How to prevent Dev from committing secrets and credentials into git repositories
Tool Demos: Talisman & Trufflehog
Lighting Talk : 10 mins Talk (25/03/2020)


Abhinav Sejpal
DevSecOps Consultant at Accenture
OWASP Suffolk - Leader
---------------------------------

Disclaimer :
- The opinion expressed here are my own, there is no relation with my employer or clients.
- Tools/Project mentioned here is just an example – No Recommendation.
- Every environment is different: Test and validate before implementing any ideas
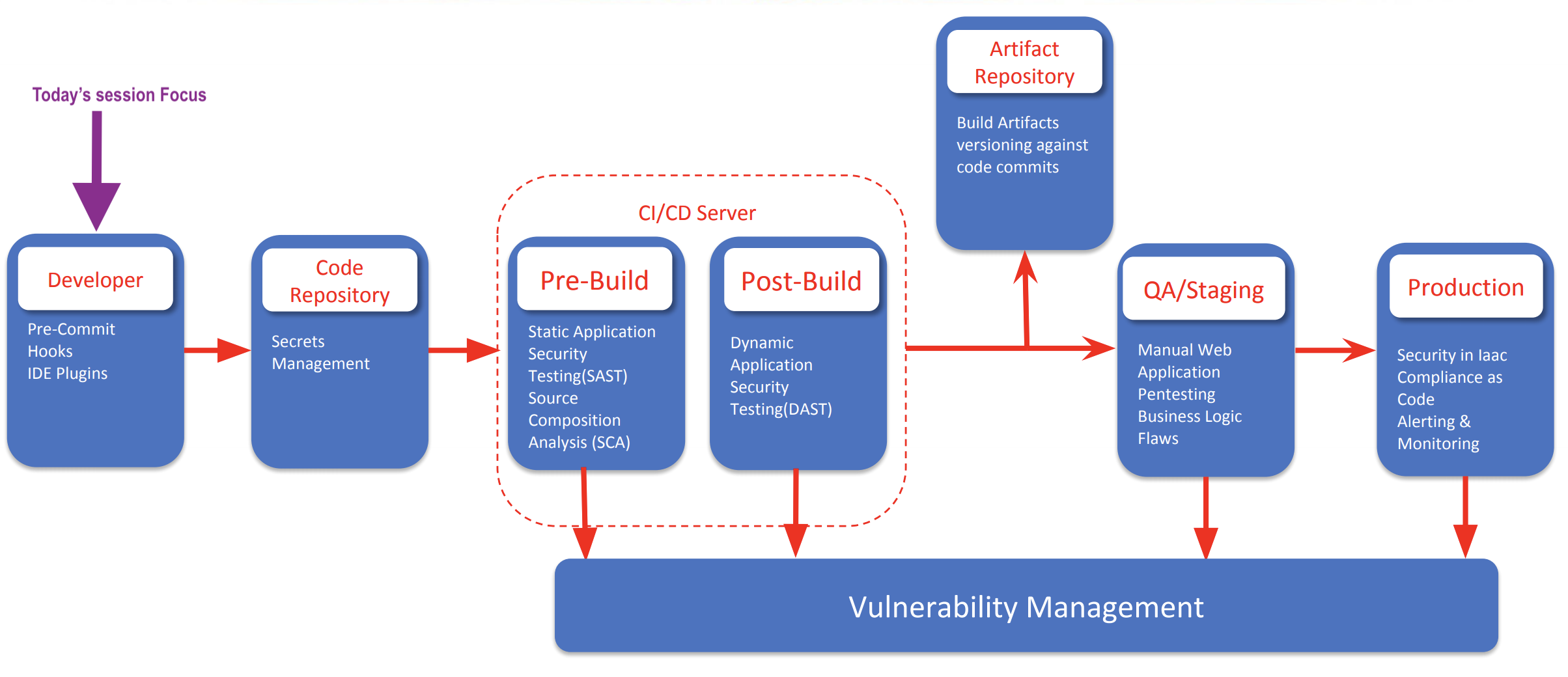
DevSecOps
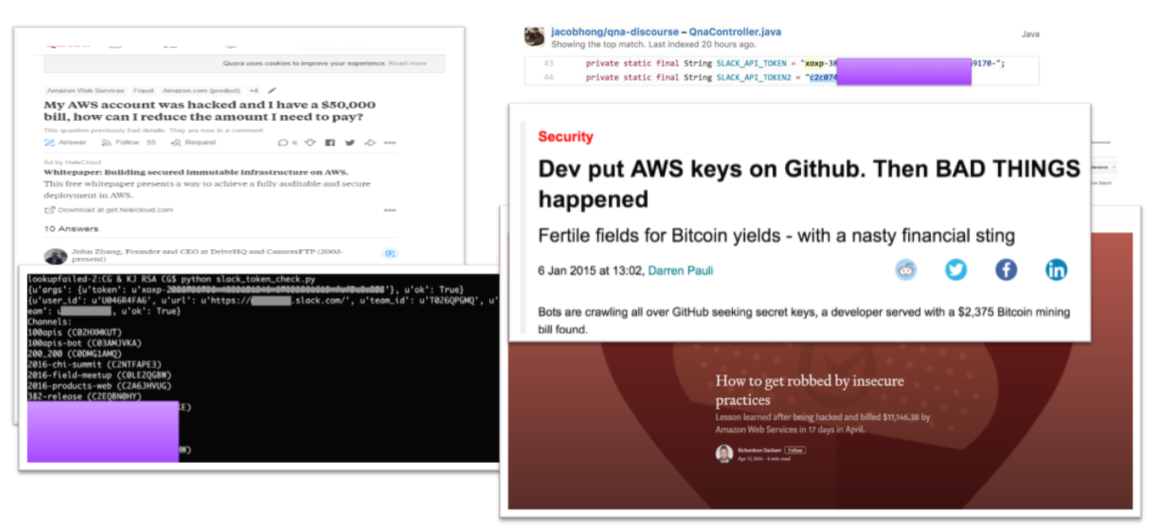
Stop Code Leaking the Secrets
Demo : Trufflehog

Git hook
No Debate: Git is one of the most brilliant pieces of software ever written!
99% DevOps Squads are using Git methodology

Talisman supports MAC OSX, Linux and Windows
Talisman can be installed and used in one of the following ways:
- As a git hook as a global git hook template and a CLI utility (for git repo scanning)
- As a git hook into a single git repository
Talisman can be set up as either a pre-commit or pre-push hook on the git repositories.
Disclaimer: Secrets creeping in via a forced push in a git repository cannot be detected by Talisman. A forced push is believed to be notorious in its own ways, and I suggest git repository admins to apply appropriate measures to authorize such activities.

- Encoded values - scans for encoded secrets in Base64, hex etc.
- File content - scans for suspicious content in a file that could be potential secrets or passwords
- File size - scans for large files that may potentially contain keys or other secrets
- Entropy - scans for content with high entropy that is likely to contain passwords
- Credit card numbers - scans for content that could be potential credit card numbers
- File names - scans for file names and extensions that could indicate them potentially containing secrets, such as keys, credentials etc
Talisman Test Scenarios :
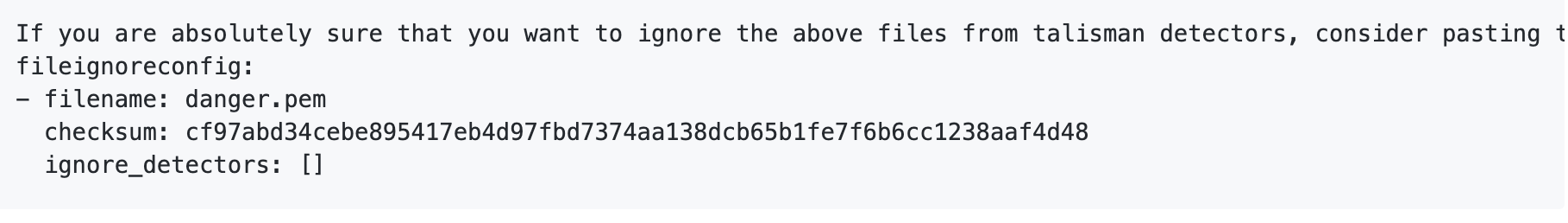
Ignoring Files
If you're really sure you want to push that file, you can configure it into the .talismanrc file in the project root. The contents required for ignoring your failed files will be printed by Talisman on the console immediately after the Talisman Error Report:
Entering this in the .talismanrc file will ensure that Talisman will ignore the danger.pem file as long as the checksum matches the value mentioned in the checksum field.
or
skip or bypass a pre-commit hook in git
commit --no-verify
Demo

Git Secrets tools
- Talisman – https://github.com/thoughtworks/talisman
- Crass – https://github.com/floyd-fuh/crass
- Git Hooks – https://githooks.com/
- Git Secrets – https://git-secret.io/
- Pre Commit – https://pre-commit.com/
- Detect Secrets – https://github.com/Yelp/detect-secrets
- Git Hound – https://github.com/ezekg/git-hound
- Truffle Hog – https://github.com/dxa4481/truffleHog
Thank you!
