Network scaning Tools and descriptions
Ankit Kumar
Berry9 It Services
1. Nmap
- Nmap (“Network Mapper”) is an open source tool for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. While Nmap is commonly used for security audits, many systems and network administrators find it useful for routine tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
Features
•Host discovery
•Port scanning
•Version detecting
•OS detection
•Scriptable interaction with the target
Tool Environment
•Runs on Linux, Windows, Mac OS X and other smaller operating systems
•GUI options:
•Zenmap
•XNMap
•NmapFE
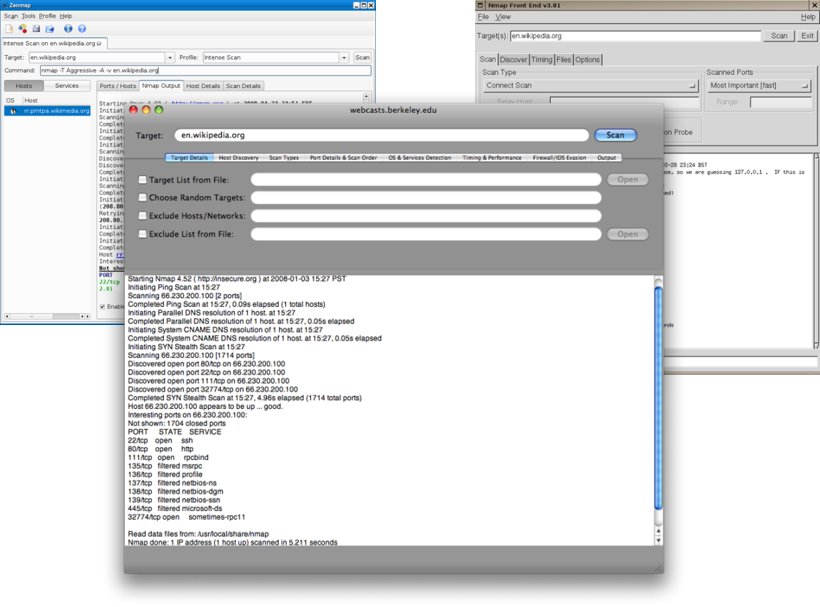
How It Works
•DNS lookup- matches name with IP
•NMap pings the remote target with 0 byte packets to each port
•If packets are not received back, port is open
•If packets are received, port is closed
•Sends different packets with different timing to determine filtered/unfiltered, version, etc.
•Firewalls can interfere with this process
Basic NMAP scans
•When run through command prompt or terminal, entry fields are:
•Program
•Constraints on run
•Target
•Ex. > nmap –sS scanme.nmap.org
•Ex. > nmap -Db ftp.pathetic.net secret.pathetic.net
Ethical Issues
•Can be used for hacking- to discover vulnerable ports
•System admins can use it to check that systems meet security standards
•Unauthorized use of Nmap on a system could be illegal. Make sure you have permission before using this tool
Download link
•https://nmap.org/download.html
2. Superscan tool
- SuperScan is a powerful connect-based TCP port scanner, pinger and hostname resolver. Multithreaded and asynchronous techniques make this program extremely fast and versatile.
Key Features
•Perform ping scans and port scans using any IP range.
•Use a text file to extract addresses from.
•Scan any port range from a built-in list or any given range.
•View responses from connected hosts.
•Modify the port list and port descriptions using the built in editor.
•Merge port lists to build new ones.
•Connect to any discovered open port using user-specified "helper" applications.
•Assign a custom helper application to any port.
•Save the scan list to a text file.
•Transmission speed control.
•User friendly interface.
•Comprehensive help file.
Download link
- This is first and foremost a tool for network administrators. Do not attempt to use this program against computers on the Internet that you have no right to scan since you are highly likely to be tracked down and attract the attention of your ISP, possibly resulting in your account being terminated.
- http://www.mcafee.com/in/downloads/free-tools/termsofuse.aspx
3. NetScan tool
- A FAST network scanner for scanning entire class B or class C IP networks for open ports. You can specify any amount of networks to scan, and any amount of ports on those networks to scan. You can also set the timeout speed to as small as 1 millisecond!
- Download Link :- http://net-scan.software.informer.com/1.0/
4. Auto-scan
- AutoScan-Network is a network scanner (discovering and managing application). No configuration is required to scan your network. The main goal is to print the list of connected equipments in your network.
Features
• Fast network scanner, Automatic network discovery
• TCP/IP scanner, Wake on lan functionality
• Multi-threaded Scanner, Port scanner
• Low surcharge on the network, VNC Client
• Telnet Client, SNMP scanner
• Simultaneous subnetworks scans without human intervention
• Realtime detection of any connected equipment
• Supervision of any equipment (router, server, firewall...)
• Supervision of any network service (smtp, http, pop, ...)
• Automatic detection of known operatic system (brand and version), you can also add any unknown equipment to the database
• The graphical interface can connect one or more scanner agents (local or remote)
• Scanner agents could be deployed all over the network to scan through any type of equipment (router, NAT, etc)
• Network Intruders detection (in intruders detection mode, all new equipments blacklisted)
• Complete network tree can be saved in a XML file.
• Privileged account is not required
Download link
•http://autoscan-network.com/download/
5. Unicornscan
- Unicornscan is an asynchronous network stimulus delivery/response recording tool. Meaning it sends out broken/unorganized/fragmented packets (without a regular pattern unlike other port scanning tools) to a host and waits for the target’s response. After getting the response the ttl value is calculated for each ports and there by identifying the operating system. For eg if the ttl=128, the operating system is Windows and so on. Pentesters use this tool when regular port scanning doesn’t work as the target might have enabled port scanning detection or has enabled IDS/IPS or honeypots. One cool feature of unicornscan is that, it uses different threads to send out packets & to receive them unlike other port scanners.
- Download link:- Website is down
6. Angry Ip scanner
- Angry IP Scanner (or simply ipscan) is an open-source and cross-platform network scanner designed to be fast and simple to use. It scans IP addresses and ports as well as has many other features.
- It is widely used by network administrators and just curious users around the world, including large and small enterprises, banks, and government agencies.
- It runs on Linux, Windows, and Mac OS X, possibly supporting other platforms as well.
- Download Link:- http://angryip.org/download/#windows
7. Splunk
•Splunk is an tool which collects data (any data!) of any amount, any location and any source. Since there is no upfront schema defined for Splunk you can really import any data you like. This is as Splunk tries to tell us the strength of their product. Splunk indexes all the data in receives on so called indexers and via a search-head you are able to search or view the data via a Dashboard. This can be done via basis search strings or via advanced graphs and/or apps.
•Download Link:- http://www.splunk.com/en_u/download.html?r=header
8. SoftPerfect Network Scanner 6.1.2
- SoftPerfect Network Scanner is a free multi-threaded IPv4/IPv6 scanner with a modern interface and many advanced features. It is intended for both system administrators and general users interested in computer security. The program pings computers, scans for listening TCP/UDP ports and discovers shared folders, including system and hidden ones.
- In addition, it can retrieve practically any information about network computers via WMI, SNMP, HTTP, NetBios and has a bunch of other features. It can also resolve host names and auto-detect the local and external IP address range. To assist with network administration, it supports remote shutdown and Wake-On-LAN.
Key features
- Performs a ping sweep and displays live devices.
- Fully supports both IPv4 and IPv6 discovery.
- Detects hardware MAC-addresses, even across routers.
- Detects hidden shared folders and writable ones.
- Detects your internal and external IP addresses.
- Scans for listening TCP ports, some UDP and SNMP services.
- Retrieves currently logged-on users, configured user accounts, uptime, etc.
- Mounts and explores network resources.
- Launches external third party applications.
- Exports results to HTML, XML, CSV and TXT.
- Supports Wake-On-LAN, remote shutdown and sending network messages.
- Retrieves any system information via WMI, remote registry, file system and service manager.
- Absolutely free, requires no installation, and does not contain any adware, spyware or malware
Download Link
- https://www.softperfect.com/download/freeware/netscan.zip
9.Siltheris Network Scanner
- Slitheris is a new highly advanced network scanner capable of scanning 100 network devices in about 5 minutes! Most IP scanners detect the basics like the MAC Address but leave the OS field empty and dont even bother identifying device types. Our IP scanner uses standard multi-threaded ping sweeps to find pingable devices and uses ARP pings and other advanced network discovery technology to detect unpingable hidden devices. Other state-of-the-art features include operating system detection of Windows Linux iOS and Android using proprietary TCPUDP OS fingerprinting. Slitheris includes experimental network device type detection to find servers printers switches routers iPhones iPads and more using heuristic analysis and device type fingerprinting. Network device names are pulled from up to 10 different possible locations on each device assisting in detecting network device types. It even detects true case-sensitive PC names for Windows computers and servers. Slitheris Network Scanner comes in both freeware and Pro versions to suit the needs of all small medium and enterprise organizations. Even home users will find Slitheris Network Scanner extremely useful on their own home networks.
Key Features
- Find Unpingable Network Devices
- Go Beyond Ping Sweeps With ARP Pings & IP Probes
- Operating System Fingerprinting
- Detect Windows, Linux, iOS , Android and More
- Device Type Identification Hints
- New Experimental Device Type Detection
- Better Device Name Detection
- More Device Names Means Less Empty Space
- 100% Free IP Scanner Included!
- Best results of any free network scanner!
Download Link
- http://slitheris-network-scanner.windows8compatible.com/download
10. IP TOOL 2.70
- This award-winning tool consists of 20 network utilities that offer a large viriety of network administration and monitoring services. Utilities: Local Info, Connection Monitor, NetBIOS Scanner, Shared resources scanner, SNMP Scanner, HostName Scanner, Port Scanner, Ping Scanner, UDP Scanner, Trace, NS LookUp, Finger, WhoIs, Time Synchronizer, Telnet client, HTTP client, IP-Monitor, Host Monitor, SNMP Trap Watcher. All information program can save to log files. HostMonitor can show messages, play sound, send e-mail, execute external programs. All this is available from an attractive tabbed interface you'll find easy to negotiate. Other features include multi-threaded operation, audio support, custom appearance, system tray support, etc.
Key Features
- Program allows multitask operation - You may use all utilities at the same time.
- Utilities can retrieve information from a single host, from all hosts within specified range of IP addresses (ex. 195.128.74.1 - 195.130.200.5) or work with list of hosts and IP addresses.
- IP-Tools can save obtained information into text file or create HTML reports.
- Highly intuitive interface makes operation easy for users
- Easy Install / Upgrade / Uninstall program
- After registration you gain the right to use ALL future IP-Tools updates and releases, on the same OS platform, in the registered mode.
Download Link
- https://www.ks-soft.net/ip-tools.eng/downpage.htm
11. NetBScanner
- NetBScanner is a network scanner tool that scans all computers in the IP addresses range you choose, using NetBIOS protocol. For every computer located by this NetBIOS scanner, the following information is displayed: IP Address, Computer Name, Workgroup or Domain, MAC Address, and the company that manufactured the network adapter (determined according to the MAC address). NetBScanner also shows whether a computer is a Master Browser. You can easily select one or more computers found by NetBScanner, and then export the list into csv/tab-delimited/xml/html file.
Key Features
- Network scanner to see which computers are connected to a IP address range
- For each computer identified as connected, see its IP Address, Computer Name, Workgroup or Domain, MAC Address, and the manufacturer of the network adapter (based on the unique MAC address)
- Export an XML or HTML file with the scan results
Download Link
- http://www.nirsoft.net/utils/netbscanner.zip
12. NetworkConnectLog 1.06
- NetworkConnectLog is a simple utility that repeatedly scans your local area network (Using ARP and Netbios protocols) and add a new log line every time that a new computer or device connects to your network, and when a computer or device disconnects from your network.
- After the connect/disconnect log lines are accumulated, you can easily export the log lines to comma-delimited/tab-delimited/html/xml file.
Key Features
- View the network activity for connections and disconnections of devices to a local area network
- View this information via either Netbios or ARP protocols
- Export the log record as an XML file or an HTML file using either tab or comma separation
Download Link
- http://www.nirsoft.net/utils/networkconnectlog.zip
13. Lizard Systems Network Scanner 3.5
- Network scanner is an IP scanner for network analysis that will allow you to see all network computers in several seconds. It can scan an unlimited number of IP address ranges or computers from a list. It scans computers not only for NetBIOS resources, but also for running FTP and web services. It is possible to check access rights to resources during the scan process. Network scanner works really fast thanks to multi-thread scanning where every computer is scanned independently. You can change the number of computers scanned simultaneously. You can export the scan results to html, txt or xml.
Key Features
- You can check for enabled web services, FTP or NetBIOS resources
- Filter the results by resources, current state (online or offline), access rights
- It works with large corporate networks spanning over hundreds of thousands of PCs
- Save the scan results as text, HTML or XML
- In order to speed up the process, Network Scanner uses multi threading
- To verify a computer is on, this utility doesn’t only ping, like other similar programs, but it also checks if a connection can be made to custom ports
- See which resources are available for the current user and the associated rights (read or write)
- You don’t need to be administrator to use the program
Download Link
- http://lizardsystems.com/downloads/
14. MiTec Network Scanner 4.0.0
- MiTeC Network Scanner is a robust, multi-threaded Port, IP, NetBIOS and SNMP scanner with many advanced features intended for both system administrators and general users who are interested in computer security. MiTeC Network Scanner performs ping sweeps, scans for opened TCP and UDP ports, resource shares and services. For devices with SNMP capability, available interfaces are detected and basic properties displayed. It also allows you to edit results, save/load results to/from CSV and print network device list and any data in any section can be exported to CSV. It can also resolve host names and auto-detect your local IP range.
Key Features
- Network neighbourhood, Ping, IP Address, MAC Address (even across routers)
- MAC Vendor, Device name, Device domain/workgroup, Logged user
- Operating system, BIOS, Model and CPU, System time and Up time
- Device description, Type flags (SQL server, Domain controller etc.)
- Remote device date and time, Listening TCP and UDP ports and SNMP services.
- Installed services on device, Shared resources
- Sessions, Open Files, Running processes
- Terminal sessions, Event Log
- Installed software
- SAM accounts
- WMI and SNMP Queries
- Powerful WhoIs client
Download Link
- http://www.mitec.cz/Downloads/NetScan.zip
15. Nsauditor Network Security Auditor 3.0.6
- Nsauditor Network Security Auditor is an advanced network security scanner for auditing and monitoring network computers for possible vulnerabilities. The software checks network computers using all potential methods that a hacker might use to attack it. Nsauditor is a complete networking utilities package for network auditing, scanning, monitoring and more. Nsauditor discovers network services and checks them for vulnerabilities. The software retrieves all TCP and UDP endpoints and shows their associated processes. Nsauditor discovers NetBios names, allows to audit MS SQL servers, scan remote computers for common Adware traces and more. The program also includes real-time network packet filtering and analyzing, remote network performance and network status monitoring, web proxy scanning, password auditing features. Nsauditor has intrusion detection system and firewall system to stop internet threats and block unwanted network connections.
Key Features
- Auditor
- Network Monitor
- NetBIOS Auditor
- MS SQL Server Auditor
- SNMP Auditor
- Packet Editor
- Sun RPC Auditor
- MS RPC Auditor
- Port Scanner
- Web Proxy Scanner
Download Link
- http://downloads.tomsguide.com/Network-Security-Auditor,0305-21956.html
16. Network Inventory Advisor 4.3
- Network Inventory Advisor audits all network software and hardware simply and efficiently. It automatically discovers all your network assets (Windows, Mac OS, Linux, SNMP-powered devices & more), scans them and builds flexible network inventory reports. It helps you control and reduce your IT costs with automated agent-free network inventory. Network Inventory Advisor simplifies enterprise assets audit and ensures effective agent-free network inventory. Track all hardware changes, manage software licenses and collect invaluable network data remotely. Our high-end network inventory software optionally integrates with Active Directory to import your OUs and recognize your IT structure immediately.
Key Features
- Software and hardware inventory
- All-in-one network inventory
- Software licensing audit
- Custom nodes inventory
- Multiple networks inventory
- Advanced network management
uChange management and control
Download Link
- http://network-inventory-advisor.en.softonic.com/download-tracker?th=1%2F6CH9aeXedl4L8u%2BBHNJXWTW%2BLP1LFlnGQpxqjlxAOiDpwTaUhlqw4XGCXzMSIHx0nxPyALx5EgWCpNtc5zMxnxIUTAQbUJ514ZBXSkJSTN4p7%2BwJmO1T5%2BbBK6l8P%2B4MUei1gemfcK%2Bk%2F2TiR9cMYWTIpVxp%2FYHX6gtMTOFFzELlFP0RYzP48f%2FxXOL%2F106VLGcK3b5IqM5OwL%2Bj0ZYg%3D%3D
17. Infiltrator Network Security Scanner 4.6
- Infiltrator is a free network security scanner that can quickly audit your network computers for possible vulnerabilities, exploits, and information enumerations. It comes with a built-in database of know vulnerabilities, that can be updated online and allows you to select the items to scan for or to add custom entries to be included. Infiltrator can reveal and catalog a variety of information, including installed software, shares, users, drives, hotfixes, NetBios and SNMP information, open ports and much more. It can also audit password and security policies, perform HTTP/CGI server auditing, registry auditing In addition, Infiltrator also comes with 19 network utilities for footprinting, scanning, enumerating and gaining access to machines (ping sweep, whois lookups, email tracing, share scanning and more). The program can be run from the commandline, allowing for external scheduling and automated scanning.
Download Link
- http://www.softsia.com/download-kfsz.htm
18. YAPS 1.2.3.49
- Fast TCP/IP port scanner. It supports simultaneous connecting to many targets and command line and GUI mode. It has a customisable timeout and can scan range of addresses, or single address. Can resolve addresses and includes names for well known ports
Key Features
- Supports simultaneous connecting to many targets
- Supports command line and GUI mode
- Customisable timeout
- Can scan range of addresses, or single address
- Can resolve addresses Includes names for well known ports
Download Link
- http://www.softpedia.com/get/Network-Tools/Network-IP-Scanner/YAPS.shtml#download
19. Global Network Inventory 4.1.0.1
- Global Network Inventory is a powerful and flexible software and hardware inventory system that can be used as an audit scanner in an agent-free and zero deployment environments. If used as an audit scanner, it only requires full administrator rights to the remote computers you wish to scan. Global Network Inventory can audit remote computers and even network appliances, including hubs, network printers, document centers, etc.
- Global Network Inventory agent can also be deployed to perform regular audits initiated through the domain login script when your users log on the network. In this scenario, Global Network Inventory agent is exported to a shared network directory, and audit results are collected in audit repository directory as snap files and later merged into the main database
Key Features
- Scan computers by IP range, by domain, single computers, or computers, defined by the Global Network Inventory host file.
- Reliable IP detection and identification of network appliances such as switches, network printers, document centers, hubs, and other devices.
- Scan only items that you need by customizing scan elements.
- View scan results, including historic results for all scans, individual machines, or selected number of addresses.
- Fully customizable layouts and color schemes on all views and reports. Export data to HTML, XML, Microsoft Excel, and text formats.
- Schedule inventory scans to run at specified time, hourly, daily, weekly, monthly, and annually. Ability to generate reports on schedule after every scan, daily, weekly, or monthly.
- Reports can be saved on disk, sent via email, or both.
- The program comes with dozens of customizable reports. New reports can be easily added through the user interface.
- Audits can be performed by deploying a scan agent through the domain login script.
- Licenses are network-based rather than user-based.
Download Link
- http://www.softpedia.com/get/Network-Tools/Misc-Networking-Tools/Global-Network-Inventory.shtml#download
20. Professional Look at Net 2.2.8.2
- "professional Look at Net" is a portable network monitoring tools - net scanner, ports scanner and packets sniffer. The Network scanning don't required network administrator privilege, only host administrator right require for silent scanning and Ethernet frames or IP packets capturing. IP packets filtering on IP addresses, ports, outgoings, incomings and more. Possible auto save 500, 2000 or 5000 capturing packets, with viewing saved and capturing packets in ASCII and HEX (hexadecimal) mode. Also possible edit any other (no packets) source in HEX mode.
Download Link
- http://www.snapfiles.com/php/sfdwnld.php?id=111440&a=7137671&loc=2
21. WhatsUp Gold PortScanner Tool 1.0
- Understanding host vulnerabilities is a critical component of overall network security. As a network engineer, you are responsible for protecting your infrastructure from malware, worms, hackers, trojans, and viruses - reducing the opportunity for exploits to find their ways in is your mission!
- The WhatsUp Gold PortScanner tool makes sure all the doors on your network are locked and secure, providing the visibility you need to ensure your hosts are secure.
Key Features
- Identify active hosts using ICMP and TCP
- Utilize multiple scanning deep-level technologies to deduce open ports
- Bookmark scanning configurations as favorites for quick assess
- Utilize the included database of known ports, or customize it to your environment
Download Link
- http://www.top4download.com/whatsup-gold-portscanner-tool/download-pmbxdzzw.html
22. LAN Spider 2.3
- LAN Spider goes through your local area network to search the shared directories for certain files: documents, drawings, music & video files and many others. LAN Spider features include: Fast multi-thread search. LAN Spider is the fastest file searching utility: tests shows 300-500% increased performance over against all other utilities on the market. Archives support. LAN Spider unpacks archives and looks through the packed files automatically.
Key Features
- Fast parallel search (up to 100 concurrent searches)
- Compressed archives support
- Domain, workgroup and IP range addressing
- Plenty of search filters and options
- Search results export & printing
- Multi-language support
- Coming soon! FTP, HTTP and P2P protocols support.
Download Link
- http://lan-spider.windows8compatible.com/force-download
23. Rogue DHCP Server Detection 1.0
- Rogue DHCP Server Detection is a free tool from the Microsoft DHCP Team that enables network administrators to detect potentially rogue DNS servers on the subnet.The program scans the selected subnet and produces a list of all DHCP servers and marks the ones that have not been authorized by Active Directory.The scan can be performed manually or automatically every X minutes from the system tray
Key Features
- The tool can be run one time or can be scheduled to run at specified interval.
- Can be run on a specified interface by selecting one of the discovered interfaces.
- Retrieves all the authorized DHCP servers in the forest and displays them.
- Ability to validate (not Authorize in AD) a DHCP server which is not rogue and persist this information Minimize the tool, which makes it invisible.
- A tray icon will be present which would display the status.
Download Link
- http://www.symantec.com/connect/sites/default/files/dhcpfind.zip
24. Medieval Bluetooth Network Scanner 1.4
- This program can analyze and scan your Bluetooth network, giving detailed informations about local and remote devices found. You can also browse supported services of each device in a clear and straightforward user-interface. Windows XP SP1 (or above) and Windows Vista are both fully supported. Works with native Microsoft Bluetooth stack only.
Key Features
- See all the local Bluetooth devices
- See all the remote Bluetooth devices
- Learn their device names, device addresses, device classes, last times seen, and other information
- Simple tabbed interface to switch between viewing local and remote Bluetooth connections
- Refresh button to re-scan for new Bluetooth devices
Download Link
- http://www.sharewarejunction.com/get/dl/52344/
25. MSR Strider URL Tracer 1.0.1.0
- When you visit a website, your browser may be instructed to visit other third-party domains without your knowledge. Some of these third-party domains raise security, privacy and safety concerns.
- The Strider URL Tracer is a tool that reveals these third-party domains and it includes a Typo-Patrol feature that generates and scans sites that capitalize on inadvertent URL misspellings, a process known as typo-squatting.
- The tool also enables parents to block typo-squatting domains that serve adult ads on typos of children´s Web sites.Requires Microsoft .NET Framework. (Note that .NET Framework is included in Windows XP. It is recommended to update to the latest version.)
Download Link
- http://www.snapfiles.com/php/sfdwnld.php?id=110118&a=7141652&loc=2
26. LanSpy 2.0
- LanSpy is a suite of networking utilities for managing a network. But they can most certainly be used for a variety of different things. The application does a very simple thing: scan a computer host. You can, of course, define what happens during that scan. By default, it pings the host, it performs a variety of network checks and an open-port scan, both UDP and TCP. The information you can acquire from a single scan is quite useful. When I scanned a random computer on my network, I received information about the local time on that computer, about what version of windows they had, the MAC address, how many ports they had open, when the system started, what kind of shares were active, and a lot more.
Key Features
- Audit your network for security reason issues
- View processes on remote computers
- Show list of installed application on workstations
- Detect shares, open ports and user accounts
Download Link
- http://lanspy.software.informer.com/download/#
27. WotWeb 1.08
- WotWeb is a cut-down port scanner specifically made to scan for and display active web servers and shows the server software running on them. IP lists can be entered manually or by reading from a file. Scanning is fast and accurate and the acquired list of servers can be saved to a comma separated text file for importing into your favorite spreadsheet application for further analysis.
Download Link
- http://www.snapfiles.com/php/sfdwnld.php?id=106380&a=7115064&loc=2