A Brief History of Containers
With a Few Noteworthy Tangents
About Me
-
Nathan Murthy
-
Software Engineer at Tesla / SolarCity
- Interests: distributed systems, microservices, big data, machine learning, clean energy for the masses
"You are always in a container. Even
when you don't run containers, you
are in a container."
(Sipe 2016)
docker = container
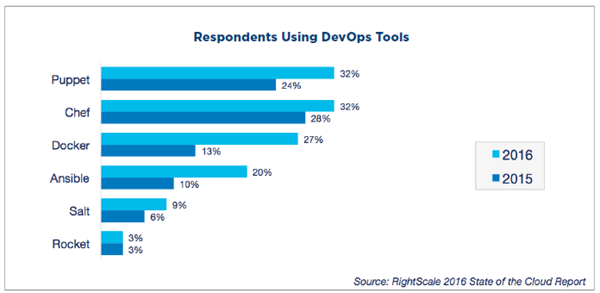

docker = automation
docker ≠ automation
https://www.pinterest.com/email2sekhar/devops-understanding/
docker ≠

1. OS-Level Virtualization
2. Hardware Virtualization
Two Historical Trends in Computing
History of OS-Level Virtualization
| 1979-1982 | UNIX chroot |
| 1998 | FreeBSD Jail |
| 2001 | Linux VServer |
| 2002 | Linux namespaces |
| 2005 | Sun Microsystems: Solaris Containers / Solaris Zones |
| 2005 | OpenVZ |
| 2007 | Google: cgroups |
| 2007 | PaaS: Heroku, Joyent, CloudFoundry |
| 2008 | LXC |
| 2010 | systemd |
| 2013 | Docker |
| 2015 | CoreOS: Application Container Spec (appC, rkt) |
| 2015 | Open Container Initiative: lmctfy, libcontainer, runC |
History of Hardware Virtualization
| 1966-1972 | IBM (CP/CMS) |
| 1974 | Popek & Goldberg coin the term "hypervisor" in Formal Requirements for Virtualizable Third Generation Architectures |
| 1989 | Insignia SoftPC |
| 1995 | Sun Microsystems: Java Virtual Machine |
| 1998 | VMWare |
| 2003 | Xen Hypervisor |
| 2006 | Amazon EC2 |
| 2007 | Sun: Logical Domains (Oracle VM Server for SPARC and x86) |
| 2007 | Linux KVM |
| 2008 | Microsoft Hyper-V |
chroot


$ man chrootjail

jail
A Jail in FreeBSD-speak is one or more tasks with the same kernel Jail-ID, bound on zero or more IP addresses, having the same chroot-environment.
https://erdgeist.org/arts/software/ezjail/
$ man jailLinux-VServer

Linux Namespaces
| Namespace | Isolates |
|---|---|
| Cgroup* | Cgroup root directory |
| IPC | System V IPC, POSIX message queues |
| Network | Network devices, stacks, ports, etc. |
| Mount | Mount points |
| PID | Process IDs |
| User | User and group IDs |
| UTS | Hostname and NIS domain name |
Linux provides the following namespaces:
http://man7.org/linux/man-pages/man7/namespaces.7.html
$ sleep 20 &
[1] 2325
$ sudo tree /proc/2325/ns
/proc/2325/ns
├── ipc -> ipc:[4026531839]
├── mnt -> mnt:[4026531840]
├── net -> net:[4026531956]
├── pid -> pid:[4026531836]
├── user -> user:[4026531837]
└── uts -> uts:[4026531838]Sun introduces Solaris Containers and Solaris Zones, an alternative to their virtual machine technology.
Solaris Containers
"chroot on steroids"
(Schmidt 2006)

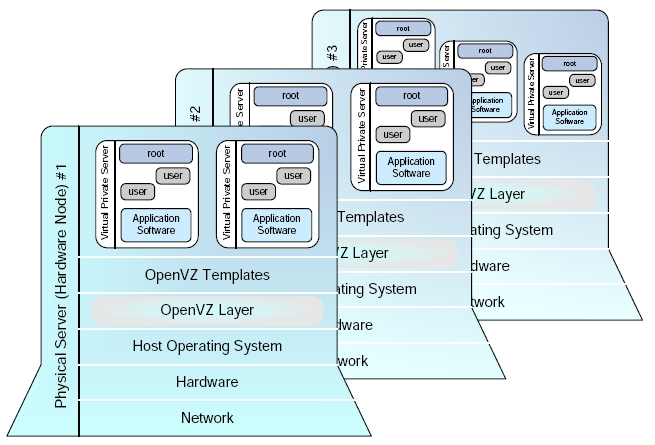
OpenVZ
cgroups
-
Contribution by Google to Linux kernel
-
Originally called "process containers"
-
Renamed to "cgroups"
- Merged into kernel 2.6.24
cgroups
$ ls -l /sys/fs/cgroup
drwxr-xr-x 4 root root 0 Feb 18 21:55 blkio
drwxr-xr-x 4 root root 0 Feb 18 21:55 cpu
drwxr-xr-x 4 root root 0 Feb 18 21:55 cpuacct
drwxr-xr-x 4 root root 0 Feb 18 21:55 cpuset
drwxr-xr-x 4 root root 0 Feb 18 21:55 devices
drwxr-xr-x 5 root root 0 Feb 18 21:55 freezer
drwxr-xr-x 4 root root 0 Feb 18 21:55 hugetlb
drwxr-xr-x 4 root root 0 Feb 18 21:55 memory
drwxr-xr-x 4 root root 0 Feb 18 21:55 perf_event
drwxr-xr-x 4 root root 0 Feb 18 21:55 systemd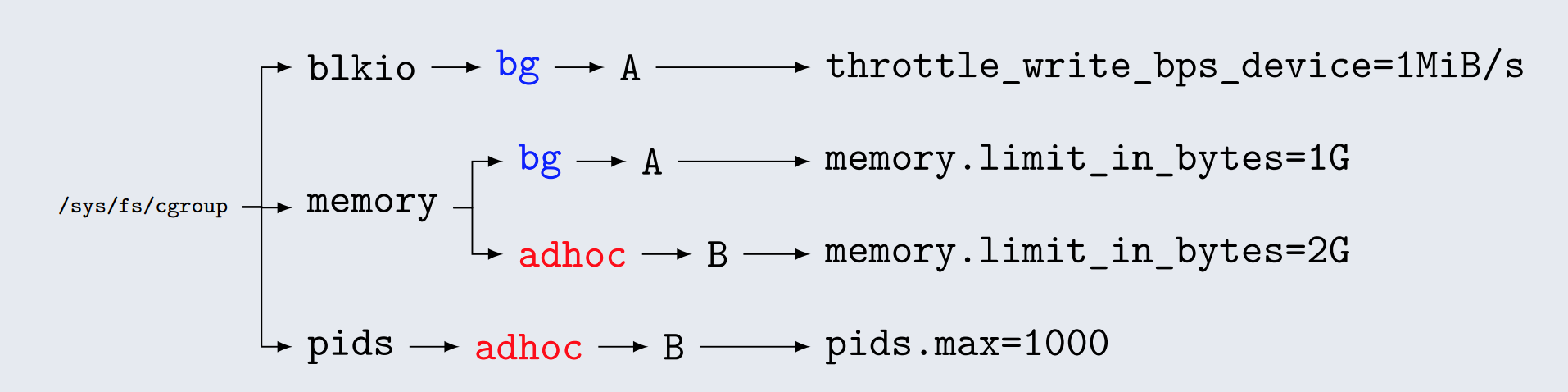
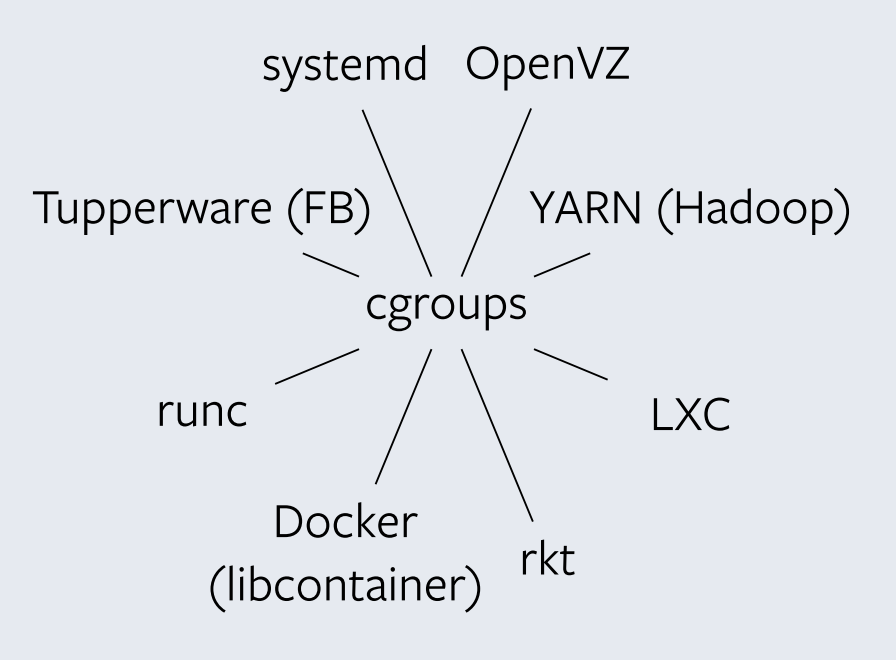
namespaces + cgroups
cgroup: limits how much you can use
namespace: limits how much you can
see (and therefore use)
(Sipe 2016)
LXC

(Hykes 2013)
Newer kids on the block



???
Landscape Today










History of OS-Level Virtualization
| 1979-1982 | UNIX chroot |
| 1998 | FreeBSD Jail |
| 2001 | Linux VServer |
| 2002 | Linux namespaces |
| 2005 | Sun Microsystems: Solaris Containers / Solaris Zones |
| 2005 | OpenVZ |
| 2007 | Google: cgroups |
| 2007 | PaaS: Heroku, Joyent, CloudFoundry |
| 2008 | LXC |
| 2010 | systemd |
| 2013 | Docker |
| 2015 | CoreOS: Application Container Spec (appC, rkt) |
| 2015 | Open Container Initiative: lmctfy, libcontainer, runC |
Containers are all about
-
OS-Level Virtualization
-
Visibility
-
Isolation
- Resource Management
- Automation (?)
- Microservices

Hmm, but you may be just as well off with tools like wget, zip, tar, upstart, systemd, and the gamut of commands already available to you on your *nix host machine.
Depends on scale and granularity.
Containers at Scale
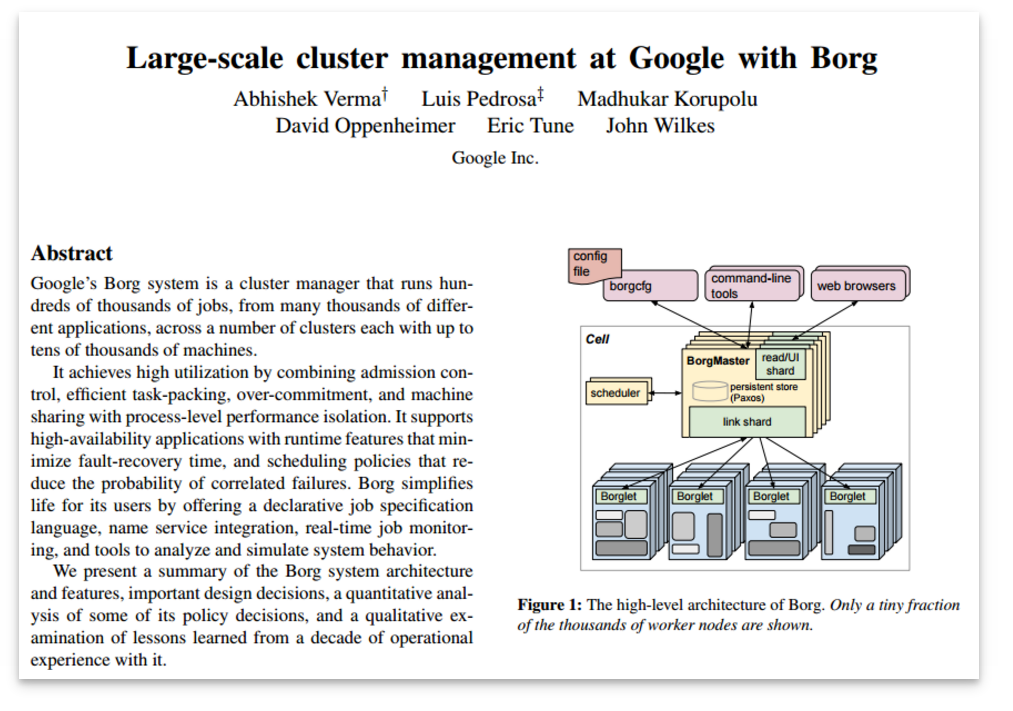
"One of Borg’s primary goals is to make efficient use of Google’s fleet of machines, which represents a significant financial investment: increasing utilization by a few percentage points can save millions of dollars.
...
Borg users request CPU in units of milli-cores, and memory and disk space in bytes."
Verma et al. "Large-scale cluster management at Google with Borg" in ACM EuroSys (2015).
Inspired by:
1. Rani Osnat: http://blog.aquasec.com/a-brief-history-of-containers-from-1970s-chroot-to-docker-2016
2. Bryan Cantrill: http://www.slideshare.net/bcantrill/run-containers-on-bare-metal-already
Q+A
-
@natemurthy
-
namurthy@tesla.com
- github.com/natemurthy
