The State of HTTPS
The importance of securing all web traffic and why Utah should take the lead
Relevant Bio
'90s: Internet native / BBS addict
2013: First InfoSec con: SAINTCON
2015: HTTPS advocate: SecureUtah.org
Always: The Ethos of Tron

Background & Disclaimers
The Ugly: HTTP abuses
The Bad: HTTPS objections
The Good: HTTPS justification
The Future: Utah
The State of HTTPS
HTTPS: What is it good for?
Data Integrity In-transit Privacy Server Identity

Background
-
About HTTPS
- What is HTTPS? (HTTP = transparent tubes)
- How HTTPS Secures Connections
- A secure channel for an insecure network
- Certificate Authorities (aka CAs)
-
How does
SSLTLS work
This is not new territory
-
April 2009 - Chris Palmer: High performance with HTTPS
-
Since 2009 - Christopher Soghoian: calling out everyone
-
Jan 2010 - Google: Gmail defaults to HTTPS
-
Oct 2010 - Eric Butler: releases Firesheep extension
-
Mar 2011 - ArsTechnica: HTTPS is more secure
- June 2010 - EFF: HTTPS Everywhere browser extension
-
Apr 2011 - EFF: HTTPS Now Campaign
- May 2011 - Mike Shema: You Should Always Use HTTPS
-
July 2012 - Adam Langley: Living with HTTPS
-
June 2013 - Edward Snowden: first docs released
-
June 2014 - Pierre & Ilya: Google's HTTPS Everywhere
-
July 2015 - Guy Podjarny: 10 Reasons to Use HTTPS
-
Oct 2015 - Myself: The State of HTTPS (ver 1.0)
-
Mar 2016 - Scott Helme: Debunking HTTPS objections
- May 2016 - Emily Stark: Mythbusting HTTPS
- June 2016 - Emily Schechter: Mythbusting HTTPS
This is not new territory

If default is your desire
HTTPS does not prevent:
Metadata collection
-
DNS request
- Domain name
- IP address & port
- Session initiation
- Session length
- Session activity
- Session volume
Disclaimers
- Traffic / content analysis
- Browser / client fingerprinting
Disclaimers
HTTPS does not prevent:
- Rogue or Compromised Certificate Authorities
Disclaimers
-
Phishing
- Certs do not guarantee safe, honest, or legit content
- Netcraft complains: phishing sites use free certs
- Let's Encrypt responds: anti-phishing is not CA's role
HTTPS does not prevent:
Disclaimers
-
Client or server compromise
- Seek professional help
- Seek professional help
-
De-Anonymization
- Seek professional help
HTTPS does not prevent:
What HTTPS attempts to protect against:
-
Eavesdroppers
- Public WiFi Snoopers
- Perversive Trackers
- Dodgy ISPs
- Prismatic Spinal Taps
-
Mischief-Makers in the Middle
- Cookie Thieves
- Tor Exit Nodes
- Code Injectors
- Nosy Nations
- Redirections to Imposters

Disclaimers
Reasons to prefer HTTP
...that aren't really reasons for actual website owners
Reasons to prefer HTTP
You’re from 2006 and you love Upside-Down-Ternet
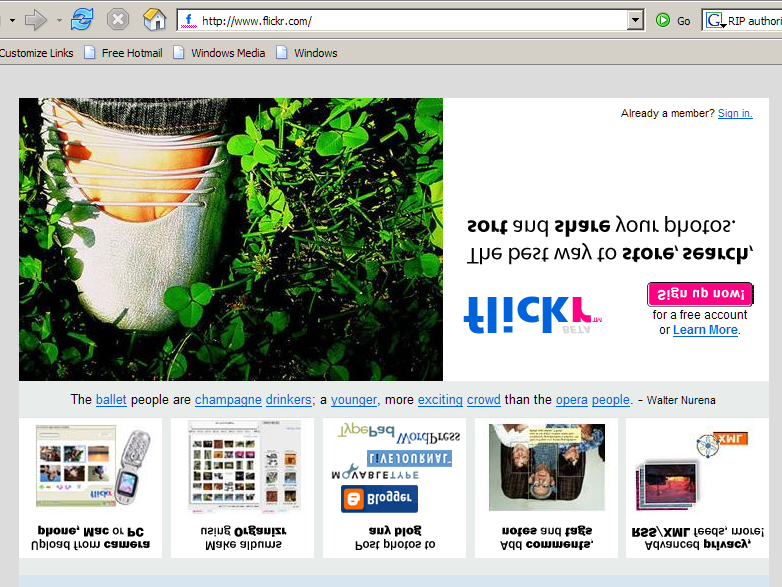
Reasons to prefer HTTP
-
2014: Comcast injects ads via JavaScript
- 2015: Comcast injects reminders about your data cap:
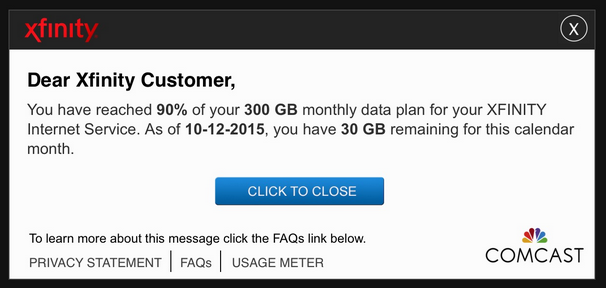
You are an ISP and want to sell out, annoy, and/or track customers as they move across the web
Reasons to prefer HTTP
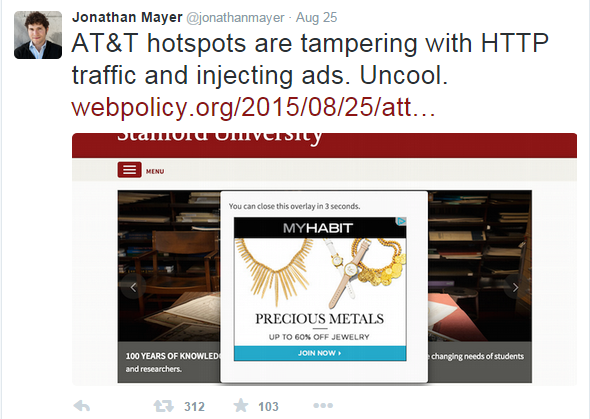
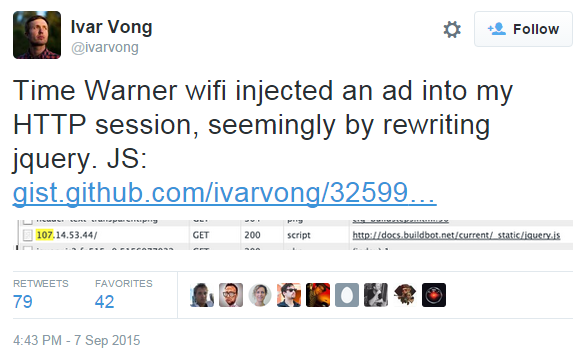
You are an ISP and want to sell out, annoy, and/or track customers as they move across the web
Reasons to prefer HTTP
- 2008: Charter and other ISPs tested DPI to sell targeted ads
- 2013: CMA Communications injects ads via JavaScript
- 2014: Company markets “Wi-Fi monetization strategies” to help ISPs “capitalize on JavaScript-injected ad campaigns…”
-
2015: Verizon, AT&T, Vodaphone and others inject tracking IDs into all mobile browsing by their customers [1, 2, 3, 4]
- Test your mobile provider: lessonslearned.org/sniff
- 2016: Chinese ISPs inject ads and malware
You are an ISP and want to sell out, annoy, and/or track customers as they move across the web
Reasons to prefer HTTP
You are SIGINT and you want an easy way to inject code or track individuals
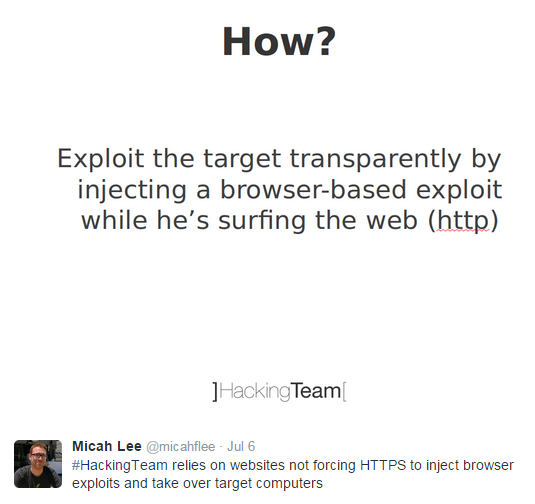
- 2014: Report on two 'Network Injection' appliances
- 2015: UK's GCHQ collects Target Detection Identifiers
- 2013: Packet injection capabilities of NSA revealed
- 2014: Canada’s CSEC captures unique identifiers and tracks thousands of individuals
Reasons to prefer HTTP
- India blocks 32 websites because they contained ISIS content
- Russian agency objected to one page of Wikipedia
- China temporarily blocks GitHub - 2013, 2015
- Malaysia blocks Medium.com - Techdirt, EFF
You are a frumpy government and you want to block only some pages of a website
Reasons to prefer HTTP
-
1998: L0pht testifies to congress about BGP weaknesses
-
2008: Pakistan hijacks YouTube for about 100 minutes
-
2013: 1,500 IP blocks hijacked across 38 distinct events
-
2013: Hacking Team help Italian Police grab IPs back
- 2014: Traffic hijacked from 19 ISPs to steal Bitcoins
-
2015: UK nuke maker’s traffic sent through Ukraine
-
2016: OMZ-IT hijacks Google's DNS
- 2016: BackConnect hijacks vDOS to mitigate the Krebs DDoS
You engage in BGP attacks for fun, profit, or malice
Reasons to prefer HTTP
-
USA has no mandatory data retention law
-
Comcast: IP addresses & session info for 180 days [PDF]
-
Century Link: Data volume, session info, IPs - days or more
-
XMission: No logging of customer activity or Tor server
- Mobile: Varies, according to leaked DHS report from 2011
You retain the web traffic you carry... just in case
Reasons to prefer HTTP
Mandatory / regulatory traffic inspection
-
Healthcare, Education, Enterprise, Mil, Gov
- Install private root certs to selectively decrypt
- Invasive end-point monitoring (keylogging)
- Aggressive traffic analysis
- Block entire domains
- Forced adaptation
...that just aren't that strong of a reason anymore
Reasons to not use HTTPS
Reasons to not use HTTPS
Encryption decreases server performance
- IsTLSFastYet.com
- Have you actually tested your system?
TLS requires a dedicated IP address
Excuse:
Rebuttal:
Excuse:
Rebuttal:
Reasons to not use HTTPS
Certificates cost money

-
Free: LetsEncrypt.org
- 20+ million active certificates
- 10+ million domains
Excuse:
Rebuttal:
- Free: Amazon AWS
- Free: Symantec
-
Free: StartSSL.com
- $16: SSLMate.com
Reasons to not use HTTPS
- Google: AdSense ad code support for SSL
- IAB: We messed up - try our new encrypted ads!
-
Mozilla: Proposed Principles for Content Blocking
- Perhaps it's time to reconsider the web ad model
- Ad-blocker use is steadily increasing
- Mobile webpage data = 50% ads
- Online ad economy is full of click fraud
- Malvertising is rampant - 2015, 2015, 2016
Can't serve lucrative relevant useful ads
Excuse:
Rebuttal:
Reasons to not use HTTPS
- Easily check a site to see what's missing or wrong:
- Industry standard: SSL Labs
- Lots of extra info: High-Tech Bridge
- OK: Symantec
- OK: Comodo
-
OK: DigiCert
- Check your HTTP headers - SecurityHeaders.io
Configuration and management are too hard
Excuse:
Rebuttal:
Reasons to not use HTTPS
- Automatic configuration is built in
- LetsEncrypt - how it works
- SSLMate - features
- Caddyserver - automatic HTTPS
- CDNs, registrars, and webhosts offer support
Configuration and management are too hard
Excuse:
Rebuttal:
Reasons to not use HTTPS
Mozilla provides an extensive guide
Configuration and management are too hard
Excuse:
Rebuttal:
Reasons to not use HTTPS
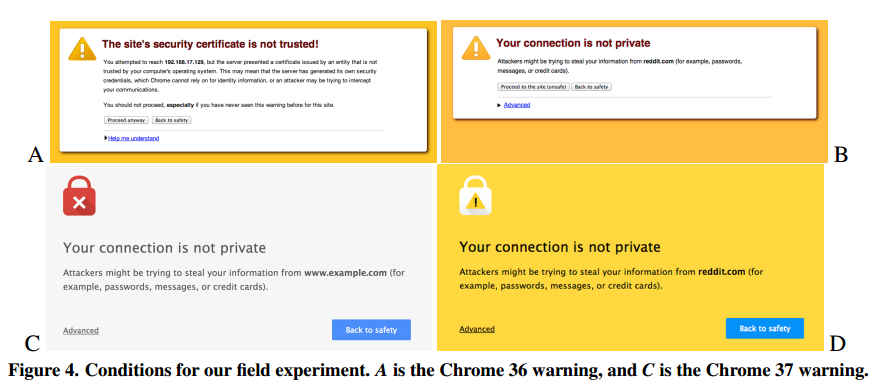
HTTPS errors produce confusing warnings

Excuse:
Reasons to not use HTTPS
Excuse:
Rebuttal:
HTTPS errors produce confusing warnings
Reasons to not use HTTPS
Chrome '15: Simplifying the Page Security Icon

Excuse:
Rebuttal:
HTTPS errors produce confusing warnings
Reasons to not use HTTPS
Chrome '16: Rethinking Connection Security Indicators
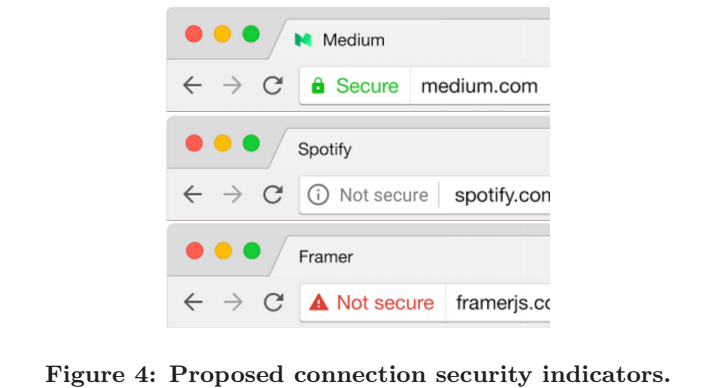
Excuse:
Rebuttal:
HTTPS errors produce confusing warnings
Reasons to not use HTTPS
View your browser's warnings:
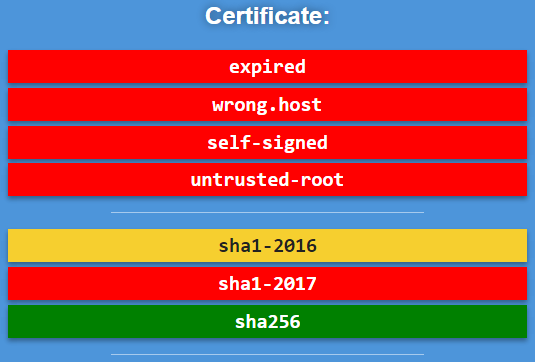
Excuse:
Rebuttal:
HTTPS errors produce confusing warnings
Reasons to not use HTTPS
Seek professional help and/or change jobs
Indifference
Excuse:
Rebuttal:
Reasons to enable HTTPS
...that are very good reasons if you are a conscientious website owner
Reasons to enable HTTPS
The whole principle is wrong; it's like demanding that grown men live on skim milk because the baby can't eat steak. - Robert A. Heinlein
The Net interprets censorship as damage and routes around it. - John Gilmore
Censorship reflects a society's lack of confidence in itself. It is a hallmark of an authoritarian regime. - Potter Stewart
Censorship sucks
Reasons to enable HTTPS
Reduce unsanctioned tracking
- W3C TAG: Unsanctioned tracking is harmful
- "...unsanctioned tracking is actively harmful to the Web, because it is not under the control of users and not transparent."
- Other entities can track injected trackers

Reasons to enable HTTPS
Matthew Green comments on AT&T + NSA collaboration:
The network is hostile

IETF RFC 1122: In general, it is best to assume that the network is filled with malevolent entities that will send in packets designed to have the worst possible effect.
Reasons to enable HTTPS
Tor nodes should be assumed to be dangerous
The network is hostile

Alec Muffet asks: Do you love your users?
Reasons to enable HTTPS
Firefox & Chrome are moving away from HTTP
- Mozilla is deprecating HTTP
- Chromium Security will prefer secure origins for powerful features and is following through on their proposal to mark HTTP as non-secure!
- IE / Edge, Safari, Opera, others - no statement yet
Reasons to enable HTTPS
Firefox & Chrome are moving away from HTTP


Reasons to enable HTTPS
HSTS helps force HTTPS connections
-
HTTP Strict Transport Security
- Header sent by server after TLS connection is made
- Browser caches the instruction to only connect via HTTPS for a defined time period, usually a year
- Slow adoption - 95% of servers are missing HSTS
-
HSTS preloading is relatively easy for Chrome
- HTTP -> HTTPS redirect happens in the browser
- HSTS Preload List: State of the Union 2016
Reasons to enable HTTPS
You provide sensitive information
AIDS.gov leaked identifying information of visitors over HTTP

Reasons to enable HTTPS
You provide sensitive information
-
Content that deserves a higher level of privacy and security:
- Domestic violence
- Sexual abuse
- Suicide help
- Mental health
- Symptoms about any medical condition
- A wide range of personal and social issues that
have the potential to be stigmatizing
Reasons to enable HTTPS
You provide sensitive information
-
Content that deserves a higher level of privacy and security:
- Politics, activism, protesting, dissent
- Whistleblower reporting and protections
- Any flavor of legal help or law firm
- News and media outlets
- Banking and financial institutions
- Security research - whitepapers, tools, binaries
Reasons to enable HTTPS
You collect sensitive information
-
Login - username and password
-
Contact Us - forms that request customer info
-
File upload - images, video, PDFs, résumés
- Geolocation - address, ZIP code
Reasons to enable HTTPS
You collect sensitive information
Every Step You Fake: A Comparative Analysis of Fitness Tracker Privacy and Security
Reasons to enable HTTPS
Everyone is doing it
Internet & web standards bodies
- May '14 - IETF RFC 7258: Pervasive Monitoring Is an Attack
- Nov '14 - IAB: Statement on Internet Confidentiality
- Jan '15 - W3C TAG: Securing the Web
- Mar '15 - IAB: The Need for HTTPS
- July '15 - W3C TAG: End-to-End Encryption and the Web
- Oct '15 - W3C: Upgrade Insecure Requests
- Oct '15 - Internet Society sponsors Lets Encrypt
- Oct '15 - IAB: We messed up
Reasons to enable HTTPS
Everyone is doing it
Major websites switch to HTTPS
- 2010: Gmail
- 2011: Facebook
- 2012: Twitter
- 2013: Apple App Store, Google Search
- 2014: Yahoo Mail, GitHub Pages
- 2014: Google says HTTPS is an SEO ranking signal
- 2015: Wikipedia, Netflix, Reddit, Google Blogspot, The Washington Post
- 2016: Tumblr, Wordpress, Buzzfeed, Wired, Amazon, BBC, iOS apps, The Guardian, many more
Reasons to enable HTTPS
Everyone is doing it
News outlets
-
NY Times: privacy security content authenticity
-
Washington Post: privacy security anti-censorship
-
JustSecurity.org: privacy security content integrity
-
Lawfare.com: block trackers anti-censorship content integrity
- The Guardian: privacy security content integrity SEO
Reasons to enable HTTPS
OMB creates HTTPS-Only Standard
Tony Scott, Federal CIO, issues mandate for all Federal websites:
Full Memorandum [PDF]
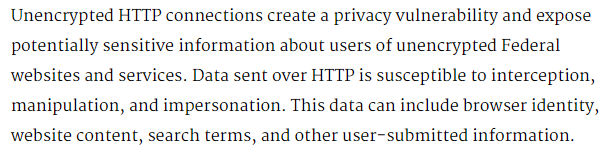
Reasons to enable HTTPS
OMB creates HTTPS-Only Standard
Tony Scott, Federal CIO, issues mandate for all Federal websites:
Full Memorandum [PDF]
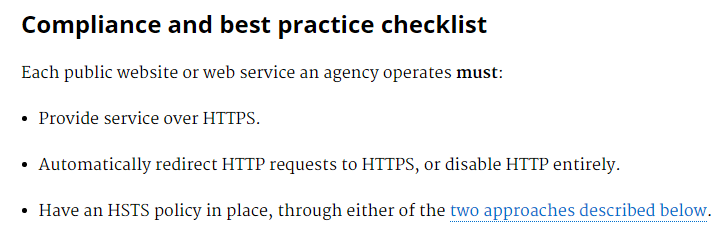
Reasons to enable HTTPS
...Empower USA's TLAs? #patrioticbackfire
Stewart A. Baker, former NSA general counsel,
from the Risky Business podcast #412, starting at 51:25
At lot of the reaction to Snowden was not wanting the U.S. in their communications. But the first thing that Silicon Valley did was say 'we need more HTTPS, more TLS.' And, ironically, that probably empowered U.S. intelligence, vis-a-vis the intelligence agencies and the law enforcement agencies of the rest of the world, more than any other technical development since international cables, because it meant that people who'd been getting communications between two Brazillians just by tapping their lines couldn't do it anymore because the communications were going straight back to Hotmail encrypted and the only way to get it was to get it at the server and that meant going hat-in-hand to the U.S. Government and saying 'could you help us investigate this crime.'
User requirements
Very easy!
- Mandatory:
- Browsers and OS should auto-update
-
Test your browser: HowsMySSL.com
-
Recommended:
- EFF’s HTTPS Everywhere
- uBlock Origin to block advertising
- Chrome: actively mark HTTP as insecure
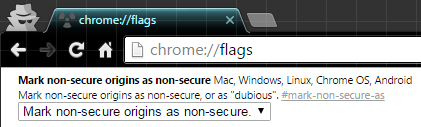

User requirements
Very easy! Probably not a good idea...

Why HTTPS?
Server-side implementation is solvable for a growing majority of websites
Client-side compatibility is handled by keeping the OS and browsers up-to-date
Choosing to enable HTTPS is now a matter of principle
Integrity & Authenticity
The Network is Hostile
All Traffic is Sensitive
You Love Your Users
Best Practice
Why HTTPS?
The State of HTTPS?
SecureUtah.org
Utah has received well-earned national attention for a pro-business environment and its many successful technology and software companies.
Utah is a perfect candidate for promoting online safety and they can (and should!) lead by example.
Currently there's almost no HTTPS advocacy work happening at the State level.
SecureUtah.org
Why Utah?
SecureUtah.org
Tracking HTTPS support of Utah websites
UtahWatch.org
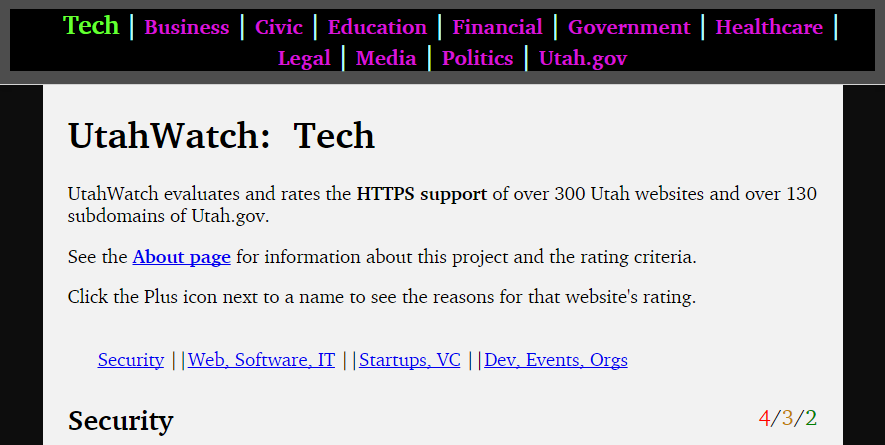
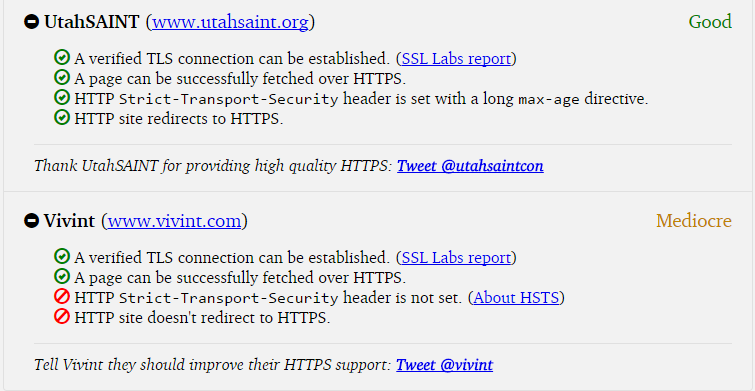
Tracking HTTPS support of Utah websites
UtahWatch.org
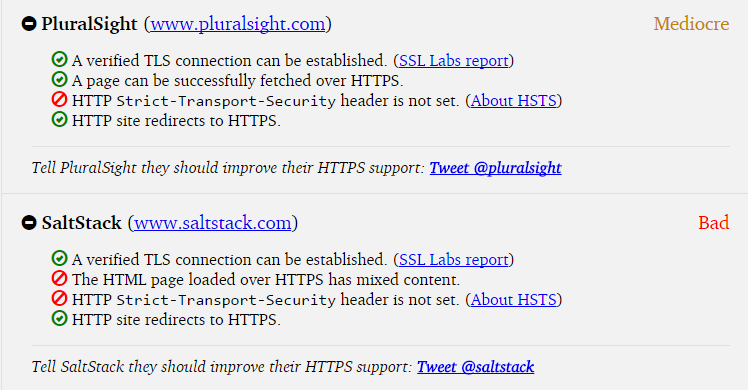
Tracking HTTPS support of Utah websites
UtahWatch.org
- Test your browser's SSL/TLS capabilities:
-
Federal .GOV domains using HTTPS: Federal Pulse
-
Federal .GOV mandate: The HTTPS-Only Standard
-
HTTPS support of prominent websites: HTTPSwatch
-
SSL/TLS and PKI monthly news: Bulletproof TLS Newsletter
-
Quality of SSL across top 1 million websites: SSL Labs Pulse
Information
-
SSL/TLS test with detailed results: Qualys SSL Labs
-
SSL/TLS test with detailed results: High-Tech Bridge
-
Best book to use: Bulletproof SSL and TLS
-
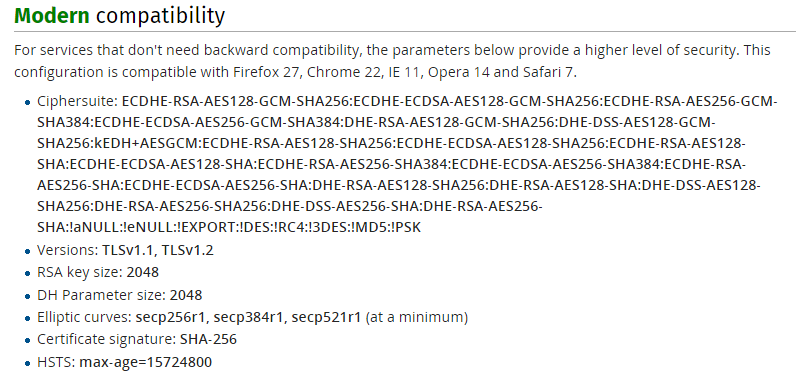
Mozilla's recommended TLS configs for server
-
Mozilla's SSL Configuration Generator
-
Google's web dev intro to TLS and HTTPS
-
Chromium's guide to TLS
-
CertSimple: What web devs should know about SSL
-
Cipherli.st: Strong ciphers for Apache, nginx and Lighttpd
-
TLS.builders: Code for OpenSSL on different servers
Testing & Configuration
-
Evaluate HTTP response headers: securityheaders.io
-
Guides for HSTS-related issues
-
caniuse.com: Browser support of front-end web tech
-
sritest.io: Scan for Subresource Integrity
- Check the Revocation Lists and OCSP status of a certificate
- An examination of Ineffective Certificate Pinning
- Use Chrome's DevTools to debug connection errors
- Google FAQs for moving from HTTP to HTTPS
Testing & Configuration
- Richard Barnes - Firefox Security Lead at Mozilla
- Ben Balter - Government Evangelist at GitHub
- Eric Mill - Developer and Technologist at 18F
Inspiration
- Matthew Green - Cryptographer and Professor at JHU
- Moxie Marlinspike - Security Researcher, Software Dev
- Alec Muffett - Software Engineer
- James Williams - Doctoral Student, Univ of Oxford
Inspiration
Thank you!!!
Twitter: @SecureUtah
The State of HTTPS
By J0NJ4RV1S
The State of HTTPS
The State of HTTPS: the importance of securing all web traffic
- 7,233