BOB 2017, Feb 24th
Benjamin Kampmann, gnunicorn.org
Privacy-first
Data Types
watch live at
tinyurl.com/privacy-first-data-types
👋 Hello

Benjamin Kampmann
Developer, Architect, Educator, Writer
Freelance, FLOSS
@gnunicornBen
gnunicorn.org
imagine

https://icsmap.shodan.io/























by Pia Guerra
Root Problem
centralised Data Warehousing




forum.safedev.org
Domain Name Service
XMPP
Bittorrent (with DTH)
Freenet
the SAFE Network
Overview
the SAFE network
A decentralized privacy-first open source data storage and communications network that provides a secure, efficient and no-cost infrastructure for app development.

Peer-to-peer Data Storage

Built-in Data Retentation

Mathematical Deduplication

Encrypted by Default


Self-Auth Registration
Infrastructure for
decentributed App
(aka truly anonymous)

the SAFE Network
From the Data Perspective


For details on the Consensus System, see
Global Key-Value-Store
key + type -> value
sha256("ben") + 1 -> AccountInfo
sha256("ben") + 2 -> ImmutableData("ben")
sha256("ben") + 15001 -> MData
Data Types
- Authentication
- Immutable data
- Mutable data*
- Currency
Immutable Data
A chunk of data, stored at the address of sha256(data)
Content Addressing
Unified Resource Location:
http://forum.safedev.net/test/someting protocol :// physical location / path within
Unified Resource Identifier:
safe://4e1243bd22c66e76c2ba9eddc1f91394e57f9f83
magnet:?xt=urn:sha1:4e1243bd22c66e76c2ba9eddc1f91394e57f9f83&dn
Deduplication
Self-encryption
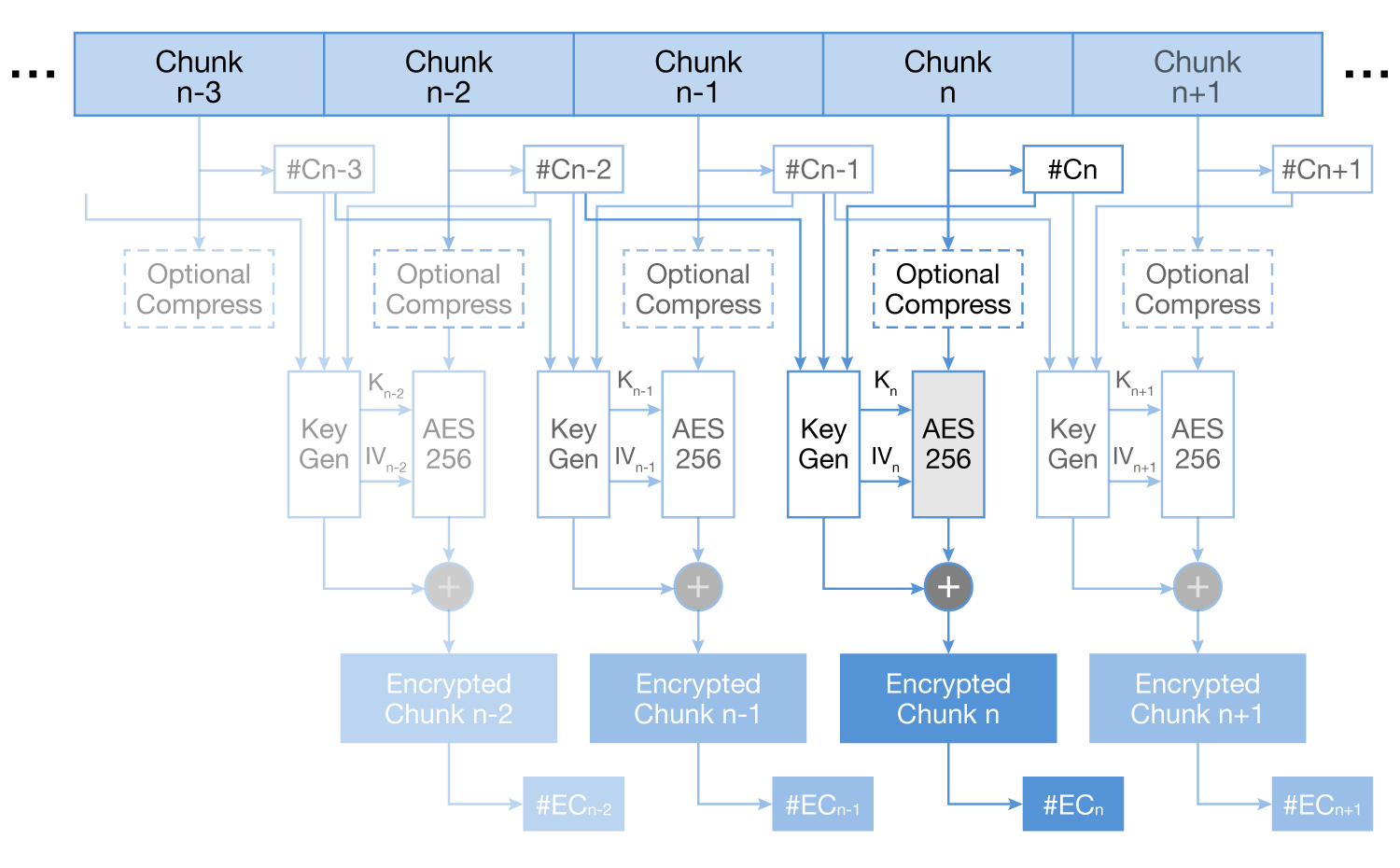
Self-encryption
💾
🔪
📄
📄
📄
📄
🔐
🎁
🔐
🎁
🔐
🎁

🔑
Data Map
order in which they need
to be put together again
Immutable Data
+ Self-encryption 🔑
- encrypted
- public & private
- deduplicated
- content addressed
Mutable Data
pub struct MutableData { name: XorName, tag: u64, data: BTreeMap<Vec<u8>, Value>, permissions: BTreeMap<User, PermissionSet>, version: u64, owners: BTreeSet<PublicKey>, }
pub struct MutableData { name: XorName, tag: u64, data: BTreeMap<Vec<u8>, Value>, permissions: BTreeMap<User, PermissionSet>, version: u64, owners: BTreeSet<PublicKey>, }
essentially just HashMap, too
Mutable Data
CRYPTO
How make it private?
pub struct MDataInfo { pub name: XorName, pub type_tag: u64, /// Key to encrypt/decrypt the content. /// and the nonce to be used for keys pub enc_info: Option<(secretbox::Key, Option<secretbox::Nonce>)>, }
pub struct MDataInfo { pub name: XorName, pub type_tag: u64, /// Key to encrypt/decrypt the content. /// and the nonce to be used for keys pub enc_info: Option<(secretbox::Key, Option<secretbox::Nonce>)>, }
💻
🔑

📅
shared access
pub struct MutableData { name: XorName, tag: u64, data: BTreeMap<Vec<u8>, Value>, permissions: BTreeMap<User, PermissionSet>, version: u64, owners: BTreeSet<PublicKey>, }
pub struct MutableData { name: XorName, tag: u64, data: BTreeMap<Vec<u8>, Value>, permissions: BTreeMap<User, PermissionSet>, version: u64, owners: BTreeSet<PublicKey>, }
pub struct MutableData { name: XorName, tag: u64, data: BTreeMap<Vec<u8>, Value>, permissions: BTreeMap<User, PermissionSet>, version: u64, owners: BTreeSet<PublicKey>, }
pub enum User {
Anyone,
Key(PublicKey),
}
pub struct PermissionSet {
insert: Option<bool>,
update: Option<bool>,
delete: Option<bool>,
manage_permissions: Option<bool>,
}
Mutable Data
+ MData Info 🔑
- encrypted
- public and private
- HashMap
- with shared access
Examples
default containers
"_documents"
"_downloads"
"_music"
"_videos"
"_public"
"_pictures"
privateRandomMData()
...
=> ser(privMDataInfo)
📱
😀
access "_pictures" to 'insert' ?
MData
add access "$Key" to 'insert'!
share
🔐

Public Names
"DNS" - domain lookup

with a "service" oriented approach




app.mutableData.newRandomPrivate(consts.TAG_TYPE_WWW)
.then((serviceMdata) => serviceMdata.quickSetup()
.then(() => {
const nfs = serviceMdata.emulateAs('NFS');
return nfs.create(content)
.then((file) => nfs.insert('/index.html', file))
.then(() => {
const dnsName = sha256Hash.digest(domain);
return app.mutableData.newPublic(dnsName, consts.TAG_TYPE_DNS)
.then((dnsData) => serviceMdata.serialise()
.then((serial) => dnsData.quickSetup({'www': serial})
));
});app.mutableData.newRandomPrivate(consts.TAG_TYPE_WWW)
.then((serviceMdata) => serviceMdata.quickSetup()
.then(() => {
const nfs = serviceMdata.emulateAs('NFS');
return nfs.create(content)
.then((file) => nfs.insert('/index.html', file))
.then(() => {
const dnsName = sha256Hash.digest(domain);
return app.mutableData.newPublic(dnsName, consts.TAG_TYPE_DNS)
.then((dnsData) => serviceMdata.serialise()
.then((serial) => dnsData.quickSetup({'www': serial})
));
});
app.mutableData.newRandomPrivate(consts.TAG_TYPE_WWW)
.then((serviceMdata) => serviceMdata.quickSetup()
.then(() => {
const nfs = serviceMdata.emulateAs('NFS');
return nfs.create(content)
.then((file) => nfs.insert('/index.html', file))
.then(() => {
const dnsName = sha256Hash.digest(domain);
return app.mutableData.newPublic(dnsName, consts.TAG_TYPE_DNS)
.then((dnsData) => serviceMdata.serialise()
.then((serial) => dnsData.quickSetup({'www': serial})
));
});
app.mutableData.newRandomPrivate(consts.TAG_TYPE_WWW)
.then((serviceMdata) => serviceMdata.quickSetup()
.then(() => {
const nfs = serviceMdata.emulateAs('NFS');
return nfs.create(content)
.then((file) => nfs.insert('/index.html', file))
.then(() => {
const dnsName = sha256Hash.digest(domain);
return app.mutableData.newPublic(dnsName, consts.TAG_TYPE_DNS)
.then((dnsData) => serviceMdata.serialise()
.then((serial) => dnsData.quickSetup({'www': serial})
));
});
app.mutableData.newRandomPrivate(consts.TAG_TYPE_WWW)
.then((serviceMdata) => serviceMdata.quickSetup()
.then(() => {
const nfs = serviceMdata.emulateAs('NFS');
return nfs.create(content)
.then((file) => nfs.insert('/index.html', file))
.then(() => {
const dnsName = sha256Hash.digest(domain);
return app.mutableData.newPublic(dnsName, consts.TAG_TYPE_DNS)
.then((dnsData) => serviceMdata.serialise()
.then((serial) => dnsData.quickSetup({'www': serial})
));
});
Comments on a Blog

Decorum


SAFE emailing

So what ?
🔐 is your Friend!
Search Idx
Social Grph
Currency
Join us!

Run your own vault:
Thanks!

Benjamin Kampmann
@gnunicornBen gnunicorn.org