Web 3.0
Smart Contracts could be leaky
Abstract
This talk is about sharing experiences with you about things that worked and that did not work as expected, when I wrote my first Smart Contract and deployed it to a "decentralised" server.
- How I leaked the sensitive flag{}, and,
- what was the fix I applied to prevent leaking sensitive information?

Takeaway
- Web3.0 is interesting
- Integer overflow is still possible, but exploitation isn't possible by standard means
- Information leakage is a real problem
About Me
Current: Freelancer History: C/C++ Secure Coding Instructor, Security Analyst Consultant, Scrum Master, Automation Engineer, Quality Engineer
At Leisure: Developer, Speaker/Trainer, Community Volunteer for Winja
Social Media:
-
Twitter (_riddhishree)
-
GitHub (riddhi-shree)
-
Medium (@riddhi-shree)
1. Integer Overflow

IntegerOverflow.sol
...
function sellArticle(string memory _name, string memory _description, int256 _price) public {
seller = msg.sender;
name = _name;
description = _description;
price = uint256(_price);
if(int256(balances[seller]) - _price >= 0) {
balances[seller] -= price;
}
}
...
Integer Arithmetics

Text
https://valid.network/post/integer-overflow-in-ethereum

-
Addition of 2 unsigned integers can overflow to a smaller value?
-
Subtraction of 2 unsigned integers can underflow to a greater value?
True or False
Contract Address
$ npx hardhat run scripts/deploy.js --network rinkeby
Compiled 1 Solidity file successfully
Deploying contracts with account: 0x231E671534B96936B48D7C2b9455d8E7FfD21543
Account balance: 1838357085301522520
IntegerOverflow address: 0x39F5bCa98883609378f850780C46e2161B419A96
ABI

React Frontend


...


Overflow Exception!
What Happened?
"In Solidity 0.8, the compiler will automatically take care of checking for overflows and underflows."
Reference:
https://ethereum-blockchain-developer.com/010-solidity-basics/03-integer-overflow-underflow/

2. Data Privacy

https://docs.soliditylang.org/en/v0.4.24/contracts.html#visibility-and-getters


Smart Contract
Contract Address: 0x150a318b4C9e8d66c1B3557bAFA497E485fEf8D2
-
Go to https://goerli.etherscan.io
-
Search contract address:
0x150a318b4C9e8d66c1B3557bAFA497E485fEf8D2 -
Locate "Contact Creation" transaction
-
Click on corresponding "Txn Hash" value
-
Select "Click to see More"
-
Locate "Input Data" section
-
Select "UTF-8"

How do I create Web3 capture-the-flag challenges, if the secret flag just can't be hidden from the world?
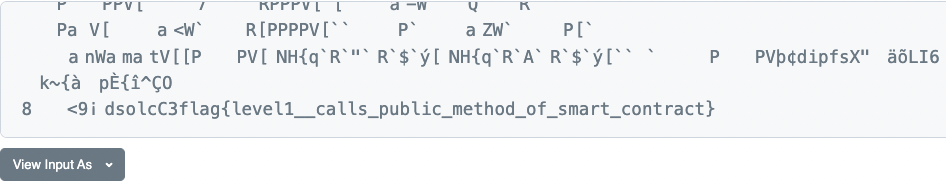
No such thing as Privacy?
Jugaad
string(abi.encodePacked(...))

New Contract Address: 0x130ccC606C9aeF1235694a2Ae6cbdc7cee4b7912
-
Go to https://rinkeby.etherscan.io/
-
Search contract address:
0x130ccC606C9aeF1235694a2Ae6cbdc7cee4b7912
-
Locate "Contact Creation" transaction
-
Click on corresponding "Txn Hash" value
-
Select "Click to see More"
-
Locate "Input Data" section
-
Select "UTF-8"
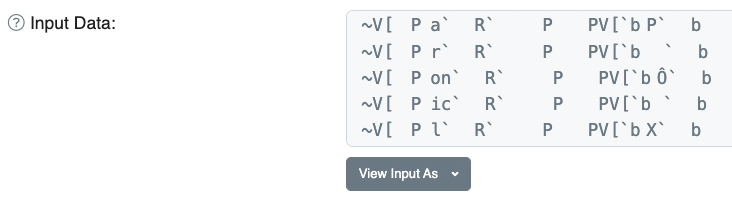

The secret flag is not readable (just like that) by the world, anymore!
3. Capture-the-Flag
Contract Address: 0x5Ae52B13d270Cb8D06DCF188657B335A142E13C5
Network: Goerli
Can you solve this?
