

About Me
-
Creator of "VyAPI – A Modern Cloud Based Vulnerable Android App"
-
Application Security Analyst at Appsecco (@appseccouk)
- Chapter Leader at null Bangalore (@nullblr)

The Goal
To provide Android security enthusiasts a platform to practice hacking a cloud-based vulnerable Android app
Your Takeaways
- What is VyAPI
- How to setup your personal VyAPI test environment
- OWASP - Mobile Top 10 2016 in VyAPI
- Built-in features for you to explore
- Reference materials
What is VyAPI?
- It's a cloud based vulnerable Android app built using modern technologies like AWS Amplify, Amazon Cognito, Glide, Room Persistence, etc.
7 steps to get started
#1: Install Required Softwares
- Node.js
- NPM
- Amplify CLI
- AWS CLI
- Android Studio
- Android Emulator
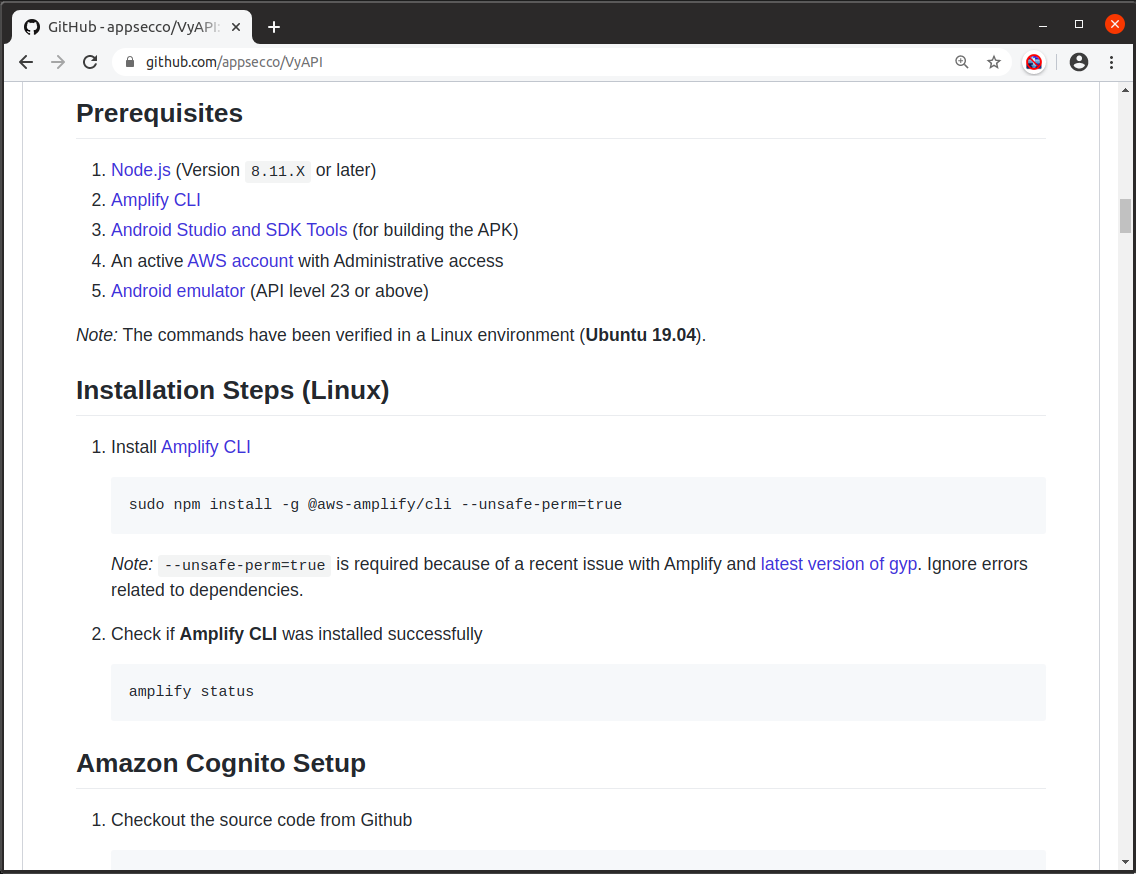
#2: Configure Amazon Cognito
$ git clone git@github.com:appsecco/VyAPI.git
$ cd VyAPI/

#3: Create Android Emulator

#4: Run VyAPI
#5: Register a user

#6: Login
#7: Start Hacking

OWASP Mobile Top 10 2016 in VyAPI
M1-Improper Platform Usage

A Vulnerable Activity
dz> run app.activity.start --component com.appsecco.vyapi com.appsecco.vyapi.MainActivityA Vulnerable Service
dz> run app.service.start --component com.appsecco.vyapi com.appsecco.vyapi.service.PlayMusicServiceSQL Injection Through Content Provider
dz> run app.provider.query content://com.appsecco.vyapi.ContactDBProvider/contacts/ --projection "*"M2-Insecure Data Storage

M3-Insecure Communication

Can you intercept the secret SMS?
M4-Insecure Authentication

M5-Insufficient Cryptography

Where is the encryption key?
M6-Insecure Authorization
First, find a Cognito Identity Pool ID
Can unauthenticated users access sensitive AWS services?
E.g., us-east-1:f0e6168e-4865-4890-97e5-489cd6106g83
Is access to unauthenticated identities enabled?

Use Boto 3 to fetch credentials for an identity pool ID

Access Key, Secret Key, and Session Token

Use enumerate-iam Python script

Which of the AWS services could be accessed by unauthorized users?

M7-Poor Code Quality

Vulnerable Broadcast Receiver
dz> run app.broadcast.send --action com.appsecco.vyapi.Broadcast --extra string new_file_name dz_file1 --extra string temp_file_path etc/hosts
dz> run app.broadcast.send --action com.appsecco.vyapi.Broadcast --extra string new_file_name ../../../../../../../../../../sdcard/Android/data/com.appsecco.vyapi/files/Pictures/dz_file2 --extra string temp_file_path etc/hostsM8-Code Tampering

M9-Reverse Engineering


Sensitive File in APK Bundle

M10-Extraneous Functionality
What's Visible
What's NOT Visible
Hands-On Training Material
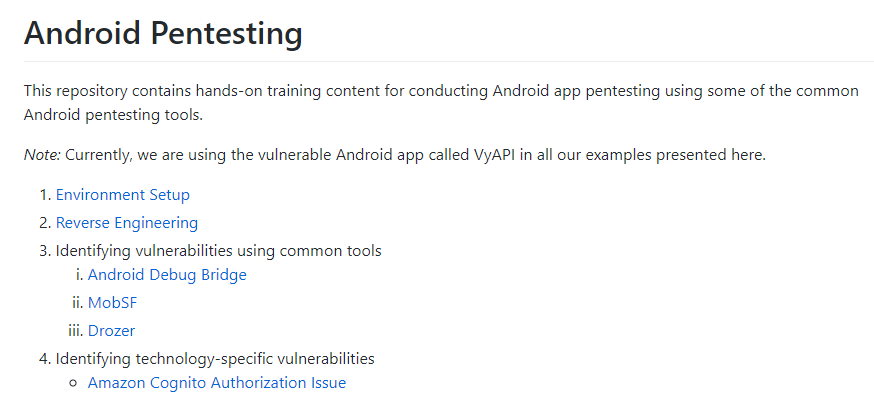
Built-in features for you to explore






Summary
VyAPI is a cloud-based vulnerable Android app for Android security enthusisats.
To get started, you need to
- Setup Amazon Cognito login using Amplify
- Explore security misconfigurations in cloud setup
- Explore Android app specific vulnerabilities
- Use your favorite tools to exploit the identified vulnerabilities

nullcon.net
@Winja_CTF

References
- VyAPI Codebase - https://github.com/appsecco/VyAPI
- Android Hacking in 7 Steps - https://slides.com/riddhishreechaurasia/breaking-an-android-app-in-7-steps#/
- Android Pentesting Training - https://android-pentesting-at-appsecco.netlify.com/
- Internet-Scale analysis of AWS Cognito Security - https://andresriancho.com/internet-scale-analysis-of-aws-cognito-security/
- OWASP - Mobile Top 10 2016 - https://www.owasp.org/index.php/Mobile_Top_10_2016-Top_10
- Amplify CLI - https://aws-amplify.github.io/docs/cli-toolchain/quickstart
References
- Boto 3 - https://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/cognito-identity.html
- Amplify - https://aws.amazon.com/amplify/faqs/
- Amazon Cognito - https://aws.amazon.com/cognito/
- Glide - https://bumptech.github.io/glide/doc/getting-started.html