Cobra Kai's Plan to The Cloud

Considerations For Proposal
- Availability: Customers have access to the services
-
Resiliency: if one server goes down, the entire website doesn't go down
- Requires Redundancy
- Secure: no one will successfully DDOS or get access to sensitive information
- Speed: Customers can access information quickly

Proposed Architecture
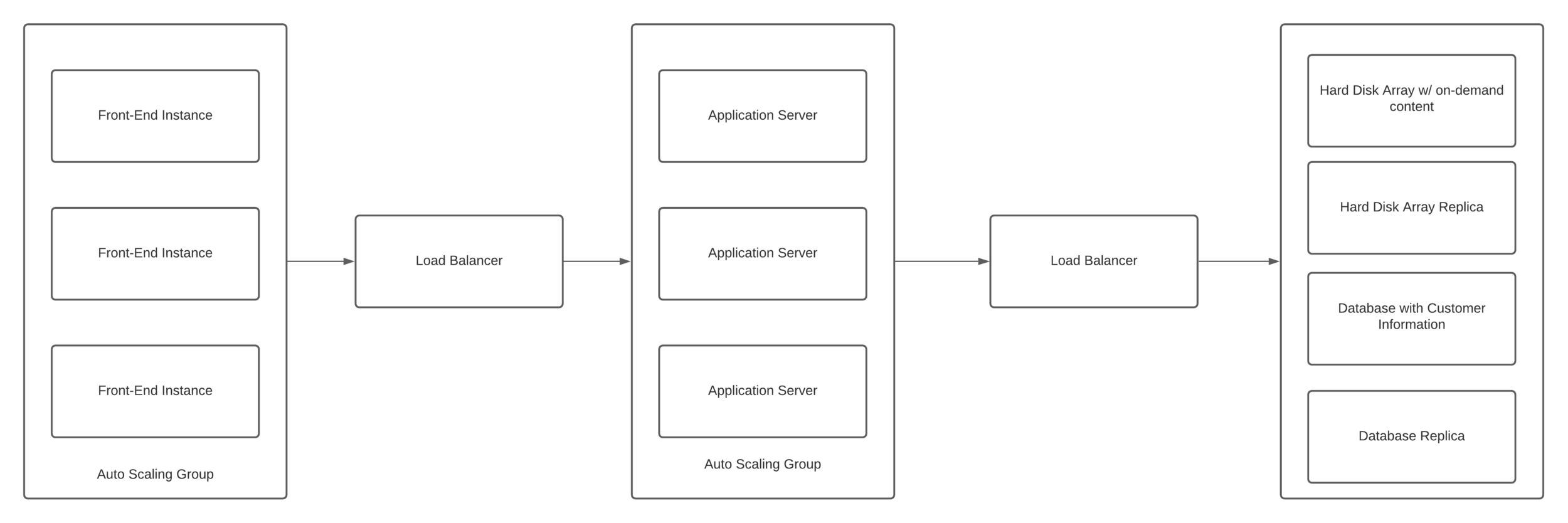
Proposed Architecture - On AWS

- Front End And Application Server: EC2 Instances
- Load Balancers: Elastic Load Balancers
- Hard Disk Array: S3 Buckets
- Database: RDS or Aurora
Proposed Architecture - Key Features
- Everything is separated by load balancers
- DDOS Protection/Speed
- Front-end and Application Service have Auto-Scaling Groups
- DDOS Protection, Speed, and Cost Savings
- Database and hard-disk array have read-only backups
- Downtime protection

User Accounts/Privileges
- Four different group
- Administrator - Full Privileges - system admin
- Developer - Has administrator access to services he needs (the cloud infrastructure)
-
Technical Executive - Has view access to cloud services
- Primarily to ensure everything is on track
- Non-Technical Executive - Limited access, only has access to services to perform their job
Patching and Backup Strategy
-
Patch At Least Monthly
- Most major updates come out monthly (Windows)
- Balance between being up-to-date and serving customers
- Patch critical infrastructure more frequently
-
Tier-based backup strategy
- Front-End/Application Service - Backup live service monthly, version control source code (GitHub)
- Hard Disk Array - backup weekly (updated frequently, but not as often as the database)
- Database - backup at least daily - Constantly changing with customer data
Additional Architectural Measures
- Encrypt user data at rest - especially sensitive PII
- Easy Options on most cloud providers
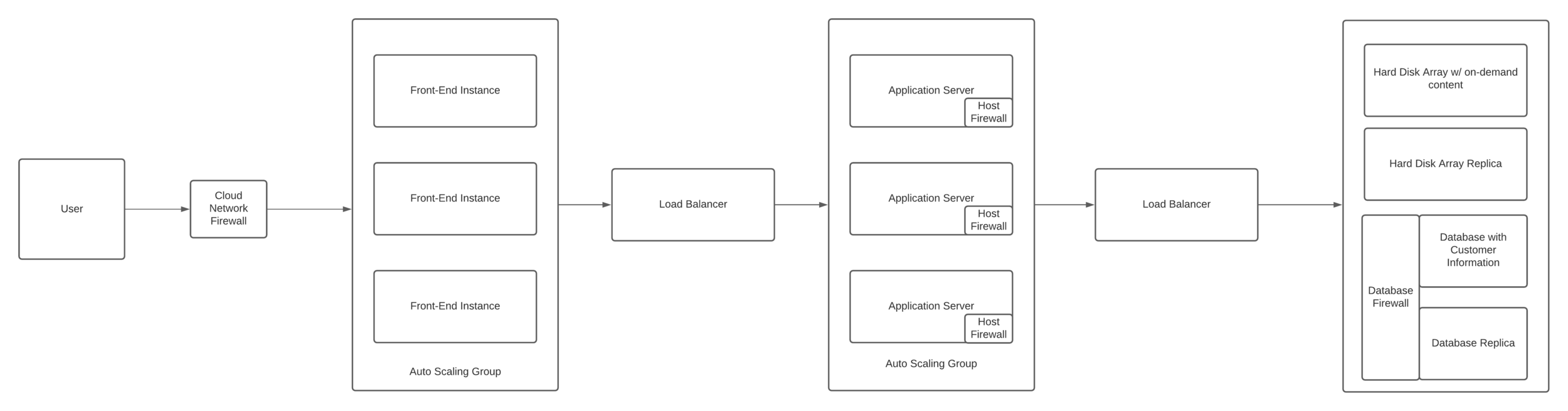
- Add network and host-based firewalls
- Can help protect against DDOS and application-based attacks like SQL injection
- Add logs to both the application components and cloud dashboard/API
- Security breaches can occur in both the application in via the cloud platform
- Know if breached and how it occurred

Example of Architecture with Firewall
Other Policies - DevSecOps
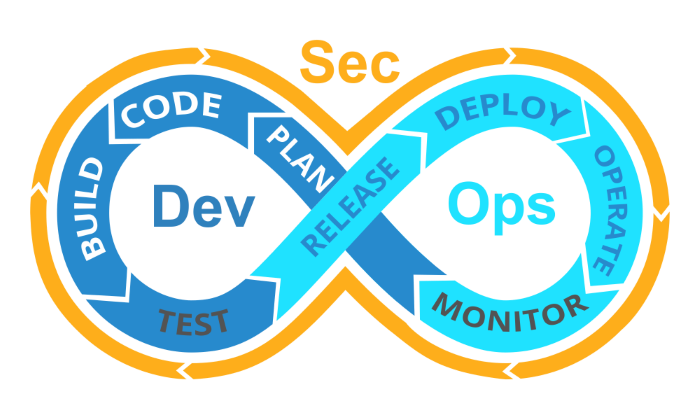
Other Policies - DevSecOps
How is this helpful?
- Adding processes through Development and Operations
- Improves processes for releasing new applications while ensuring the product is operational, and compliant
- Adding DevSecOps will help to ensure PCI Complicance

Other Policies - DevSecOps
- Necessary Components to Implement
- Threat Modeling
- Code Review/Auditing
- Testing
- Monitoring
- Recovery
- Log activity
- Both on the server and on the cloud
- Check for suspicious activity in the application and in the infrastructure
Summary
- Cloud infrastructure will help in three major areas
- Availability of Services
- Increased Security
- Cost Savings
- Policy changes will ensure procedures for updating, patching, and code/infrastructure improvements are standardized
- Combination of architectural and policy changes will ensure compliance (e.g. PCI Compliance

