GRAPL
A Graph Platform for
Detection and Response
Twitter:
@graplsecurity
{
"host_id": "cobrien-mac",
"parent_pid": 3,
"pid": 4,
"image_name": "word.exe",
"create_time": 600,
}
{
"host_id": "cobrien-mac",
"parent_pid": 4,
"pid": 5,
"image_name": "payload.exe",
"create_time": 650,
}explorer.exe
payload.exe
word.exe
word.exe
payload.exe
word.exe
word.exe
payload.exe
ssh.exe
/secret/file
11.22.34.55
mal.doc
PARSING
SUBGRAPH
GENERATION
IDENTIFICATION
MERGING
ANALYSIS
ENGAGEMENTS
PYRAMID OF PAIN
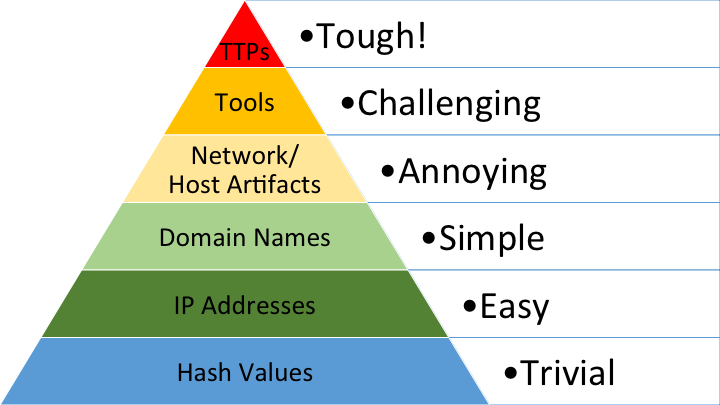
WE WANT
TO BE HERE!
AT BEST,
WE'RE HERE
MOST ARE HERE
<any process>
<any file>
<external ip>
Process with external network access creates file, executes child from it
<any browser>
Browser Executing Child Process
<any process>
<winrar/7zip/zip>
<any file>
Process Executed From Unpacked Binary
<any process>
created file
executed as
Mitre ATT&CK | T1204 - User Execution
<any process>
Rare Parent Child Process
<any process>
executed
executed
created file
executed as
connected to
executed
<any process>
Rare Parent LOLBAS Process
<any process>
executed
<binary>
<lolbas path>
<word/reader/etc>
Commonly Target Application with Non-Whitelisted Child Process
<non whitelisted process>
executed
<any process>
Questions?
?