SAST, Code Quality, Secret Detection



Abdullah Fathi


Pautan Muat Turun
Static Application Security Test
(SAST)
Gitlab SAST use analyzer to check source code for any known vulnerabilities
include:
- template: Jobs/SAST.gitlab-ci.yml
#Static Application Security Test (SAST)
sast:
stage: test
artifacts:
paths: [gl-sast-report.json]
reports:
sast: gl-sast-report.jsonCustom SAST Parser
Transform gl-sast-report.json to HTML file for easiness of viewing and analyse the report
.sast_html: &sast_html
services:
- name: docker:dind
command: ["--tls=false"]
after_script:
- sleep 10
- apk add --update docker openrc
- docker pull pcfens/sast-parser
- alias sast-parser="docker run --rm -v \"$(pwd):/reports\" pcfens/sast-parser"
- sast-parser ${INPUT_JSON} > ${OUTPUT_HTML}
artifacts:
paths:
- ${OUTPUT_HTML}
nodejs-scan-sast:
<<: *sast_html
variables:
DOCKER_DRIVER: overlay2
DOCKER_HOST: tcp://docker:2375/
DOCKER_TLS_CERTDIR: ""
INPUT_JSON: "gl-sast-report.json"
OUTPUT_HTML: "nodejs-scan-sast.html"
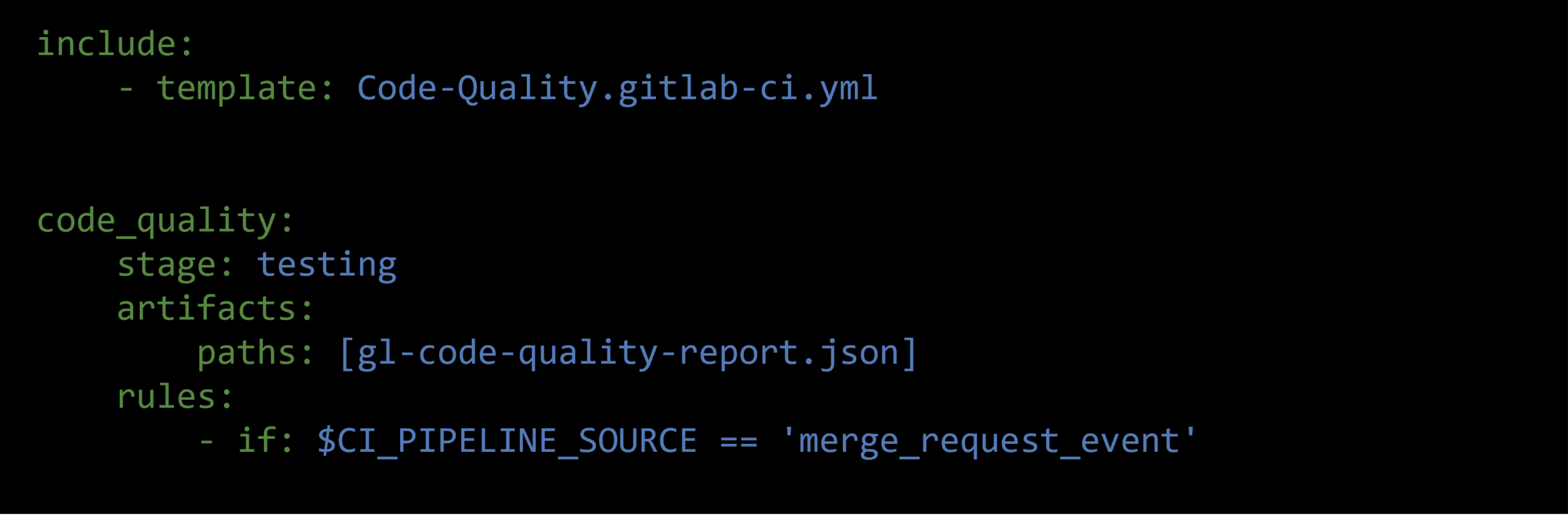
Code Quality Test
- Gitlab uses plugins supported by Code Climate, which are free and open source. Code Quality does not require a Code Climate subscription.
- To ensure your project’s code stays simple, readable, and easy to contribute to
Secret Detection
Scans your repository to help prevent your secrets from being exposed. Secret Detection scanning works on all text files, regardless of the language or framework used
include:
- template: Jobs/Secret-Detection.gitlab-ci.ymlYour feedback matters


There are no secrets to success. It is the result of preparation, hard work, and learning from failure. - Colin Powell