A titkosítás
(TLS)
alapjai II.
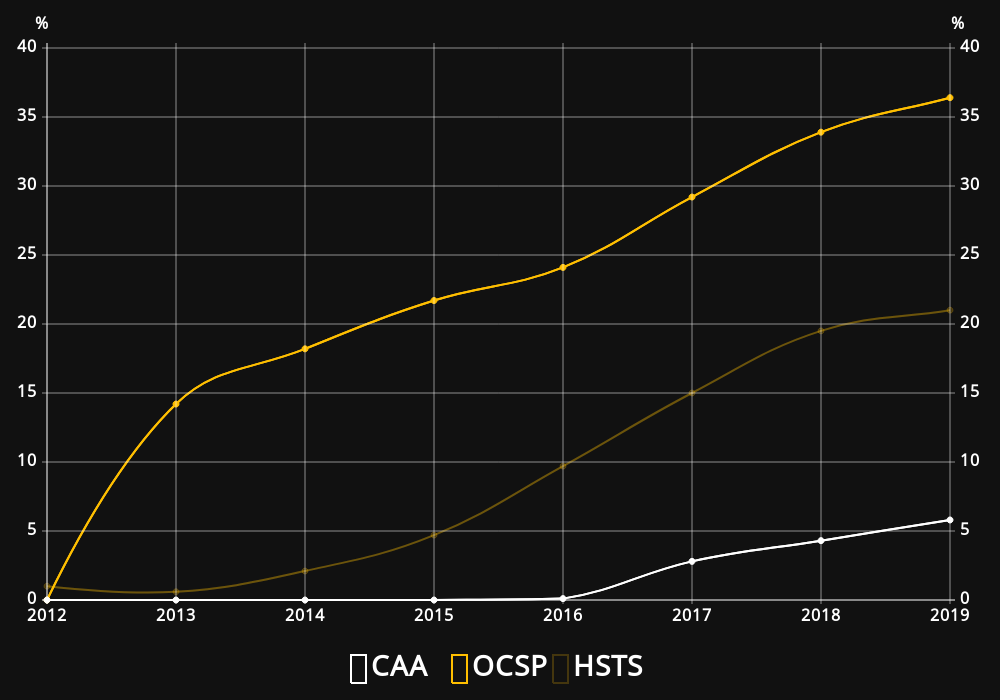
Revocation Check
-
Certificate Revocation List
-
Online Certificate Status Protocol
-
Responders
-
Stapling
-
-
Certificate validity period
Revocation Check
Location
CRL
✗
Access
Size
✗
✗
OCSP
✗
✗
✓
Privacy
✗
✓
OCSP Stapling
✓
✓
✓
✓
Full Chain
✗
✓
✓
OCSP Multi Stapling
✓
✓
✓
✓
✓
?
Support
✓
✓
✓
Hack proof
✗
✗
✗
✗
OCSP Stapling
OCSP Stapling
-
Lighttpd
ssl_stapling on;
Nginx
SSLUseStapling on
Apache
Should Be On
Certificate Transparency
- transparent
- append-only
- cryptographically assured
- reproducible
- publicly monitorable and auditable
- log
TLS 1.3
-
Key Exchange
- Authentication
- Bulk Cipher
- Hash Algorithm
-
Session Resumption
-
Revocation Check
-
Performance
-
Support
Key Exchange
ephemeral
static
Diffie–Hellman
(DH)
Rivest–Shamir–Adleman
(RSA)
Elliptic-curve
Diffie–Hellman
(ECDH)
Elliptic-curve
Diffie–Hellman Ephemeral
(ECDHE)
Diffie-Hellman Ephemeral
(DHE)
Authentication
secure
insecure
anonymous
(NULL)
Rivest–Shamir–Adleman
(RSA)
Elliptic Curve
Digital Signature Algorithm
(ECDSA)
Digital Signature Algorithm
(DSA)
Edwards-Curve
Digital Signature Algorithm
(EdDSA)
unused
Stream Cipher
secure
insecure
Rivest Cipher 4
(ARCFOUR/RC4)
ChaCha
(ChaCha20)
Block Cipher
secure
insecure
Block Size of 64 bits
(DES, 3DES, GHOST, IDEA, RC2)
Advanced Encryption Standard
(AES128, AES256)
CBC mode only
(SEED)
unused
Far East
(ARIA, Camellia)
Block Cipher Mode
authenticated
not authenticated
Cipher Block Chaining
(CBC)
Galois/Counter Mode
(GCM)
Counter with CBC-MAC
(CCM/CCM-8)
MAC
secure
collisions
Message-Digest Algorithm 5
(MD5)
Poly1305
(POLY1305)
Secure Hash Algorithm 2
(SHA256, SHA384)
Secure Hash Algorithm 1
(SHA-1)
Cipher Suites
-
TLS_AES_256_GCM_SHA384 -
TLS_AES_128_GCM_SHA256
-
TLS_AES_128_CCM_SHA256 -
TLS_AES_128_CCM_8_SHA256
-
TLS_CHACHA20_POLY1305_SHA256
Revocation Check
-
Certificate Revocation List
-
Online Certificate Status Protocol
-
Responders
-
Stapling
-
Session Resumption
PFS
obsolated
session resumption
(session id)
session resumption without server-side state
(session ticket)
non PFS
static pre-shared-key
(PSK_KE)
ephemeral pre-shared-key
(PSK_DHE_KE)
Performance
-
Handshake
-
Resumption
-
Application layer
Support
library
browser
Most popular
(Chrome/Chromium, Firefox)
Less popular
(Apple, Edge)
server
CDN
Most popular
(Apache, NGINX)
Less popular
(IIS, Lighty)
Most popular
(Cloudflare, KeyCDN)
Most popular
(OpenSSL, GnuTLS)
Less popular
(Boring SSL, Fizz)
HTTPS
-
Automatic Redirection to HTTPS
- HSTS Preload
-
Security Headers
Secure Headers
-
Automatic Redirect to HTTPS
-
Public Key Pinning
-
Defense against
-
Clickjacking
-
Content Injection Attacks
-
Cross-site scripting
-
HTTP STS
setenv.add-response-header=("Strict-Transport-Security"=>"Value")
Lighttpd
add_header Strict-Transport-Security 'Value' always;
Nginx
Header always set Strict-Transport-Security "Value"
Apache
max-age=63072000; includeSubdomains;
preload
HTTP STS

HTTP Public Key Pinning
setenv.add-response-header=("Public-Key-Pins"=>"Value")
Lighttpd
add_header Public-Key-Pins 'Value' always;
Nginx
Header always set Public-Key-Pins "Value"
Apache
pin-sha256="GRAH5Ex+kB4cCQi5gMU82urf...";
report-uri="https://example.com/report/hpkp";
max-age=15768000;
includeSubDomains
Expect Staple
setenv.add-response-header=("Expect-Staple"=>"Value")
Lighttpd
add_header Expect-Staple 'Value' always;
Nginx
Header always set Expect-Staple "Value"
Apache
max-age=31536000;
report-uri="https://example.com/report/staple";
includeSubDomains;
preload
Expect CT
setenv.add-response-header=("Expect-Staple"=>"Value")
Lighttpd
add_header Expect-Staple 'Value' always;
Nginx
Header always set Expect-Staple "Value"
Apache
max-age=31536000;
report-uri="https://example.com/report/staple";
enforce
Clickjacking
setenv.add-response-header=("X-Frame-Options"=>"Value")
Lighttpd
add_header X-Frame-Options "Value" always;
Nginx
Header always set X-Frame-Options "Value"
Apache
deny/sameorigin
XSS Protection
setenv.add-response-header=("X-XSS-Protection"=>"Value")
Lighttpd
add_header X-XSS-Protection "Value" always;
Nginx
Header always set X-XSS-Protection "Value"
Apache
X-XSS-Protection: 1; mode=block
Feature Policy
setenv.add-response-header=("Feature-Policy"=>"Value")
Lighttpd
add_header Feature-Policy "Value" always;
Nginx
Header always set Feature-Policy "Value"
Apache
microphone 'none';
geolocation ''*'';
payment 'self';
...
Content Security Policy
setenv.add-response-header=("Content-Security-Policy"=>"Value")
Lighttpd
add_header Content-Security-Policy "Value" always;
Nginx
Header always set Content-Security-Policy "Value"
Apache
default-src https://same.domain:443
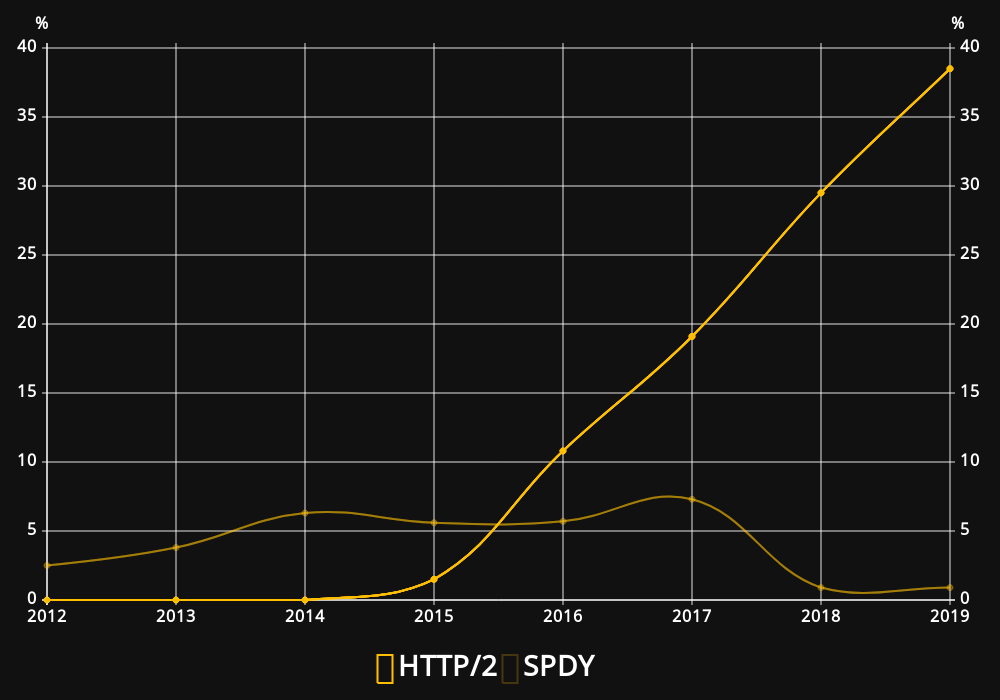
Application Protocols
Tools
-
Online checkers
-
Offline checkers
- TLS offloaders
Online Checkers
-
Transport Layer Security
-
Security Headers
Offline Checkers
TLS offloaders
Questions?
