It is a process that ensures and confirms the identity of a person or device - identity that is immutable across all apps in our system.
What is authentication?
Examples:
- User: User ID, Email, Last Name, etc.
- Device: Device ID, any immutable property
We’ve implemented a centralized server that we call Identity Provider which is based on OIDC to provide identity.
How do we authenticate clients at ITH?
A client is an application and, based on their ability to maintain the confidentiality of their client credentials we classify them as:
- Public: User-agent-based Applications or Native Applications (e.g. TC frontend, Desktop/Web PAS)
- Confidential: Web Applications or APIs (e.g. FMS Web Portal, Kafka Consumers, Imaging API)
A good developer is like a werewolf,
afraid of silver bullets
Use cases & Solutions
- Server to Server Communication (Client Credentials)
- Browser-based Applications (Auth Code Flow)
- Web-Applications (Hybrid)
- Native Applications (Auth Code Flow)
- IoT Devices (Mutual TLS)
Server-Server

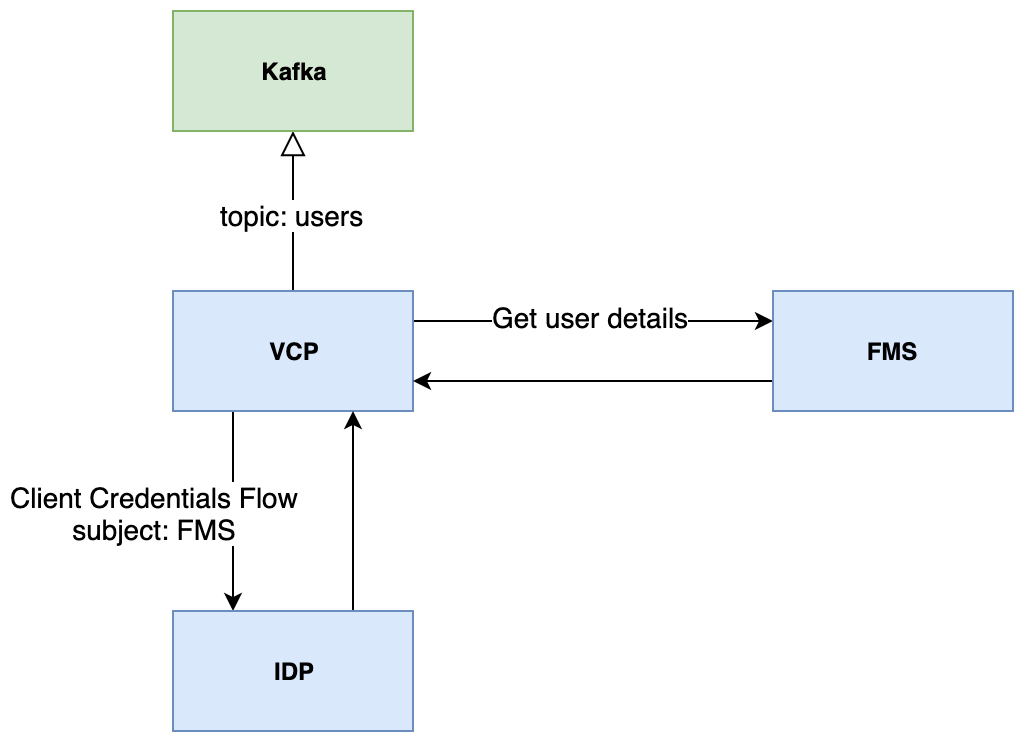
Pub/Sub
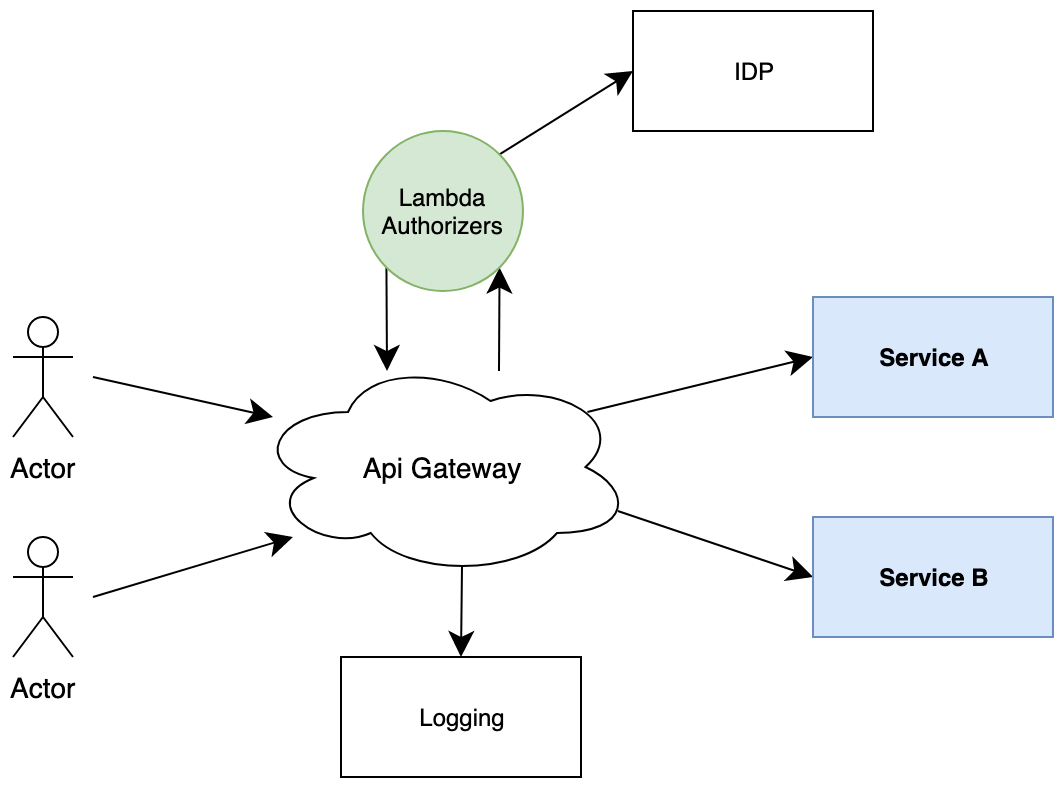
API Gateway
Principle of least privilege
every module must be able to access only the information and resources that are necessary for its legitimate purpose
Delegation

Best practices for Clients
- Don’t use the Password Flow
- Don’t use the Implicit Flow
- Access token credentials must be kept confidential in transit and storage, and only shared among the authorization server, the resource servers the access token is valid for, and the client to whom the access token is issued.
- Access token credentials must only be transmitted using TLS.
For interactive (requires user action) clients:
- Use PKCE
- Use State and Nonce parameters
- For confidential clients, clients should always use a secret
- If the token leaves the company infrastructure (e.g. to a browser or a mobile device), use reference tokens to be in complete control.
- Keep the tokens small
Discussion - Questions - Comments