iOS App Security Testing :: Session 1
Agenda
- Setting up iOS pen-testing platform
- Understanding the iOS filesystem & Assessment
- Insecure data storage
- Basics of Cycript
- Client side injection
Set up iOS pen-testing platform
Jailbreak device:
- Jailbreak the device by downloading the software from pangu http://en.pangu.io/
- Click on "Start" and follow the process to jailbreak your device
- Cydia appears in the apps, once your device is jailbroken
Latest version of iOS (currently it's 9.1) can't be jailbreak
Setting up mobile auditing platform
- Install OpenSSH, MobileTerminal & Bigboss recommended tools from Cydia app
- SSH the device for the root user. The default password is "alpine"
- Install class-dump from https://code.google.com/p/networkpx/wiki/class_dump_z
- Run the following commands to get the latest packages:
- apt-update
- apt-upgrade
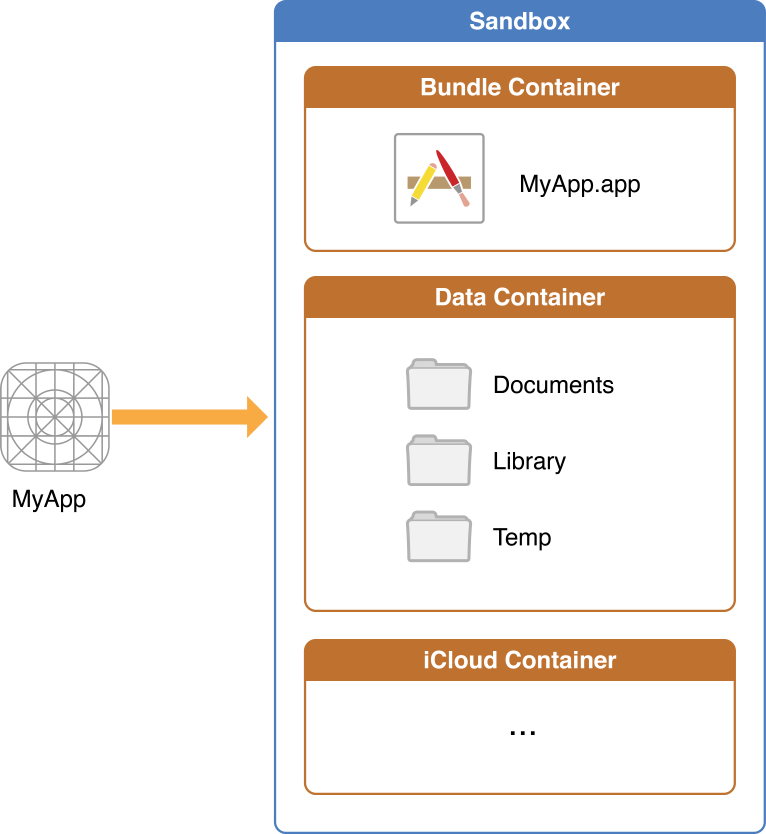
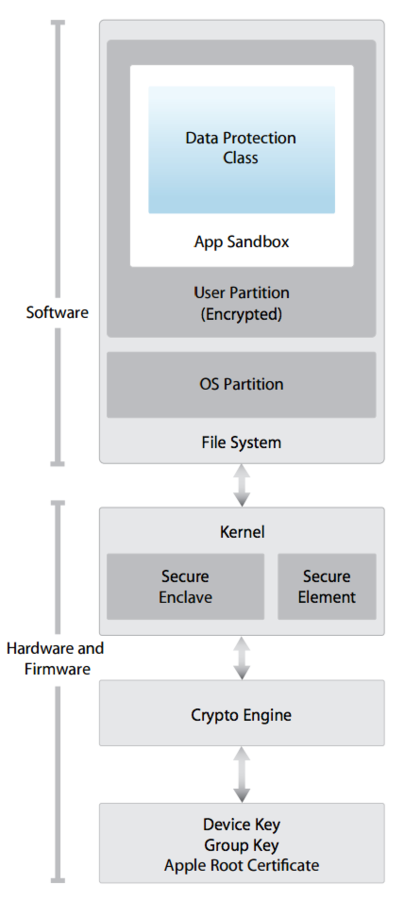
Understanding the iOS filesystem
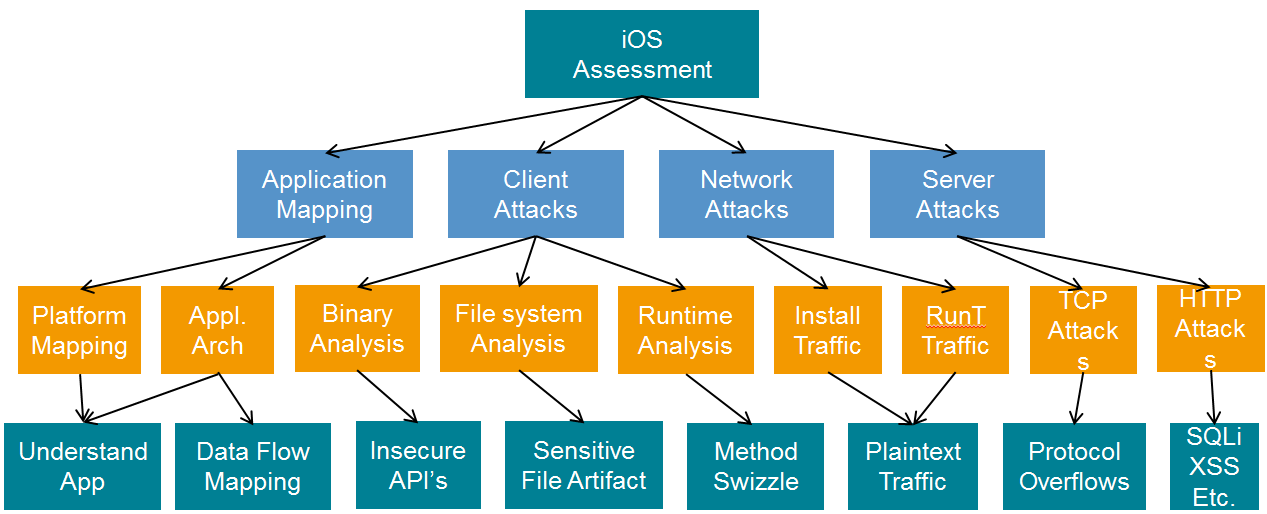
iOS Assessment - Overview
Insecure Data Storage
- Plist
- NSUserDefaults
- Core data (Sqlite)
- Keychain
- Webkit Caching
- Realm
- Couchbase Lite
- YapDatabase
Basics of Cycript
Cycript allows developers to explore and modify running applications on either iOS or Mac OS X using a hybrid of Objective-C++ and JavaScript syntax through an interactive console that features syntax highlighting and tab completion.
Why is it required for Security Testing?
- Hooking
- To identify methods used in the app
- To modify the values of variable during runtime
- Ability to execute Obj C & Javascript code
- Method Swizzling
How does it work?
- Install Cycript from cydia
- SSH the device and find the app's process using this command: ps -u <<user>> | grep "<<app_name>>
- Hook into the process using this command: cycript -p <<PID>
Client Side Injection
Data injection attacks are as real in mobile apps as they are in web apps, although the attack scenarios tend to differ (e.g., exploiting URL schemes to send premium text messages or toll phone calls).
- Javascript Injection (for e.g. XSS)
- URL Schemes Injection: Refer to http://wiki.akosma.com/IPhone_URL_Schemes#TikiSurf
- SQL Injection
SQL Injection Example

Tools & Commands Info
| Class-dump-z Installation | 1. Go to https://code.google.com/p/networkpx/wiki/class_dump_z and copy the download link 2. SSH into device and run this command: wget <<class-dump-z download link>> 3. Once this is done, go inside the folder iphone_armv6 and copy the class-dump-z executable into /usr/bin directory |
| Keychain | 1. SSH your device and run this command: wget https://github.com/ptoomey3/Keychain-Dumper/archive --no-check-certificate 2. Navigate inside Keychain_Dumper directory and run the executable by using the command ./keychain_dumper |
| Cycript | 1. Go to http://www.cycript.org/debs/ and download the latest deb file 2. Copy the package to your device and install it using dpkg with this command: dpkg -i <<deb_package_name>> 3. Once the package is installed run cycript in terminal |
Tools
Commands
| SSH | ssh root@<<device_ip_address>> password: alpine |
| Copy over Shell | scp <<source_path>> root@<<device_ip_address>><<destination_path>> |
| Convert plist to xml | plutil -convert xml1 <<plist_file>> |
| Find application PID | a. ps aux | grep "app_name" b. ps -u mobile | grep "app_name" |
| Sqlite | Sqlite3 <<sqlite_db>> |
| Extract .tar files | tar -xvzf <<tar_file>> |
Thank you