Web Application Security
Parameter Tampering Vulnerability
Parag Dave parag.dave@qualitrix.com

Text
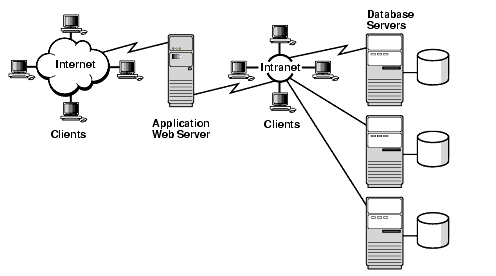
What is Web application?
A web application or web service is a software application that is accessible using a web browser or HTTP(s) user agent.
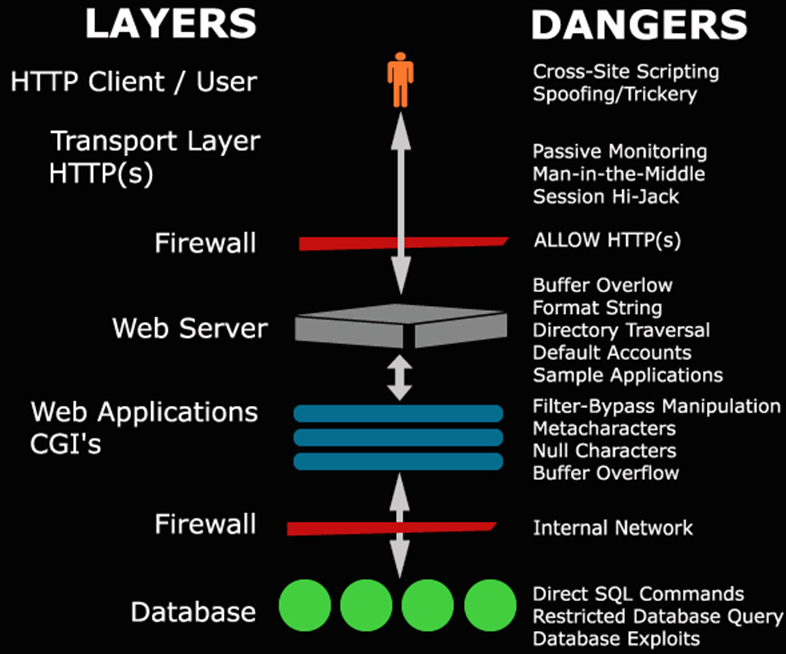
Image Reference: http://www.blackhat.com/presentations/bh-europe-01/jeremiah-grossman/bh-europe-01-grossman.ppt
Why is this important?

Parameter Tampering
- The Parameter Tampering attack is based on the manipulation of parameters exchanged between client and server in order to modify application data, such as user credentials and permissions, price and quantity of products, etc.
- This attack can be performed by a malicious user who wants to exploit the application for their own benefit, or an attacker who wishes to attack a third-person using a Man-in-the-middle attack.
How is it exploited?
Some of the exploited area:
- Many times simple playing with parameter in query string.
- Burp suite can intercept data.
- Proxies can be attacked (Man in the middle).
- Plug-ins can show data.
Demo
Description:
This vulnerability is found from one of the international food chain websites.
How do you prevent it?
Some of the prevention places:
- Web forms should contain some built-in protection
- Use regex to limit or validate data
- Server side validation is always compared with all inputs
- Avoid unwanted or hidden data
- Don't allow interception
Thank You