the key elements of risk
by hvale vale
What is risk?

the key elements
Threat + Probability + Impact
=
risk
Threat
Threat is any negative action aimed towards a person / group
Probability is the likelihood of a threat becoming real
probability
impact
RIsk
Impact is what will happen when a threat is realized; consequences
Risk is the intersection of these three concepts
threats
- An intent to cause harm towards an individual or group in order to control their actions
- Direct threats are declared intention to cause harm
- Indirect threats are those that happen as a result of a change in a situation
- In defining threats, it is important to identify where the threat is coming from
- Even better, who is the threat from
Probability
- Is the likelihood of a threat becoming real
- This can be about location, practice and behaviour of the individual / group that increase the opportunities for a threat to be realised
- This is also about the capacity of the groups / individuals that are making the threat
- To assess probability, ask if you have real examples of a threat happening to someone or a group that you know – and compare that situation with yours
impact
- What will happen when a threat is realised – the consequences
- Impact can be on the individual, organisational, network or movement
- The higher and more number of impacts of one threat, the greater the risk
Risk Analysis
Probability – Impact of Threats
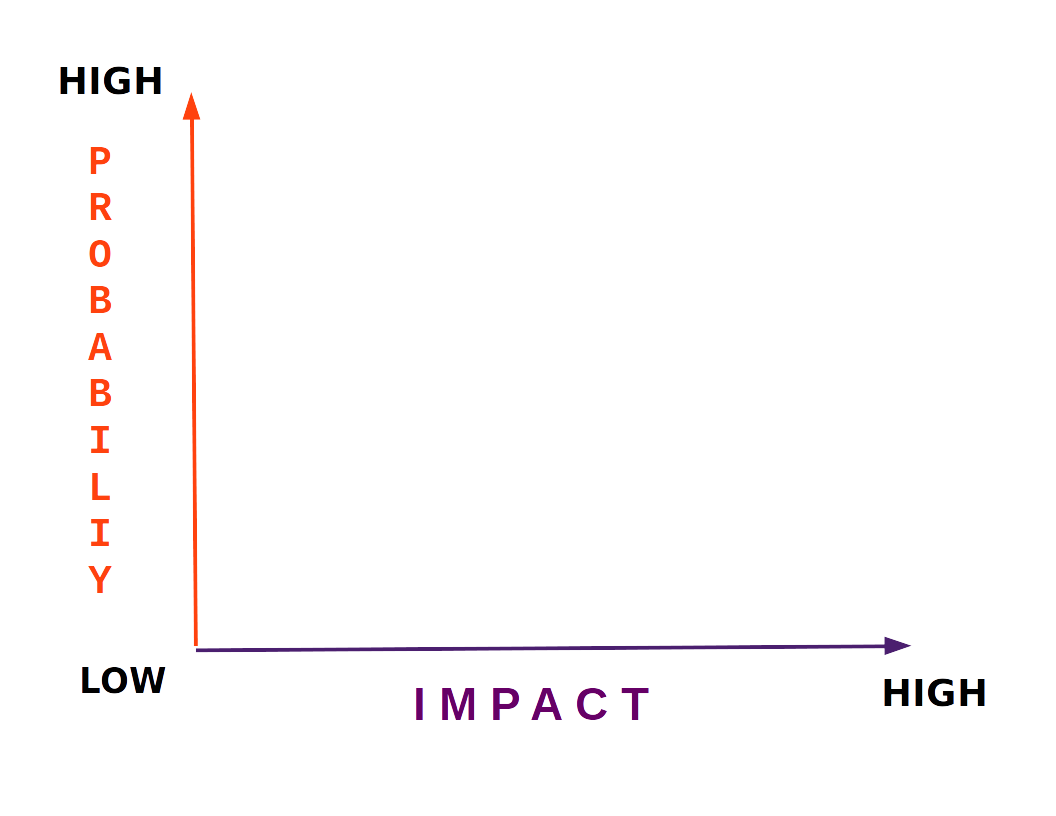
assessing risk
why?
- To make realistic decisions and plans about the risks that you / your group are facing
- To be able to prioritise which risks to focus on – high probability and / or high impact
- To manage fear
- First step to identify / see:
- current and needed capacities,
- strategies & resources
required to avoid risks or minimize the impact of risks
risk assessement
a simple template
| Risk: |
|---|
| Threat: (Be specific. Name who is the source of the threat and what is it) |
|
Probability: (Low – Medium - High) Vulnerabilities – What kind of information is readily available online about the person posting opinion? – What are the vulnerabilities in the used platform(s)? Capacity of the individual/group threatening – How many are they? Known Incidents – Have other people with the same opinions been targeted? |
Impact: (Low – Medium - High) |
Mitigation Tactics Input and Discussion
1. Accept the risk and make contingency plans
Contingency planning is about imagining the risk and the worst case impact happening, and taking steps to deal with it.
2. Avoid the risk. Decrease your vulnerabilities
What skills will you need? What behavioral changes will you have to undertake to avoid the risk?
3. Control the risk. Decrease the severity of the impact
Focus on the impact and not the threat, and work towards minimising the impact.
What skills will you need to address the impact?
4. Transfer the risk. Get an outside resource to assume the risk and its impact
5. Monitor the risk for changes in probability and impact
This is generally for low probability risks.
dealing with risks
Preventive Strategies
-
What actions and capacities do you already have in order to prevent this threat?
-
What actions will you take in order to avoid this threat from being realised? How will you change the processes in the network in order to prevent this threat from happening?
-
Are there policies and procedures you need to create in order to do this?
-
What skills will you need in order to prevent this threat?
dealing with risks
Incident Response
-
What will you do when this threat is realised? What are the steps that you will take when this threat happens?
-
How will you minimise the severity of the impact of this threat?
-
What skills do you need in order to take the steps necessary to respond to this threat?
Some considerations
- Risk assessment is useful to come up with realistic strategies (preventive and responsive)
- Focus on the threats that have high probability and high impact
- Risk assessment takes practice
Credits
The Risk Assessment presentation is part of FTX: Safety Reboot a resource developed by the APC Women’s Rights Programme (APC WRP) as a contribution to existing training guides on digital security but rooted in a feminist approach to technology.