Cyber101 - Getting into Cyber as a Student

Who are we?
Graduated from UMD in '19 with a BS in CS and '21 with a ME in Cyber Security. Involved in CSEC and helped create challenges for UMDCTF-2019/20/21.
Held various cyber security roles:
- Software Security Engineer at RunSafe Security
- Software Security Engineer for the Department of Defense
Mike - WittsEnd2

Software Engineer - C, Python, & Web
Reverse Engineer/Binary Exploitation
Hobbies: CTFs/Dev Projects, Entrepreneurship, Baseball, Music, Stocks
How to reach me


#include <stdlib.h>
typedef struct Contact {
char discord[15];
char twitter[15];
char github[10];
} Contact;
int main() {
Contact *contactInfo = malloc(sizeof(struct Contact));
contactInfo->discord = "WittsEnd2#9274";
contactInfo->twitter = "@RagnarSecurity"
contactInfo->github = "WittsEnd2";
contactInfo->blog = "https://ragnarsecurity.medium.com/"
return 0;
}
These are my own views/thoughts and do not reflect the views/thoughts of my employer.
What is Cyber Security?
What it is
Cyber security refers to the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. Cyber security may also be referred to as information technology security.

- Policies (clearance, compartmentalization)
- Patch Tuesday
- Vulnerability scanning
- Threat/network scanning
- Research
- Vulnerabilities
- Exploits
- Protocols, cryptography, and obfuscation
What it is not
https://hackertyper.net

Genres (topics) in Cyber
*What you will see frequently in CSEC*
Reverse Engineering
Understanding how something works, whether its software, hardware, or anything else.
Ghidra
IDA Pro
Binary Ninja
Radare2
ptrace/strace
Sysinternals Suite
AnyRun
Cuckoo Sandbox
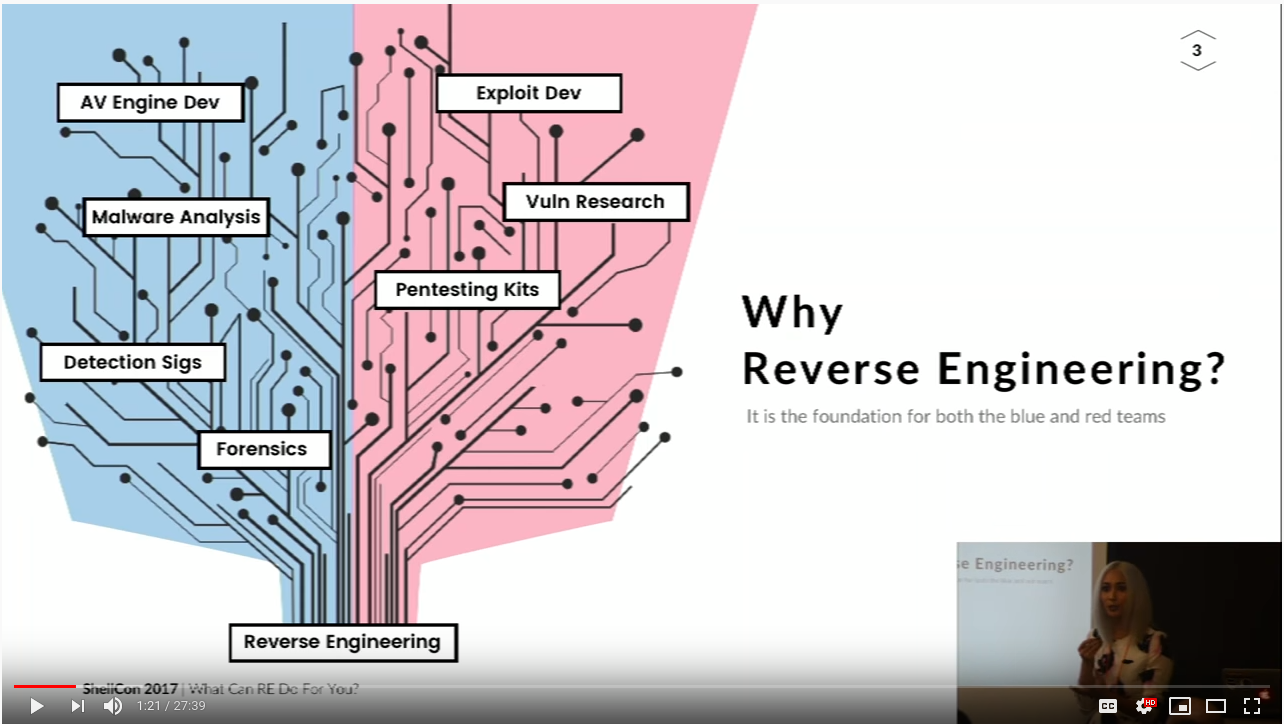
Tools (Software):

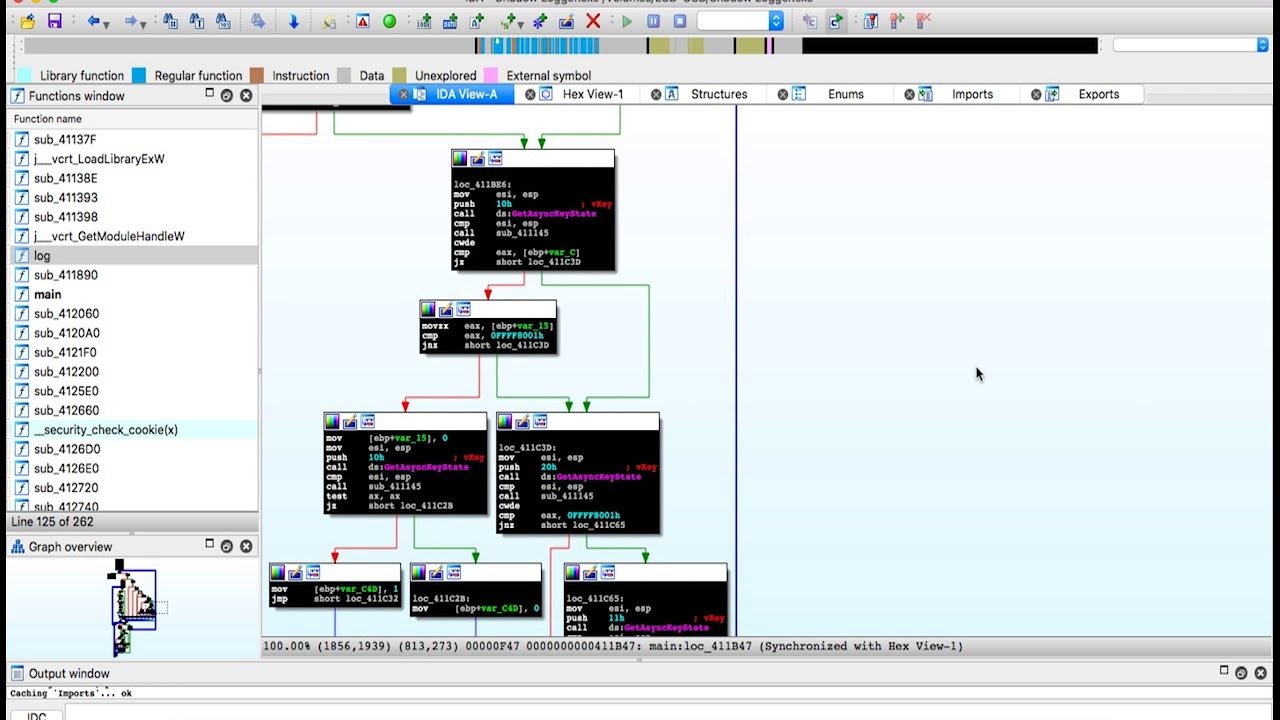
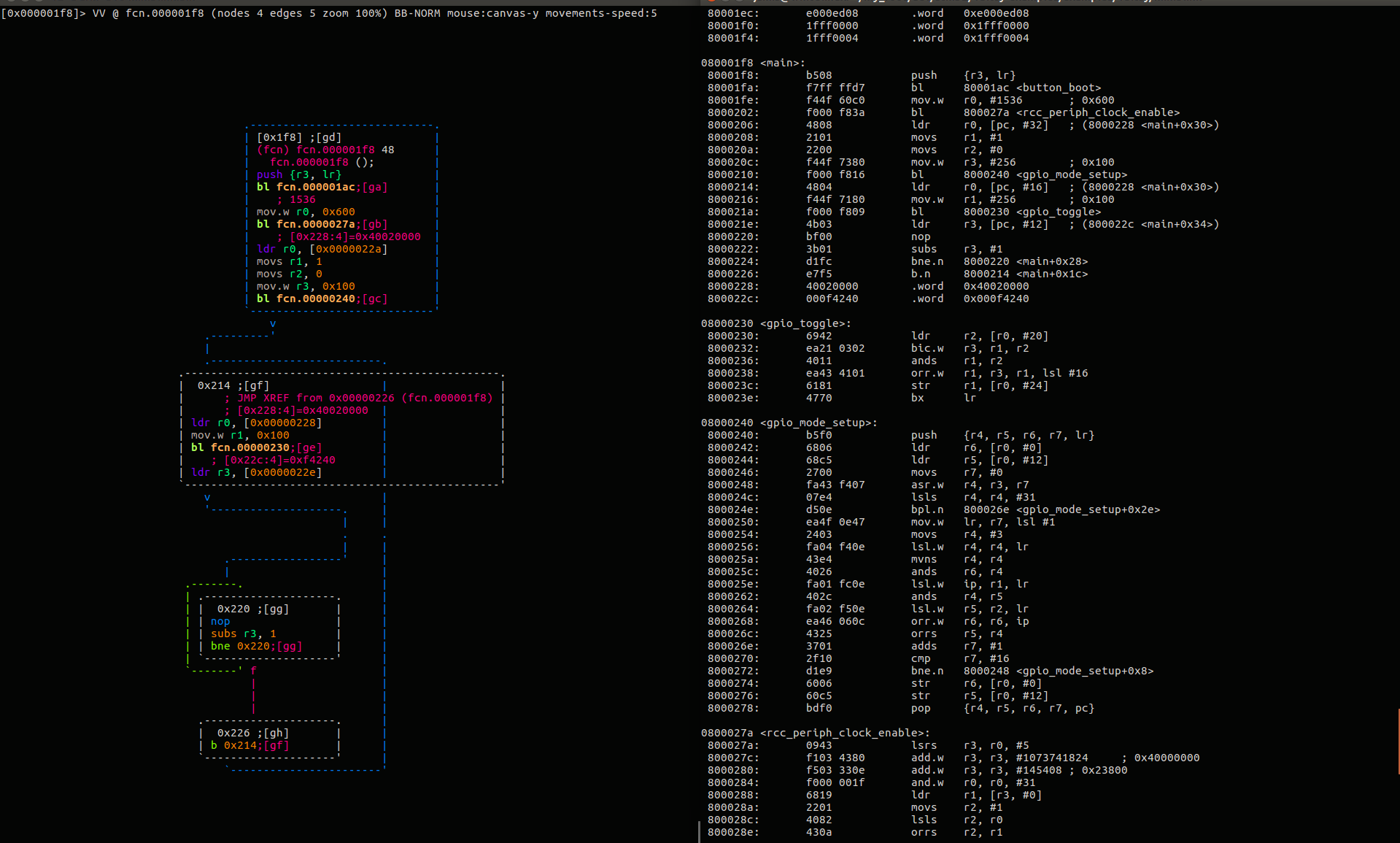


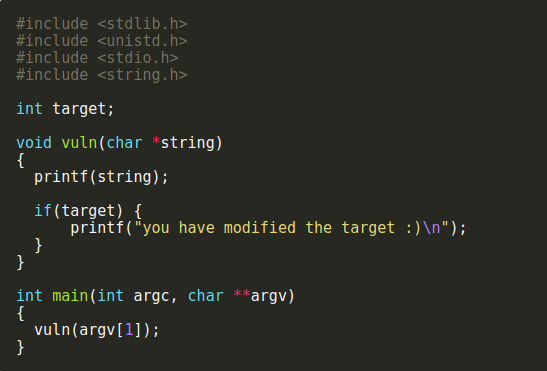
Exploit
Taking advantage of an unintended bugs features
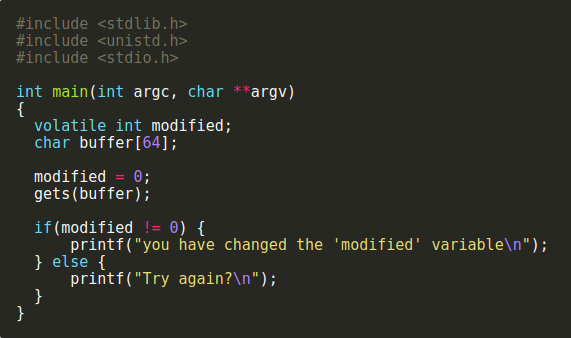
Binary -
Buffer Overflow
String Format
Return Oriented Programming (ROP)
Timing Attacks
Side channel
Web -
SQL Injections
XSS/CSRF
Can require some RE to do successfully.
Examples
Whats the exploit here?
Digital Forensics
Data Analysis - Aggregated Data investigations
Disk - Storage Drive forensics
Memory - RAM/Snapshot forensics
Network - IP traffic forensics
Mobile/Embedded - Niche technology based forensics

Popular Areas
Forensics is uncovering evidence and artifacts like a detective solving a crime scene.
Criminal Investigations
Malware / Intrusion Detection


Volatility
Autopsy
Hardware
Embedded Systems - Internet of Things
Software Defined Radio - RF Hacking
Hardware Hacks - Side channel
Tools/Resources:
- GNU Radio
- Hak5
- HackRF
- Architecture Manuals
- Baremetal &
- etc

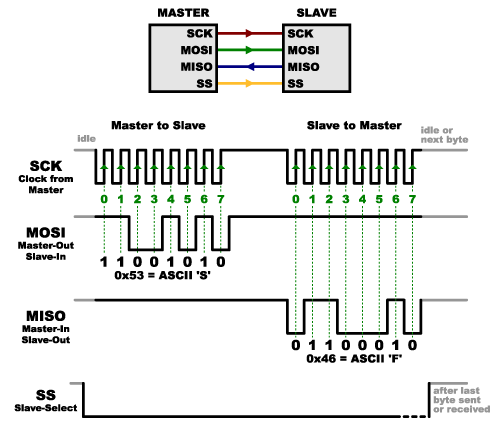
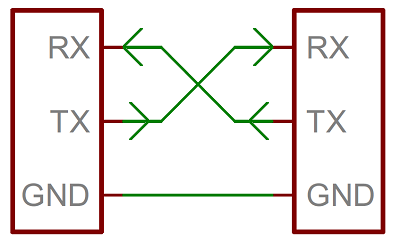
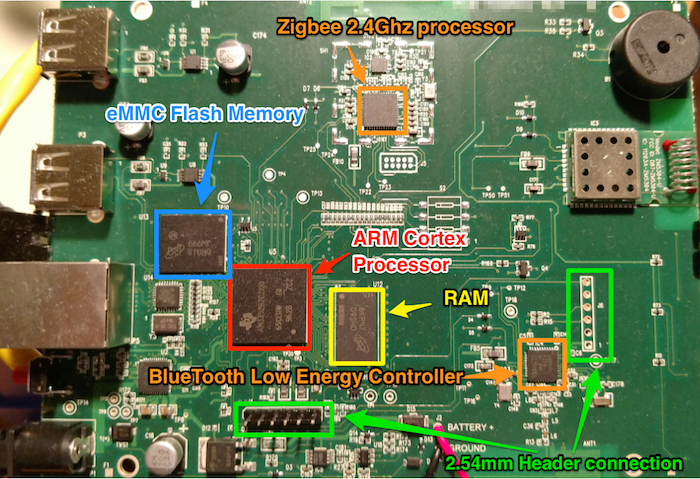
Hardware covers a variety of topics, and as Software folk we generally don't get to play with this stuff.

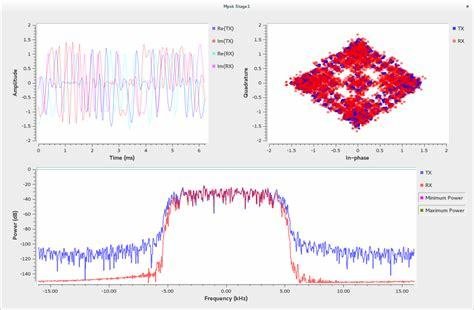
Cryptography
Secure communications in an adversarial setting. In CTFs, usually breaking uses of crypto or broken crypto. (there's a difference!)
Broadly speaking, unless you become an expert in Cryptography, uses of crypto are limited to consulting and designing with secure crypto primitives. (secure primitives does not imply secure communications!)
data = 'CAPTURETHEFLAG'
key = 'A'
encrypted = ''.join([chr(ord(x) ^ ord(key)) for x in data])
print(encrypted)
# '\x02\x00\x11\x15\x14\x13\x04\x15\t\x04\x07\r\x00\x06'



Networks/Web/Cloud
- Web applications
- Industrial Control Systems
- Open Source Intelligence
- Cloud Application Security
Both offensive and defensive, multiple subjects (like exploitation and cryptography) can apply to this field as well.
Tools:
- Burp Suite
- WireShark
- OWASP Zap
- Snort




Policies & Procedures

Policies & Procedures
The Business Side of Cyber Security. This defines the steps to defend an organization from a cyber attack.
- Confidentiality, integrity, availability
- Security Models
- Biba Model
- Chinese Wall Model
- Threat Models - Quantitative vs Qualitative
- Access Controls
- Password Policies
- Identification Policies
- Risk Scoring


Other Topics You May Find
- Malware Analysis
- Crypto Currencies & Blockchain
- Machine Learning & AI
- Endpoint Security
- IOT Security (different than hardware security)
Roles/Positions in Cyber
Information Security Analyst
Utilizes tools (both closed and open source) to defend an organization's information technology system from unauthorized access.
- Creating firewall rules
- Defending endpoints from threats
- Monitoring network traffic & scan for vulnerabilities
- Developing scripts/applications to automate intrusion detection/prevention
- Developing Security Playbooks
Lots of certifications/classes (CISSP, CISA, Security+, etc).
Penetration Tester
Evaluating an organization's security using tools and methodologies hackers (ethical hacking).
- Using software (and sometimes hardware) to determine exploitability of an organization
- Figuring out how deep you can go (and if you can achieve persistent access).
- Writing reports to organizations about your findings.
You are not developing the tools as much as using them.
Certifications:
- Certified Ethical Hacker (easy)
- OSCP/OSCE (Medium/Hard)
- LPT from EC Council (Medium)
Security Researcher
Finding new vulnerabilities/zero-days in existing system.
- Technology Companies
- Google Project Zero
- Academia
- Government - LTS
- Startup Companies
This is one of the most difficult jobs to do as it requires in-depth technical knowledge.

Security Software Engineer
Developing new technologies to protect information security systems.
Diverse skill-set:
- Low-level: C/C++ and Rust
- Web: JavaScript Python
- Databases: SQL/NoSQL
- Network Based: Scripting
Technology companies, government, and startups generally are looking to hire for this kind of talent


Non-Technical Role (Management/Auditors)
Develop, implement, and audit policies and best practices to protect an organization's technology. Extremely broad set of responsibilities.
- Authentication policies (e.g. single sign-on/multifactor authentication)
- Implementing Security Models
- Zero-Trust Architecture
- Access Control Systems
- Working with technological workforce to balance productivity with security
- Budget - convincing executives for more money


Specialized Roles
- Digital Forensics Analyst
- Cryptography Researcher
- Bug Bounty
- Hardware Security Engineer/Researcher
How do you get started?
How you feel right now

Keep participating in CSEC!
Evaluate Goals
- Have specific goals in mind
- Can be narrow or broad
- What do you want to improve on?
- Why do you want that as your goal?
- What outcomes are you hoping to achieve?


Create A Schedule
- Devote several hours per week to practicing
- Make sure there are no distractions
- Why Create A Schedule?
- School & Personal Life takes a lot of time
- You will need to organize your schedule when working
Learn
- Utilize websites and resources designed for structured learning
- Listen to security podcasts and follow security researchers
- Watch YouTube Videos and blog posts
- Reddit & Twitter
- Will discuss specific later



Compete in CTFS
- CTF Competitions put your skills to the test
- Time limit
- Never before seen challenges
- Different designs for CTFs
- Many different categories
- Can be specialized
- Attack/Defense
- HackASat
- Learning opportunity
- UMDCSEC Comp Team Website



Compete in CTFS
- CTFS aren't always easy
- You will spend lots of time feeling like you're struggling to solve a challenge
- READ WRITEUPS!
- You will learn why you weren't able to solve the challenge
- Especially the ones where you spend hours getting no where
- You will learn why you weren't able to solve the challenge



Apply Security to Projects
- Break software that you build
- Use your skills with CSEC
- Website/Infrastructure
- Machine Learning/Data
- Use hackathons as a way to build cybersecurity projects
- Build a set of vulnerable code
- Build tools to help you solve CTF challenges (or penetration testing)
Talk to Professors
- Learn about the research they do and some suggestions regarding research
- Participate in research activities
- Breakerspace
- This can lead to graduate school
Open Source Projects
- Open Source Community is always looking for contributors!
- Join Discord channels and see how you can get involved.
- Examples: Pwntools, Radare2
Generating Ideas for Projects
- How can someone break this software?
- What am I having difficulty with and how can I make it easier?
- What do people seem to be having difficulty figuring out?
- How can I protect this better?
- Why did someone implement this and how can I make it better?
Find a Group of Freinds
- UMDCSEC is a great group of friends interested in Cyber
- Ask questions and share what you are doing
- Ask other friends not in the club if they want to join you with cyber-related projects/events


Resources
General Resources
(The good stuff)
Reddit:
- r/cybersecurity
- r/ReverseEngineering
- r/ghidra
- r/hacking
- r/HowToHack
- r/humblebundles
- r/memoryforensics
- r/RTLSDR
- r/securityCTF
- r/netsec
- r/netsecstudents
- r/LiveOverflow
- r/linux
- r/linuxmemes
- r/linuxmasterrace
- r/Hacking_Tutorials
- r/unixporn #getricingYoutube:
- LiveOverflow
- Hak5
- pwn.college
- RTL Engineering
- Guided Hacking
- Ben Eater
- Computerphile
- DEFCONConference
- Aerospace Village
- Car Hacking Village
- Cheat The Game
- LockPickingLawer
- Suckerpinch
- John Hammond
- Nahmsec
- Zero Day Initiative
- stacksmashingWebsites:
- vx-underground.org
- index-of.es
- repnz.github.io
- corelan.be
- github.com/RPISEC/MBE
- pwn.college
- exploit.education
- hockthebox.eu
- hackthissite.org
- overthewire.org
- tryhackme.com
- ringzer0ctf.com
- ctftime.org
- picoctf.com
- lobste.rs
- 2thi.cc/doc
- nostarch.com
- flaws.cloudProgramming
- Python : Useful for everything
- C/C++ & ASM : Exploit & RE
- Golang & Rust
- Web - JavaScript, PHP, etc.
- Machine Learning: For working with data
Little reason to write in assembly, Lots of reasons to read assembly
- Hackerrank - Great for learning languages fast and practicing your understanding of algorithms. Ex. functional programming, Regex, ML, Bash, C/C++, etc.)
- Side Projects - Websites, Hardware, SDR, IOT, etc.
- If you know how to build it, you can break it!


CTFs
CTFs are a great way to learn and apply skills!

- ctftime.org - Following and keeping up with CTFs
- UMDCTF past challenges - Jeopardy
- picoCTF - Beginner CTF / Jeopardy
- HackTheBox - Pen. Testing / Jeopardy
- RingZer0 - Jeopardy
- Malware-Traffic-Analysis - Forensics based (Wireshark :D)
- Exploit.Education - VMs for learning exploits and privilege escalation
- TryHackMe - Pen. Testing / Jeopardy
Where to start!


Classes
Cybrary - Red Team and Blue Team Cyber
RPISEC-MBE - Intro to Exploit Dev.
ACES-Minor @UMD
pwn.college - Intro to cyber (and ctfs)
Graduate Degree: M. ENG and Computer Science
CMSC389R - Intro to Ethical Hacking
CMSC389J - Intro to Reverse Engineering
Certifications:


Open Source
Git____ is your friend!
CTF Writeups/Source Code
Metasploit
Wireshark
Nikto
NMap
Volatility
angr
Capstone - (not a school project)
BAP - Binary Analysis Platform
Many many more!




Books
-
Ghidra Book - Reverse Engineering
-
Practical Reverse Engineering
-
Practical Malware Analysis
-
Programming Linux Anti-Reversing Techniques
-
Black Hat Python - Development (Pen. Testing)
-
The Hacker Playbook 2 & 3 (Pen. Testing)
-
PoC || GTFO
-
Hacking the Art of Exploitation
-
Shellcoders Handbook
-
Grey Hat Hacking
-
Open Source Intelligence Techniques



Academia
- Research (Network with professors/faculty)
- ACES
- Cyber Security Specialization
- Lots of open source projects are being run by universities as research projects. You can easily get involved by contributing to these projects. Features/Bug Fixes/Documentation are all encouraged!

Internships
NETWORK NETWORK NETWORK
Go to CSEC meetings & meet recruiters (they are here for you)
Pro tips -
Open conversation with... "I'm taking <some class title> and I really enjoyed this project on <topic like bufferoverflows>. Do you guys do stuff like that on the job?"
Ask... "What kind of training/learning opportunities do you have? I love to learn!"
Ask... "Whats the office culture like?" (You'll love your job if you love your coworkers)