Security Testing
Arun.S
Senior Security Consultant @ IBM
Email : aruns014@in.ibm.com
@Arunthomas115
www.linkedin.com/in/arun1105


Let's start with basics!!!
CIA Triad of Information Security
- Confidentiality
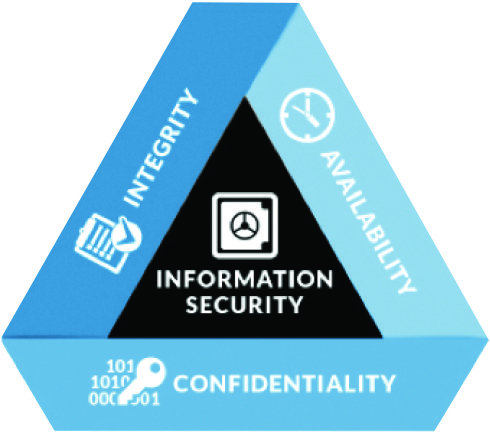
- Integrity
- Availability
Security Testing is deemed successful when the below attributes of an application are intact
- Non-Repudiation
OVERVIEW
- Integrity
- Confidentiality
- Availability
- Authorization
- Authentication
Security Testing
Authentication - Is the person / package being truthful about their identity?
Authorization - Is the package/person allowed to do this operation?
Availability - Will this service do me good any time of the day?
Confidentiality - Is the service and information safe from unauthorized prying eyes?
Integrity - Does the service provide only the correct information to the user?
Non-Repudiation - Did the communication happen between two legitimate users?
Secure SDLC
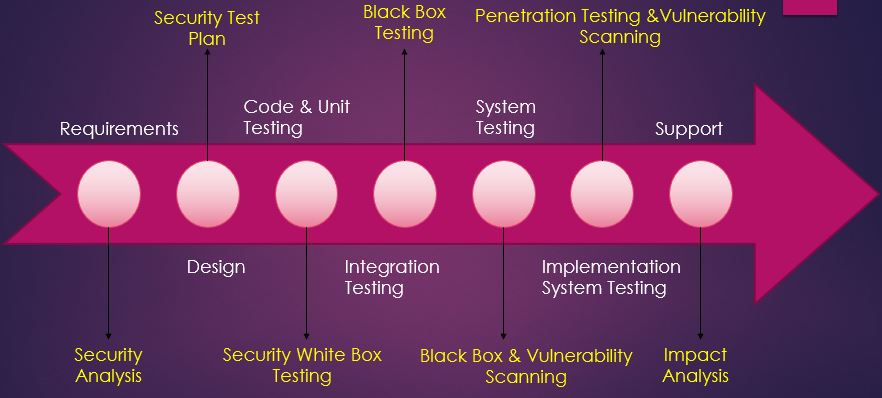
Why Should I learn all these?
The goal is to make sure that the system/ application does not have any loopholes/vulnerabilities/system fallbacks.
Types of Security Testing

Types of Penetration Testing

Penetration Testing Life Cycle

Penetration Testing Services
- Network Pentesting
- IoT Pentesting
- Web Application Pentesting
- Mobile Application Pentesting
- Web Services Pentesting
- WiFi Pentesting
So to perform all these pentesting is there any standards available?
PenTesting Methodologies
OWASP testing guide
PCI Penetration testing guide
Penetration Testing Execution Standard(PTES)
NIST 800-115
Penetration Testing Framework
Information Systems Security Assessment Framework (ISSAF)
Open Source Security Testing Methodology Manual (“OSSTMM”)
OWASP
The Open Web Application Security Project (OWASP) is a great resource for software security professionals.
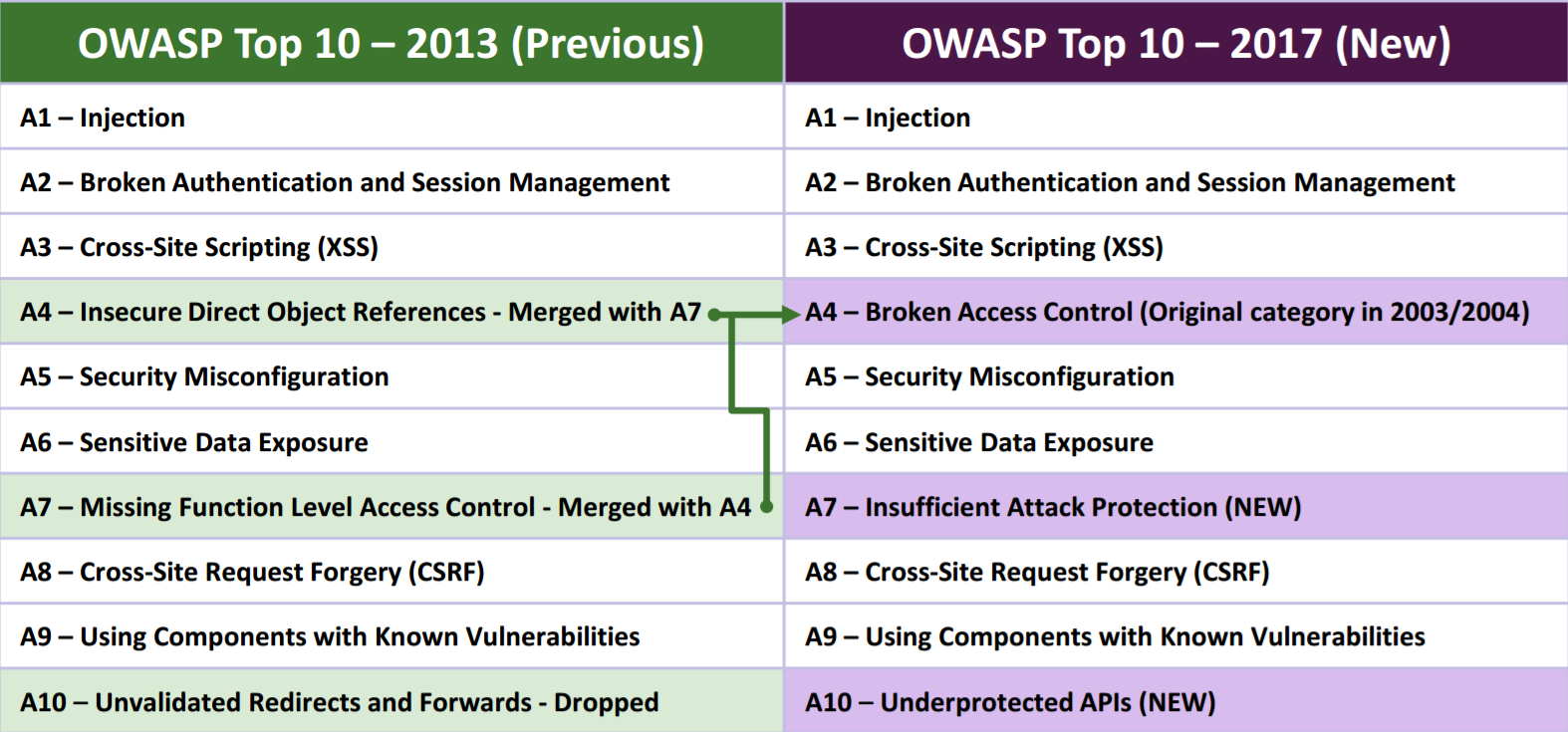
What are the list of tools used for Security Testing???
The list quite exhaustive!!!!

These are few Important Tools !!!!!!
It's time for Demo!!!!
But how to start Learning Security Testing?
- XSS-Payloads - Ultimate resource for all things cross-site including payloads, tools, games and documentation.
- PTES - Penetration Testing Execution Standard
- Vulnerability Assessment Framework - Penetration Testing Framework.
- PENTEST-WIKI - A free online security knowledge library for pentesters / researchers.
- OWASP - Open Web Application Security Project
Useful Resources
Is there any Vulnerable Websites/Platforms available for Practicing?
https://ibm.box.com/s/mj5tyh9wnocexsiytge3nruozewktnf5

https://goo.gl/E6HCCC
What's the future of Security Testing???
Let's see some products which already available in online !!!!



What about the security ???
What Needs to be Secured?
-
Misconception - IoT Security is != Device Security.
Hardware

Web/Mobile Interface

Communication Channel
- But, we can categories it as follows;
- There are many surface areas which needs to be evaluated for IoT Security.
Web/Mobile Interface Security?
Webapplication security Issues - OWASP Top 10 WebAppSec
Mobile Application Security Issues - OWASP Top 10 MobileAppsec
https://www.owasp.org/index.php/Top_10_2013-Top_10
https://www.owasp.org/index.php/Mobile_Top_10_2016-Top_10
OWASP - IoT Top 10
- I1 : Insecure Web Interface.
- I2 : Insufficient Authentication/Authorization.
- I3 : insecure Network Services.
- I4 : Lack of Transport Encryption/Integrity Verification.
- I5 : Privacy Concerns.
- I6 : Insecure Cloud Interface.
- I7 : Insecure Mobile Interface.
- I8 : Insufficient Security Configurability.
- I9 : Insecure Software/Firmware.
- I10 : Poor Physical Security.

