GNAP
The future of oauth
@chalas_r


Robin Chalas

@chalas_r
chalasr
Les-Tilleuls.coop

Core Team

@chalas_r
DISCLAIMER
I'm NOT A SEcuRITY EXPERT
@chalas_r

DISCLAIMER 2
I MAY PRONOUNCE
OAUTH
INCORRECTLY
@chalas_r

REMINDER
What IS OAUTH?
@chalas_r

OAUTH?
industry-standard AUTHORIZATION protocol
for web, desktop, mobile & iOt.
@chalas_r

OAUTH WINS
-
Successful as a standard
-
Better than prior art
- Continuously improving
@chalas_r

A BIT OF HISTORY
OAuth 1.0?
-
For browser-based clients only
-
Based on Flickr’s authorization API & Google’s AuthSub
- Security concerns on the clients' shoulders
@chalas_r

OAUTH 1.0
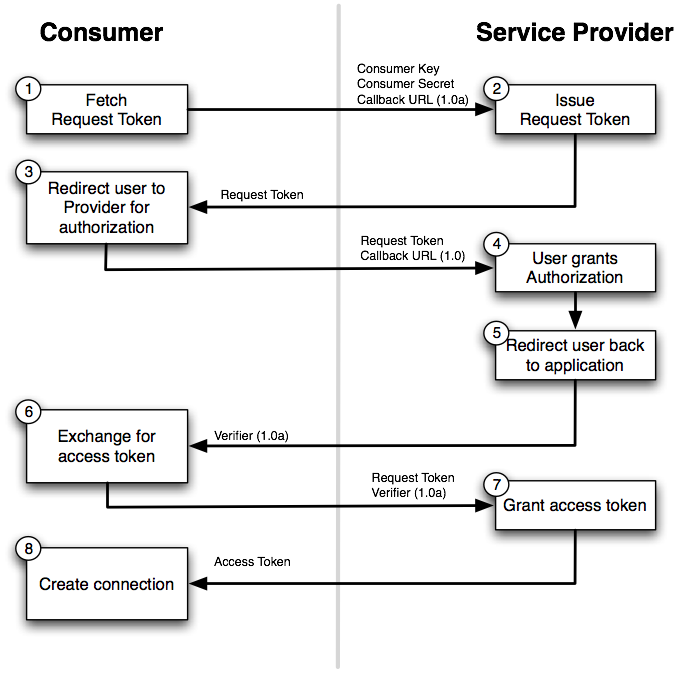
@chalas_r

A BIT OF HISTORY
OAuth 2.0?
-
Complete rewrite of OAuth 1
-
For anything that builds on HTTP(S)
- Relies on TLS (& eventually JOSE)
@chalas_r

OAuth 2.0
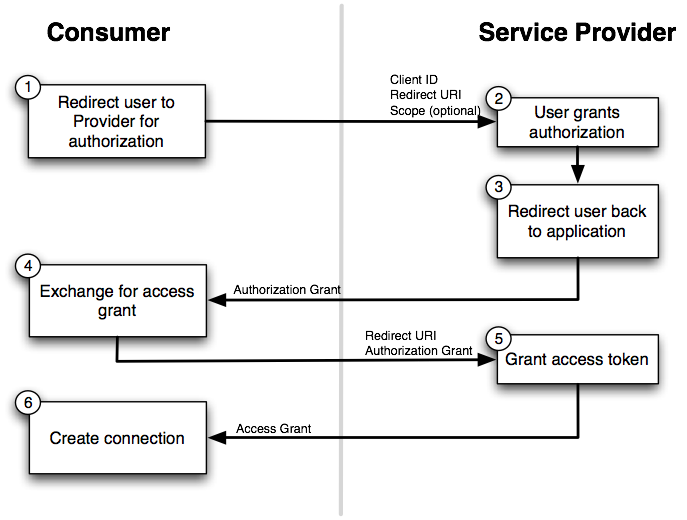
@chalas_r

OAuth 2.0
BUILT-IN Grant types
- Resource Owner Password Credentials
- Implicit
- Client Credentials
- Authorization Code
@chalas_r

OAuth 2.1
BUILT-IN Grant types
Resource Owner Password CredentialsImplicit- Client Credentials
- Authorization Code + Proof Key for Code exchange (PKCE)
@chalas_r

OAuth 2.1
OTHER MAJOR CHANGES
-
No more Bearer tokens in the query string (URL)
-
Refresh tokens must either be one-time use or sender-constrained
-
Simplified "Public VS Confidential clients" concept
- Identification/authentication concept is mentioned
@chalas_r

WHAt's WRONG WITH OAUTH2?
@chalas_r


OAuth2 FLAWS
OVERLY Complex
28 RFC + 10 ACTIVE DRAFTS
SaaS solutions exist e.g. Keycloak
@chalas_r

OAuth2 FLAWS
AUTHENTICATION
LEFT ASIDE
🎁 You've got 10+ more specifications to read!
Welcome OpenID Connect
openid.net/developers/specs/
@chalas_r

OAuth2 FLAWS
STILL TIED TO REDIRECTS
therefore to BROWSERS
@chalas_r

OAuth2 FLAWS
proof of possession
LATE to THE GAME
Welcome Mutual-TLS & DPoP
@chalas_r

OAuth2 FLAWS
CRYPTO KEYS ROTATION
NOT COVERED
@chalas_r

OAuth2 FLAWS
PAINFUL ON MOBILE
Better with RFC8252 - OAuth 2.0 for Native Apps
@chalas_r

OAuth2 FLAWS
OLD-FASHIONED
UX/DX
@chalas_r

👋 GNAP
@chalas_r

Grant
Negotiation &
Authorization Protocol
@chalas_r

GNAP
FOR MODERN APPLICATIONS' SECURITY NEEDS
@chalas_r

FOR ANY CLIENT/PLATFORM
GNAP: KEY POINTS
@chalas_r

INTERACTIONS
AS
FIRST-CLASS CONCEPTS
GNAP: KEY POINTS
@chalas_r

NO PRE-FLIGHT DISCOVERY NEEDED
GNAP: KEY POINTS
@chalas_r

GNAP: KEY POINTS
CRYPTO Keys everywhere
+ (EXTENSIBLE) rotation MECHANISMs
@chalas_r

GNAP: KEY POINTS
Bearer TOKENS
AND MORE
@chalas_r

GNAP: KEY POINTS
Multiple Access Tokens
PER GRANT REQUEST
@chalas_r

GNAP: KEY POINTS
Built-in identity!
{
"user": {
"sub_ids": [ {
"subject_type": "email",
"email": "user@example.com"
} ],
"assertions": {
"id_token": "eyj..."
}
}
}@chalas_r

GNAP: KEY POINTS
BETTER DEVELOPER ERGONOMICS
@chalas_r

GNAP: OVERALL PROTOCOL SEQUENCE
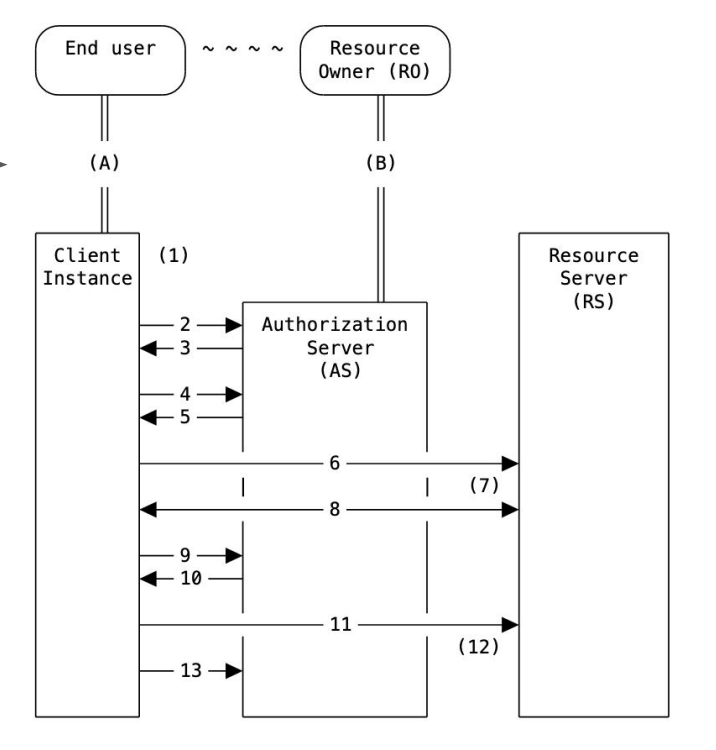
NOT
BACKWARDS-COMPATIBLE
WITH OAUTH2
@chalas_r

OAUTH GRANT TYPES EQUIVALENTS
-
Auth Code Grant =>
redirectinteraction mode (with automatic PKCE)
-
Device Grant =>
user_codeinteraction mode
- Client Credentials Grant =>
Just a Grant request with no interaction
@chalas_r

RELATIONSHIP TO OTHER SPECS
-
OpenID Connect (OIDC) =>
Identity is part of GNAP Core & Resource Server.
-
User-Managed Access (UMA) =>
Same can be achieved with only GNAP Core.
- Proof Of Posssesion (PoP, M-TLS & DPOP) =>
All tokens are key-bound by default in GNAP
@chalas_r

CURRENT STATE
WG STARTED IN OCTOBER 2020,
LED BY JUSTIN RICHER.
PROTOCOL IMPROVED A LOT SINCE THEN.
@chalas_r

It's MOSTLY Getting stable
LAST WG MEETING hAPPENED IN NOVEMBER 2022
NO PROTOCOL CHANGES.
datatracker.ietf.org/meeting/114/materials/slides-114-gnap-protocol-slides-00
@chalas_r

NEXT STEPS?
@chalas_r

GET INVOLVED
-
Read the specification
-
Subscribe to the mailing list
ietf.org/mailman/listinfo/txauth
- Implement it in your favorite language
(existing implementations available on oauth.xyz)
@chalas_r

WHAT ABOUT SYMFONY?
@chalas_r

THANK YOU!

@chalas_r
@chalas_r

