(O)Auth Gone South
OAuth attacks



{
"alg": "none",
"typ": "JWT"
}.
{
"name": "César Silva",
"email": "mail@apl3b.com",
"role": "AppSec Guy",
"twitter": "Apl3b",
"company": "Farfetch",
"location": "Porto"
}Quick Review
The Juice
Questions


(AuthN)
Authentication

The act of confirming the truth of an attribute of a single piece of data claimed true by an entity

Authorization
(AuthZ)

The function of specifying access rights/privileges to resources
Jargon 101


{Resource Owner}
{Client}
{Authorization Server}
{Resource Server}
Resource Owner => User
Client => Application
Authorization Server => Identity Provider
Resource Server => API

OAuth
Stands for Open Authorization





{Resource Owner}
{Client}
{Authorization Server}
{Resource Server}
Single User Identity across multiple system
Each application is also known
Identities Centralized
Understanding of a "Access Context"
{Flow}

Implicit Grant
Redirect-based Flow
User credentials inserted in AS
Tokens in the Browser
Cannot use Refresh Tokens
Currently Deprecated
+----------+ | | | User- | | Agent | | | | | | | | | | | | | | | | | | | | | +----------+ | (A) | ^ +---------+ | | | Client | | | +---------+
Client Identifier +---------------+ ----(A)-- & Redirection URI --->| | | Authorization | | Server | | | | | +---------------+
+----------+ | Resource | | Owner | | | +----------+ ^ | (B)
----(B)-- User authenticates -->
<---(C)--- Redirection URI ----< with Access Token in Fragment
+---------------+ ----(D)--- Redirection URI ---->| Web-Hosted | without Fragment | Client | | Resource | | | +---------------+
<---(E)------- Script ---------<
(F)
|
(G) Access Token (+ ID Token for OIDC)
|
v
+
-
-
-


Authorization Code Grant
Redirect-based Flow
+----------+ | | | User- | | Agent | | | | | +----------+ | (A) | ^ +---------+ | | | Client | | | +---------+
Client Identifier +---------------+ ----(A)-- & Redirection URI --->| | (+PKCE) | Authorization | | Server | | | | | +---------------+
+----------+ | Resource | | Owner | | | +----------+ ^ | (B)
----(B)-- User authenticates -->
---(C)-- Authorization Code ---<
^ | | | | >---(D)-- Authorization Code ---------' & Redirection URI (+PKCE)
| (C) | v
v
|
|
|
|
|
|
|
<---(E)----- Access Token (+ ID Token)-------'
(+ Optional Refresh Token)
User credentials inserted in AS
All the bells and whistles
Can use Refresh Tokens
Can avoid tokens in the Browser
+
+
+
+
-
More complex to implement



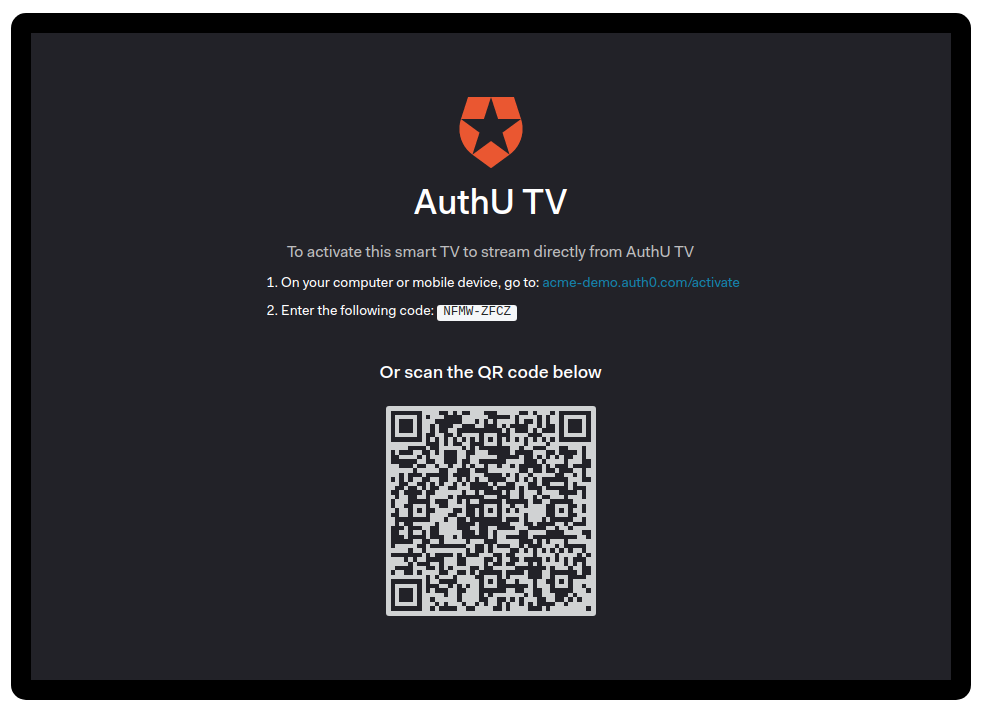
Device Code Grant
"Intermediary" Flow
Inputless devices supported
No credentials inserted
+
+----------+ +----------------+
| |>---(A)-- Client Identifier --->| |
| | | |
| | | |
| | | |
| Device | | |
| Client | | |
| | | |
| | | |
| | | |
| | | Authorization |
| | | Server |
+----------+ | |
| |
| |
| |
| |
| |
| |
| |
| |
| |
+----------------+
<---(B)-- Device Code, --------< User Code, & Verification URI
v : (C) User Code & Verification URI : v +----------+ | End User | | at | | Browser | +----------+
<---(D)-- End user reviews ---> authorization request
[polling] >---(E)-- Device Code ---------> & Client Identifier
<---(F)-- Access Token --------< (+ Optional Refresh Token)
+
-
More complex to implement
-
Relies on secondary client
(or have a worse experience)


Resource Owner Password Grant
"Direct input" Flow
Credentials inserted into the Client
Tokens in the browser/application
-
Deprecated
+----------+
| Resource |
| Owner |
| |
+----------+
v
| Resource Owner
(A) Password Credentials
|
v
+---------+
| |
| |
| Client |
| |
| |
+---------+
+---------------+ >--(B)---- Resource Owner ------->| | Password Credentials | Authorization | | Server | | | | | +---------------+
<--(C)---- Access Token ---------< (w/ Optional Refresh Token)
-
-


Client Credentials Grant
"Machine to Machine" Flow
Simple to implement
Just for Clients (no Users)
+
-
+---------+ | | | | | Client | | | | | +---------+
+---------------+
| |
>--(A)- Client Authentication --->| Authorization |
| Server |
| |
| |
+---------------+
<--(B)---- Access Token ---------<







Session Fixation
Account Binding Attacks

<a href="https://hackerone.com/reports/423136"/>
(Attacker)
(Victim)
(Authorization Server)
(Application A)
(fixates session)
(attacker's session)
(sends crafted URL to AS)
(users already had account)
(goes to AS and accepts consent)
(attacker's tokens returned)
(sends tokens to application, previous account associated)
(uses account to access victim's account)
<a href="https://hackerone.com/reports/922456"/>

Open Redirect

<a href="https://hackerone.com/reports/110293"/>
<a href="https://hackerone.com/reports/665651"/>
<a href="https://hackerone.com/reports/405100"/>
<a href="https://hackerone.com/reports/131202"/>
<a href="https://hackerone.com/reports/541701"/>
<a href="https://hackerone.com/reports/3930"/>
(Attacker)
(Authorization Server)
(Victim)
(Application)
(Malicious App)
(maliciouly crafted URL)
(goes to AS and Authenticates)
(AS tells to be redirected to Malicious APP)
(expected landing)
(malicious redirect)

CSRF

(Authorization Server)
(Victim)
(Malicious App)
(API)
(navigates to malicious site)
(tells the browser to perform consent)
(commands AS to accept consent)
(steals victim's info)
<a href="https://blog.teddykatz.com/2019/11/05/github-oauth-bypass.html"/>
<a href="https://hackerone.com/reports/215381"/>

XSS

(Attacker)
(Authorization Server)
(Victim)
(goes to AS)
(Sends Credentials)
<a href="https://hackerone.com/reports/456333"/>
<a href="https://hackerone.com/reports/87040"/>

Token Leaks

<a href="https://hackerone.com/reports/202781"/>
(Application)
(API)
(request with token)
(Another API)
(request with token)

Replay Attacks

(Attacker)
(Victim)
(Authorization Server)
(API)
(goes to AS and accepts consent)
(code returned)
(sends autheticated request)
(information)
(replays leaked request)
(exchanges code )
(token returned )
(token returned)
(sends autheticated request)
(information)
<a href="https://hackerone.com/reports/55140"/>

Clickjacking
Tapjacking

(Victim Application)
(Interaction)
(Malicious Application)
<a href="https://hackerone.com/reports/87561"/>
<a href="https://hackerone.com/reports/65825"/>
<a href="https://hackerone.com/reports/244967"/>

Client Misconfiguration

<a href="https://hackerone.com/reports/434763"/>

Code Injection

(Attacker)
(Victim)
(Authorization Server)
(API)
(goes to AS and accepts consent)
(code returned)
(sends autheticated request)
(information)
(exchanges stolen code)
(exchanges code )
(token returned )
(token returned)
(sends autheticated request)
(information)
<a href="https://hackerone.com/reports/219205"/>
<a href="https://hackerone.com/reports/46485"/>

?

Extra Refs
<a href="https://tools.ietf.org/html/rfc6819"/>

Federation Examples

Token Exchange by the Client

(Mobile App)
(WeChat Server)
(Our API)
(goes to AS and authenticates)
(code returned)
(sends autheticated request)
(information)
(exchanges code )
(token returned )
(FF Identity)
(Wanna Auth)
(Redirect to WeChat)
(WeChat Token)
(FF Token)

Token Exchange by the AS

(Mobile App)
(WeChat Server)
(Our API)
(goes to AS and authenticates)
(code returned)
(sends autheticated request)
(information)
(exchanges code )
(WeChat token)
(FF Identity)
(Wanna Auth)
(Redirect to WeChat)
(WeChat Code)
(FF Token)
