Summer Internship
at
Cyber Crime Cell Gurgaon Police
Internship Mentor:- Mr. Rakshit Tandon
Name:- Ankit Kumar
2012ECS16
Introduction : Cyber Crime Cell, Gurgaon Police
Cyber Crime Cell is located in DCP Traffic Office, near Mayfield Gardens, Sec-51, Gurgaon. The Cyber Crime Cell enquires into all Cyber Crime related complaints and submits its reports to senior officers for appropriate action, under the supervision of Inspector - Sudhir Kumar.

The Cell receives complaints related to data theft, misuse of data, defamatory/abusive cases, e-mail hacking, cracking, forwarding, online lottery frauds, misuse of credit/debit cards, net banking frauds, fraudulent transfer of money and so on..
In year 2013, Cyber Crime Cell received total no. of 150 complaints related to Cyber Crimes and Mr. Sudhir Kumar was awarded the Best Cyber Cop of India.
Introduction: Mr. Rakshit Tandon Sir, Summer Internship Head
Rakshit Tandon is an Advisor/Investigation Expert to Cyber Crime Unit of Uttar Pradesh at Agra and Cyber Crime Cell of Gurgaon, Haryana police, a visiting faculty-Lecturer at Dr. B.R. Amedkar Police Academy-Moradabad (U.P), Haryana Police Academy- Madhuvan, Karnal, Police Radio Training School, Indore, CDTS (Central Detective Training School) Chandigarh and Ghaziabad.
He regularly Conducts Training Programs on Cyber Crime Investigation for Police Department across the nation, to name some are Police Range at Kanpur, Lucknow STF(Special Task Force),Agra, Greater Noida, Meerut STF, Surat(Gujarat Police) Rohtak Range, Gurgaon (Haryana).
He provides experts guidance In solving different Cyber Crime Cases to UP and Haryana
Police.
He is working as a Chief Resource Advisor and Speaker of IAMAI (Internet and Mobile
Association Of India), presently executing the “SAFE SURFING CAMPAIGN” conducting
workshops and Seminars on ‘cyber Threats to Children in Digital World’ for students, teachers
and parents to Sensitize them about the types of Cyber Crime, preventive Measures to be
taken while surfing The internet, Information Technology Act and The Remedial Measures that
can be taken if one Victimized by the cyber criminals.
Major Types of Cyber Crime
- Cyber Defamation:- Defame someone via Digital media,usually through the Internet.
- Cyber Stalking:- Cyberstalking is a crime in which the attacker harasses a victim using electronic communication, such as e-mail or instant messaging (IM), or messages posted to a Web site or a discussion group.
- Email Hacking:- hack email password of their account.
-
Vishing/phishing:- Vishing is the act of using the telephone in an attempt to scam the user into surrendering private information that will be used for identity theft.
Phishing is the fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers, online.
- Mobile Crimes:- Mobile used as a Device of communication to commit a Crime.
- Hacking/Defacement of website:- Website defacement is an attack on a website that changes the visual appearance of the site or a webpage. These are typically the work of system crackers, who break into a web server and replace the hosted website with one of their own.
- Data Theft:- Data theft is the act of stealing computer-based information from an unknowing victim with the intent of compromising privacy or obtaining confidential information.
-
E-fraud:- > Online Banking Fraud
>Online Shopping fraud
>ATM/ Credit Card/ Debit Card Fraud.
> Job Scams
Social Media Crime
> Facebook, Youtube, Twitter, Google+, Whatsapp
> Two types of Social media Crime:-
- Social Crimes
>Stalking
>Defamation
>Rumors
>Sexting/Revenge Porn - Heinous Crimes
>Kidnapping
>Online Human Trafficking
>Religious Riots
E-mail Crime
> Tracking/Tracing.
>Lottery/Scam/Threats/Ransom/Defamation/Hacking
>Fake Email (emkei.cz)
>Header Analysis (tools:- cyberforensics.in, iptrackeronline.com)
>Tool for email notification:- readnotify.com
Mobile crime
>Isp/Msp:- CDR (Call Details Record)
Cdr will give:- Date, Time, Calling party, Called party, Duration I/O, SMS I/O, SMS Center No, IMEI(International Mobile Station Equipment Identity), IMSI(International Mobile Subscriber Identity ), Call Id.
>Analysis
FCLS- First Call Last Call
Frequency of calling/SMS
Incoming SMS, Service center No translation.
Tower Dump Analysis (Only Used in Dead Cases)
GPRS logs- Sessions, Private Ip, Public IP, Destination Ip, Data usages, Urls.
>Mobile Forensics- Call logs, SMS, Inbox/Sent items, Photos/Videos/Audios.
Tools name:- Oxygen for govt. use only, Purple Radiance for cdr analysis.
Online Fraud
>Shopping Platform
>Banking platform
>ATM, Debit/Credit Cards
>Scams
>Net Banking Frauds
>Fake e-commerce Frauds
>C2C Frauds
>Phishing/Smishing(SMS phishing)/Vishing/Cloning/MIM Attacks
>Card Swapping
>Dumpster Diving (staling info. From Dustbins)
Banking Platform
> Illegal NEFT, Cheque fraud
>Phishing, Trojans, Social Engineering, Vishing, SIM card Issue, OTP, Mobile Banking.
>Cards - Tempering, swapping, Clonning
>Fake e-commerce site. eg:- timtara.com, streetstyle.com
>Payment diversion via Fake Emails...
Isp via Nigeria
>Procedures for investigation.
1. Bank Statement
2.Ip logs from the Bank
3. Final beneficiary Account Details with CAF(customer application form), Guarantor, ATM/CHQ Dispatch Details
4. Payment Gateway Details
5. Final Benefeciary Details merchant Ptoduct.
Methods Used To Attack Ecommerce Websites
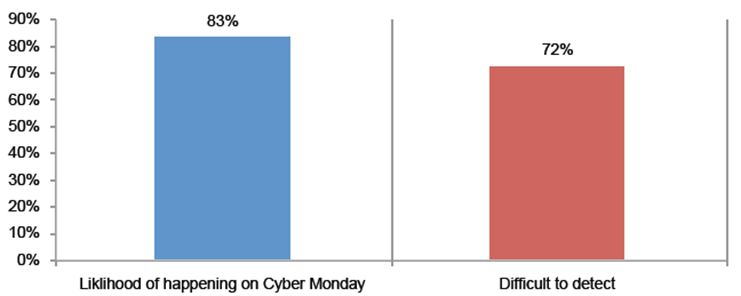
Attack 1: Botnet and DoS. This type of attack tops the list. We define this scenario as occurring when a cyber criminal targets a botnet against a company and this results in a denial of Service (DoS) attack that ultimately brings down its websites. Eighty-three percent say it is more likely to
occur on high traffic days and 72 percent say it would be very difficult or difficult to detect.
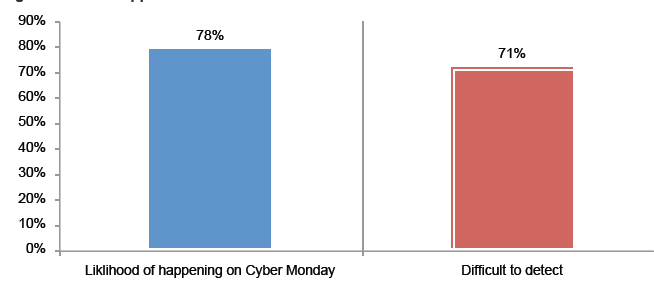
Attack 2: Mobile app store fraud. The likelihood of this type of fraud taking place on Cyber Monday is also high. Companies that are vulnerable have an app store/market place that provides access to products and instant rebates. Criminals masquerading as a merchant and a
buyer manipulate the open platform for financial gain, cashing in on rebates and earning points from credit card incentive programs. Seventy-eight percent say it is more likely to occur on Cyber Monday than other times and 71 percent say it would be difficult to detect.
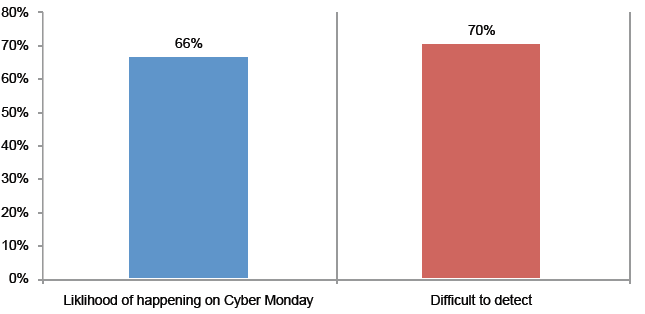
Attack 3. Mobility use case. A company expanded its consumer reach using a mobility platform that allows customers to access its websites using smart phones and other mobile devices. Cyber criminals infiltrate these devices with malware that captures customers’ account access credentials. The criminals harvest this information to takeover accounts using a laptop or desktop computer. Sixty-six percent say it is more likely to occur and a higher percentage (70 percent) say it would be very difficult or difficult to detect.
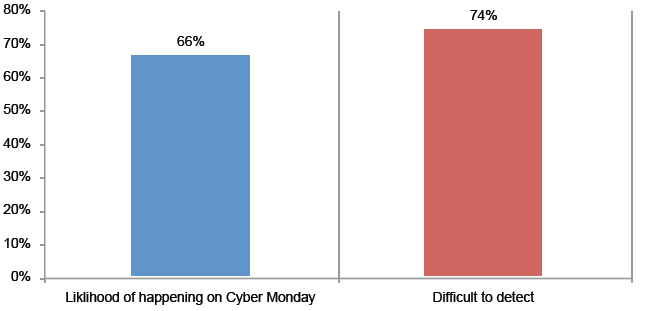
Attack 4: Click fraud. A company hires an agency to conduct an online advertising campaign. The agency is paid on a “per click” basis. In reality, many of the paid “per clicks” are not authentic
(i.e. not involving an interested consumer). Sixty-six percent say it is more likely to occur and a higher percentage (74 percent) say it would be very difficult or difficult to detect.
Attack 5: Testing stolen credit cards. A cyber criminal steals hundreds of credit card numbers and uses a company’s credit or debit card payments function to validate active credit cards. Sixtyfour percent of respondents say this is more likely to happen and 66 percent say it would be very difficult or difficult to detect.
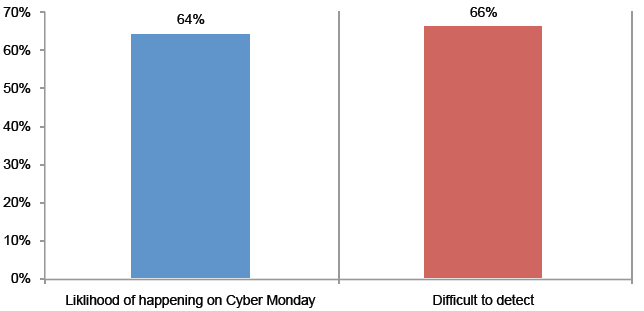
Attack 6. eCoupons. Fraudsters do an end-run around a company’s pricing policy. They select a heavily discounted item and place it in the “shopping cart.” They delay the checkout in order to obtain and apply an eCoupon to the final purchase price, thus obtaining the item well below the company’s cost. Again, 64 percent say this is more likely to happen and a significant percentage (70) say this would be very difficult or difficult to detect.
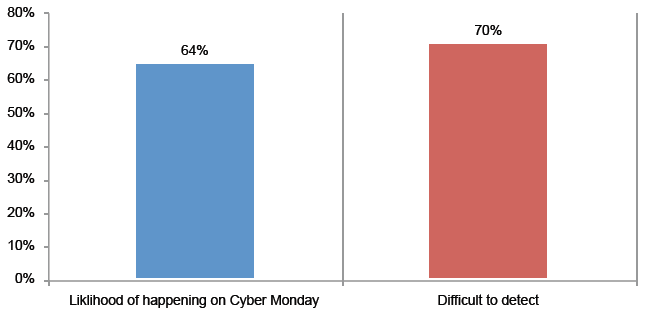
Attack 7: Account hijacking. A successful spear phishing scam resulted in cyber criminals obtaining the user names and passwords of customers. The leakage of customer account information occurred because employees were duped by what appeared to be a legitimate internal company email communication. The crime originated when the criminal obtained key employee email addresses directly from the website. Sixty-one percent say it is more likely to occur and 72 percent say it would be very difficult or difficult to detect.
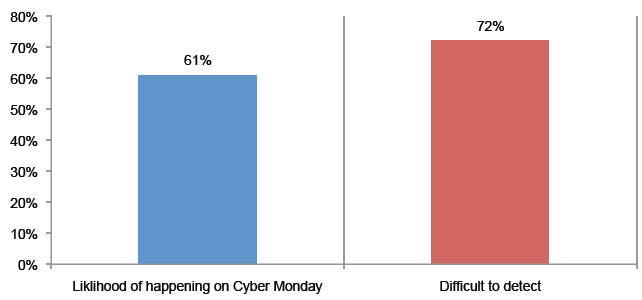
Attack 8. Electronic wallet. A company has expanded customer payment options to include Internet payment methods such as PayPal, Google Wallet, Amazon Checkout and others. A criminal looking for sites that have recently added internet payment processes identifies its site and exploits the lack of fully implemented security controls. Sixty percent say this is more likely to happen and a much higher percentage (81 percent) say it would be very difficult or difficult to detect.
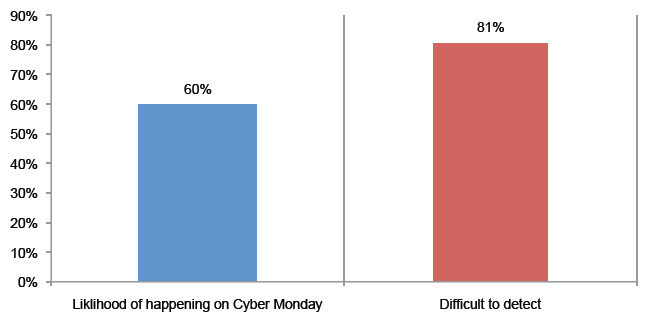
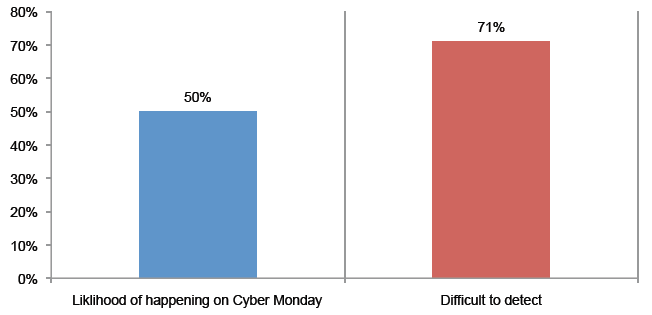
Attack 9. Mass registration. A cyber criminal creates a fake website that imitates your company’s website. Loyal and prospective customers are lured to this bogus website, which asks them to provide personal information in order to register for a promotion or offer. This results in the theft of sensitive information. In this case, 50 percent say it is more likely to occur but a much
higher percentage (71 percent) says it would be very difficult or difficult to detect.
CASE : 1
Police Station : Palam Vihar, Gurgaon
Sanjeev Kumar v/s Ravi Kishan (name changed)
FIR – 310
Case Fact:- Sanjeev Kumar is an architect. From his bank account 1 lac has been transferred through Net Banking and someone has taken 3 lac loan from his credit card Request from Victim
Sanjeev Kumar gets admitted to the hospital and due to hospitalization, he was not able to check his mobile. When he comes out of sickness, he sees his mobile which was blocked and his e-mail was also hacked. After some days, he got his Bank Statement in which he saw that his Rs. 1 lac has been transferred through Net Banking and Rs. 3 lacs has loan on his Credit Card. Although he has not done anything, his statement shows not even a single thing mentioned
Investigation:- Police had checked his CDR of mobile and traced down the location when he was in hospital and the location was Najafgarh, Delhi. Then Police went to the bank and investigated the KYC details of the beneficiary’s account. Police came to know that all the details given by the beneficiary account holder were fake except his photo. Police seized the account.
And for the e-mail, ISP sent the login IP details to the Police. Through the tracking of IP’s, Police found the culprit. He belonged to Bihar and he was an MBA guy.
CASE : 2
Police Station : Sadar, Gurgaon
Divya Singh v/s Unknown (name changed)
FIR – 526
Case Fact:- Someone calls to Divya Singh and informs her that he is calling from Bank and told her that her card has been blocked and asked for all details of her card in order to reactivate again . Divya also gave all her details assuming the situation and call to be genuine.
Request from Victim:- Divya Singh is an HR in a company. On 12 May 2014, she received a call from someone who informed her that he is calling from Bank and her card has been blocked. Now if she wants to activate her card, she has to give her old card details. Divya soon gave him all the required details of her card. After few minutes, she received a message from her bank that she had shopped for Rs.40,000/- Later on she received another message showing that she had shopped for Rs.20,000/- more.
Investigation:- Police had checked out her CDR’s of mobile but unfortunately they found that the call was spoofed. Then Police asked for login IP’s from the Bank through which machine shopping hs been done. And also asked to the concerned website to give them the address on which the shopped items have been delivered. Through the address, Police caught the culprit.
CASE : 3
Police Station : Civil Lines, Gurgaon
Ram Pyaare v/s Unknown (name changed)
FIR – 426
Case Fact:- On 23 May 2014, Ram Pyaare went to ATM near Bus Stand to withdraw money. After carrying out his transaction, when he reached home, he received a message from his bank that his bank account is debited Rs.20,000/- but he has not withdrawn the amount.
Request from Victim
Ram Pyaare went to ATM near Bus Stand, where he observed that two men were standing before him. And then when he left the ATM, they entered in the ATM and he is sure that they might have withdarwn his money.
Investigation
Police asked for the CCTV footage from the respected Bank and after analysing Police caught the Culprit.
Website Crime & Investigation
Website defacement is an attack on a website that changes the visual appearance of the site or a webpage. These are typically the work of system crackers, who break into a web server and replace the hosted website with one of their own.
>Website Cases and investigation
a. Domain:- Registrar , Payment Mode, Valid email id, creation Ip
b. Web Hosting:- Creation, Payment, valid email id, Control panel access.
c. Accessing/Development:-
Logs:- server Hosting FTP logs
Why websites get hacked?
1. It cost money to an organization to secure a website and most of the firms see it as a burden to them.
2. Even If they are willing to spend money to protect their websites, they lack competent developers that can develop secure web applications.
3. There are various weaknesses (Vulnerabilities) in technology that can have catastrophic impact if ignored.
Web Vulnerabilities
An OWASP report called “The Ten Most Critical Web Application Security Vulnerabilities” was issued this year to raise awareness about the biggest security challenges facing Web developers.Experts say most Web applications can be hacked. Here are the top ten vulnerabilities that could put your Web site at risk.
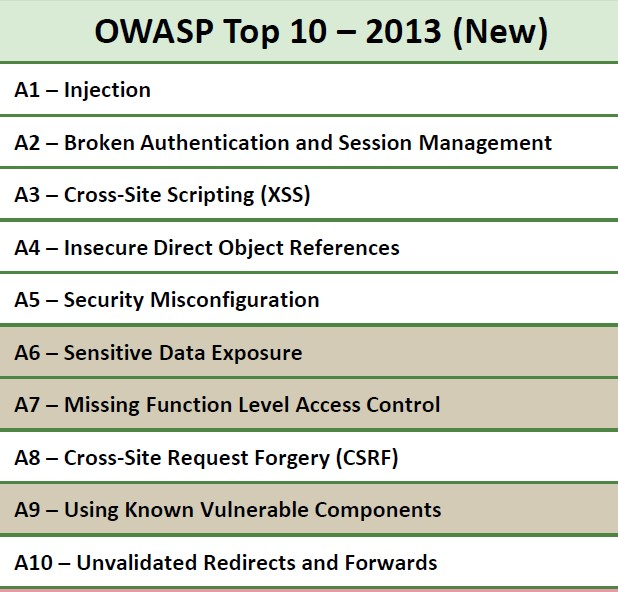
A1-Injection:
Injection flaws, such as SQL, OS, and LDAP injection occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
A2 – Broken Authentication and Session Management:
Application functions related to authentication and session management are often not implemented correctly, allowing attackers to compromise passwords, keys, or session tokens, or to exploit other implementation flaws to assume other users’ identities.
A3 – Cross-Site Scripting (XSS):
XSS flaws occur whenever an application takes untrusted data and sends it to a web browser without proper validation or escaping. XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.
A4 – Insecure Direct Object References:
A direct object reference occurs when a developer exposes a reference to an internal implementation object, such as a file, directory, or database key. Without an access control check or other protection, attackers can manipulate these references to access unauthorized data.
A5 – Security Misconfiguration:
Good security requires having a secure configuration defined and deployed for the application, frameworks, application server, web server, database server, and platform. Secure settings should be defined, implemented, and maintained, as defaults are often insecure. Additionally, software should be kept up to date.
A6 – Sensitive Data Exposure:
Many web applications do not properly protect sensitive data, such as credit cards, tax IDs, and authentication credentials. Attackers may steal or modify such weakly protected data to conduct credit card fraud, identity theft, or other crimes. Sensitive data deserves extra protection such as encryption at rest or in transit, as well as special precautions when exchanged with the browser.
A7 – Missing Function Level Access Control:
Most web applications verify function level access rights before making that functionality visible in the UI. However, applications need to perform the same access control checks on the server when each function is accessed. If requests are not verified, attackers will be able to forge requests in order to access functionality without proper authorization.
A8 - Cross-Site Request Forgery (CSRF):
A CSRF attack forces a logged-on victim’s browser to send a forged HTTP request, including the victim’s session cookie and any other automatically included authentication information, to a vulnerable web application. This allows the attacker to force the victim’s browser to generate requests the vulnerable application thinks are legitimate requests from the victim.
A9 - Using Components with Known Vulnerabilities:
Components, such as libraries, frameworks, and other software modules, almost always run with full privileges. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications using components with known vulnerabilities may undermine application defenses and enable a range of possible attacks and impacts.
A10 – Invalidated Redirects and Forwards:
Web applications frequently redirect and forward users to other pages and websites, and use untrusted data to determine the destination pages. Without proper validation, attackers can redirect victims to phishing or malware sites, or use forwards to access unauthorized pages.
1) Case one: School website hacked
Website of Reputed school of Gurgaon “XYZ public school” has been hacked by a Pakistan hacker and the home page of the website was replaced by the page written as “Pakistan Zindabad”.
The hosting server on which it was hosted, had been breached by the hackers and the files were replaced by their respective files in the subdomain directory.

INVESTIGATION PROCESS
1) The Cyber Cell acquired the “whois information” of the domain and came to know about the admin email-id of the hosting server.
2) An application was sent to the respective email-id under the section 91 CRPC, requesting the FTP (file transfer protocol) Logs on the hosting server. (Following is the image of the application)
3) In the FTP logs they acquired the login and logout IP-address which were different from the admin IP-addresses.
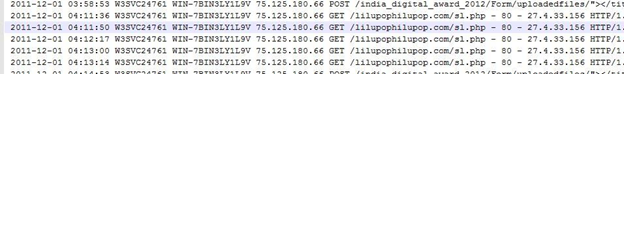

4) By the above information the Cyber Cell came to know that the location of the IP-addresses was from the Pakistan.
Hence, the case was closed.
2) Case Two: Bihar website hacked

The next day after Bihar BJP's official website get hacked by hacker claimed to be from Pakistan, the official website of Senior BJP Leader LK Advani (www.lkadvani.in) also got defaced by the same hacker.
The hacker who called himself Muhammad Bilal began the defacement message by saying "I'M Back; D gOOd mOrNing Narendra Modi". The hacker also wrote "Free Kashmir..Freedom is our goal."
The hacker also claimed to have defaced the websites of Bharti Janta Party in Lok Sabha and Bharti Janta Party in Rajya Sabha.
A screenshot published in the hacker's profile shows that he also gained access to the database server. The accessed information includes email IDs, hashed-passwords, phone numbers and other details.
At the time of writing, the LK Advani's website is down for maintenance.
Thank You!