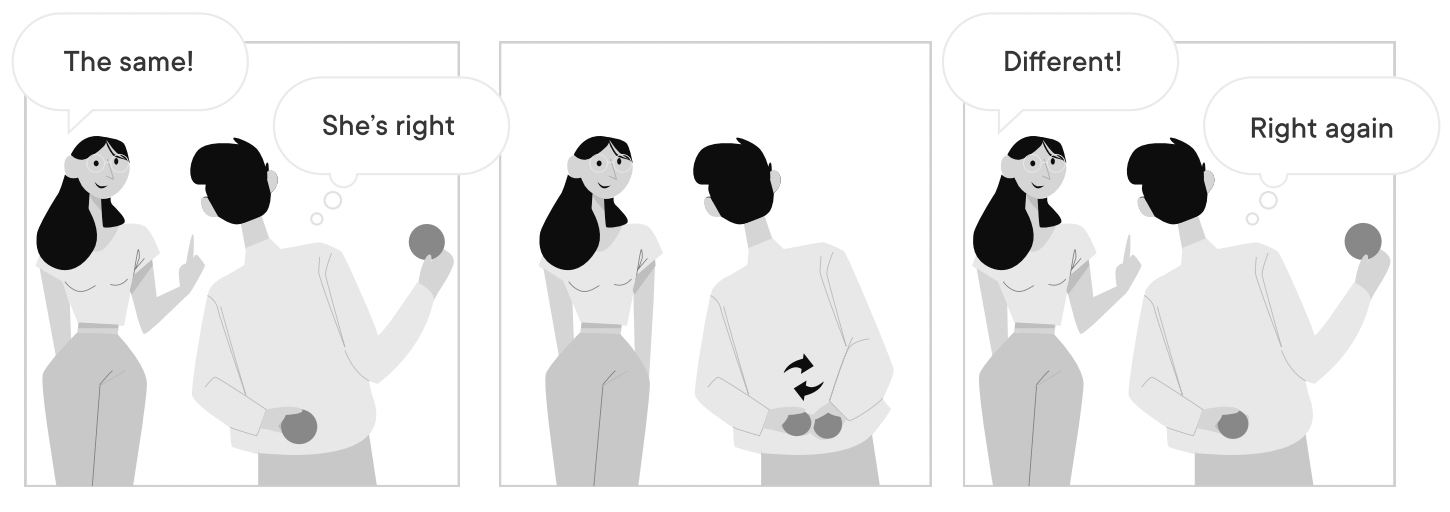
How? Toy Example 2
Toy example #2 for a zero knowledge proof
- Note: these examples are interactive.
- SNARK = Succinct Non-interactive Argument of Knowledge
Privacy solutions
Current Compliance Solutions
| Approach | Objective | Problem |
|---|---|---|
| deposit limits at off-ramps | block illicit funds | blocks some bad actors but frustrates regular people |
| sanctioned addresses | block bad actors | whack a mole |
| data analytics | risk scoring | significant type I and type II errors |
| view-only access | let regulators see transactions | relies on cooperation, including from criminals |
| association sets | proof of innocence | slow to detect, concern about criminals sneaking in |
| KYC of addresses/whitelisting | verify identify of account | no privacy towards KYC provider _ honeypots |
| selective de-anonymization | proof of innocence with stick | currently works only in L2s/rollups |
Decentralized Compliance Networks
Underlying Idea
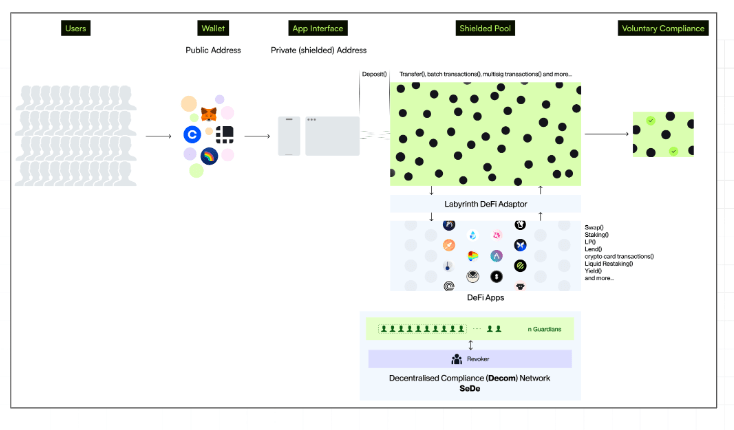
- user onboards with public address
- performs compliance checks etc
- obtains private address(es)
- does business privately
Compliance violation occurs
-
Users:
-
Choose their revokers.
-
Users have full control over their privacy.
-
-
Revokers:
-
Initiate requests for de-anonymization based on suspicious activity.
-
Must post verifiable public requests to trigger the process, ensuring transparency.
-
Can be entities like Chainalysis, TRM Labs, or other trusted individuals decided through the public governance portal.
-
-
Guardians:
-
Vote to approve or deny the de-anonymization request.
-
Operate with a threshold mechanism (e.g., 6 of 10 must agree to proceed).
-
Guardians cannot see the transaction details themselves. Only Revoker can see it after receiving threshold permission from Guardians.
-
Economic Research on Privacy
Economic Research on Privacy
"Privacy-Enhanced Payment Systems", Capponi, Lee, Zhu, 2025, https://papers.ssrn.com/sol3/papers.cfm?abstract_id=5136803
- Multidimensional approach to privacy:
- Identity privacy – are user identities connected to account(s)?
- Transaction privacy – is tx history auditable?
- Modeling a payment system environment:
- Operator selects rules governing privacy-enhancements
- → Irrevocable commitments ex-ante (e.g. smart contract)
- Users (good and bad) create and use accounts for various reasons
- Enforcer attempts to trace TXs back to users
Economic Research on Privacy
"Privacy-Enhanced Payment Systems", Capponi, Lee, Zhu, 2025, https://papers.ssrn.com/sol3/papers.cfm?abstract_id=5136803
- Multidimensional approach to privacy:
- Identity privacy – are user identities connected to account(s)?
- Transaction privacy – is tx history auditable?
- Modeling a payment system environment:
- Operator selects rules governing privacy-enhancements
- → Irrevocable commitments ex-ante (e.g. smart contract)
- Users (good and bad) create and use accounts for various reasons
- Enforcer attempts to trace TXs back to users
Model Sketch
- Two types of privacy
- identity (on/off)
- transaction (trace/no-trace)
- Good users
- suffer utility loss when traced
- Bad users
- benefit if not traced, lose when traced
- Enforcer
- Chooses tracing probability (not possible with private identity)
- System designer:
- chooses system to maximize welfare (utility of bad guys is negative for welfare)
Model Sketch
- Two types of privacy
- identity (on/off)
- transaction (trace/no-trace)
- Good users
- suffer utility loss when traced
- Bad users
- benefit if not traced, lose when traced
- Enforcer
- Chooses tracing probability (idea: can pick out bad transactions (fraud etc))
- chooses system to maximize welfare (utility of bad guys is negative for welfare)
Result Sketch
- With identity privacy, tracing cannot reasonably occur
- tracing decision rule as a function of transaction size is complex (assuming bad guys don't "innovate")
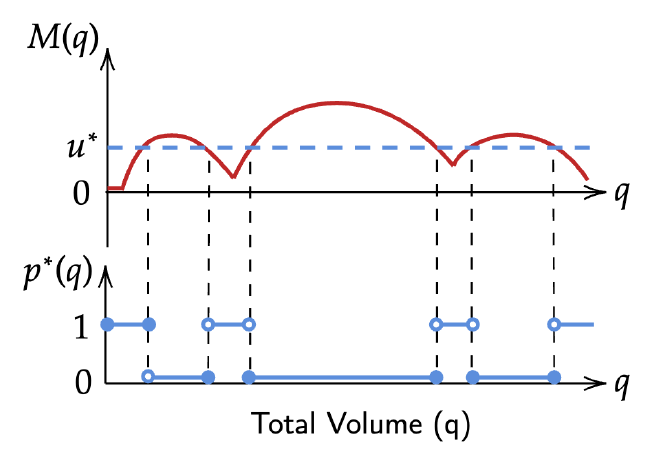
trace
don't trace
Result Sketch when bad guys innovate
- tracing decision rule as a function of transaction size is simple
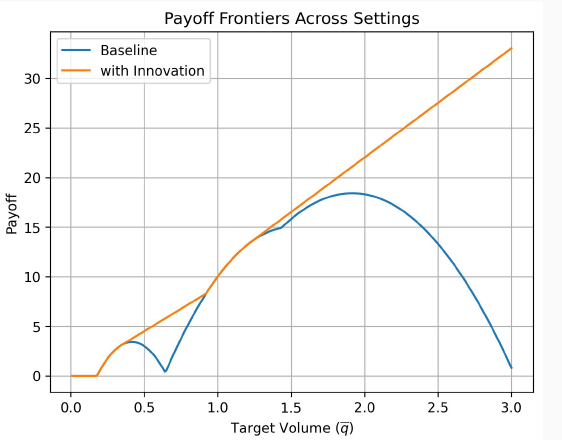
trace
don't trace
Pecking order
identity privacy
transaction privacy
on
off
on
off
|
|
|
|---|---|
|
|


proposed by model
legacy finance
blockchain
blockchain with Tornado Cash
- public blockchains vs legacy?
- depends on enforcement
- weak enforcement is bad
- strong enforcement is too
- Result. Public blockchain is socially better than legacy systems under intermediate enforcement capabilities