Detecting the Behavioral Relationships of Malware Connections
(positional paper)
Sebastian Garcia & Michal Pechoucek
sebastian.garcia@agents.fel.cvut.cz
@eldracote
Live: bit.ly/praise2016



-
Privacy and surveillance. The MasterMind program.
-
We should know how to deal with this, and use it.
-
-
Behavior of malware, how to detect it.
The origin
The Problem
-
False positives: You detect malicious when is not.
-
Detection of what?
-
Packets?
-
Flows?
-
Web logs?
-
Unique computers?
-
-
-
Differentiating normal from malicious
-
We may detect malicious alone. But when it is mixed with normal, it's far more difficult.
-
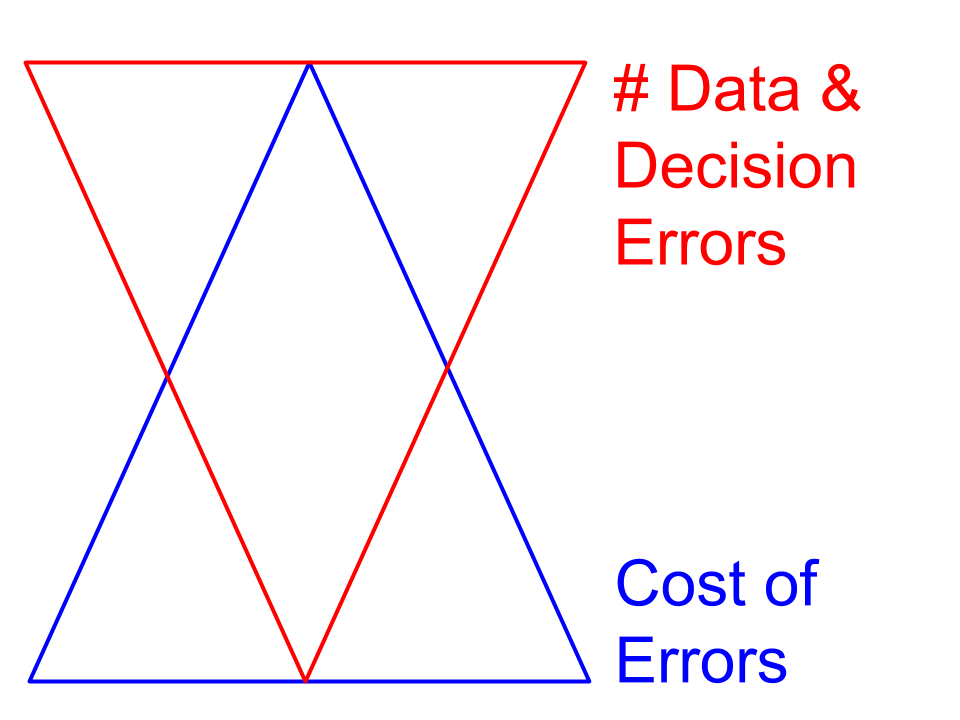
Stratosphere IPS Project
-
Model network behaviors as a string of letters.
-
1 flow 3 features 1 letter
-
1 connection (srcIP, dstIP, dstPort, Proto) String

The Problem of Stratosphere
-
Usually working, but some behaviors are very similar.
-
Normal Radio Streaming
-
88,h,h,h,h,h,h,H,H,h,h,h,h,H,H,h,H,H,h,H,h,H,H,H,h,
-
-
Botnet C&C server 23.247.5.27 port 25000/tcp
-
88,H,H,h,H,H,h,h,h,h,h,H,h,H,H,H
-
A better differentiation
-
We are looking too closely.
-
Analyze the behavior of the Host, instead of a connection.
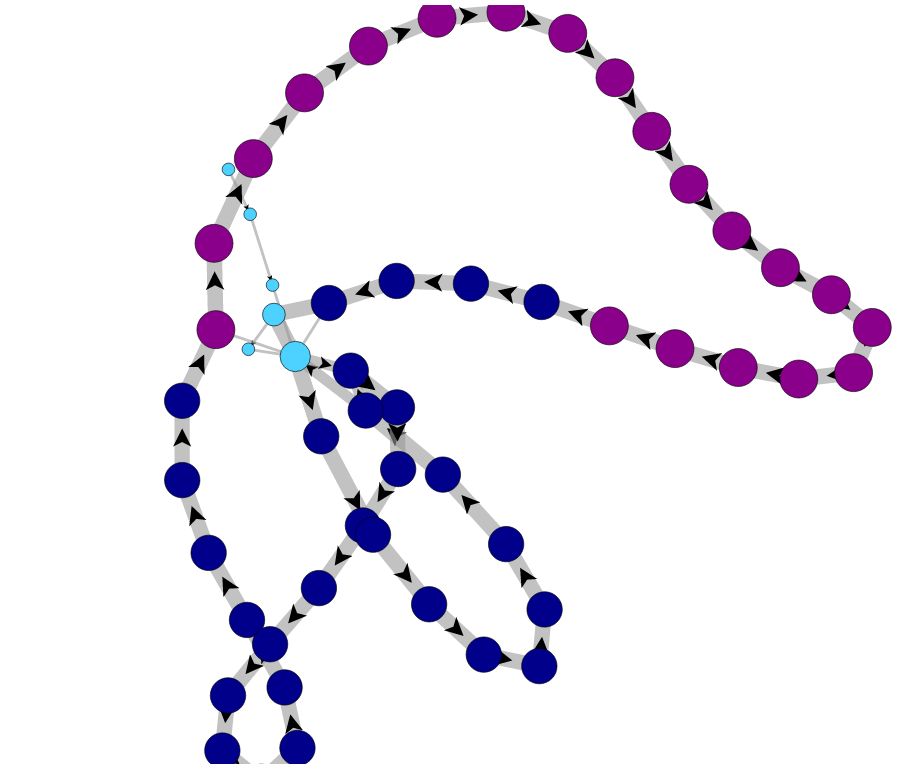
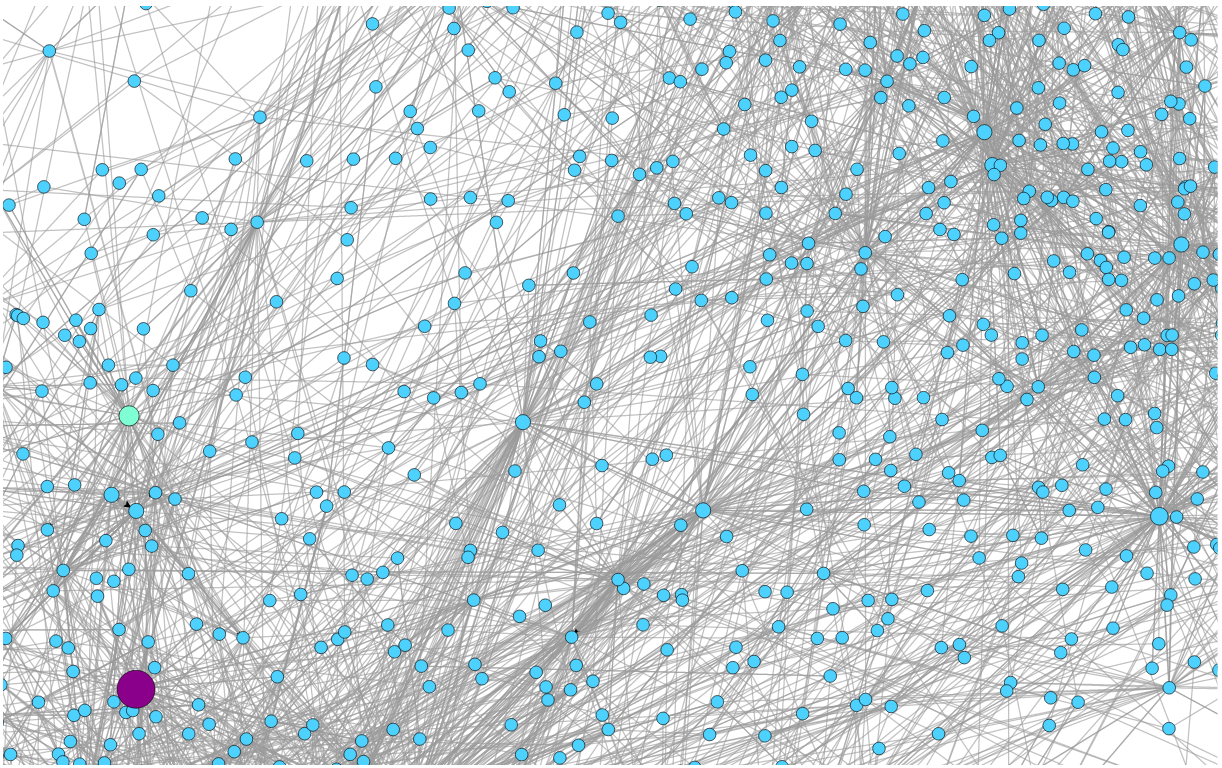
A New type of Graph
-
A graph to show the relationships of flow sequences.
-
Made by Daniel Šmolík, from the Stratosphere team.
-
A graph per client (source IP).
-
A node is the combination of dst IP, dst port, protocol.
-
An edge is a flow sequence as seen in the network.
-
-
The more times the edge is found, the thicker.
-
The more times the node is repeated, the larger.
-
The more times the node looped, the color changes.
Normal Graph
-
1 client
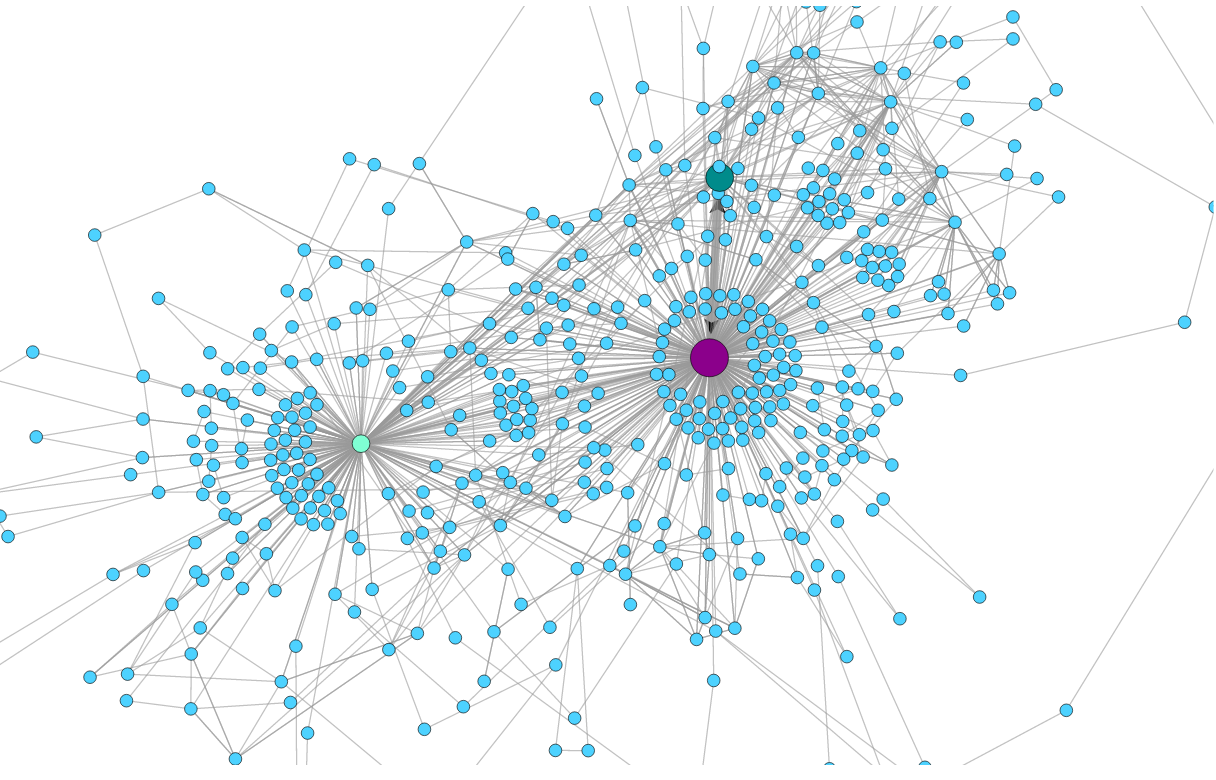
Normal Graph
-
Same 1 client, not DNS servers.
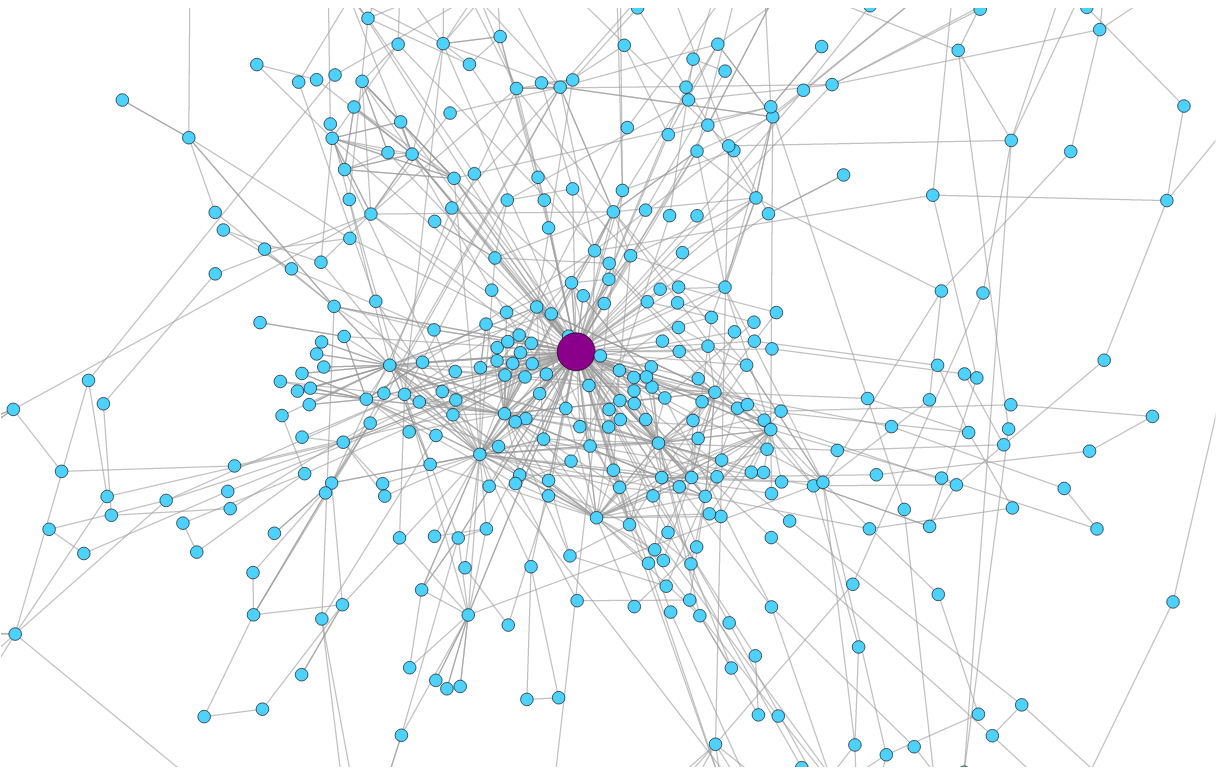
Geodo Botnet complete graph
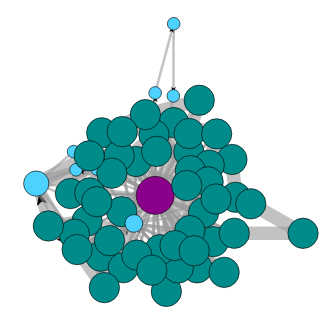
Geodo Botnet filtered graph
-
No DNS, icmp, ipv6, arp or multicast.
Mixed Normal and Adware
-
Before Infection. No DNS

Mixed Normal and Adware
-
After Infection. No DNS
Mixed Normal and Adware
-
After Infection. No DNS

Analyzing the Behavior of a Host
-
Now
-
Amount of times a [dst ip, dst port and protocol] is accessed (node).
-
Amount of times a node comes after other node in sequence (edge).
-
Amount of times a node loops with itself.
-
-
Work in progress
-
Loops
-
Find loops in the graph structure.
-
Complex loops, double loops (Geodo).
-
-
Type of nodes.
-
Type of nodes connecting to each node (relation).
-
Stratosphere Behaviors
-
Conclusion and Thanks!
-
The behavior of a host may be modeled looking at its actions, relationships and loops.
-
These are the differentiable features of malware.
-
-
More experiments, evaluation and comparison.