Why is Cyber-security of Businesses Crucial? Lessons from Ethical Hackers
Ing Roman Fulop and Ing Pavol Luptak
Nethemba s.r.o.
HACKERS' DEMOS
Please, be a part of the experiment:
Sensitive information
harvesting
(please provide your company domain)
Who we are?
- 10 computer security experts (penetration testers, security consultant, social engineers, ...) from Slovakia, UK, Argentina
- Established in Central Europe covering German-speaking market through Nethemba GmbH
- Holders of renowned security certifications including OSCP (Offensive Security Certified Professional), OSCE (Offensive Security Certified Expert), CISSP (Certified Information System Security Professional), CEH (Certified Ethical Hacker), SCSecA (Sun Certified Security Administrator), CCNP Security, CCSP (Cisco Certified Security Professional), OSWP, OSWE
WhatsApp vs Signal privacy battle
- Signal, unlike WhatsApp, is open-source (everybody can read it and look for security vulnerabilities)
- Signal, unlike WhatsApp, does not share metadata and private keys with Facebook
- WhatsApp communication is encrypted, but you are not the only one who owns the keys!
- Top exposed people (like Snowden) recommend and use Signal
- US military and EU commission recommend to use Signal internally in their communication (not WhatsApp)
Use Signal if you really care about the privacy of your text messages and calls!
Download it here
https://signal.org/download/
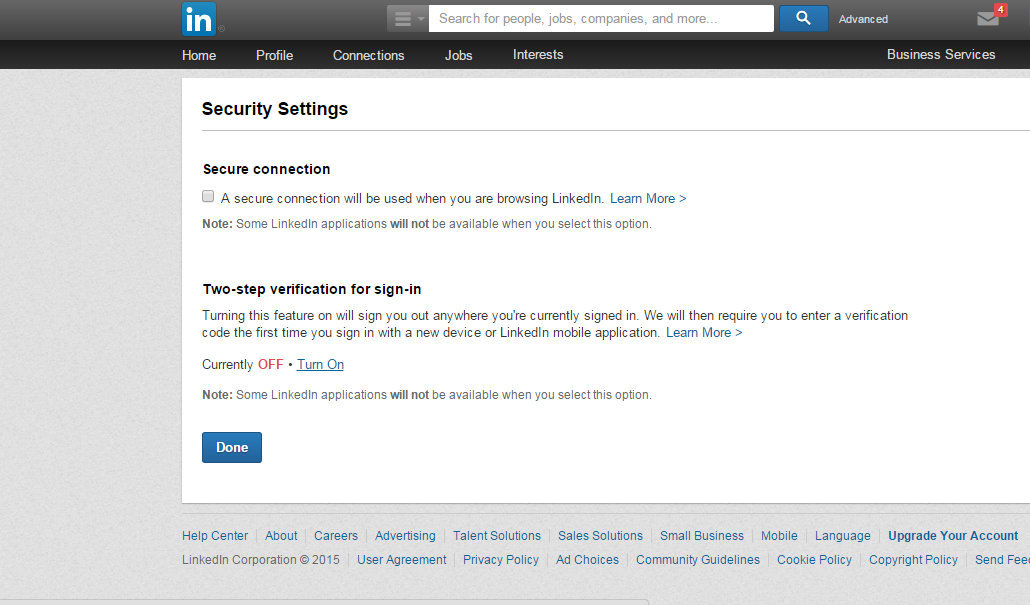
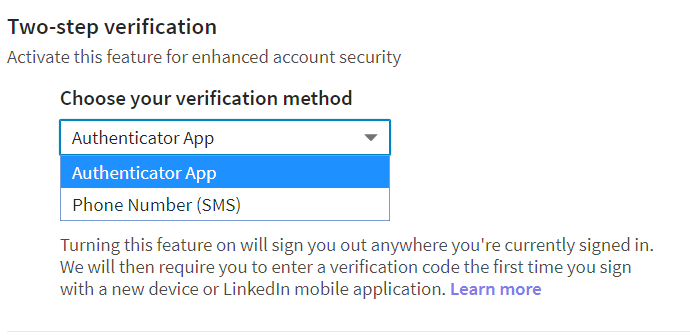
Enable two-factor authentication
- For all your Internet services including Facebook, Twitter, LinkedIn, Google, Apple, Microsoft
- It significantly improves security of your accounts
- Do not use the traditional SMS verification, it is not secure enough
- always prefer two-factor authentication (2FA)
- Install Google Authenticator or Authy
Use secure password managers
- Most people are not able to remember most of their passwords and passphrases
- Using secure password managers is always a better idea than write your password to the text file or to the paper
- The most advanced and secure are Dashlane, LastPass, KeyPass
- Remember just one strong passphrase (and optionally enable 2FA)
What is a penetration test?
- A method of evaluating the security of a computer system or network by simulating an attack by a malicious hacker
- Involves an active analysis of the system for any weaknesses, technical flaws or vulnerabilities and exploitation
- OSSTMM methodology or OWASP Testing Guide is used
-
TEST APPROACHES
- Black box - a zero-knowledge attack - no relevant information about the target environment is provided, the most realistic external penetration test
- White box - a full-knowledge attack - all the security information related to an environment and infrastructure is considered
- Grey box - a partial-knowledge attack
Test Phases
- Discovery - information about the target system is identified and documented (WHOIS service, public search engines, domain registrators, etc.).
- Enumeration - using intrusive methods and techniques to gain more information about the target system (port scanning, fingerprinting).
- Vulnerability mapping - mapping the findings from the enumeration to known and potential vulnerabilities.
- Exploitation - attempting to gain access through vulnerabilities identified in the vulnerability-mapping phase. The goal is to gain user-level and privileged (administrator) access to the system (custom exploit scripts or exploit frameworks are used).
Standard Web Application Test
- Reveal as much as possible the most critical security vulnerabilities in the web application/web server during 3 days
- Exploit them and gain privileged access if it is possible
- Reveals the most serious vulnerabilities (SQL/LDAP injections, XSS/CSRF, buffer overflows, business logical flaws, authentication bypass, local file inclusions)
- Provides a technical report with an executive summary, all revealed vulnerabilities, risk levels, and recommendations.
- Due to manual inspection, the test is highly recommended when you automatized security scanners have already failed.
Comprehensive Web Application Audit
- The most comprehensive and deepest web application audit on the market
- Strictly follows the OWASP Testing Guide v4
- A Practical hacking demonstration (writing exploit codes, database dump, XSS/CSRF demonstration etc)
- The comprehensive report in English/Spanish/Czech/Slovak
- It takes 2-4 weeks per one application
- Suitable for the large organizations (banks, any fintech companies)
Smartphone Application Security Audit
- The smartphone security audit system involves a technical security audit of the mobile application itself and appropriate server web services (REST / SOAP).
- During testing, we follow the OWASP Mobile Security Project mainly focusing on the Top Ten Mobile Controls
- Suitable for all companies which develop or operate their own mobile applications
- Testing time: 1-3 weeks depending on the complexity
Social Engineering
- The best way to verify security awareness in your organization - it exploits the human basic nature - altruism, greed, the need to help
- Depending on the project we plan multiple scenarios, many of them are 100% successfull
- Internet Social Engineering - usually customized phishing (spearphishing) when we use publicly available information
- Phone Social Engineering - with Caller ID spoofing it works very often
- Physical Infiltration - bypassing physical obstacles in order to get the physical building, offices and customer's data
- Red Teaming is a combination of Social Engineering and Black Box penetration tests
Thanks a lot for your attention!