Who am I
- Next Generation problem Solver
- Researcher & Reader in free time
- Speaker at Null & OWASP Community
- Facilitator at Weekend Testing
- Bug bounty Hunter (eX .Crowd Tester)
- Reported Security Vulnerabilities for 50+ unique customers all over the world including Apple, yahoo, Outlook, adobe & etc.
- Love to develop nasty code & Hack it :)
- Works as Security Researcher at Accenture Digital Mobility
- Certified Ethical Hacker AKA. Bug Wrangler

Disclaimer
- This Presentation is intended for educational purposes only and I cannot be held liable for any kind of damages done whatsoever to your machine, or other damages.
- Please - Don't try this attack on any others system without having context knowledge or permission, this may harm to someone directly or indirectly.
- Feel free to use this presentation for practice or education purpose.
- It's no way related to my employer - its my own research and ideas.
^ I hope - You gotcha ^
Humla
Means 'attack' in Hindi



Social Media feed
Hashtag for this session
#NullHumla, #MobileSecurity
: Twitter handle for feedback :
~ We aren't going to do this ~

So, feel free to stop when you have a doubt!
Android Package - APK

Development Plan
Android Architecture
My home is your APK
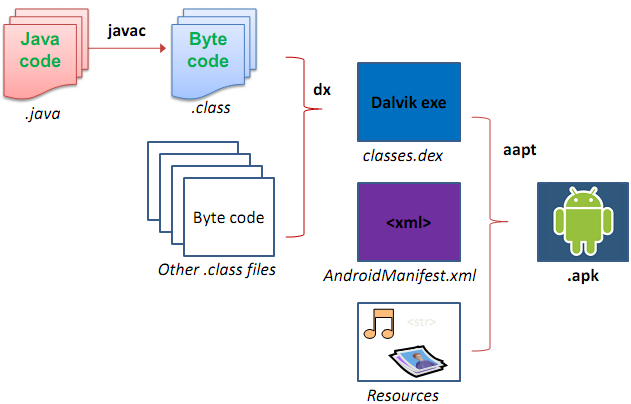
Our Arsenal
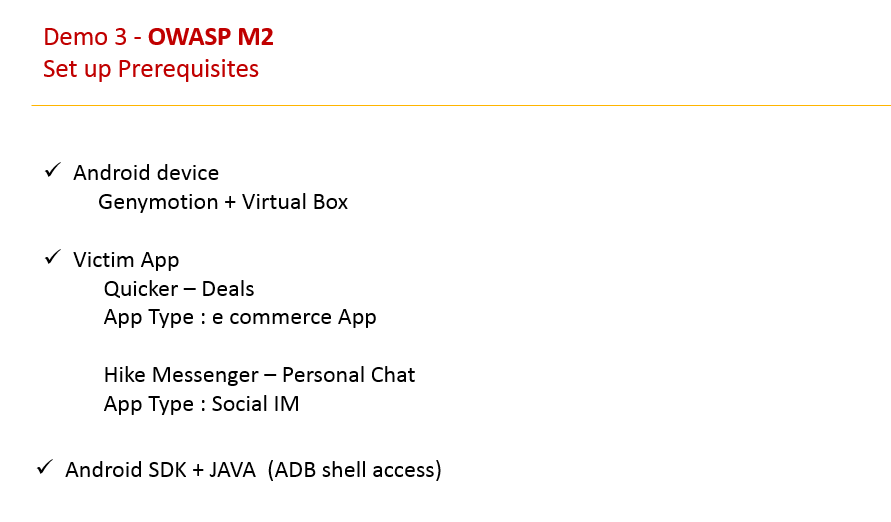
Prerequisites Checks
- Genymotion Emulator
- Appie / Android Tamer
- Copy of Shared APK
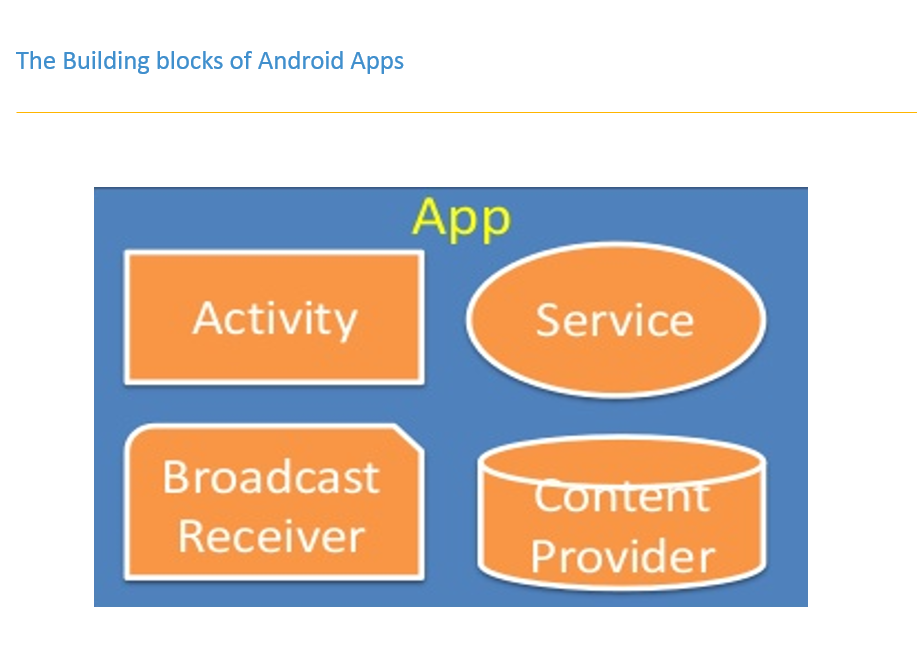
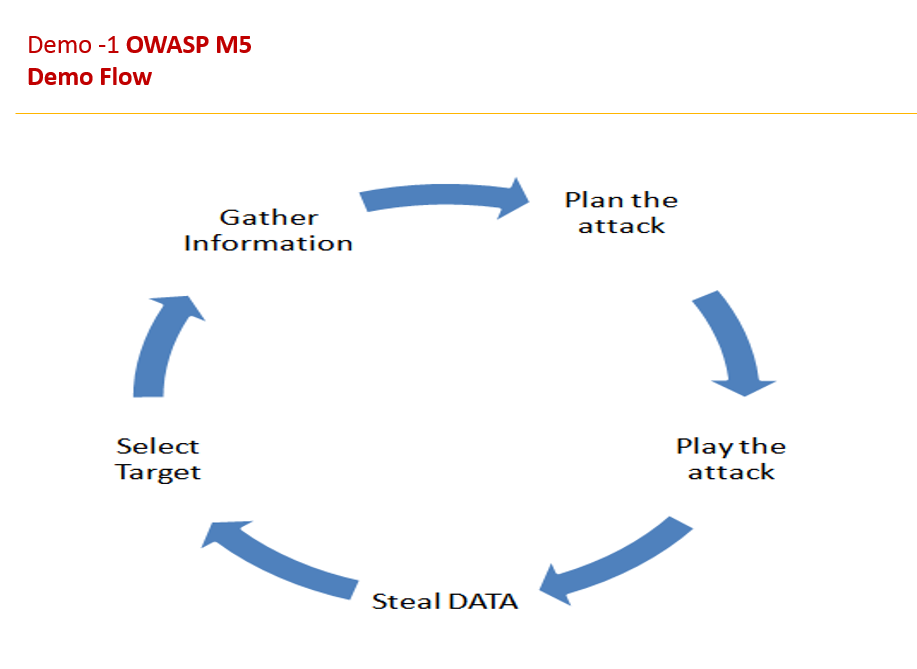
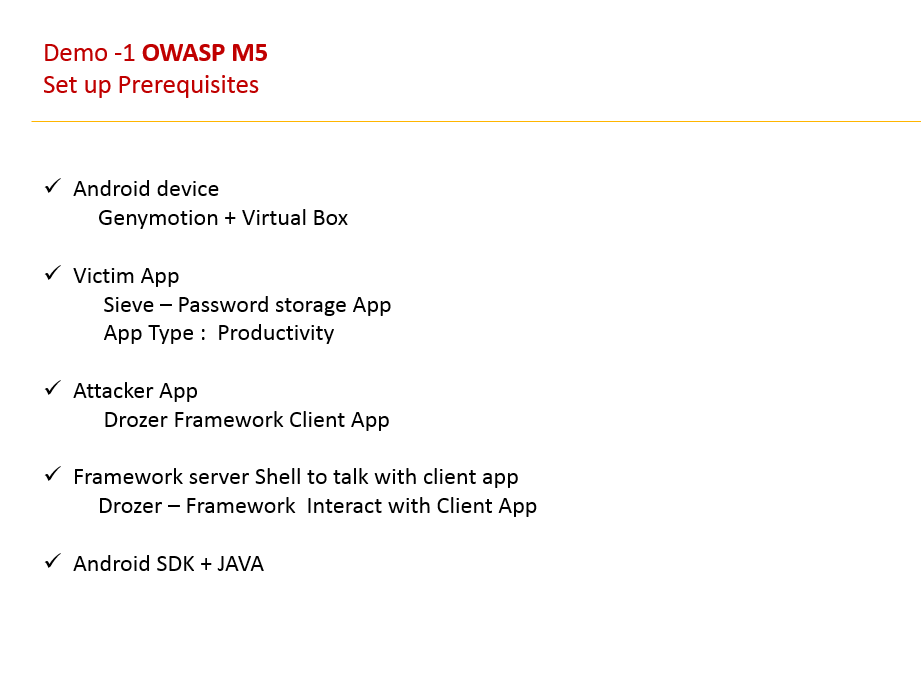
Drozer Framework
Introduction
- Drozer Server
- Drozer Agent
Self-Practice Session
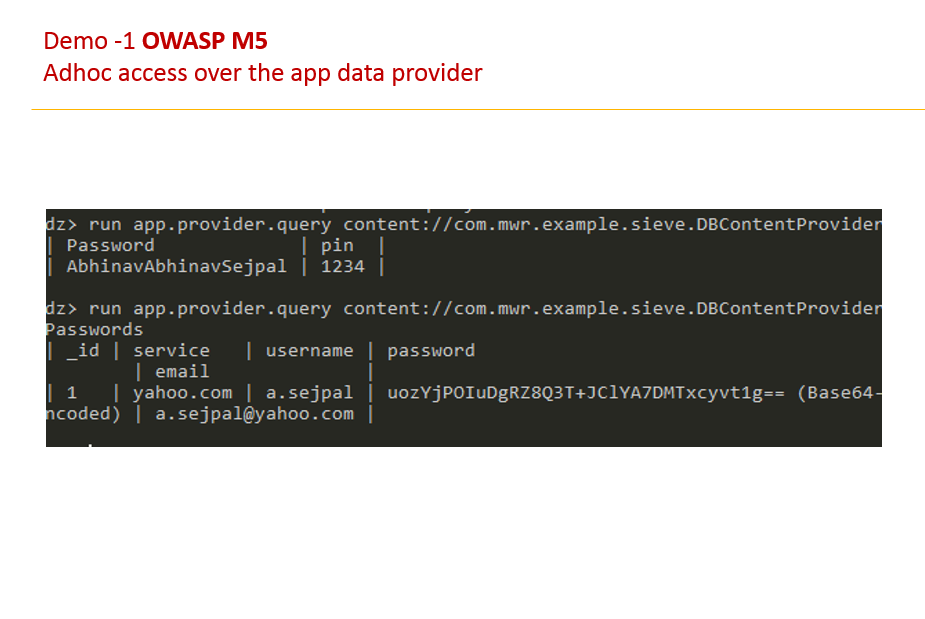
Challenge 1 – By Pass authorization for the whisper
Challenge 2 - By pass Authorization for the Lock
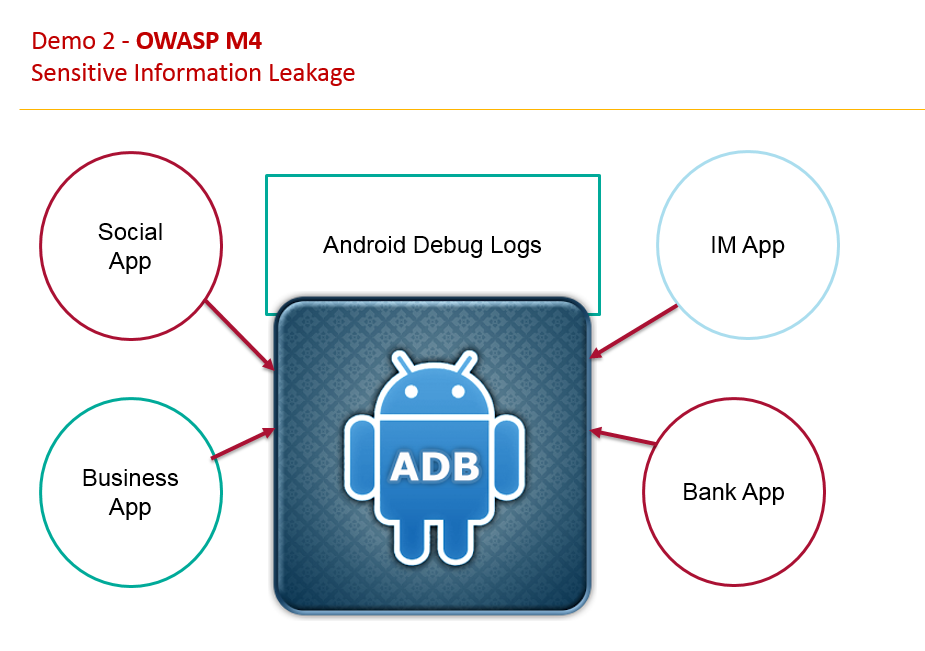
Can we replicate this issue for the LinkedIn / Hike App ?
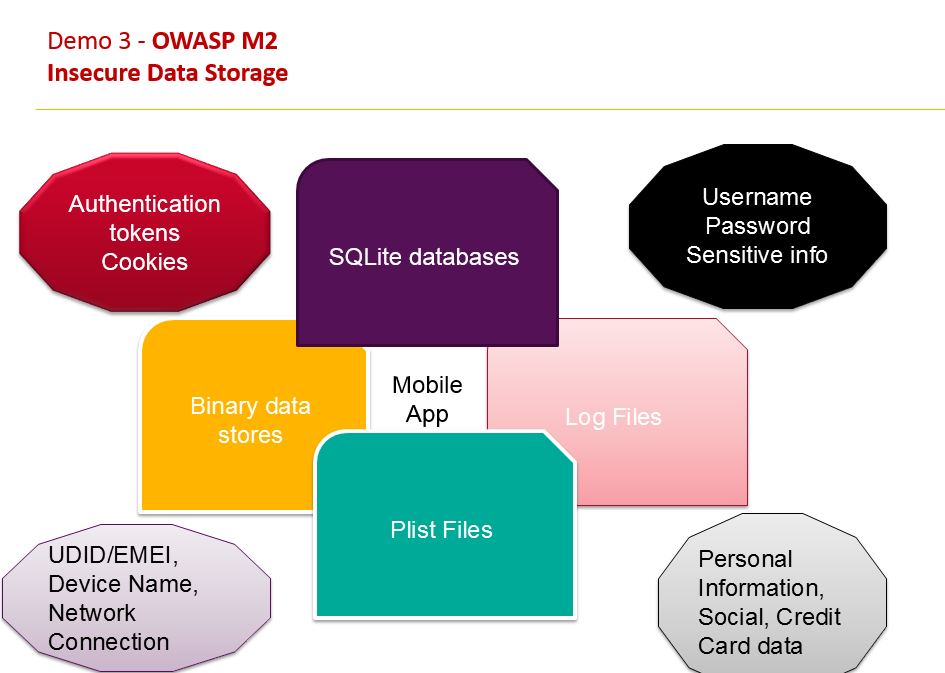
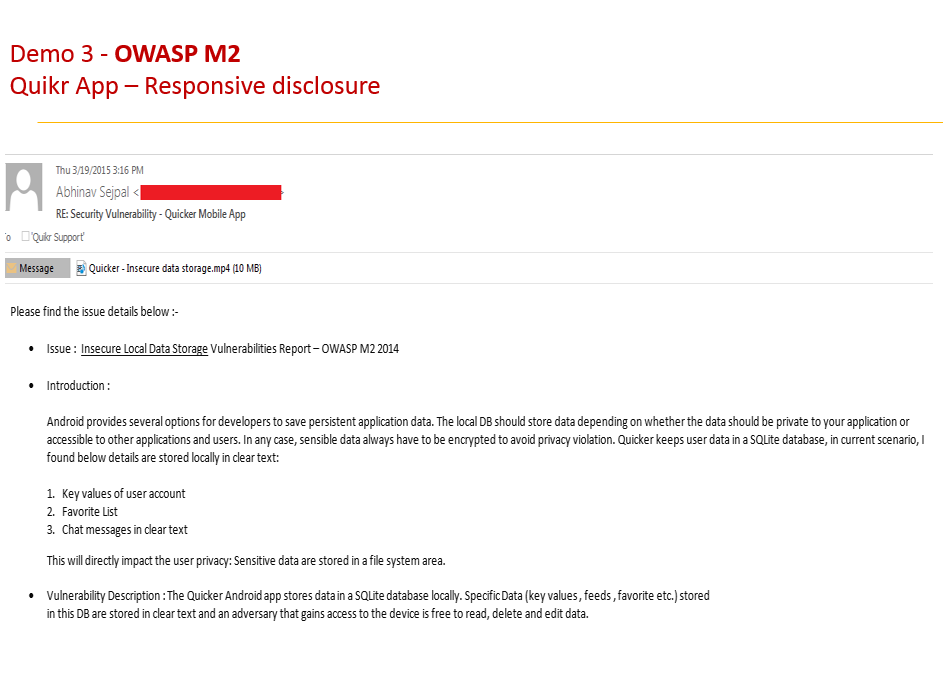
Linkedin Insecure data stroage
Demo on Missing Root Detection
Demo on Reverse the APK
Fix : Use the Dex Guard not pro guard for Java
Demo on rebuild the APK
Demo on weak Binary
Security is not taken seriously
So your IP is at risk !!
~ Game done ~
Yes - I'm Done!

Feel free to write me at bug.wrangler at outlook.com
License and Copyrights
https://slides.com/abhinavsejpal/null-humla-android-mobile-application-offensive-security-workshop
copyrights 2015-2016 Abhinav Sejpal
-----
(CC BY-NC-ND 3.0)
Attribution-NonCommercial-NoDerivs 3.0 Unported
Dedicated to my lovely daddy