Library and System Call
Libc
The term "libc" is commonly used as a shorthand for the "standard C library", a library of standard functions that can be used by all C programs (and sometimes by programs in other languages).
-wikipedia
What is happening when we use printf in our binaries?
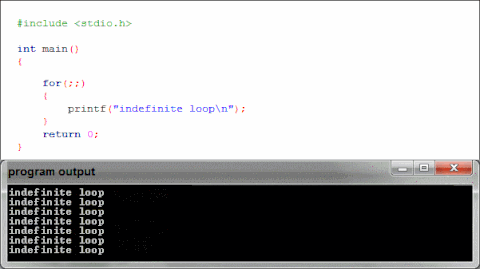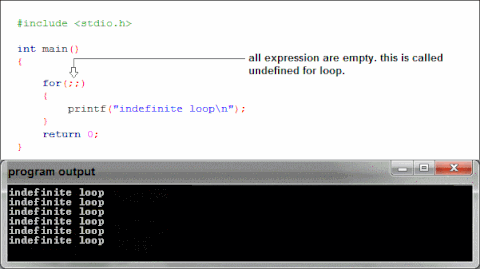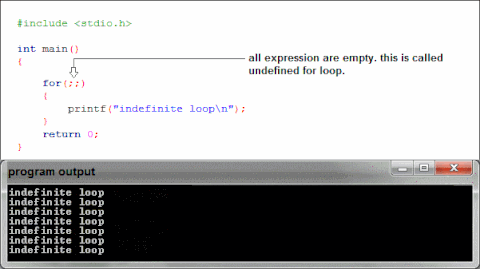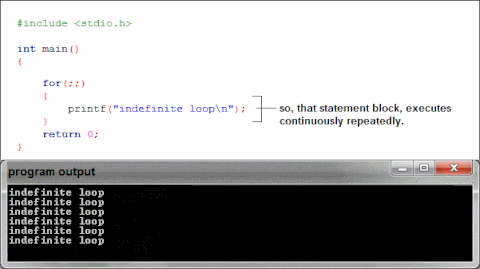
Libc
What is happening when we use printf in our binaries?
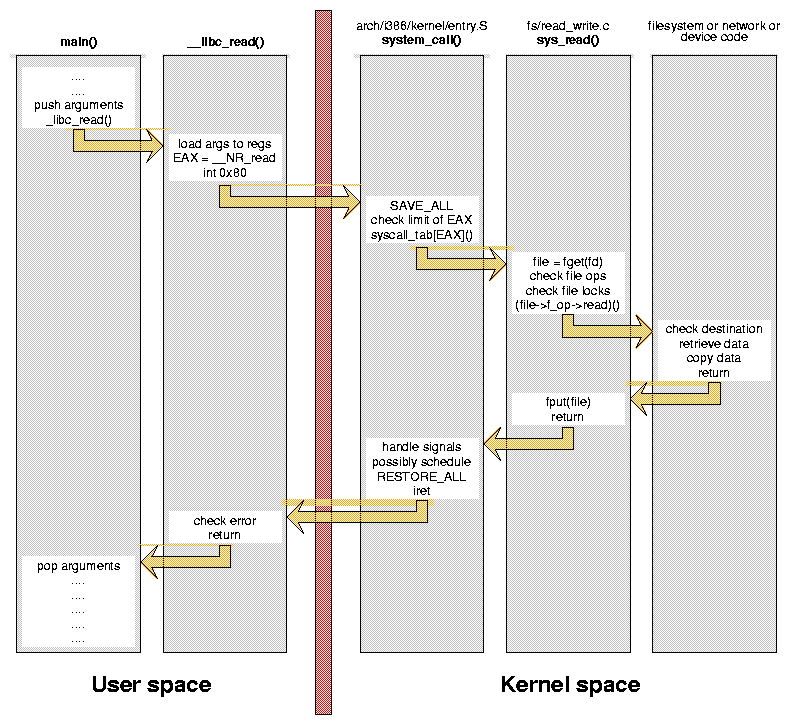
How does text make it to the screen?

printf gets linked to the first instance in the
included libraries of a printf, then printf does its
thing.
Libc to Systemcalls
How does text make it to the screen?

printf, malloc, read, write, etc. are all wrappers for
system calls.
System calls are the process' way of asking for
permission to do something with a resource.
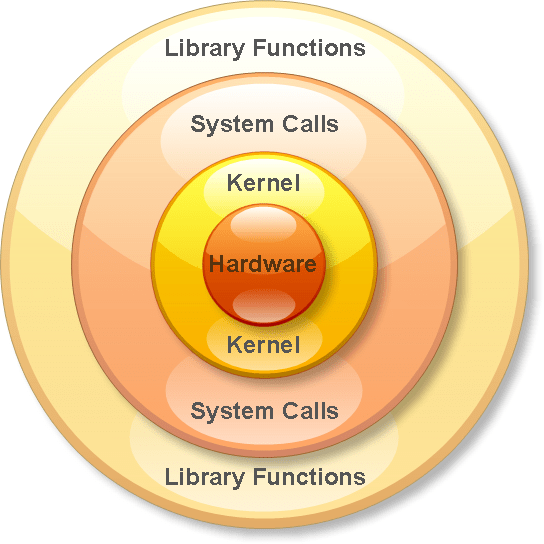
System calls
Syscalls are not standardized on all architectures or Kernels
In Linux, they are interrupts ('int' 32bit or 'syscall' 64bit).
In Windows, depending on the version or architecture, you might see 'syscall' or 'int' or even just 'call'

System calls
What are these 'resources'?
Resources are anything the computer can do, reaching devices, printing to terminals, key presses, etc.
In windows, resources are called handles, and everything is an object. More wrappers for syscalls.
System calls
Simple in assembly:
; ----------------------------------------------------------------------------------------
; Writes "Hello, World" to the console using only system calls. Runs on 64-bit Linux only.
; To assemble and run:
;
; nasm -felf64 hello.asm && ld hello.o && ./a.out
; ----------------------------------------------------------------------------------------
global _start
section .text
_start: mov rax, 1 ; system call for write
mov rdi, 1 ; file handle 1 is stdout
mov rsi, message ; address of string to output
mov rdx, 13 ; number of bytes
syscall ; invoke operating system to do the write
mov rax, 60 ; system call for exit
xor rdi, rdi ; exit code 0
syscall ; invoke operating system to exit
section .data
message: db "Hello, World", 10 ; note the newline at the endLibrary calls
1. Linker sets up the Global Offset table in memory (.got)
2. When the function is called, we use an offset plus the .got address to call the correct function in the .plt (process linkage table).
3. From the linked function, we jump into the shared object to execute.
What does this all mean for attackers?
