Title Text
Digital Currency & Blockchain
Lecture 7
Privacy & Security Considerations in Crypto


- Wallet Types
- User Security & Key management
- Privacy
Content
- Researching crypto since 2012
- Advisor to multiple crypto startups
- Cofounder Blockchain Slovakia
- Cofounder of Paralelna Polis
- CTO, CIO @ Fumbi
- Advisor @ Vacuumlabs
- Author of Coinstory
- Cofounder of Cork Protocol
Contact:
david@coinstory.tech
About me
- Bitcoin ATM - cash, anonymous, fast and expensive
- Localbitcoins, Vexl (app) - similar but face to face
- Online Broker (Fumbi) - fast, easy, higher fee
- Bitcoin Exchange (Kraken) - cheap, big volumes, verified
How to get crypto
- 12-24 words
- Recovery and Backup
- Out of 2048 words (BIP39) - possible combinations - 2048^12 = 2^132
- Multiple languages (EN, FR, CZ, IT, ES, JAP..)
- "Brainwallet"
- Bitcoin Wiki on Seeds
-
Everything about Address Generation
- Example:
witch collapse practice feed shame open despair creek road again ice least
Seed




Base58
- Base58 is a set of characters you can use to represent big numbers in a shorter and more user-friendly format.
- The more characters you have in your base, the less of them you will need to use to represent big numbers. So the bigger your base, the shorter your “number” can be.
- Because 58 is the number of characters you are left with when you use all the characters in the alphanumeric alphabet (62), but remove all the easily mistakable characters like 0, O, l and I.

BTC address
-
P2PK - Pay To Public Key
- Original format
- Privacy issues and waste of blockspace
-
P2PKH - Pay to Public Key Hash
- addresses that start with "1"
- when spending from this address sender needs to reveal PK
-
P2SH - Pay to Script Hash
- An elegant solution for more complex unlocking scripts (timelock, multisig)
- hides script (created by the receiver), saves space & fees,
- Addresses that start with "3"
-
Bech32
- Native Segwit - the latest form of addresses
- saves block space
- start with "bc1"
Types of Wallets

Paper wallets:
Paper Wallet


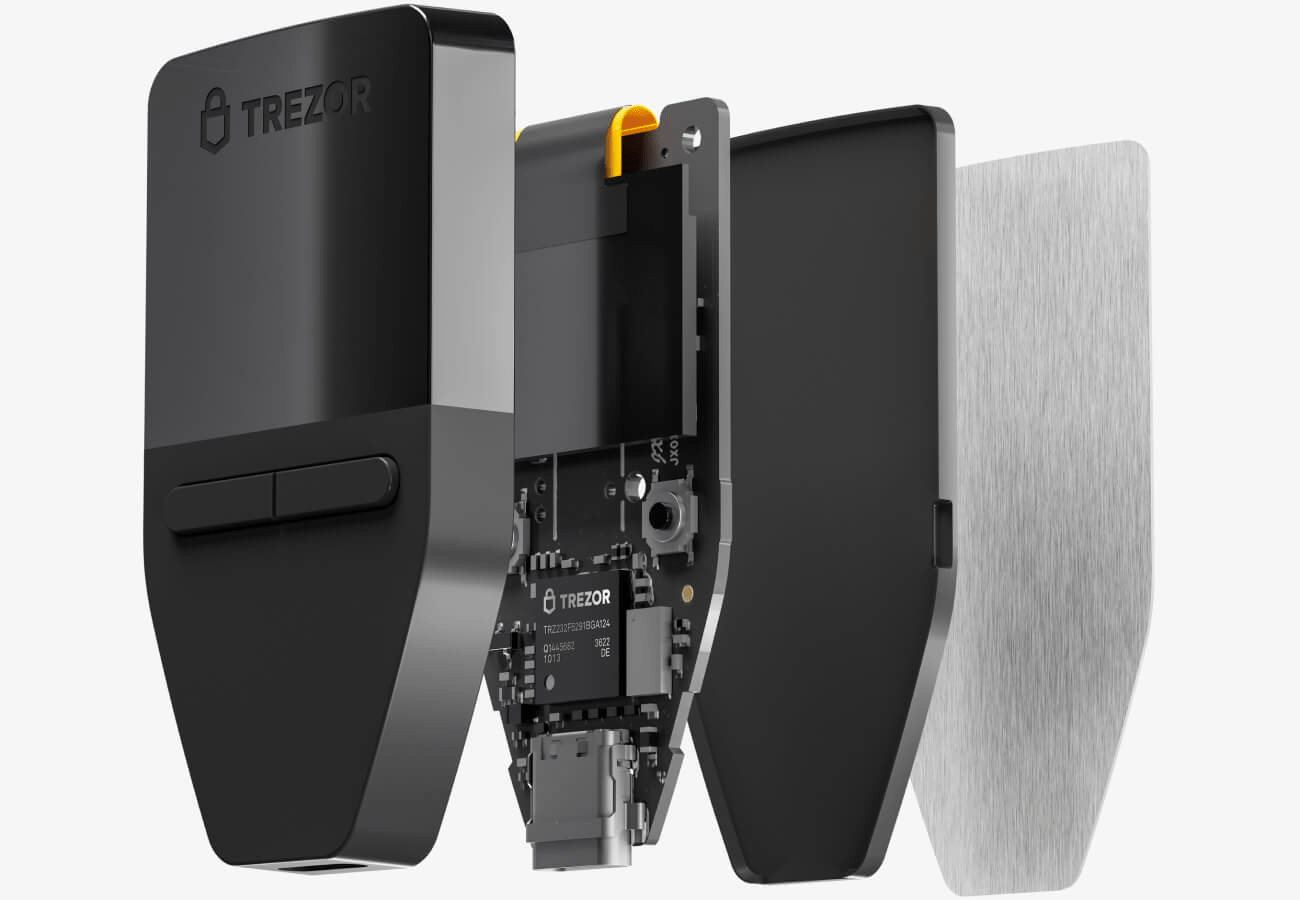
HW Wallets - Trezor

- trezor.io
- 1st in the world
- Open source HW aj SW
- Blind keyboard generated randomly
- Passphrase protected
- PIN code
- almost impossible remote attacks
HW Wallets - Trezor Model T

- Colourful display
- Open source HW aj SW
- Random generated keyboard
- Passphrase protected
- PIN code
- Password Manager
- Shamir scheme (SSSS)
Trezor 3
Ledger Nano X

- https://www.ledgerwallet.com/
- Open source SW but no HW
- Harder to use
- Small Memory for a limited amount of apps
- Closer-sourced Secure Chip
SW wallets
Mobile apps:
- BTC: Green Wallet
- Lightning: Phoenix, Breez
- Altcoins: Coinomi
- ETH: Argent
Crypto Steel

https://jlopp.github.io/metal-bitcoin-storage-reviews/





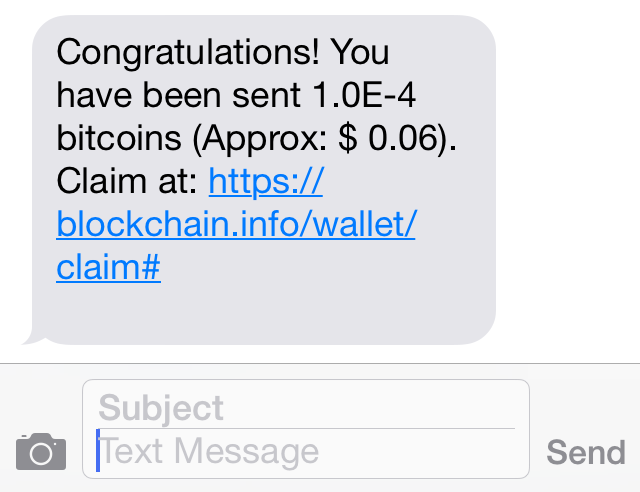
BTC via SMS
Bitcoin ATMs
www.coinatmradar.com

- quite anonymous in some countries
- no ID required usually
- KYC-less purchase up to 5k
- 2way ATMs as well
Exchanges
- Trading against others
- Orderbook - supply and demand
- Low fees
- Many coins, higher liquidity
- Registration, Verificaiton AML, KYC
- Margin, Funding, Futures, CFD
- Bitstamp, Coinmate, Bittrex, Bitfinex, Kraken
- Sophisticated tools:
- Limit order, market price, stoploss, trailing stop, hidden
- Graphs & analytical tools, indicators
- Market depth, liquidity
Privacy
How much privacy should we allow?

What are the potential ethical and legal implications of using privacy-focused cryptocurrencies, and how might this impact their adoption and regulation in the future?
Steganography for seeds

Emergence of Privacy Coins
A zero-knowledge proof (ZKP) is a cryptographic method which allows one person (the prover) to prove to another person (the verifier) that they have the possession of some information without revealing the information to the verifier.
In other words, ZKP allows conveying the assurance that the information is in hand without revealing the information itself.
ZKP
Completeness
If the statement is true, the honest verifier (that is, one following the protocol properly) will be convinced of this fact by an honest prover.
Soundness
If the statement is false, no cheating prover can convince the honest verifier that it is true, except with some small probability.
Zero-Knowledge
If the statement is true, no verifier learns anything other than the fact that the statement is true. In our example, Varun does not get the knowledge of the secret words to open the magic door in the verification process.
ZKP Overview

ZKP Overview II.

ZKP Ecosystem


zkEVM Equivalence



- User generates a private "deposit note" (sequence of digits)
- Tornado Cash pool contract prompted to process deposit
- User supplies hash of deposit note and tokens for deposit
- Pool smart contract records encoded note in public list
- Deposit note retained as receipt for future token withdrawal
- User splits deposit note into "secret" and "lock" for withdrawal
- User prompts Tornado Cash smart contract to withdraw with hash of "lock" and zero-knowledge proof
- Smart contract verifies proof, ensuring tokens are rightfully withdrawn and not withdrawn previously
- If verified, contract sends tokens to user and records encoded "lock" publicly
- Process maintains anonymity, hiding the specific encoded note corresponding to the withdrawal

Readings
- How to Create BTC adress: https://en.bitcoin.it/wiki/Technical_background_of_version_1_Bitcoin_addresses
- Base58 encoding: https://en.bitcoin.it/wiki/Base58Check_encoding
- Seed: https://en.bitcoin.it/wiki/Seed_phrase
- Mastering Monero (Chapter 3) -https://masteringmonero.com/free-download.html
- zkEVM equivalence: https://www.galaxy.com/research/whitepapers/zkevms-the-future-of-ethereum-scalability/
- Tornado Cash - https://www.coincenter.org/education/advanced-topics/how-does-tornado-cash-work/
- Deterministic Wallet: https://en.bitcoin.it/wiki/Deterministic_wallet
Thank you!
- davidstancel.com/crypto