Json Web Token
You will love it more than your parents!
@About me



let benjamin = {
age: 26,
city: 'Versailles',
company: 'Companeo',
dev: ['Javascript', 'AngularJs', 'Node.js', 'C#', 'Unity3D'],
devSince: '2012-08-01'
}-
Identification by Login/password -
Create session on server -
Store session cookie on browser -
Send back cookie to server with every request
- Verify access right from session for every request
'Normal ' login Stack
JWT login stack
-
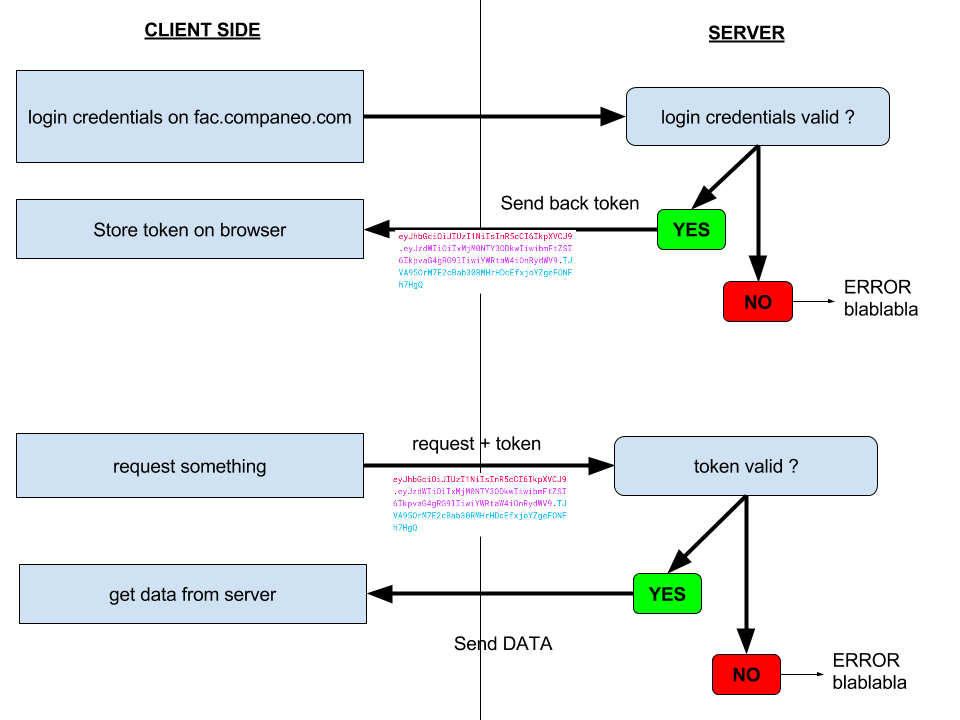
Identification by Login(/password) -
Store JWT on browser -
Send back JWT to server with every request
- Verify access right from JWT for every request
NO STATE STORED ON SERVER!

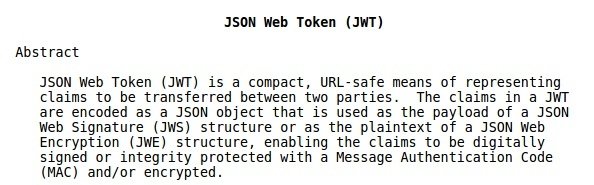
What's a JWT

Overview
JWS
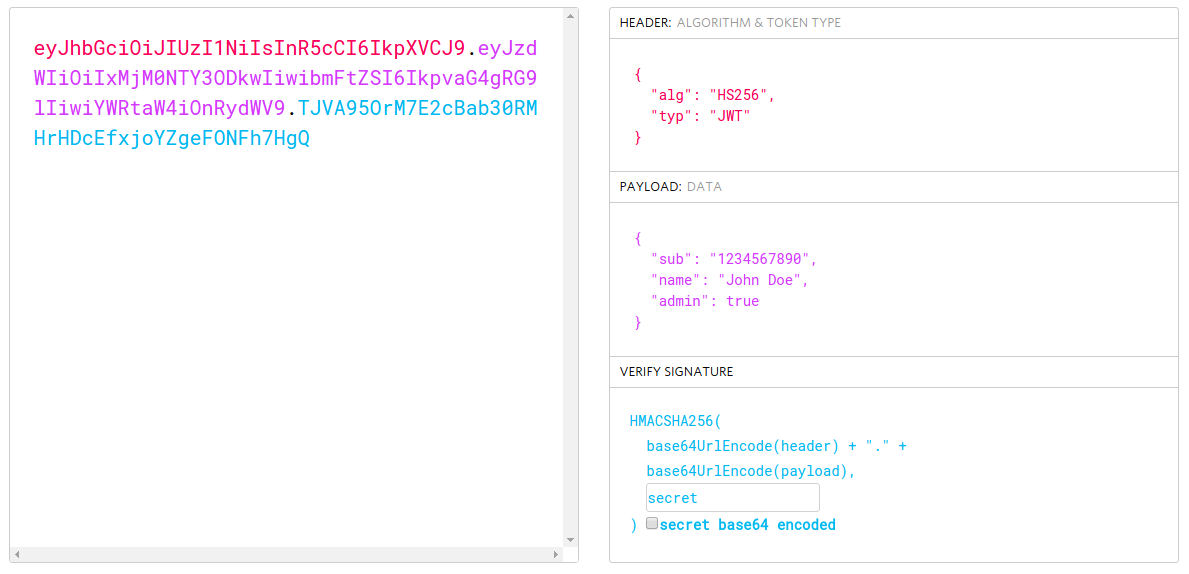
Header
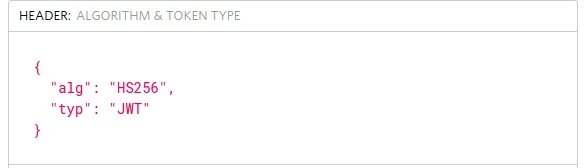

Available keys:
- typ (mandatory)
- alg (mandatory)
-
cty (mandatory if nested JWT or JWE)
Payload
Available keys (link):

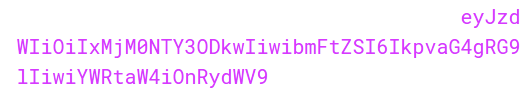
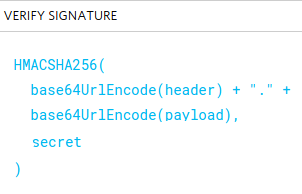
Signature

My best practices:
with JWS
-
Never store JWT inside Db -
Don't store sensitive data in signed JWT
-
Store JWT with HTML5 solutions (localStorage/sessionStorage)
-
Send JWT inside your headers request -
Use short token expiration date -
Use issuer claim to identify your token -
Avoid nested JWT ( JWE inside a JWT ) #KISS
- Don't trust data from unchecked JWT
Basics with JWT
Time to test!
with a JWS
How to manage JWT?
-
Store the jti inside your dB and remove it when you want to block access to your app
-
It will keep track of your created tokens
JWT libraries
CLICK !
CLICK !
CLICK !
CLICK !
CLICK !
CLICK !
CLICK !
CLICK !
CLICK !
CLICK !
CLICK !
CLICK !
CLICK !
CLICK !