Neuropil
secure | souvereign | sustainable
data integration

_
Problem: IIoT is faced with ...
_ lack of security experts and skills
_ inconsistent use of security protocols
_ increased connectivity demand, i.e. supply chain
_ increased compliance and GDPR regulations
_ competition on new business models

_
Problem: IIoT urgently needs ...
_ data ownership and data provenance
_ automated discovery and usage of service providers
_ security and privacy by design features ootb
_ data governance across the supply chain
_ access control and policy enforcement
_ a high level of trustworthyness and reliability

_
Solution: a middleware that enables ...
_ fine grained access control for users and enterprises
_ automated discovery of interfaces and partners
_ connection of devices, processes and applications, users
_ integrated security controls for zero trust environments
_ value creation and competition for service providers
_ integration based on data spaces
_

Solution: a middleware that enables ...
_
Market: the IIoT market is ...
_ huge (what did you expect?)
_ in numbers:
by 2023 USD 232,15 billion
by 2025 USD 949,49 billion
(how did they make up the decimal places?)
_ but: IIoT is dead ... Long live the SiTH !
_ secure, sovereign, sustainable integration of things
_

Product: neuropil.net is an asset ...
_ trademark has been established in Europe and worldwide
_ collaboration platform around data exchange
_ ecosystem for security, sovereignty and sustainability
_ data integration best practices and know how
_ available for interested business partners!
_

Product: neuropil.io is a business ...
_ subscription based SaaS offer to establish trust
_ enable data transmission across the globe
_ feature development and LTS on request
_ security reviews and consulting
_ available for interested service partners!
_

Product: neuropil.com is a product...
_ open-source security and privacy by design framework
_ a "connector" for international data spaces (IDSA)
_ full stack security library is easy to install and use
_ a revolution for data integration !
_ available for interested development partners!
_

_ Stephan Schwichtenberg
Founder & Business Development
_ Simon Klampt
IT-Development
_ Paula Pütz
Organizational Development
_ Jenny Kollo
Communications & Marketing
_ various students and apprentices
Team
_

pi-lar GmbH
Kreuzgasse 2-4
D-50667 Köln
+49 221 16531700
info@pi-lar.net
www.pi-lar.net
Neuropil
secure | souvereign | sustainable
data integration

_
Security
of the Past:
Limitations
_ only protection of bilateral IP connections
_ not protecting different data objects, but apis
_ unsuited for rapid change of
data owners / new data channels

_
Security
of the Past:
Limitations

_
Security
of the Past:
Limitations
_ static design: build once, run forever
_ new requirements vs. security design
_ introduce security exceptions on change

_
Security
of the Past:
Limitations

_
Security
of the Future:
Zero Trust
_ trust perimeter has changed
_ fragmented information (flows) need protection
_ authn/authz must be possible everywhere
_ data objects governed by
external/internal access policies (AP)

_
Security
of the Future:
Zero Trust
_ defines trust levels for data objects
or smaller groups
_ fine grained access to objects possible
_ more insights means minimizing risk
_ Never trust, always verify

_
Security
of the Future:
Zero Trust

Security for Complex Ecosystems:
Zero Trust & Access Policy
_ data object interactions main driver
for future IT architecture
_ devices produce and consume data
at the same time
_ respect different data owners per device
if one fails, all suffer!

_
Security of Ecosystems:
Zero Trust, AccesPolicies
_ business agility: enables your company
to adapt and survive
_ switch to a different service provider is easy
_ change policies in days (rather than months)
_ enables data reduction and data economy

_
Text


Our Approach

_
_Neuropil
_the first decentralized
_open-source messaging layer
_with security and privacy by design.
Neuropil
connects everything
_
_ devices, edge, applications, users, processes, enterprises
_ with the help of a trusted B2B mesh network
Security First
- digital identities
- dual encryption layer (transport and end-to-end)
- attribute based access control
- decentralized access delegation
- object level permissions via security token
- limit packet size / throughput
- standardized security measures (OSI Layers 1-7)
- stacked/pseudonymized identities
- transport layer privacy
- addressing and discovery is hash based (Blabe2b)
- DHT to protect from metadata discovery
- "blind" broker nodes
- stay secure behind closed firewalls
- packet segmentation
-
Security and
Privacy First
_
Privacy First
_fully-automated
_security and privacy by design
_decentralized
_open-source
Benefits
_
_...
_...
_...
Business Model
_
_healthcare sector
_industrial plants
_..
_...
Target Market: Ecosystems with highly-sensitive data exchange
_
Ten principles of zero trust architecture
(https://www.ncsc.gov.uk/blog-post/zero-trust-architecture-design-principles)
- Know your architecture including users, devices, and services
- Create a single strong user identity
- Create a strong device identity
- Authenticate everywhere
- Know the health of your devices and services
- Focus your monitoring on devices and services
- Set policies according to value of the service or data
- Control access to your services and data
- Don’t trust the network, including the local network
- Choose services designed for zero trust
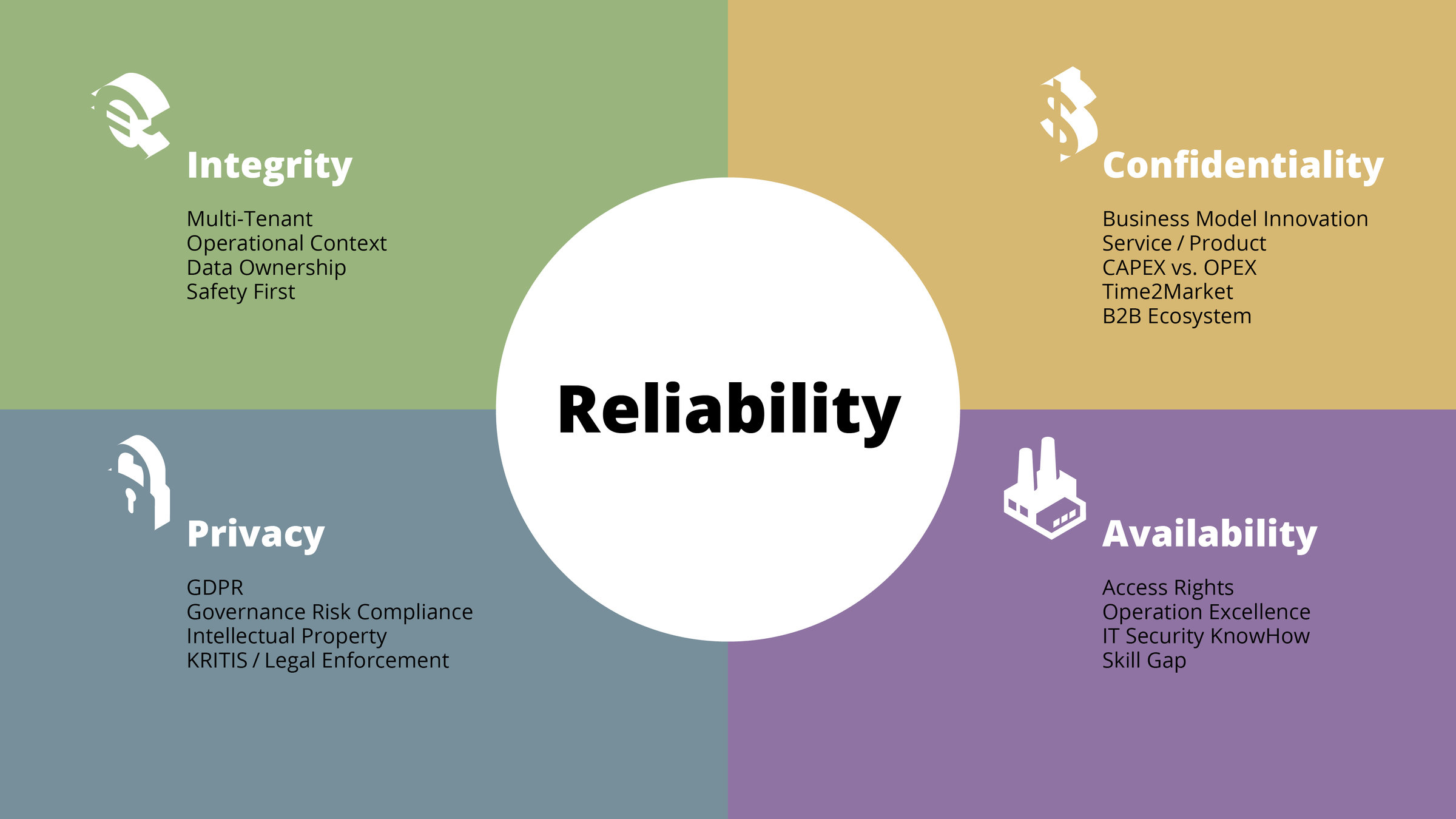
Reliability
_ Legal
_ Economic
_ Environment
_ Social

_
NIST - Implementing a zero trust architecture (March 2020)
https://www.nccoe.nist.gov/sites/default/files/library/project-descriptions/zt-arch-project-description-draft.pdf
O’Reilly - Zero Trust Fundamentals
https://www.oreilly.com/library/view/zero-trust-networks/9781491962183/ch01.html
UK NCSC - Principles to help you design and deploy a zero trust architecture
https://github.com/ukncsc/zero-trust-architecture

Security First
_ digital identities
_ dual encryption layer
_ attribute based access control
_ decentralized access delegation
... and more
_
Privacy First
_ stacked identities (realm / audience)
_ addressing hash based
_ DHT to protect metadata discovery
... and more
_
Easy to use
_ installed as a OS library
_ connect once, communicate globally
_ python / lua binding available
_ identity / data based routing
... and more
_
no more gateways
decentralized
P2P networks
>
>
Trusted B2B mesh network
Benefits
_ stay secure behind closed firewalls
_ standardized security measures
_ limit packet size / throughput
_ "blind broker" nodes

_
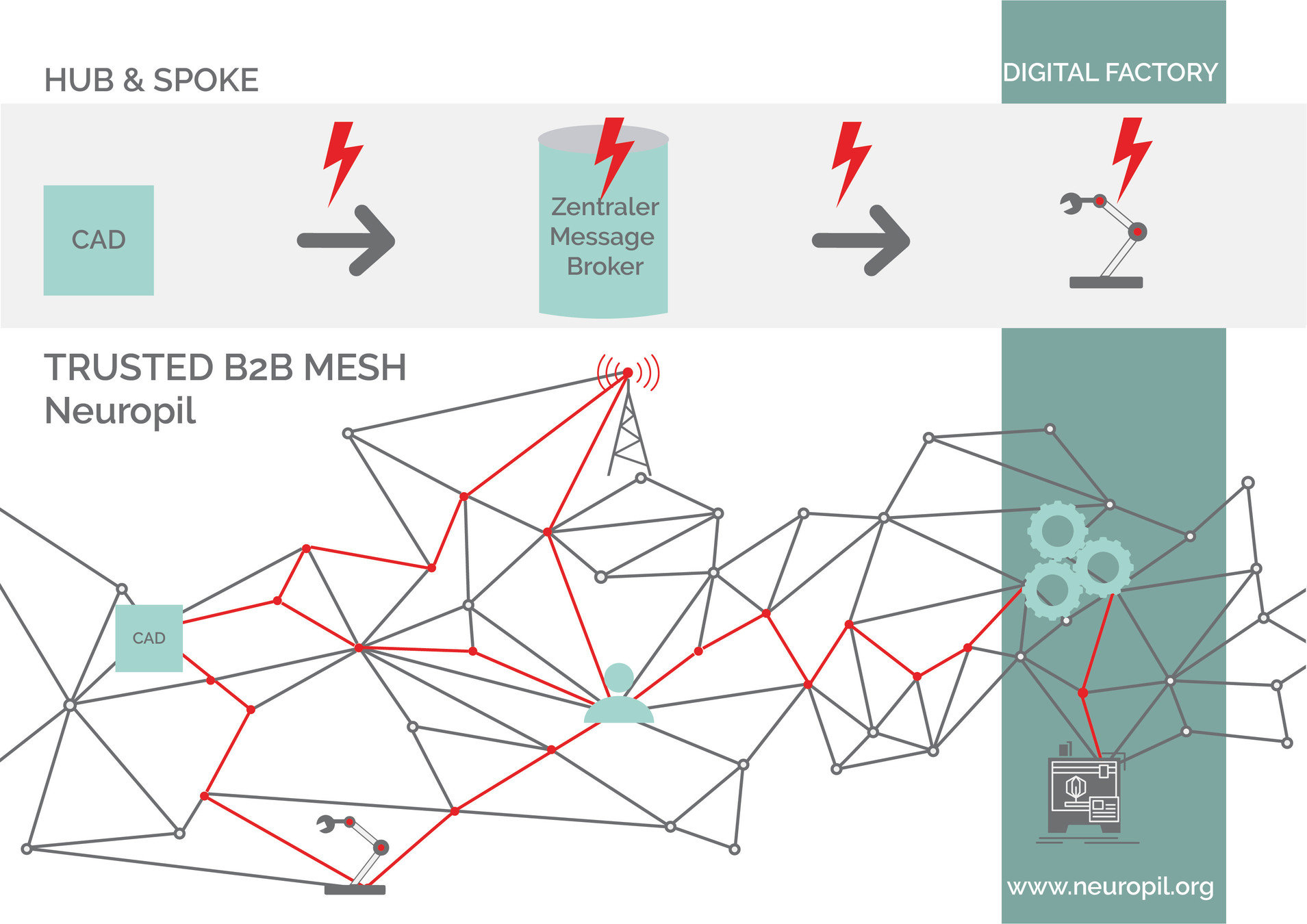
Trusted B2B mesh network
connects everything:
devices, edge, processes,
applications, users, enterprises
...
Neuropil
Cooperation, dialogue, contribution etc.