The web remembers

A web cookie (yum) is a small piece of data sent from a website and stored in your browser.
HTTP cookies are so 1995.

Lou Montulli
Cookies were designed to be a reliable mechanism for websites to remember stateful information (such as items added in the shopping cart in an online store) or to record the user's browsing activity (including clicking particular buttons, logging in, or recording which pages were visited in the past).
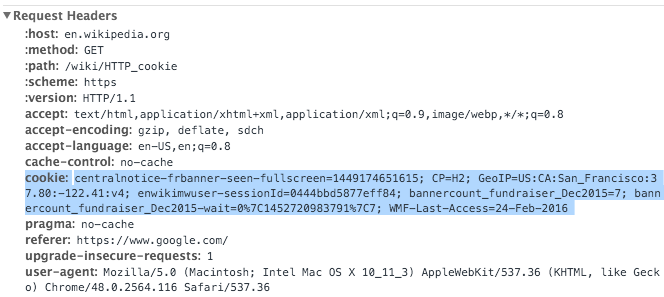
Cookies are sent with EVERY request.
Two decades later, we are no longer tracking products but people.

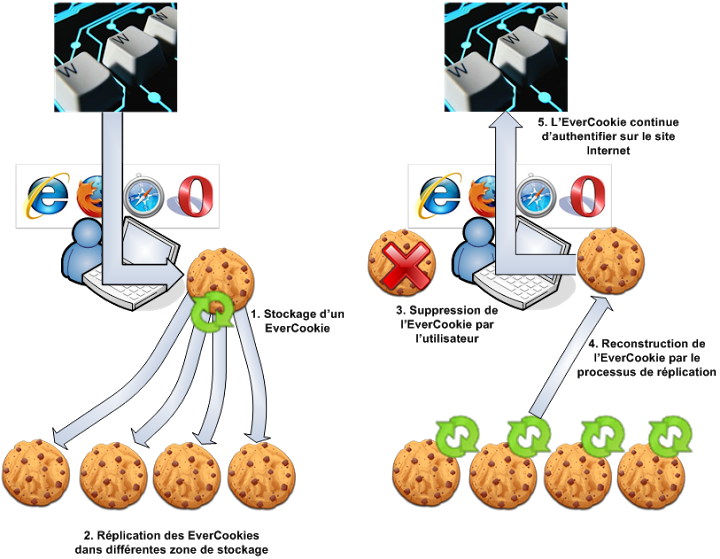
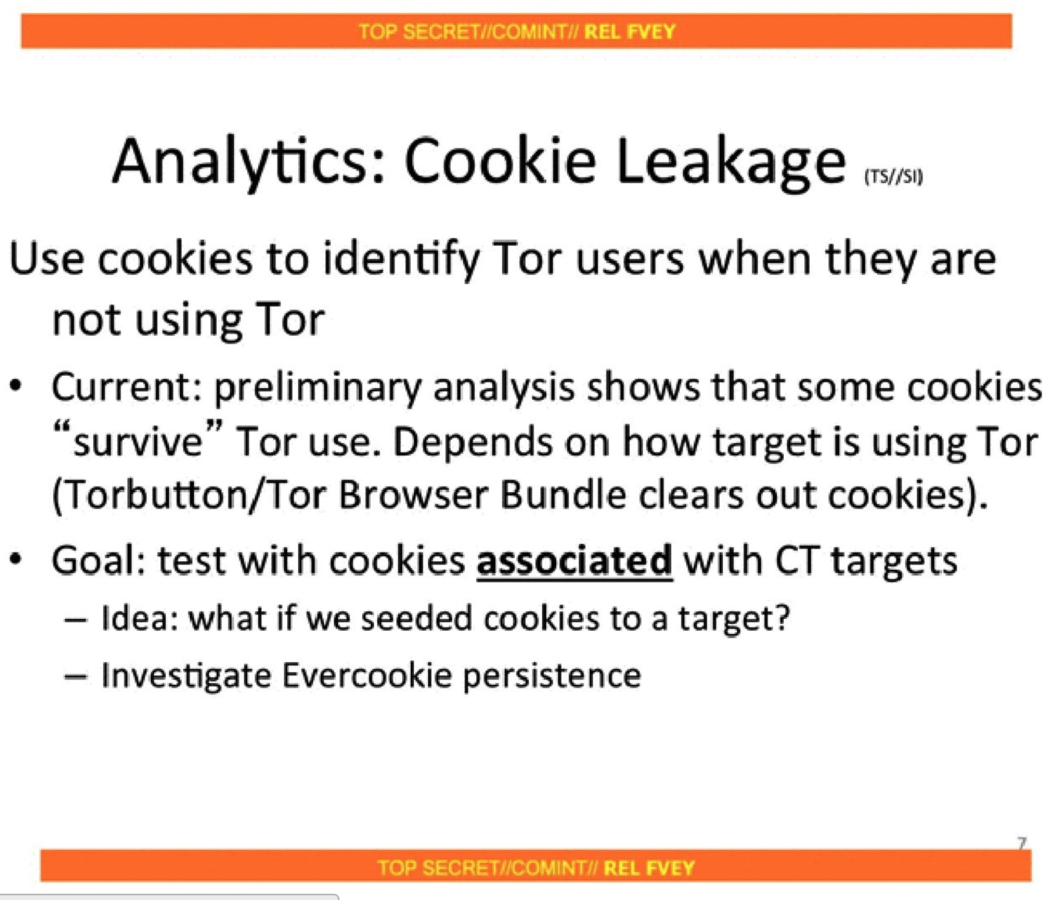
Samy Kamkar published the Evercookie library that not only sets a cookie, but actively resists deletion by copying itself in different forms on your machine and resurrecting itself like some privacy stealing zombie if it notices that some of the copies are missing or expired.
- Standard HTTP cookies (yawn)
- Locale Shared Objects (Flash cookies — not so popular these days)
- window.name caching (2–32MB but gets cleared easily)
- Silverlight Isolated Storage (good old Microsoft)
- Internet Explorer userData storage
- HTML5 Session Storage
- HTML5 Local Storage
- HTML5 Global Storage
- HTML5 Database Storage via SQLite
- HTTP ETags
- Web History
- Canvas fingerprinting
HTTP ETags
ETags are used for HTTP web cache validation to let your browser know if the
content needs to be refreshed or not using a collision-resistant hash function to fingerprint the asset.
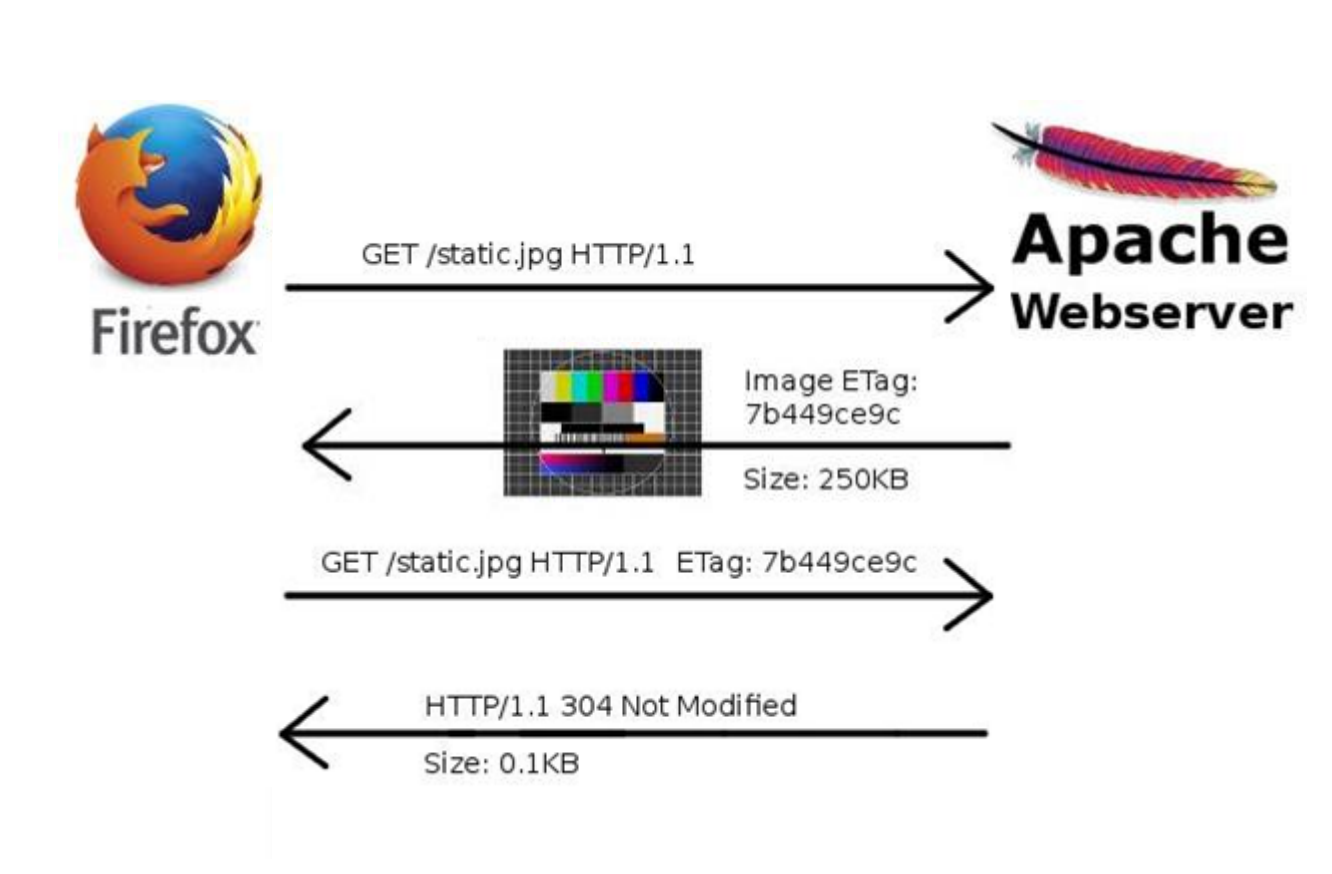
ETags can be used to track unique users, as HTTP cookies are increasingly being
deleted by privacy-aware users.
In July 2011, a team of researchers
at UC Berkeley reported that a number of websites, including Hulu.com and kissmetrics.com were using ETags
for tracking purposes.
Hulu and KISSmetrics have both ceased "respawning" as of 29 July 2011,
as KISSmetrics and over 20 of its clients are facing a class-action lawsuit over the use of
"undeletable" tracking cookies partially involving the use of ETags.
WebHistory
When a cookie is set, assuming the Web History caching is enabled,
it Base64 encodes the data to be stored.
Let's assume this data is "bcde" in Base64.
then access the following URLs in the background:
google.com/evercookie/cache/b
google.com/evercookie/cache/bc
google.com/evercookie/cache/bcd
google.com/evercookie/cache/bcde
google.com/evercookie/cache/bcde-
These URLs are now stored in history.
To get the session back, a code would loop through every possible Base64 character with brute force until it reaches the ending “-”
Canvas Fingerprint
Canvas fingerprinting works by exploiting the HTML5 canvas element. When a user visits a website with canvas fingerprinting, their browser is instructed to "draw" a hidden line of text or 3D graphic that is then converted to a digital token.
- different web browsers,
- different image processing engines,
- image export options,
- compression levels,
- final checksums may differ even if pixel-identical,
- operating systems have different fonts, and
- different algorithms and settings for anti-aliasing and sub-pixel rendering.
The token can be stored and shared with advertising partners to identify users when they visit affiliated websites. A profile can be created from the user's browsing activity allowing advertisers to target advertising to the user's inferred demographics and preferences.
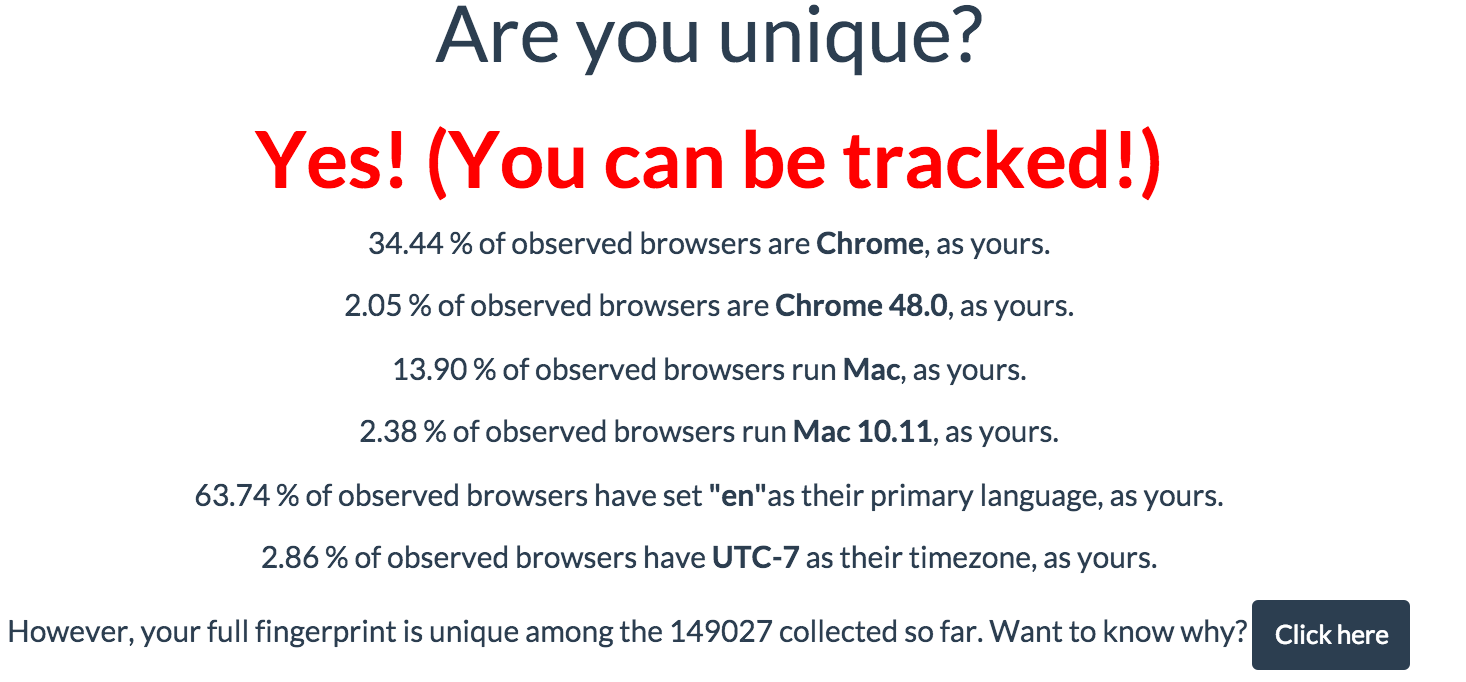
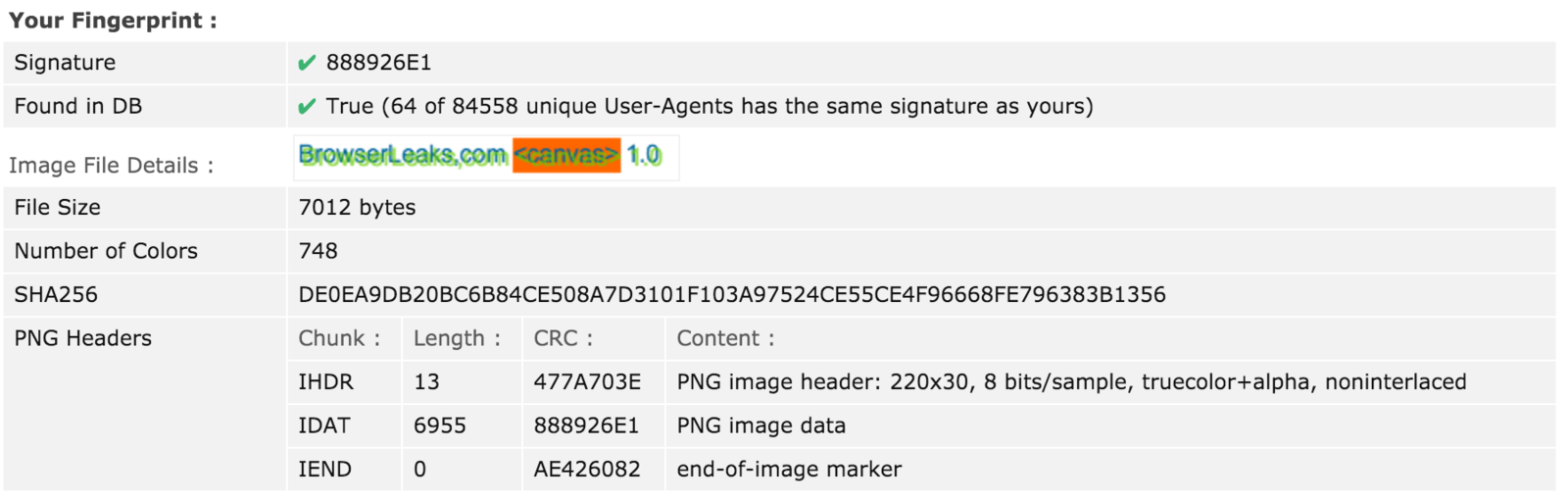
Good news for us, web browsers have found ways to mitigate and defend against most of the “evercookie” type of storage techniques. Unfortunately, people have a lot of free-time. The Chromium team published an article which pretty much says anything your browser does to communicate with the outside world is traceable.
https://www.chromium.org/Home/chromium-security/client-identification-mechanisms
You religiously clear your cookies and only use “safe browsing”, but your browser is leaking enough identifying bits of information to create a unique device-specific fingerprint. Without leaving cookies behind
Device fingerprinting
- screen size and color depth
- browser plugin details
- time zone
- HTTP_ACCEPT Headers
- language
- system fonts
- platform
- USER_AGENT
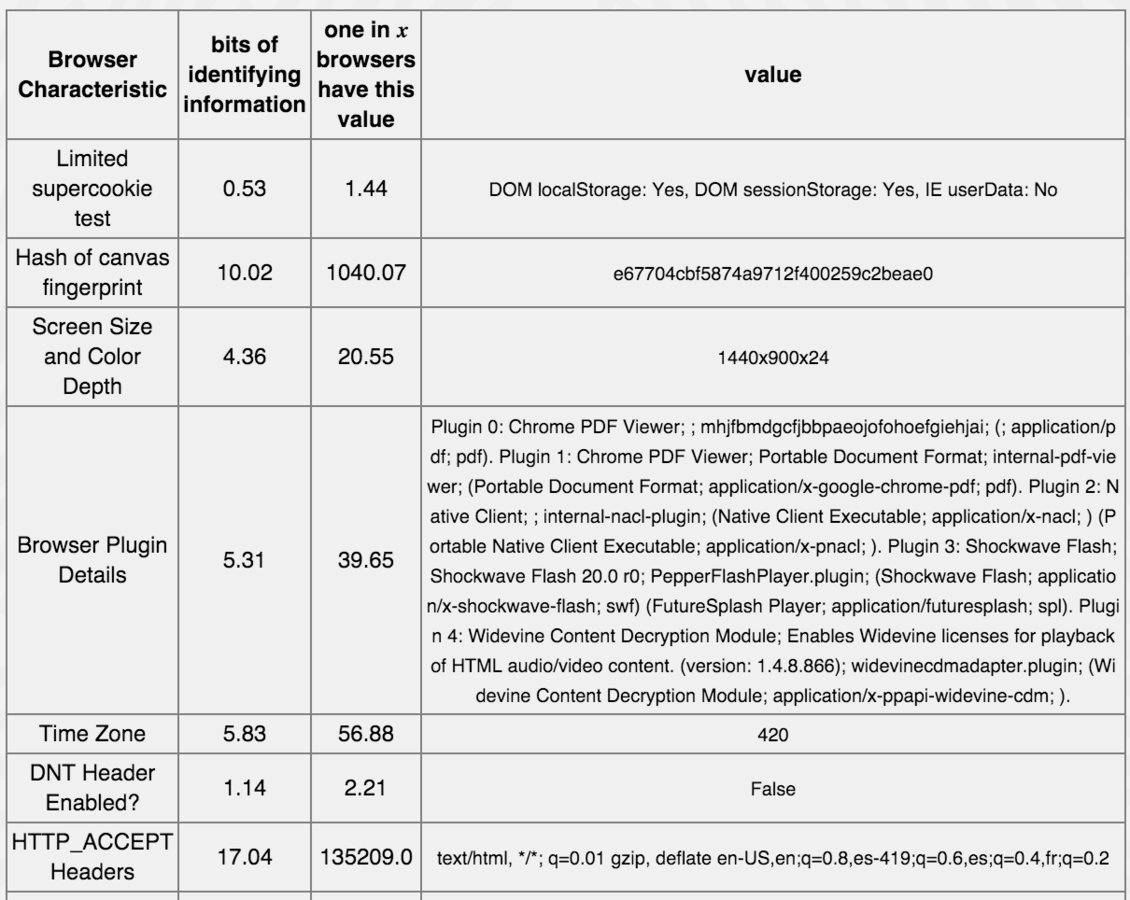
When device finger-printing is used in combination with other methods, you can only hope on the goodwill of sites not employing this technique and that a unicorn will magically appear and grant you a magic wish.
Recommendations:
- Keep in mind that if you want to use the Internet, there is no escape.
- Live in a cave
- Turn off JavaScript
- Use private navigation (though it wont work)
- Use addblock and other cool extensions
- Wipe web history often
Sleep well tonight
Thanks!
ccontreras@nearsoft.com
contact:
