No place is safe
General Information Security defense
Prepare your weapon
Security Consultant
Defense / Forensic / Analysis
SOC "Tier All" Engineer
"Monitor"
Free and Open
ethen @ VSSecurity.com.tw
Ethen @ VSSecurity
Your Enemy is trying to DESTROY your faith


Who
WHO?
Government
Big Power
Lots of Money
Hacker army
Monitoring everywhere
XKeyScore
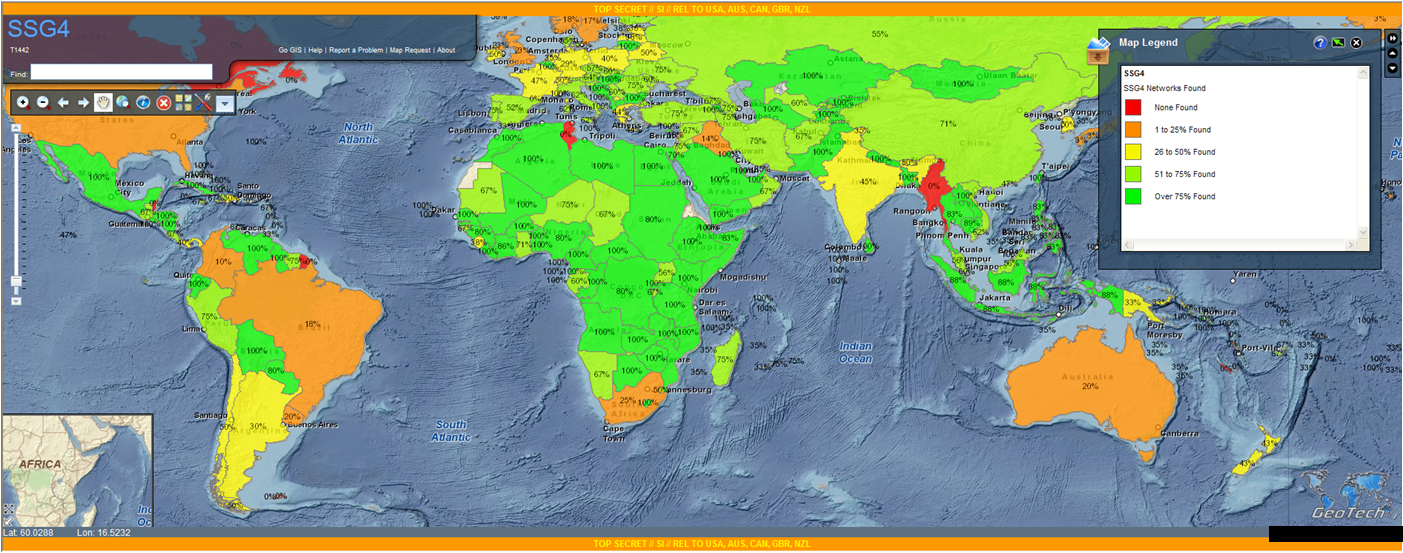
We even know themselve better then they do“
Employee in NSA
Big Company
Profit oriented
Hire hackers
Advertising
User tracking = profit
Backed by Government
WHY?
In his way
©Undertale by Toby Fox
Freedom of speech
Human rights
Privacy
Nature conservation
......
HOW?
People think hackers do...
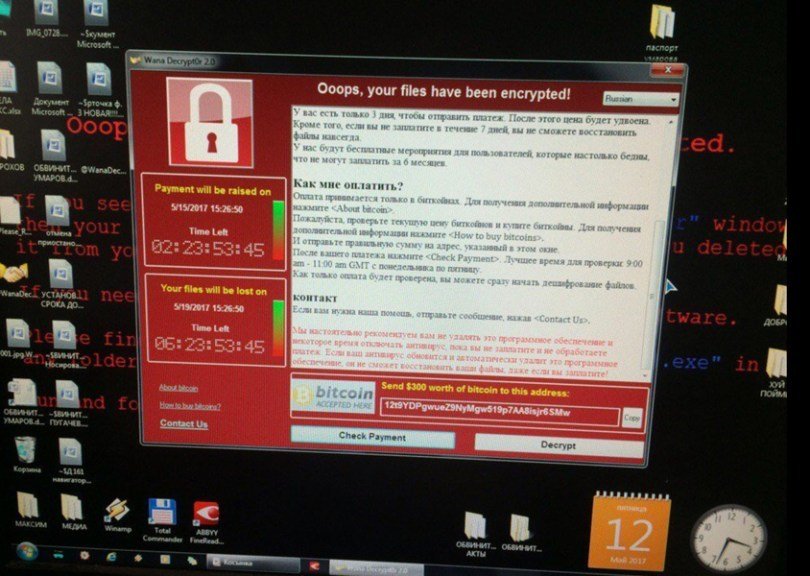
Oh thats cute
What you talk,
What you think,
What you have,
What you prefer,
What you want,
What you do,
What you believe,
What you trust,
Where you are,
When you have a date....
Modify what you write,
Trash your reputation,
Screw up your plan,
Fake your identify,
Playoff your relationship,
Trapped you in law,
Flush your property,
Forge your experience,
Affect your choose,
Change what your believe...
What hackers CAN do
Hacking into your system
Hide in the shadow
Steal Data
change the result
Not killing YOU
But your FAITH
your Partner
your Organize
Things you Protect
Time to arm yourself
For the future we trust
BASIC
Know your enemy
China or America?
or....BOTH?
Know the Value
can't be lost
can't be known
Valuable
Dangerous
Something
to your enemy
Manage your RISK
Then
WHAT might happens?
COST if it happens?
how much CHANCE?
Control Level
They can control what I do
They can control what I see
They know where I go
They know me but hard to trace
They didn't notice me
Anything they take is harmless
How much cost should I pay for this RISK?
Rating your DATA
Public
Sensitive
Private
Critical
three domain
Network
Device
Internet Service
Network
Street to street, land to land
You can't control
Monitoring / Fake Info everywhere
Encryption is important
Device
Your Kingdom, your responsibility
Can control your LIFE
SPYs (Malware) is waiting
Internet Service
put your DATA to the company/Gov
Your personal data is their business
Hard to refuse
Where do ATTACKs comes from?
Network
Malicious / Monitoring Network
Public network
Non-secured network
Device
Untrusted Installation source
Non-patched Operation System
Old un-managed system
Public Service
Web browsing
hacked partner/family
Advanced Persistent Threat, APT
Internet Service
Data selling
Non-secured WebSite / APPs
Hacked by some one
Government take data without notification
of course..
Social Engineering
USB
Operation System
Update Service
Repair service
....
BASIC Rule
You should keep in mind
unless checked by yourself
Trust nothing
Incoming call? new friends?
free WIFI? USB left on parking lot?
A secret between more than two is no secret
Keep your info
fast and diversity
Some method to keep secure
Network
Choose reliable network
Use VPN when using un-trusted network
Choose your ISP carefully
Firewall is basic equipment
Trust only if...
Device
keep your device CLEAN
keep device UP-TO-DATE
Device
Choose right vendor
Only install APPs you TRUST
get files form OFFICIAL way
Cautious of PERMISSION you give
Password
Device
keep
Personal device / accounts
PERSONAL
BadUSB, thunderbolt DMA
Device
Patch as fast as possible
subscribe Security MailList / news
good password policy
Know your own device
Internet Service
the REPUTATION of the service provider
notice how they handle your data
read Agreement carefully
Internet Service
choose the info you give
use independent idetification & password
login notification
2 step authentication
build your own service
Some tools you need
VPN
Commercial VPN Service?
Tor?
Buy a VPN router?
Build your own?
Caution: never use PPTP again!
Proxy is not private!
Choose VPN Vendor
Double Encrypt in tunnel
Amazon has VPN service
some vendor can blocking traffic if VPN is not connect
VPN box
data leakage between network switching!

https://netaidkit.net
VPN box
or build your own

https://pi-hole.net/
Communication
Signal / Telegram
OpenPGP Email security
Encrypt your file before send
Build your own
prism-break.org

Thanks
Any Question?
ethen@aurigasec.com
Question
you might not know
China software
America Device
USB / Thunderbolt / 1394
Device Clone is easy
a pic / web browsing can hack you
hackers spread backdoor with cracker
you might not know
Local network can do a lot
Fake WIFI / Cellular station is common
Updating service is a official backdoor
You don't have to provide anything
Most question
Mass surveillance by the government
Targeted attack from the government
Monitoring stage
Collecting data
Associate data to human
Ranking
Drill down by human
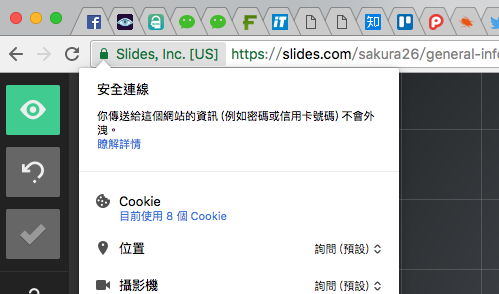
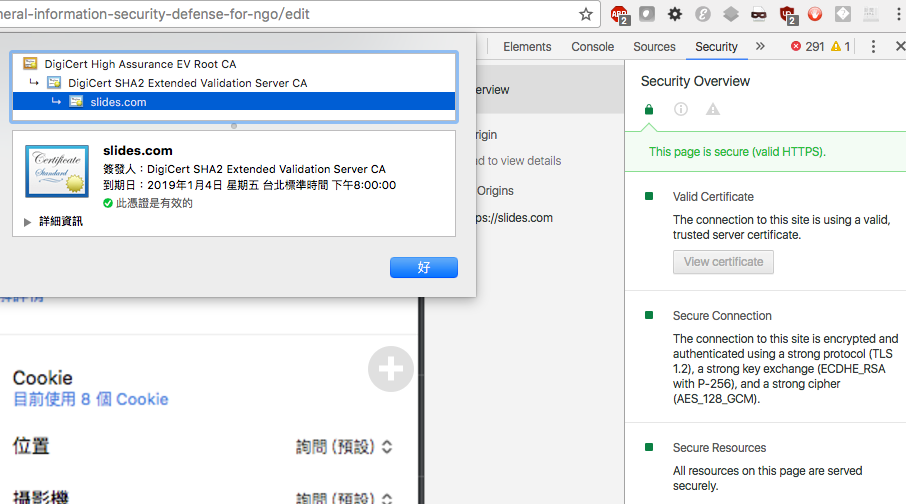
Secure WebSite?
HTTPS
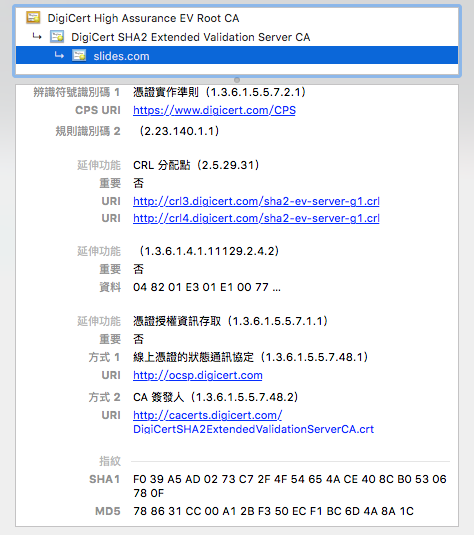
Check certificate
plain-text password?
Read EULA
WTF
Title Text
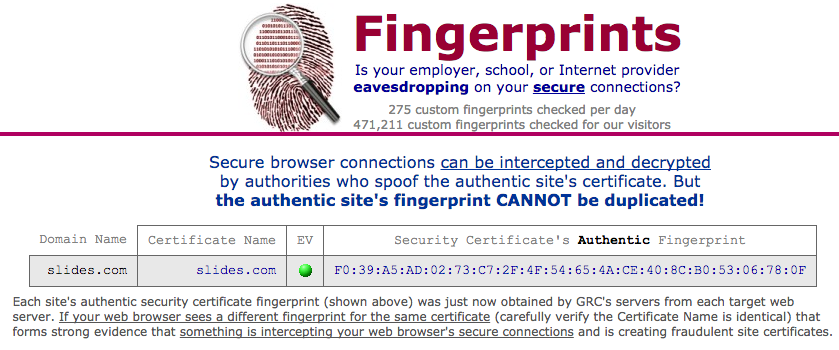
https://www.grc.com/fingerprints.htm
Browsing secure
NoScript
uBlock
Update!!
Know the URL
Seal web browser/Mail in VM
Travel?
prepare spare VPN
say no to free USB charger
don't leave your device alone
FaceID / TouchID
Travel to CHINA?
No safe network
prepare lots of VPN spare
prepare non-VPN solution
No China 3C device
Never buying 3C in china
don't bring un-necessary sensitive data
Travel to America?
hold the sensitive data, even government take the device and password from you
The most powerful tracking in the world
Device Security
Never give your pin code to others
Full device encryption
If possible, don't bring your own device
pack your data in encrypted tar
Storage safity
offline storage
if use NAS, store in encrypt disk and isolated network
RAID or Duplicated backup is needed
NEVER sync sensitive data to cloud!
Self-destruct button

https://github.com/sakura26/killallbtn
more VPN
All VPN is illegal in China!
TOR is trackable by NSA!
TOR is blocked in CHINA!
SSH is a good alternative, but too geek
OpenVPN is great, but blocked in CHINA
SSLVPN is good, but not stable in CHINA
L2PT is easy to identify
build your VPN
ask your MIS
many Router have OpenVPN Server
rent a VPS as a server
Meraki
*don't forget sealing your VPN guest in isolated network
Non-VPN Solution?
http://anonymouse.org/anonwww.html
http://www.spammimic.com/
http://anonymouse.org/anonemail.html
https://10minutemail.com
https://protonmail.com/
Anti-tracking?
less data, less tracking
Break the connection
Hidden in crowd
multiple accounts / device
annoy with Noise
another option: totally open
Web Tracking?
incognito window not helping you actually
choose browser carefully
choose your plugin carefully
eat cookies
know the URL
change IP (proxy/VPN)
Data processing
Release data to the world
Hide data in non-sensitive Info (Steganography)
Hide data in your device
Using public device?
if possible, get your own device
or, use VM to create your env
or, create tmp id with tmp mail
encrypt data and put to public space
get data back when you are in safe
Using public device?
Use TAILS Linux or something else
https://tails.boum.org/
VM can bypass many things....