Data Encryption with KMS
Kajihiro Kazunori

#kichijojirb
Komoju

- http://docs.komoju.com/
- Japanese Payment Gateway
- API Access
- Supports many Japanese payment methods
- Credit Card
- Konbini(コンビニ)
- Bank Transfer
- WebMoney
- PayEasy
Komoju

- http://docs.komoju.com/
- Japanese Payment Gateway
- API Access
- Supports many Japanese payment methods
- Credit Card
- Konbini(コンビニ)
- Bank Transfer
- WebMoney
- PayEasy
We need to store credit card data



We need to store credit card data
How should we store credit card data?
PCI DSS v3
Payment Card Industry Data Security Standard
PCI DSS provides a baseline of technical and operational requirements designed to protect cardholder data.
PCI DSS v3
Payment Card Industry Data Security Standard
3.4 Render PAN unreadable anywhere it is stored (including on portable digital media, backup media, and in logs) by using any of the following approaches:
- One-way hashes based on strong cryptography, (hash must be of the entire PAN)
- Truncation (hashing cannot be used to replace the truncated segment of PAN)
- Index tokens and pads (pads must be securely stored)
- Strong cryptography with associated key-management processes and procedures.
PCI DSS v3
Payment Card Industry Data Security Standard
3.5.2 Store secret and private keys used to encrypt/decrypt cardholder data in one (or more) of the following forms at all times:
- Encrypted with a key-encrypting key that is at least as strong as the data-encrypting key, and that is stored separately from the data-encrypting key
- Within a secure cryptographic device (such as a host security module (HSM) or PTS-approved point-of-interaction device)
- As at least two full-length key components or key shares, in accordance with an industry
Secret Key Types
So, we should have 2 types of key
- Data-encrypting key
- Key-encrypting key
Amazon KMS
The AWS Key Management Service (AWS KMS) is a managed service that makes it easy for you to create and control the encryption keys used to encrypt your data.
How KMS works
-
Customer Master Keys(CMK)
- Basically KMS manages CMK
- can be used inside of AWS KMS to encrypt or decrypt data
- This is a key-encrypting key

How KMS works
-
Data Key
- Generated by KMS via API
- "generate_data_key" resource
- The API returns plaintext and encrypted version of data key
- This is a data-encrypting key
- Generated by KMS via API
How KMS works
-
Decrypt
- Decrypts encrypted data key
- "decrypt" resource
- The API returns plaintext version of data key
- Decrypts encrypted data key
How KMS works
-
Permission Control
- You can define a resource-based policy
How KMS works
client = Aws::KMS::Client.new
### Generating data key
resp = client.generate_data_key(key_id: "c4daa226-...",
key_spec: "AES_256")
Base64.encode64(resp.plaintext)
#=> "m4Qi66NvmLlV5ut8Qxiw/qA1q0vt2yadjqp6YhHthmA=\n"
encrypted_data_key = Base64.encode64(resp.ciphertext_blob)
#=> "CiDFJioCMK4fkTzvs2KVLh737rxUi3bT0GsQkCpsiT3nxhKnAQEBAwB4xSYq\nAjCuH5E87..."
### Decrypting encrypted data key
resp2 = client.decrypt(ciphertext_blob: Base64.decode64(encrypted_data_key))
Base64.encode64 resp2.plaintext
#=> "m4Qi66NvmLlV5ut8Qxiw/qA1q0vt2yadjqp6YhHthmA=\n"Code Example
How Komoju Use KMS
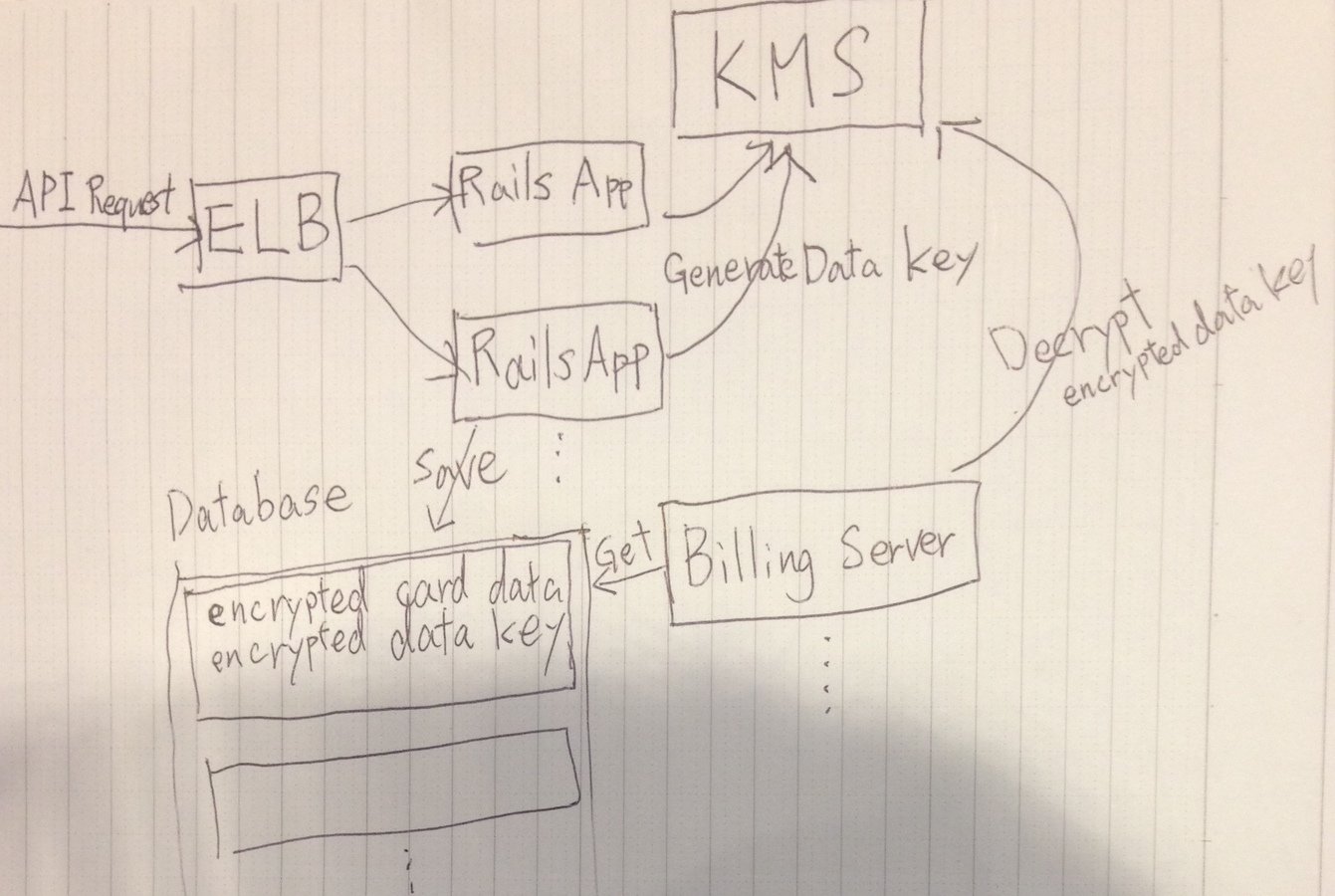
How Komoju Use KMS

- can only "generate data key"
- can't "decrypt"
- generate data key
- encrypt data with data key
- save encrypted data / key
How Komoju Use KMS

Stores
- encrypted card data
- encrypted data key
- can only "generate data key"
- can't "decrypt"
- generate data key
- encrypt data with data key
- save encrypted data / key
How Komoju Use KMS

Stores
- encrypted card data
- encrypted data key
-
Get encrypted data from DB
- encrypted card data
- encrypted data key
- decrypt data key
- decrypt card data
- can only "generate data key"
- can't "decrypt"
- generate data key
- encrypt data with data key
- save encrypted data / key
まとめ
KMSを使えばセキュアなシステムを簡単に構築できます