Encryption
and
Key Distribution Methods
APPLIED DATA COMMUNICATION
Tallinn University of Technology
Gülçin Yıldırım - Team #12
What is Encryption?

Encryption is the process of encoding messages or information in such a way that only authorized parties can read it.

Why Encryption?
Confidentiality
Authentication
Message Integrity
Access and Availability
Eavesdropping
Intercept messages

Inserting messages
Actively insert messages into connection

Impersonation
Can fake (spoof) source address in packet (or any field in packet)

Hijacking
"Take over" ongoing connection by removing sender or receiver by inserting himself in place

Denial of Service
Prevent service from being used by others (e.g, by overloading resources)

Insecure Communication

Sender
Intended Receiver

MITM
Secure Channel

Sender
Intended Receiver
MITM

Encrypted Message

Sender
Intended Receiver
MITM


A Secret Message
371c79266d08ca124f3f8ea8ebb5d368

Encryption
- Generates a ciphertext from a plaintext using an encryption key and an encryption algorithm (cipher)
- It is a two way process:
an encrypted data is expected to be decrypted later.
Plaintext

A Secret Message
371c79266d08ca124f3f8ea8ebb5d368
Ciphertext
Cipher

Key
Encryption Types
Symmetric Key Encryption
Public
Key Encryption



Symmetric Key Encryption

-
All communicating parties use the same key
- Key is used both for encryption and decryption
Symmetric Key Encryption
- Faster compared to public key encryption
- Key needs to be stored securely (only accessed when required)
- Secure channel required to transfer the key
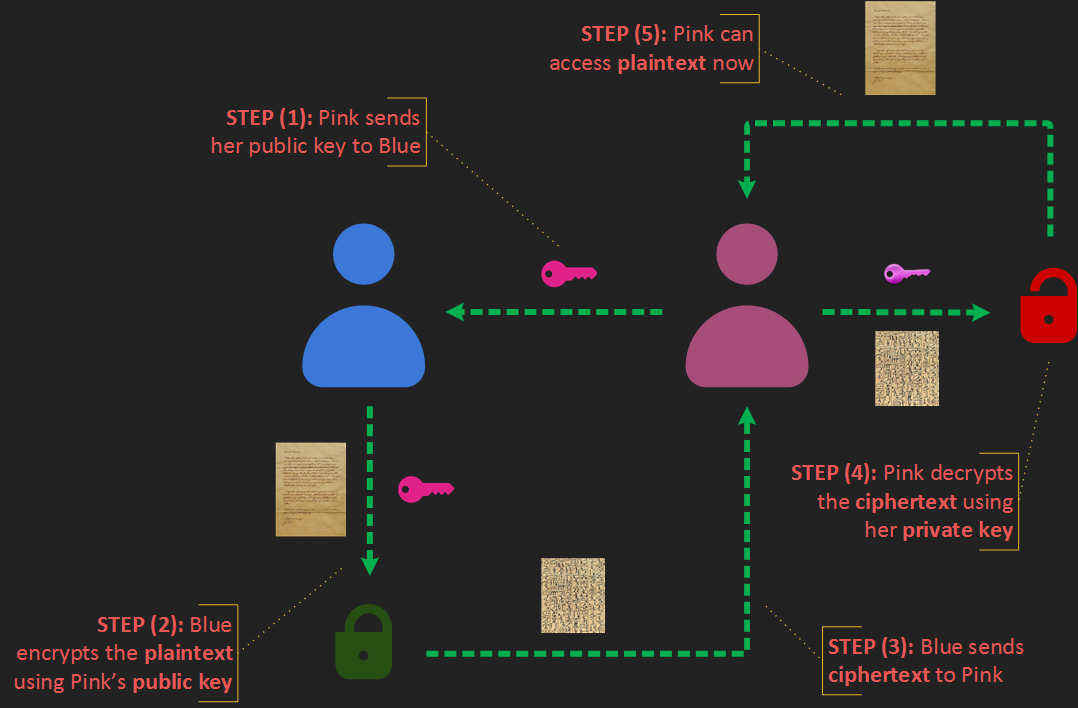
Public Key Encryption
Requires two keys:
- Public Key: used for encryption
- Private Key: used for decryption
All communicating parties exchange their public keys
Sender encrypts the plaintext using receiver's public key
Receiver decrypts the ciphertext using their own private key


Public Key Encryption
-
Slower compared to Symmetric Key Encryption
-
Public key & ciphertext can be sent over an insecure channel
- More secure because there is no need to share private keys with anyone
Public Key Encryption




Public Key
(share with pink)
Private Key
(keep it secret)
Public Key
(share with blue)
Private Key (keep it secret)
Public Key Encryption
Logic Behind the Keys
Trying to find a prize behind a series of number of doors

Public & Symmetric Key Mix
Performance ?
Security ?
Public key encryption used to exchange keys
Symmetric key encryption used to encrypt data
Encryption Algorithms

Block Cipher and Stream Cipher
Encryption Algorithms
- An encryption algorithm is called "cipher"
- There are two types of ciphers:
- Block cipher
-
Stream cipher
- Two concepts are very important for both of them:
- Prime numbers
- Entropy for random number generation
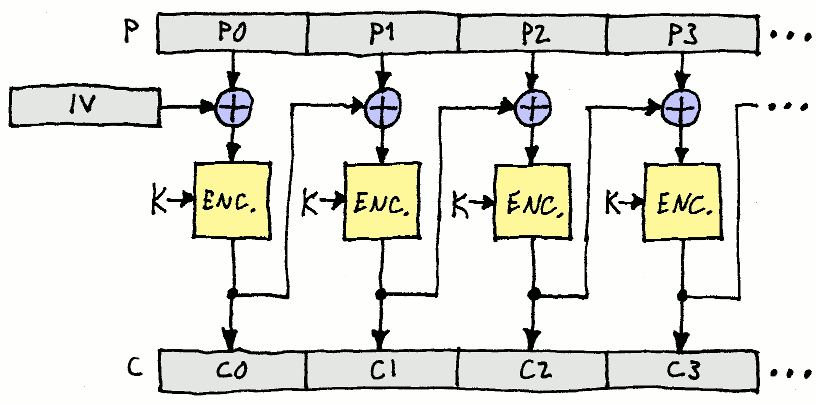
Block Cipher
Operates on fixed-size blocks (N bits) and uses fixed-size keys (K bits)
- Reads N-bits of data from the plaintext
- Uses the key and applies the encryption algorithm
- Produces ciphertext in size of N-bits
- Repeats steps 1-4 until all plaintext is processed
Block Cipher - AES
One of the most popular block ciphers is the AES algorithm.
Some other examples are: DES, Blowfish, RC5, ...
- AES stands for Advanced Encryption Standard
- Works on 128 bits (16 bytes) of blocks
- Uses 128, 192 or 256 bits of keys
- Operates on a 4x4 matrix of bytes
There are four stages in the algorithm:
-
KeyExpansions: Keys are derived from the provided key
-
InitialRound: AddRoundKey
-
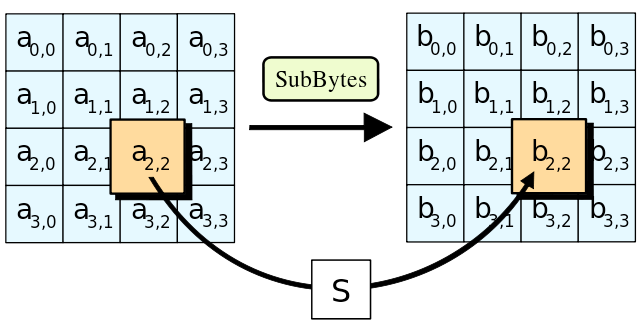
Rounds: SubBytes, ShiftRows, MixColumns, AddRoundKey
-
FinalRound: SubBytes, ShiftRows, AddRoundKey
Block Cipher - AES
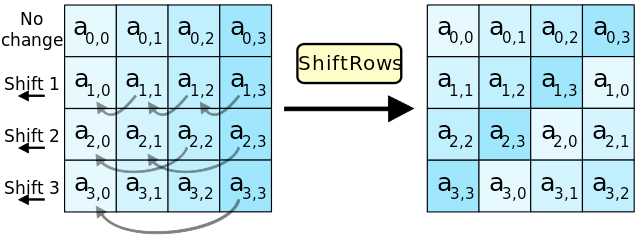
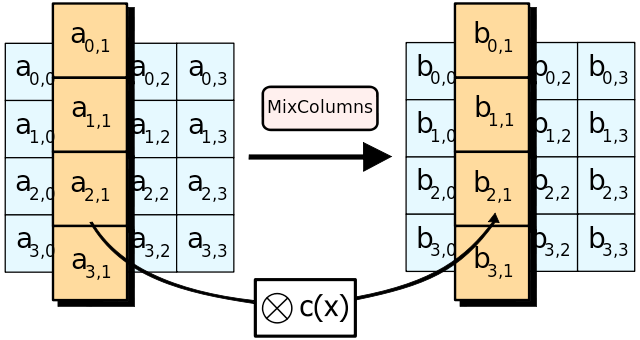
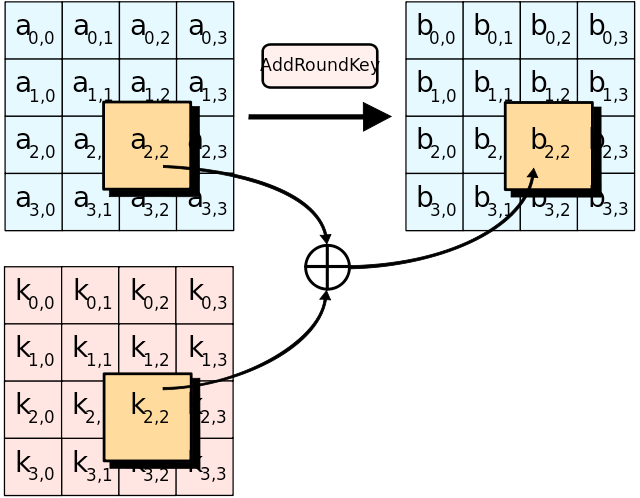
Stream Cipher
Operates on variable-size blocks (N bits) and uses random-size keys
- Generates a random number N
- Reads N-bits of data from the plaintext
- Uses the key and applies the encryption algorithm
- Produces ciphertext in size of N-bits
- Repeats steps 1-5 until all plaintext is processed
A popular stream cipher algorithm is RC4.
However, it is replaced by RC5, a block cipher algorithm.
Key Distribution Methods
The main concern of a key distribution method is how to securely supply keys between all communicating parties
There are some important security questions we must consider:
-
Symmetric Key Encryption
- Is the shared key stored securely? Is it compromised?
- Is the communication channel secure?
-
Public Key Encryption
- Am I encrypting for the intended receiver?
A key distribution method helps us with those concerns.
Key Distribution Methods
There are various different key distribution methods for different encryption types:
-
In symmetric key encryption, trusted key distribution center (KDC) is acting as intermediary between parties
-
In public key encryption, public key servers are used for both uploading and downloading public keys
- One another method is using a public key infrastructure (PKI) to share SSL certificates. A Certificate Authority (CA) provides public keys and also validates SSL certificates
Use-Case: GPG
- GPG (GNU Privacy Guard) is a very popular application that uses public key encryption
- Most commonly used for encryption / decryption of files & email messages
- Available for many platforms: Linux, Mac OS X, Microsoft Windows, BSD, etc...
- There are very large key servers to distribute public keys (e.g., MIT PGP Public Key Server)
Demo - Sender
Demo - Receiver
References
- https://dribbble.com/shots/2295470-Encryption-Key-Zoom
- https://dribbble.com/shots/2321171-Secure-Area
- https://pixabay.com/p-369540/?no_redirect
- https://www.istockphoto.com/illustrations/one+burglar
- https://dribbble.com/shots/1708900-Encryption-Keys-Animation
- https://dribbble.com/shots/1883333-Lock-and-Key
- https://dribbble.com/shots/2028614-Cripto
- https://dribbble.com/shots/1512967-The-Key
- https://dribbble.com/shots/1386297-Gold-Key-GIF
- https://www.cs.rit.edu/~ark/lectures/https02/https.shtml
- https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
- http://people.ee.duke.edu/~romit/courses/f07/material/7-security.pdf
- https://www.youtube.com/watch?v=ERp8420ucGs
Thank you!
